
Cryptanalysis
Encyclopedia

Code (cryptography)
In cryptography, a code is a method used to transform a message into an obscured form, preventing those who do not possess special information, or key, required to apply the transform from understanding what is actually transmitted. The usual method is to use a codebook with a list of common...
).
Cryptanalysis is also used to refer to any attempt to circumvent the security of other types of cryptographic algorithm
Algorithm
In mathematics and computer science, an algorithm is an effective method expressed as a finite list of well-defined instructions for calculating a function. Algorithms are used for calculation, data processing, and automated reasoning...
s and protocols
Cryptographic protocol
A security protocol is an abstract or concrete protocol that performs a security-related function and applies cryptographic methods.A protocol describes how the algorithms should be used...
in general, and not just encryption
Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
. However, cryptanalysis usually excludes methods of attack that do not primarily target weaknesses in the actual cryptography
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, such as bribery
Bribery
Bribery, a form of corruption, is an act implying money or gift giving that alters the behavior of the recipient. Bribery constitutes a crime and is defined by Black's Law Dictionary as the offering, giving, receiving, or soliciting of any item of value to influence the actions of an official or...
, physical coercion
Rubber-hose cryptanalysis
In cryptography, rubber-hose cryptanalysis is the extraction of cryptographic secrets from a person by coercion or torture, in contrast to a mathematical or technical cryptanalytic attack....
, burglary
Burglary
Burglary is a crime, the essence of which is illicit entry into a building for the purposes of committing an offense. Usually that offense will be theft, but most jurisdictions specify others which fall within the ambit of burglary...
, keystroke logging
Keystroke logging
Keystroke logging is the action of tracking the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored...
, and social engineering
Social engineering (security)
Social engineering is commonly understood to mean the art of manipulating people into performing actions or divulging confidential information...
, although these types of attack are an important concern and are often more effective than traditional cryptanalysis.
Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like Bombe
Bombe
The bombe was an electromechanical device used by British cryptologists to help decipher German Enigma-machine-encrypted signals during World War II...
s and Colossus computer
Colossus computer
Not to be confused with the fictional computer of the same name in the movie Colossus: The Forbin Project.Colossus was the world's first electronic, digital, programmable computer. Colossus and its successors were used by British codebreakers to help read encrypted German messages during World War II...
s at Bletchley Park
Bletchley Park
Bletchley Park is an estate located in the town of Bletchley, in Buckinghamshire, England, which currently houses the National Museum of Computing...
in World War II
World War II
World War II, or the Second World War , was a global conflict lasting from 1939 to 1945, involving most of the world's nations—including all of the great powers—eventually forming two opposing military alliances: the Allies and the Axis...
, to the computer-based schemes of the present. The results of cryptanalysis have also changed — it is no longer possible to have unlimited success in codebreaking, and there is a hierarchical classification of what constitutes an attack. In the mid-1970s, a new class of cryptography was introduced: asymmetric cryptography. Methods for breaking these cryptosystem
Cryptosystem
There are two different meanings of the word cryptosystem. One is used by the cryptographic community, while the other is the meaning understood by the public.- General meaning :...
s are typically radically different from before, and usually involve solving carefully constructed problems in pure mathematics
Pure mathematics
Broadly speaking, pure mathematics is mathematics which studies entirely abstract concepts. From the eighteenth century onwards, this was a recognized category of mathematical activity, sometimes characterized as speculative mathematics, and at variance with the trend towards meeting the needs of...
, the best-known being integer factorization
Integer factorization
In number theory, integer factorization or prime factorization is the decomposition of a composite number into smaller non-trivial divisors, which when multiplied together equal the original integer....
.
History of cryptanalysis
Cryptanalysis has coevolved together with cryptography, and the contest can be traced through the history of cryptographyHistory of cryptography
The history of cryptography begins thousands of years ago. Until recent decades, it has been the story of what might be called classic cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids...
—new cipher
Cipher
In cryptography, a cipher is an algorithm for performing encryption or decryption — a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. In non-technical usage, a “cipher” is the same thing as a “code”; however, the concepts...
s being designed to replace old broken designs, and new cryptanalytic techniques invented to crack the improved schemes. In practice, they are viewed as two sides of the same coin: in order to create secure cryptography, you have to design against possible cryptanalysis.
Classical cryptanalysis

Code (cryptography)
In cryptography, a code is a method used to transform a message into an obscured form, preventing those who do not possess special information, or key, required to apply the transform from understanding what is actually transmitted. The usual method is to use a codebook with a list of common...
and cipher
Cipher
In cryptography, a cipher is an algorithm for performing encryption or decryption — a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. In non-technical usage, a “cipher” is the same thing as a “code”; however, the concepts...
s are much older. The first known recorded explanation of cryptanalysis was given by 9th-century Arab
Arab
Arab people, also known as Arabs , are a panethnicity primarily living in the Arab world, which is located in Western Asia and North Africa. They are identified as such on one or more of genealogical, linguistic, or cultural grounds, with tribal affiliations, and intra-tribal relationships playing...
ian polymath
Polymath
A polymath is a person whose expertise spans a significant number of different subject areas. In less formal terms, a polymath may simply be someone who is very knowledgeable...
, Al-Kindi
Al-Kindi
' , known as "the Philosopher of the Arabs", was a Muslim Arab philosopher, mathematician, physician, and musician. Al-Kindi was the first of the Muslim peripatetic philosophers, and is unanimously hailed as the "father of Islamic or Arabic philosophy" for his synthesis, adaptation and promotion...
(also known as "Alkindus" in Europe), in A Manuscript on Deciphering Cryptographic Messages. This treatise includes a description of the method of frequency analysis
Frequency analysis
In cryptanalysis, frequency analysis is the study of the frequency of letters or groups of letters in a ciphertext. The method is used as an aid to breaking classical ciphers....
(Ibrahim Al-Kadi, 1992- ref-3). Italian
Italy
Italy , officially the Italian Republic languages]] under the European Charter for Regional or Minority Languages. In each of these, Italy's official name is as follows:;;;;;;;;), is a unitary parliamentary republic in South-Central Europe. To the north it borders France, Switzerland, Austria and...
scholar Giambattista della Porta
Giambattista della Porta
Giambattista della Porta , also known as Giovanni Battista Della Porta and John Baptist Porta, was an Italian scholar, polymath and playwright who lived in Naples at the time of the Scientific Revolution and Reformation....
was author of a seminal work on cryptanalysis "De Furtivis Literarum Notis".
