
Power analysis
Encyclopedia
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, power analysis is a form of side channel attack
Side channel attack
In cryptography, a side channel attack is any attack based on information gained from the physical implementation of a cryptosystem, rather than brute force or theoretical weaknesses in the algorithms...
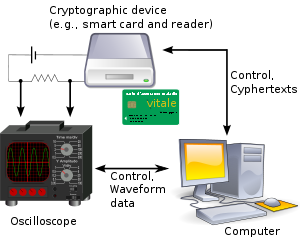
in which the attacker studies the power consumption of a cryptographic hardware device (such as a smart card
Smart card
A smart card, chip card, or integrated circuit card , is any pocket-sized card with embedded integrated circuits. A smart card or microprocessor cards contain volatile memory and microprocessor components. The card is made of plastic, generally polyvinyl chloride, but sometimes acrylonitrile...
, tamper-resistant
Tamper resistance
Tamper resistance is resistance to tampering by either the normal users of a product, package, or system or others with physical access to it. There are many reasons for employing tamper resistance....
"black box", or integrated circuit
Integrated circuit
An integrated circuit or monolithic integrated circuit is an electronic circuit manufactured by the patterned diffusion of trace elements into the surface of a thin substrate of semiconductor material...
). The attack can non-invasively extract cryptographic keys and other secret information from the device.
Simple power analysis (SPA) involves visually interpreting power traces, or graphs of electrical activity over time. Differential power analysis (DPA) is a more advanced form of power analysis which can allow an attacker to compute the intermediate values within cryptographic computations by statistically analyzing data collected from multiple cryptographic operations. SPA and DPA were introduced in the open cryptologic community in 1998 by Cryptography Research
Cryptography Research
Cryptography Research, Inc.. is a San Francisco based cryptography company specializing in applied cryptographic engineering, including technologies for building tamper-resistant semiconductors. It was purchased on June 6, 2011 by Rambus for more than $250M in cash and stock. The company licenses...
's Paul Kocher
Paul Kocher
Paul Carl Kocher is an American cryptographer and cryptography consultant, currently the president and chief scientist of Cryptography Research, Inc....
, Joshua Jaffe and Benjamin Jun.
Simple power analysis
Simple power analysis (SPA) is a side-channel attack which involves visual examination of graphs of the current used by a device over time. Variations in power consumption occur as the device performs different operations. For example, different instructions performed by a microprocessor will have differing power consumption profiles. As a result, in a power trace from a smart card performing a DESData Encryption Standard
The Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
encryption, the sixteen rounds can be seen clearly. Similarly, squaring and multiplication operations in RSA implementations can often be distinguished, enabling an adversary to compute the secret key. Even if the magnitude of the variations in power consumption are small, standard digital oscilloscopes can easily show the data-induced variations. Frequency filters and averaging functions (such as those built into oscilloscopes) are often used to filter out high-frequency components.
Differential power analysis
Differential power analysis (DPA) is a side-channel attack which involves statistically analyzing power consumption measurements from a cryptosystemCryptosystem
There are two different meanings of the word cryptosystem. One is used by the cryptographic community, while the other is the meaning understood by the public.- General meaning :...
. The attack exploits biases varying power consumption of microprocessors or other hardware while performing operations using secret keys. DPA attacks have signal processing and error correction properties which can extract secrets from measurements which contain too much noise to be analyzed using simple power analysis. Using DPA, an adversary can obtain secret keys by analyzing power consumption measurements from multiple cryptographic operations performed by a vulnerable smart card or other device.
High-order differential power analysis
High-Order Differential Power Analysis (HO-DPA) is an advanced form of DPA attack. HO-DPA enables multiple data sources and different time offsets to be incorporated in the analysis. HO-DPA is less widely practiced than SPA and DPA, as the analysis is complex and most vulnerable devices can be broken more easily with SPA or DPA.Power analysis and algorithmic security
Power analysis provides a way to "see inside" otherwise 'tamperproof' hardware. For example, DES's key scheduleKey schedule
[[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES [[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES [[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES ("[[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES ("...
involves rotating 28-bit key registers. Many implementations check the least significant bit to see if it is a 1. If so, the device shifts the register right and prepends the 1 at the left end. If the bit is a zero, the register is shifted right without prepending a 1. Power analysis can distinguish between these processes, enabling an adversary to determine the bits of the secret key.
Implementations of algorithms such as AES
Advanced Encryption Standard
Advanced Encryption Standard is a specification for the encryption of electronic data. It has been adopted by the U.S. government and is now used worldwide. It supersedes DES...
and triple DES
Triple DES
In cryptography, Triple DES is the common name for the Triple Data Encryption Algorithm block cipher, which applies the Data Encryption Standard cipher algorithm three times to each data block....
that are believed to be mathematically strong may be trivially breakable using power analysis attacks. As a result, power analysis attacks combine elements of algorithmic cryptanalysis and implementation security.
Standards and practical security concerns
For applications where devices may fall into the physical possession of an adversary, protection against power analysis is generally a major design requirement. For example, FIPS 140FIPS 140
The 140 series of Federal Information Processing Standards are U.S. government computer security standards that specify requirements for cryptography modules...
-3 requires power analysis countermeasures for cryptographic devices bought to the U.S. government. Power analysis have also been reportedly used against conditional access modules used in pay television systems.
The equipment necessary for performing power analysis attacks is widely available. For example, most digital storage oscilloscopes provide the necessary data collection functionality, and the data analysis is typically performed using conventional PCs. Commercial products designed for testing labs are also available.
Preventing simple and differential power analysis attacks
Power analysis attacks cannot generally be detected by a device, since the adversary's monitoring is normally passive. In addition, the attack is non-invasive. As a result, physical enclosures, auditing capabilities, and attack detectors are ineffective. Instead, cryptosystem engineers must ensure that devices' power variations do not reveal information usable by adversaries.Simple power analysis can easily distinguish the outcome of conditional branches in the execution of cryptographic software, since a device does different things (consuming different power) depending on whether the conditional branch is taken. For this reason, care should be taken to ensure there are no secret values which affect the conditional branches within cryptographic software implementations. Other sources of variation