Frequency analysis
Frequency analysis
In cryptanalysis, frequency analysis is the study of the frequency of letters or groups of letters in a ciphertext. The method is used as an aid to breaking classical ciphers....
is the basic tool for breaking most classical cipher
Classical cipher
A cipher is a means of concealing a message, where letters of the message are substituted or transposed for other letters, letter pairs, and sometimes for many letters. In cryptography, a classical cipher is a type of cipher that was used historically but now has fallen, for the most part, into...
s. In natural languages, certain letters of the alphabet
Alphabet
An alphabet is a standard set of letters—basic written symbols or graphemes—each of which represents a phoneme in a spoken language, either as it exists now or as it was in the past. There are other systems, such as logographies, in which each character represents a word, morpheme, or semantic...
appear more frequently than others; in English
English language
English is a West Germanic language that arose in the Anglo-Saxon kingdoms of England and spread into what was to become south-east Scotland under the influence of the Anglian medieval kingdom of Northumbria...
, "E
E
E is the fifth letter and a vowel in the basic modern Latin alphabet. It is the most commonly used letter in the Czech, Danish, Dutch, English, French, German, Hungarian, Latin, Norwegian, Spanish, and Swedish languages.-History:...
" is likely to be the most common letter in any sample of plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
. Similarly, the digraph
Digraph (orthography)
A digraph or digram is a pair of characters used to write one phoneme or a sequence of phonemes that does not correspond to the normal values of the two characters combined...
"TH" is the most likely pair of letters in English, and so on. Frequency analysis relies on a cipher failing to hide these statistics
Statistics
Statistics is the study of the collection, organization, analysis, and interpretation of data. It deals with all aspects of this, including the planning of data collection in terms of the design of surveys and experiments....
. For example, in a simple substitution cipher (where each letter is simply replaced with another), the most frequent letter in the ciphertext
Ciphertext
In cryptography, ciphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher...
would be a likely candidate for "E". Frequency analysis of such a cipher is therefore relatively easy, provided that the ciphertext is long enough to give a reasonably representative count of the letters of the alphabet that it contains.
In Europe during the 15th and 16th centuries, the idea of a polyalphabetic substitution cipher
Polyalphabetic cipher
A polyalphabetic cipher is any cipher based on substitution, using multiple substitution alphabets. The Vigenère cipher is probably the best-known example of a polyalphabetic cipher, though it is a simplified special case...
was developed, among others by the French diplomat Blaise de Vigenère
Blaise de Vigenère
Blaise de Vigenère was a French diplomat and cryptographer. The Vigenère cipher is so named due to the cipher being incorrectly attributed to him in the 19th century....
(1523–96). For some three centuries, the Vigenère cipher
Vigenère cipher
The Vigenère cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution....
, which uses a repeating key to select different encryption alphabets in rotation, was considered to be completely secure (le chiffre indéchiffrable—"the indecipherable cipher"). Nevertheless, Charles Babbage
Charles Babbage
Charles Babbage, FRS was an English mathematician, philosopher, inventor and mechanical engineer who originated the concept of a programmable computer...
(1791–1871) and later, independently, Friedrich Kasiski
Friedrich Kasiski
Major Friedrich Wilhelm Kasiski was a Prussian infantry officer, cryptographer and archeologist. Kasiski was born in Schlochau, West Prussia .-Military service:...
(1805–81) succeeded in breaking this cipher. During World War I
World War I
World War I , which was predominantly called the World War or the Great War from its occurrence until 1939, and the First World War or World War I thereafter, was a major war centred in Europe that began on 28 July 1914 and lasted until 11 November 1918...
, inventors in several countries developed rotor cipher machines such as Arthur Scherbius
Arthur Scherbius
Arthur Scherbius was a German electrical engineer who patented an invention for a mechanical cipher machine, later sold as the Enigma machine.Scherbius was born in Frankfurt am Main and his father was a small businessman...
' Enigma
Enigma machine
An Enigma machine is any of a family of related electro-mechanical rotor cipher machines used for the encryption and decryption of secret messages. Enigma was invented by German engineer Arthur Scherbius at the end of World War I...
, in an attempt to minimise the repetition that had been exploited to break the Vigenère system.
In practice, frequency analysis relies as much on linguistic
Linguistics
Linguistics is the scientific study of human language. Linguistics can be broadly broken into three categories or subfields of study: language form, language meaning, and language in context....
knowledge as it does on statistics, but as ciphers became more complex, mathematics
Mathematics
Mathematics is the study of quantity, space, structure, and change. Mathematicians seek out patterns and formulate new conjectures. Mathematicians resolve the truth or falsity of conjectures by mathematical proofs, which are arguments sufficient to convince other mathematicians of their validity...
became more important in cryptanalysis. This change was particularly evident before and during World War II
World War II
World War II, or the Second World War , was a global conflict lasting from 1939 to 1945, involving most of the world's nations—including all of the great powers—eventually forming two opposing military alliances: the Allies and the Axis...
, where efforts to crack Axis
Axis Powers
The Axis powers , also known as the Axis alliance, Axis nations, Axis countries, or just the Axis, was an alignment of great powers during the mid-20th century that fought World War II against the Allies. It began in 1936 with treaties of friendship between Germany and Italy and between Germany and...
ciphers required new levels of mathematical sophistication. Moreover, automation was first applied to cryptanalysis in that era with the Polish Bomba
Bomba (cryptography)
The bomba, or bomba kryptologiczna was a special-purpose machine designed about October 1938 by Polish Cipher Bureau cryptologist Marian Rejewski to break German Enigma-machine ciphers....
device, the British Bombe
Bombe
The bombe was an electromechanical device used by British cryptologists to help decipher German Enigma-machine-encrypted signals during World War II...
development of it, the use of punched card
Punched card
A punched card, punch card, IBM card, or Hollerith card is a piece of stiff paper that contains digital information represented by the presence or absence of holes in predefined positions...
equipment, and in the Colossus computers — the first electronic digital computers to be controlled by a program.
Depth
Sending two or more messages with the same key is an insecure process. To a cryptanalyst the messages are then said to be "in depth". This may be detected by the messages having the same indicator by which the sending operator informs the receiving operator about the key generator initial settingsKey (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
for the message. In a symmetrical cipher, the same key that was applied to the plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
to produce the ciphertext
Ciphertext
In cryptography, ciphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher...
is applied to the ciphertext to recover the plaintext. A simple example of such a system is the Vernam cipher
Gilbert Vernam
Gilbert Sandford Vernam was an AT&T Bell Labs engineer who, in 1917, invented the stream cipher and later co-invented the one-time pad cipher. Vernam proposed a teleprinter cipher in which a previously-prepared key, kept on paper tape, is combined character by character with the plaintext message...
in which a long key is bit-for-bit combined with the plaintext or ciphertext using the "XOR" operator (symbolized by
 ):
): at each bit position
at each bit positionand
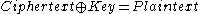 at each bit position
at each bit positionWhen the ciphertexts are in depth, combining them eliminates the common key, leaving just a combination of the two plaintexts:
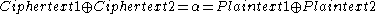 at each bit position
at each bit positionThe individual plaintexts can then be worked out by trying probable words (or phrases) at various locations; when the corresponding section of
 is XORed with a correct guess at the probable word, a stretch of the other plaintext is revealed, which can be recognized and (quite often) extended at each end, working back and forth between the plaintexts to recover much or all of them. When a recovered plaintext is then combined with its ciphertext, the key is revealed:
is XORed with a correct guess at the probable word, a stretch of the other plaintext is revealed, which can be recognized and (quite often) extended at each end, working back and forth between the plaintexts to recover much or all of them. When a recovered plaintext is then combined with its ciphertext, the key is revealed: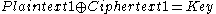 at each bit position
at each bit positionKnowledge of keys from a cipher may allow cryptanalysts to work out the system used for constructing them.
Depth reading can be applied in more complicated contexts to eliminate some of a system's parameters, or to "stack" messages so that source language statistics become exploitable. One way to properly align multiple messages that use the same periodic key starting at different positions is by the kappa test.
Modern cryptanalysis
Cryptanalysis of the Enigma
Cryptanalysis of the Enigma enabled the western Allies in World War II to read substantial amounts of secret Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military intelligence which, along with that from other decrypted Axis radio...
and other systems during World War II, it also made possible new methods of cryptography orders of magnitude more complex than ever before. Taken as a whole, modern cryptography has become much more impervious to cryptanalysis than the pen-and-paper systems of the past, and now seems to have the upper hand against pure cryptanalysis. The historian David Kahn notes,
Kahn goes on to mention increased opportunities for interception, bugging, side channel attack
Side channel attack
In cryptography, a side channel attack is any attack based on information gained from the physical implementation of a cryptosystem, rather than brute force or theoretical weaknesses in the algorithms...
s, and quantum computers
Quantum cryptography
Quantum key distribution uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages...
as replacements for the traditional means of cryptanalysis. In 2010, former NSA technical director Brian Snow said that both academic and government cryptographers are "moving very slowly forward in a mature field."
However, any postmortems for cryptanalysis may be premature. While the effectiveness of cryptanalytic methods employed by intelligence agencies remains unknown, many serious attacks against both academic and practical cryptographic primitives have been published in the modern era of computer cryptography:
- The block cipherBlock cipherIn cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
MadrygaMadrygaIn cryptography, Madryga is a block cipher created in 1984 by W. E. Madryga. It was designed to be easy and efficient for implementation in software...
, proposed in 1984 but not widely used, was found to be susceptible to ciphertext-only attackCiphertext-only attackIn cryptography, a ciphertext-only attack or known ciphertext attack is an attack model for cryptanalysis where the attacker is assumed to have access only to a set of ciphertexts....
s in 1998. - FEAL-4FEALIn cryptography, FEAL is a block cipher proposed as an alternative to the Data Encryption Standard , and designed to be much faster in software. The Feistel based algorithm was first published in 1987 by Akihiro Shimizu and Shoji Miyaguchi from NTT...
, proposed as a replacement for the DESData Encryption StandardThe Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
standard encryption algorithm but not widely used, was demolished by a spate of attacks from the academic community, many of which are entirely practical. - The A5/1A5/1A5/1 is a stream cipher used to provide over-the-air communication privacy in the GSM cellular telephone standard. It was initially kept secret, but became public knowledge through leaks and reverse engineering. A number of serious weaknesses in the cipher have been identified.-History and...
, A5/2A5/2A5/2 is a stream cipher used to provide voice privacy in the GSM cellular telephone protocol.The cipher is based around a combination of four linear feedback shift registers with irregular clocking and a non-linear combiner.In 1999, Ian Goldberg and David A...
, CMEA, and DECTDECT Standard CipherDECT Standard Cipher is an encryption standard, used in DECT phones to protect communication between a handset and its associated base station...
systems used in mobileMobile phoneA mobile phone is a device which can make and receive telephone calls over a radio link whilst moving around a wide geographic area. It does so by connecting to a cellular network provided by a mobile network operator...
and wireless phone technology can all be broken in hours, minutes or even in real-time using widely-available computing equipment. - Brute-force keyspace searchBrute-force searchIn computer science, brute-force search or exhaustive search, also known as generate and test, is a trivial but very general problem-solving technique that consists of systematically enumerating all possible candidates for the solution and checking whether each candidate satisfies the problem's...
has broken some real-world ciphers and applications, including single-DES (see EFF DES crackerEFF DES crackerIn cryptography, the EFF DES cracker is a machine built by the Electronic Frontier Foundation in 1998 to perform a brute force search of DES cipher's key space — that is, to decrypt an encrypted message by trying every possible key...
), 40-bit "export-strength" cryptography, and the DVD Content Scrambling System. - In 2001, Wired Equivalent PrivacyWired Equivalent PrivacyWired Equivalent Privacy is a weak security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standard ratified in September 1999, its intention was to provide data confidentiality comparable to that of a traditional wired network...
(WEP), a protocol used to secure Wi-FiWi-FiWi-Fi or Wifi, is a mechanism for wirelessly connecting electronic devices. A device enabled with Wi-Fi, such as a personal computer, video game console, smartphone, or digital audio player, can connect to the Internet via a wireless network access point. An access point has a range of about 20...
wireless networkWireless networkWireless network refers to any type of computer network that is not connected by cables of any kind. It is a method by which homes, telecommunications networks and enterprise installations avoid the costly process of introducing cables into a building, or as a connection between various equipment...
s, was shown to be breakable in practice because of a weakness in the RC4RC4In cryptography, RC4 is the most widely used software stream cipher and is used in popular protocols such as Secure Sockets Layer and WEP...
cipher and aspects of the WEP design that made related-key attackRelated-key attackIn cryptography, a related-key attack is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker...
s practical. WEP was later replaced by Wi-Fi Protected AccessWi-Fi Protected AccessWi-Fi Protected Access and Wi-Fi Protected Access II are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks...
. - In 2008, researchers conducted a proof-of-concept break of SSLTransport Layer SecurityTransport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
using weaknesses in the MD5MD5The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
hash functionCryptographic hash functionA cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
and certificate issuer practices that made it possible to exploit collision attackCollision attackIn cryptography, a collision attack on a cryptographic hash tries to find two arbitrary inputs that will produce the same hash value, i.e. a hash collision...
s on hash functions. The certificate issuers involved changed their practices to prevent the attack from being repeated.
Thus, while the best modern ciphers may be far more resistant to cryptanalysis than the Enigma
Enigma machine
An Enigma machine is any of a family of related electro-mechanical rotor cipher machines used for the encryption and decryption of secret messages. Enigma was invented by German engineer Arthur Scherbius at the end of World War I...
, cryptanalysis and the broader field of information security
Information security
Information security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction....
remain quite active.
The results of cryptanalysis

Treason
In law, treason is the crime that covers some of the more extreme acts against one's sovereign or nation. Historically, treason also covered the murder of specific social superiors, such as the murder of a husband by his wife. Treason against the king was known as high treason and treason against a...
for her involvement in three plots to assassinate Elizabeth I of England
Elizabeth I of England
Elizabeth I was queen regnant of England and Ireland from 17 November 1558 until her death. Sometimes called The Virgin Queen, Gloriana, or Good Queen Bess, Elizabeth was the fifth and last monarch of the Tudor dynasty...
which were known about because her coded correspondence with fellow conspirators had been deciphered by Thomas Phelippes
Thomas Phelippes
Thomas Phelippes was a forger and intelligence gatherer. He served mainly under Sir Francis Walsingham, in the time of Elizabeth I, deciphering the codes of those plotting against her. He is most remembered for his adding of a postscript to the "bloody letter" sent by Mary, Queen of Scots, to...
; in World War I
World War I
World War I , which was predominantly called the World War or the Great War from its occurrence until 1939, and the First World War or World War I thereafter, was a major war centred in Europe that began on 28 July 1914 and lasted until 11 November 1918...
, the breaking of the Zimmermann Telegram
Zimmermann Telegram
The Zimmermann Telegram was a 1917 diplomatic proposal from the German Empire to Mexico to make war against the United States. The proposal was caught by the British before it could get to Mexico. The revelation angered the Americans and led in part to a U.S...
was instrumental in bringing the United States into the war; in World War II
World War II
World War II, or the Second World War , was a global conflict lasting from 1939 to 1945, involving most of the world's nations—including all of the great powers—eventually forming two opposing military alliances: the Allies and the Axis...
, the cryptanalysis of the German ciphers — including the Enigma machine
Enigma machine
An Enigma machine is any of a family of related electro-mechanical rotor cipher machines used for the encryption and decryption of secret messages. Enigma was invented by German engineer Arthur Scherbius at the end of World War I...
and the Lorenz cipher
Lorenz cipher
The Lorenz SZ40, SZ42A and SZ42B were German rotor cipher machines used by the German Army during World War II. They were developed by C. Lorenz AG in Berlin. They implemented a Vernam stream cipher...
— has been credited with everything between shortening the end of the European war by a few months to determining the eventual result (see Ultra). The United States
United States
The United States of America is a federal constitutional republic comprising fifty states and a federal district...
also benefited from the cryptanalysis of the Japanese Purple code (see Magic
Magic (cryptography)
Magic was an Allied cryptanalysis project during World War II. It involved the United States Army's Signals Intelligence Section and the United States Navy's Communication Special Unit. -Codebreaking:...
).
Governments have long recognized the potential benefits of cryptanalysis for intelligence, both military and diplomatic, and established dedicated organizations devoted to breaking the codes and ciphers of other nations, for example, GCHQ and the NSA, organizations which are still very active today. In 2004, it was reported that the United States had broken Iran
Iran
Iran , officially the Islamic Republic of Iran , is a country in Southern and Western Asia. The name "Iran" has been in use natively since the Sassanian era and came into use internationally in 1935, before which the country was known to the Western world as Persia...
ian ciphers. (It is unknown, however, whether this was pure cryptanalysis, or whether other factors were involved:).
Types of cryptanalytic attack
Cryptanalytic attacks vary in potency and how much of a threat they pose to real-world cryptosystemCryptosystem
There are two different meanings of the word cryptosystem. One is used by the cryptographic community, while the other is the meaning understood by the public.- General meaning :...
s. A certificational weakness is a theoretical attack that is unlikely to be applicable in any real-world situation; the majority of results found in modern cryptanalytic research are of this type. Essentially, the practical importance of an attack is dependent on the answers to the following four questions:
- What knowledgeKnowledgeKnowledge is a familiarity with someone or something unknown, which can include information, facts, descriptions, or skills acquired through experience or education. It can refer to the theoretical or practical understanding of a subject...
and capabilities does the attacker need? - How much additional secret information is deduced?
- How much computation is required? (What is the computational complexityComputational ComplexityComputational Complexity may refer to:*Computational complexity theory*Computational Complexity...
?) - Does the attack break the full cryptosystem, or only a weakened version?
Access needed for the attack
Cryptanalysis can be performed under a number of assumptions about how much access the attacker has to the system under attack. As a basic starting point it is normally assumed that, for the purposes of analysis, the general algorithmAlgorithm
In mathematics and computer science, an algorithm is an effective method expressed as a finite list of well-defined instructions for calculating a function. Algorithms are used for calculation, data processing, and automated reasoning...
is known; this is Kerckhoffs' principle
Kerckhoffs' principle
In cryptography, Kerckhoffs's principle was stated by Auguste Kerckhoffs in the 19th century: A cryptosystem should be secure even if everything about the system, except the key, is public knowledge.Kerckhoffs's principle was reformulated by Claude Shannon as...
of "the enemy knows the system". This is a reasonable assumption in practice — throughout history, there are countless examples of secret algorithms falling into wider knowledge, variously through espionage
Espionage
Espionage or spying involves an individual obtaining information that is considered secret or confidential without the permission of the holder of the information. Espionage is inherently clandestine, lest the legitimate holder of the information change plans or take other countermeasures once it...
, betrayal
Betrayal
Betrayal is the breaking or violation of a presumptive contract, trust, or confidence that produces moral and psychological conflict within a relationship amongst individuals, between organizations or between individuals and organizations...
and reverse engineering
Reverse engineering
Reverse engineering is the process of discovering the technological principles of a device, object, or system through analysis of its structure, function, and operation...
. (On occasion, ciphers have been reconstructed through pure deduction; for example, the German Lorenz cipher
Lorenz cipher
The Lorenz SZ40, SZ42A and SZ42B were German rotor cipher machines used by the German Army during World War II. They were developed by C. Lorenz AG in Berlin. They implemented a Vernam stream cipher...
and the Japanese Purple code, and a variety of classical schemes).
Other assumptions include:
- Ciphertext-onlyCiphertext-only attackIn cryptography, a ciphertext-only attack or known ciphertext attack is an attack model for cryptanalysis where the attacker is assumed to have access only to a set of ciphertexts....
: the cryptanalyst has access only to a collection of ciphertextCiphertextIn cryptography, ciphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher...
s or codetexts. - Known-plaintextKnown-plaintext attackThe known-plaintext attack is an attack model for cryptanalysis where the attacker has samples of both the plaintext , and its encrypted version . These can be used to reveal further secret information such as secret keys and code books...
: the attacker has a set of ciphertexts to which he knows the corresponding plaintextPlaintextIn cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
. - Chosen-plaintext (chosen-ciphertext): the attacker can obtain the ciphertexts (plaintexts) corresponding to an arbitrary set of plaintexts (ciphertexts) of his own choosing.
- Adaptive chosen-plaintext: like a chosen-plaintext attack, except the attacker can choose subsequent plaintexts based on information learned from previous encryptions. Similarly Adaptive chosen ciphertext attack.
- Related-key attackRelated-key attackIn cryptography, a related-key attack is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker...
: Like a chosen-plaintext attack, except the attacker can obtain ciphertexts encrypted under two different keys. The keys are unknown, but the relationship between them is known; for example, two keys that differ in the one bit.
These types of attack clearly differ in how plausible they would be to mount in practice. Although some are more likely than others, cryptographers will often take a conservative approach to security and assume the worst-case when designing algorithms, reasoning that if a scheme is secure even against unrealistic threats, then it should also resist real-world cryptanalysis as well.
The assumptions are often more realistic than they might seem upon first glance. For a known-plaintext attack, the cryptanalyst might well know or be able to guess at a likely part of the plaintext, such as an encrypted letter beginning with "Dear Sir", or a computer session starting with "LOGIN:". A chosen-plaintext attack is less likely, but it is sometimes plausible: for example, you could convince someone to forward a message you have given them, but in encrypted form. Related-key attacks are mostly theoretical, although they can be realistic in certain situations, for example, when constructing cryptographic hash function
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
s using a block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
.
Usefulness of attack results
The results of cryptanalysis can also vary in usefulness. For example, cryptographer Lars KnudsenLars Knudsen
Lars Ramkilde Knudsen is a Danish researcher in cryptography, particularly interested in the design and analysis of block ciphers, hash functions and message authentication codes .-Academic:...
(1998) classified various types of attack on block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
s according to the amount and quality of secret information that was discovered:
- Total break — the attacker deduces the secret keyKey (cryptography)In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
. - Global deduction — the attacker discovers a functionally equivalent algorithmAlgorithmIn mathematics and computer science, an algorithm is an effective method expressed as a finite list of well-defined instructions for calculating a function. Algorithms are used for calculation, data processing, and automated reasoning...
for encryption and decryption, but without learning the key. - Instance (local) deduction — the attacker discovers additional plaintexts (or ciphertexts) not previously known.
- Information deduction — the attacker gains some Shannon informationInformation entropyIn information theory, entropy is a measure of the uncertainty associated with a random variable. In this context, the term usually refers to the Shannon entropy, which quantifies the expected value of the information contained in a message, usually in units such as bits...
about plaintexts (or ciphertexts) not previously known. - Distinguishing algorithm — the attacker can distinguish the cipher from a random permutationPermutationIn mathematics, the notion of permutation is used with several slightly different meanings, all related to the act of permuting objects or values. Informally, a permutation of a set of objects is an arrangement of those objects into a particular order...
.
Similar considerations apply to attacks on other types of cryptographic algorithm.
Computational resources required
Attacks can also be characterised by the resources they require. Those resources include:- Time — the number of computation steps (like encryptions) which must be performed.
- Memory — the amount of storage required to perform the attack.
- Data — the quantity of plaintexts and ciphertexts required.
It's sometimes difficult to predict these quantities precisely, especially when the attack isn't practical to actually implement for testing. But academic cryptanalysts tend to provide at least the estimated order of magnitude of their attacks' difficulty, saying, for example, "SHA-1 collisions now 252"
Bruce Schneier
Bruce Schneier
Bruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
notes that even computationally impractical attacks can be considered breaks: "Breaking a cipher simply means finding a weakness in the cipher that can be exploited with a complexity less than brute force. Never mind that brute-force might require 2128 encryptions; an attack requiring 2110 encryptions would be considered a break...simply put, a break can just be a certificational weakness: evidence that the cipher does not perform as advertised."
Partial breaks
Academic attacks are often against weakened versions of a cryptosystem, such as a block cipher or hash function with some rounds removed. Many, but not all, attacks become exponentially more difficult to execute as rounds are added to a cryptosystem, so it's possible for the full cryptosystem to be strong even though reduced-round variants are weak. Nonetheless, partial breaks that come close to breaking the original cryptosystem may mean that a full break will follow; the successful attacks on DESDES
-Computing:* Data Encryption Standard* DirectShow Editing Services, an Application Programming Interface-Medical:* Diethylstilbestrol, a synthetic estrogen and the origin of the phrase "DES daughter"* DES gene, which encodes the Desmin protein...
, MD5
MD5
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
, and SHA-1 were all preceded by attacks on weakened versions.
Academic weakness versus practical weakness
In academic cryptography, a weakness or a break in a scheme is usually defined quite conservatively: it might require impractical amounts of time, memory, or known plaintexts. It also might require the attacker be able to do things many real-world attackers can't: for example, the attacker may need to choose particular plaintexts to be encrypted or even to ask for plaintexts to be encrypted using several keys related to the secret key. Furthermore, it might only reveal a small amount of information, enough to prove the cryptosystem imperfect but too little to be useful to real-world attackers. Finally, an attack might only apply to a weakened version of cryptographic tools, like a reduced-round block cipher, as a step towards breaking of the full system.Cryptanalysis of asymmetric cryptography
Asymmetric cryptography (or public key cryptography) is cryptography that relies on using two keys; one private, and one public. Such ciphers invariably rely on "hard" mathematical problemMathematical problem
A mathematical problem is a problem that is amenable to being represented, analyzed, and possibly solved, with the methods of mathematics. This can be a real-world problem, such as computing the orbits of the planets in the solar system, or a problem of a more abstract nature, such as Hilbert's...
s as the basis of their security, so an obvious point of attack is to develop methods for solving the problem. The security of two-key cryptography depends on mathematical questions in a way that single-key cryptography generally does not, and conversely links cryptanalysis to wider mathematical research in a new way.
Asymmetric schemes are designed around the (conjectured) difficulty of solving various mathematical problems. If an improved algorithm can be found to solve the problem, then the system is weakened. For example, the security of the Diffie-Hellman key exchange
Diffie-Hellman key exchange
Diffie–Hellman key exchange Synonyms of Diffie–Hellman key exchange include:*Diffie–Hellman key agreement*Diffie–Hellman key establishment*Diffie–Hellman key negotiation...
scheme depends on the difficulty of calculating the discrete logarithm
Discrete logarithm
In mathematics, specifically in abstract algebra and its applications, discrete logarithms are group-theoretic analogues of ordinary logarithms. In particular, an ordinary logarithm loga is a solution of the equation ax = b over the real or complex numbers...
. In 1983, Don Coppersmith
Don Coppersmith
Don Coppersmith is a cryptographer and mathematician. He was involved in the design of the Data Encryption Standard block cipher at IBM, particularly the design of the S-boxes, strengthening them against differential cryptanalysis...
found a faster way to find discrete logarithms (in certain groups), and thereby requiring cryptographers to use larger groups (or different types of groups). RSA's security depends (in part) upon the difficulty of integer factorization
Integer factorization
In number theory, integer factorization or prime factorization is the decomposition of a composite number into smaller non-trivial divisors, which when multiplied together equal the original integer....
— a breakthrough in factoring would impact the security of RSA.
In 1980, one could factor a difficult 50-digit number at an expense of 1012 elementary computer operations. By 1984 the state of the art in factoring algorithms had advanced to a point where a 75-digit number could be factored in 1012 operations. Advances in computing technology also meant that the operations could be performed much faster, too. Moore's law
Moore's Law
Moore's law describes a long-term trend in the history of computing hardware: the number of transistors that can be placed inexpensively on an integrated circuit doubles approximately every two years....
predicts that computer speeds will continue to increase. Factoring techniques may continue to do so as well, but will most likely depend on mathematical insight and creativity, neither of which has ever been successfully predictable. 150-digit numbers of the kind once used in RSA have been factored. The effort was greater than above, but was not unreasonable on fast modern computers. By the start of the 21st century, 150-digit numbers were no longer considered a large enough key size
Key size
In cryptography, key size or key length is the size measured in bits of the key used in a cryptographic algorithm . An algorithm's key length is distinct from its cryptographic security, which is a logarithmic measure of the fastest known computational attack on the algorithm, also measured in bits...
for RSA. Numbers with several hundred digits were still considered too hard to factor in 2005, though methods will probably continue to improve over time, requiring key size to keep pace or other methods such as elliptic curve cryptography
Elliptic curve cryptography
Elliptic curve cryptography is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. The use of elliptic curves in cryptography was suggested independently by Neal Koblitz and Victor S...
to be used.
Another distinguishing feature of asymmetric schemes is that, unlike attacks on symmetric cryptosystems, any cryptanalysis has the opportunity to make use of knowledge gained from the public key.
Quantum computing applications for cryptanalysis
Quantum computerQuantum computer
A quantum computer is a device for computation that makes direct use of quantum mechanical phenomena, such as superposition and entanglement, to perform operations on data. Quantum computers are different from traditional computers based on transistors...
s, which are still in the early phases of research, have potential use in cryptanalysis. For example, Shor's Algorithm
Shor's algorithm
Shor's algorithm, named after mathematician Peter Shor, is a quantum algorithm for integer factorization formulated in 1994...
could factor large numbers in polynomial time, in effect breaking some commonly used forms of public-key encryption.
By using Grover's algorithm
Grover's algorithm
Grover's algorithm is a quantum algorithm for searching an unsorted database with N entries in O time and using O storage space . It was invented by Lov Grover in 1996....
on a quantum computer, brute-force key search can be made quadratically faster. However, this could be countered by doubling the key length.
Methods of cryptanalysis
Classical cryptanalysis:- Frequency analysisFrequency analysisIn cryptanalysis, frequency analysis is the study of the frequency of letters or groups of letters in a ciphertext. The method is used as an aid to breaking classical ciphers....
- Index of coincidenceIndex of coincidenceIn cryptography, coincidence counting is the technique of putting two texts side-by-side and counting the number of times that identical letters appear in the same position in both texts...
- Kasiski examinationKasiski examinationIn cryptanalysis, Kasiski examination is a method of attacking polyalphabetic substitution ciphers, such as the Vigenère cipher...
Symmetric algorithms:
- Boomerang attackBoomerang attackIn cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David Wagner, who used it to break the COCONUT98 cipher....
- Brute force attackBrute force attackIn cryptography, a brute-force attack, or exhaustive key search, is a strategy that can, in theory, be used against any encrypted data. Such an attack might be utilized when it is not possible to take advantage of other weaknesses in an encryption system that would make the task easier...
- Davies' attackDavies' attackIn cryptography, is a dedicated statistical cryptanalysis method for attacking the Data Encryption Standard . The attack was originally created in 1987 by Donald Davies. In 1994, Eli Biham and Alex Biryukov made significant improvements to the technique. It is a known-plaintext attack based on the...
- Differential cryptanalysisDifferential cryptanalysisDifferential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash functions. In the broadest sense, it is the study of how differences in an input can affect the resultant difference at the output...
- Impossible differential cryptanalysisImpossible differential cryptanalysisIn cryptography, impossible differential cryptanalysis is a form of differential cryptanalysis for block ciphers. While ordinary differential cryptanalysis tracks differences that propagate through the cipher with greater than expected probability, impossible differential cryptanalysis exploits...
- Improbable differential cryptanalysis
- Integral cryptanalysisIntegral cryptanalysisIn cryptography, integral cryptanalysis is a cryptanalytic attack that is particularly applicable to block ciphers based on substitution-permutation networks. It was originally designed by Lars Knudsen as a dedicated attack against Square, so is commonly known as the Square attack. It was also...
- Linear cryptanalysisLinear cryptanalysisIn cryptography, linear cryptanalysis is a general form of cryptanalysis based on finding affine approximations to the action of a cipher. Attacks have been developed for block ciphers and stream ciphers...
- Meet-in-the-middle attackMeet-in-the-middle attackThe meet-in-the-middle attack is a cryptographic attack which, like the birthday attack, makes use of a space-time tradeoff. While the birthday attack attempts to find two values in the domain of a function that map to the same value in its range, the meet-in-the-middle attack attempts to find a...
- Mod-n cryptanalysis
- Related-key attackRelated-key attackIn cryptography, a related-key attack is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker...
- Sandwich attack
- Slide attackSlide attackThe slide attack is a form of cryptanalysis designed to deal with the prevailing idea that even weak ciphers can become very strong by increasing the number of rounds, which can ward off a differential attack. The slide attack works in such a way as to make the number of rounds in a cipher irrelevant...
- XSL attackXSL attackIn cryptography, the XSL attack is a method of cryptanalysis for block ciphers. The attack was first published in 2002 by researchers Nicolas Courtois and Josef Pieprzyk. It has caused some controversy as it was claimed to have the potential to break the Advanced Encryption Standard cipher—also...
Hash functions:
- Birthday attackBirthday attackA birthday attack is a type of cryptographic attack that exploits the mathematics behind the birthday problem in probability theory. This attack can be used to abuse communication between two or more parties...
- Rainbow tableRainbow tableA rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering the plaintext password, up to a certain length consisting of a limited set of characters. It is a form of time-memory tradeoff, using less...
Attack model
Attack model
Attack models or attack types specify how much information a cryptanalyst has access to when cracking an encrypted message...
s:
- Chosen-ciphertext attackChosen-ciphertext attackA chosen-ciphertext attack is an attack model for cryptanalysis in which the cryptanalyst gathers information, at least in part, by choosing a ciphertext and obtaining its decryption under an unknown key. In the attack, an adversary has a chance to enter one or more known ciphertexts into the...
- Chosen-plaintext attackChosen-plaintext attackA chosen-plaintext attack is an attack model for cryptanalysis which presumes that the attacker has the capability to choose arbitrary plaintexts to be encrypted and obtain the corresponding ciphertexts. The goal of the attack is to gain some further information which reduces the security of the...
- Ciphertext-only attackCiphertext-only attackIn cryptography, a ciphertext-only attack or known ciphertext attack is an attack model for cryptanalysis where the attacker is assumed to have access only to a set of ciphertexts....
- Known-plaintext attackKnown-plaintext attackThe known-plaintext attack is an attack model for cryptanalysis where the attacker has samples of both the plaintext , and its encrypted version . These can be used to reveal further secret information such as secret keys and code books...
Side channel attack
Side channel attack
In cryptography, a side channel attack is any attack based on information gained from the physical implementation of a cryptosystem, rather than brute force or theoretical weaknesses in the algorithms...
s:
- Power analysisPower analysisIn cryptography, power analysis is a form of side channel attack in which the attacker studies the power consumption of a cryptographic hardware device...
- Timing attackTiming attackIn cryptography, a timing attack is a side channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute cryptographic algorithms...
Network attacks:
- Man-in-the-middle attackMan-in-the-middle attackIn cryptography, the man-in-the-middle attack , bucket-brigade attack, or sometimes Janus attack, is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other...
- Replay attackReplay attackA replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and retransmits it, possibly as part of a masquerade attack by IP packet...
External attacks:
- Black-bag cryptanalysisBlack-bag cryptanalysisIn cryptography, black-bag cryptanalysis is a euphemism for the acquisition of cryptographic secrets via burglary, or the covert installation of keystroke logging or trojan horse software/hardware on target computers or ancillary devices...
- Rubber-hose cryptanalysisRubber-hose cryptanalysisIn cryptography, rubber-hose cryptanalysis is the extraction of cryptographic secrets from a person by coercion or torture, in contrast to a mathematical or technical cryptanalytic attack....
Related topics
- Information securityInformation securityInformation security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction....
, the overarching goal of most cryptography - Security vulnerability; vulnerabilities can include cryptographic or other flaws
- Security engineeringSecurity engineeringSecurity engineering is a specialized field of engineering that focuses on the security aspects in the design of systems that need to be able to deal robustly with possible sources of disruption, ranging from natural disasters to malicious acts...
, the design of applications and protocols - Information assuranceInformation AssuranceInformation assurance is the practice of managing risks related to the use, processing, storage, and transmission of information or data and the systems and processes used for those purposes...
, a term for information security often used in government - Economics of securityEconomics of securityThe economics of information security addresses the economic aspects of privacy and computer security. Economics of information security includes models of the strictly rational “homo economicus” as well as behavioral economics...
General
- Cryptanalysis of the EnigmaCryptanalysis of the EnigmaCryptanalysis of the Enigma enabled the western Allies in World War II to read substantial amounts of secret Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military intelligence which, along with that from other decrypted Axis radio...
- CryptographyCryptographyCryptography is the practice and study of techniques for secure communication in the presence of third parties...
- Cryptography portal
- DeciphermentDeciphermentDecipherment is the analysis of documents written in ancient languages, where the language is unknown, or knowledge of the language has been lost....
- Topics in cryptography
- National Cipher ChallengeNational Cipher ChallengeThe National Cipher Challenge is an annual cryptographic competition organised by the University of Southampton School of Mathematics. Competitors attempt to break cryptograms published on the competition website. In the 2007/08 challenge, 1301 teams participated...
- Zendian ProblemZendian ProblemThe Zendian Problem was an exercise in communication intelligence operations devised by Lambros D. Callimahos as part of an advanced course, CA-400, that Callimahos taught to National Security Agency cryptanalysts....
Historic cryptanalysts
- Conel Hugh O'Donel AlexanderConel Hugh O'Donel AlexanderConel Hugh O'Donel Alexander, CMG, CBE was an Irish-born British cryptanalyst, chess player, and chess writer. He worked on the German Enigma machine at Bletchley Park during World War II, and was later the head of the cryptanalysis division at GCHQ for over 20 years...
- Charles BabbageCharles BabbageCharles Babbage, FRS was an English mathematician, philosopher, inventor and mechanical engineer who originated the concept of a programmable computer...
- Lambros D. CallimahosLambros D. CallimahosLambros Demetrios Callimahos was a US Army cryptologist. Born in Alexandria of Greek parents, the family emigrated to the United States when he was four...
- Alastair DennistonAlastair DennistonCommander Alexander Guthrie Denniston CMG CBE RNVR was a British codebreaker in Room 40 and first head of the Government Code and Cypher School and field hockey player...
- Agnes Meyer DriscollAgnes Meyer DriscollAgnes Meyer Driscoll was, known as Miss Aggie or Madame X, an Americancryptanalyst during both World War I and World War II.-Early years:...
- Elizebeth FriedmanElizebeth FriedmanElizebeth Smith Friedman was a cryptanalyst and author, and a pioneer in U.S. cryptography. The special spelling of her name is attributed to her mother, who disliked the prospect of Elizebeth ever being called "Eliza." She has been dubbed "America's first female cryptanalyst".Although she is...
- William F. FriedmanWilliam F. FriedmanWilliam Frederick Friedman was a US Army cryptographer who ran the research division of the Army's Signals Intelligence Service in the 1930s, and parts of its follow-on services into the 1950s...
, the father of modern cryptology - Meredith GardnerMeredith GardnerMeredith Knox Gardner was an American linguist and codebreaker. Gardner worked in counter-intelligence, decoding Soviet intelligence traffic regarding espionage in the United States, in what came to be known as the Venona project.-Early life and career:Gardner was born in Okolona, Mississippi and...
- Friedrich KasiskiFriedrich KasiskiMajor Friedrich Wilhelm Kasiski was a Prussian infantry officer, cryptographer and archeologist. Kasiski was born in Schlochau, West Prussia .-Military service:...
- Al-KindiAl-Kindi' , known as "the Philosopher of the Arabs", was a Muslim Arab philosopher, mathematician, physician, and musician. Al-Kindi was the first of the Muslim peripatetic philosophers, and is unanimously hailed as the "father of Islamic or Arabic philosophy" for his synthesis, adaptation and promotion...
- Dilly KnoxDilly KnoxAlfred Dillwyn 'Dilly' Knox CMG was a classics scholar at King's College, Cambridge, and a British codebreaker...
- Solomon KullbackSolomon KullbackSolomon Kullback was an American cryptanalyst and mathematician, who was one of the first three employees hired by William F. Friedman at the US Army's Signal Intelligence Service in the 1930s, along with Frank Rowlett and Abraham Sinkov. He went on to a long and distinguished career at SIS and...
- Marian RejewskiMarian RejewskiMarian Adam Rejewski was a Polish mathematician and cryptologist who in 1932 solved the plugboard-equipped Enigma machine, the main cipher device used by Germany...
- Joseph RochefortJoseph RochefortJoseph John Rochefort was an American Naval officer and cryptanalyst. His contributions and those of his team were pivotal to victory in the Pacific War....
, whose contributions affected the outcome of the Battle of MidwayBattle of MidwayThe Battle of Midway is widely regarded as the most important naval battle of the Pacific Campaign of World War II. Between 4 and 7 June 1942, approximately one month after the Battle of the Coral Sea and six months after Japan's attack on Pearl Harbor, the United States Navy decisively defeated... - Frank RowlettFrank RowlettFrank Byron Rowlett was an American cryptologist.Rowlett was born in Rose Hill, Virginia and attended Emory & Henry College in Emory, Virginia, where he was a member of the Beta Lambda Zeta fraternity. In 1929 he received a bachelor's degree in mathematics and chemistry...
- Abraham SinkovAbraham SinkovDr. Abraham Sinkov was a US cryptanalyst.-Biography:Sinkov, the son of immigrants from Russia, was born in Philadelphia, but grew up in Brooklyn. After graduating from Boys High School—what today would be called a "magnet school" -- he took his B.S. in mathematics from City College of New York...
- Giovanni SoroGiovanni SoroGiovanni Soro was a Venetian professional code-cracker. He was more than likely the Renaissance's first outstanding cryptanalyst and the Western world's first great cryptanalyst. Soro is known as the father of modern cryptography.-Career:...
, the Renaissance's first outstanding cryptanalyst - John Tiltman
- Alan TuringAlan TuringAlan Mathison Turing, OBE, FRS , was an English mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, providing a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which played a...
- Herbert YardleyHerbert YardleyHerbert Osborne Yardley was an American cryptologist best known for his book The American Black Chamber . The title of the book refers to the Cipher Bureau, the cryptographic organization of which Yardley was the founder and head...
External links
- Basic Cryptanalysis (files contain 5 line header, that has to be removed first)
- Distributed Computing Projects
- Simon Singh's crypto corner
- The National Museum of Computing
- UltraAnvil tool for attacking simple substitution ciphers

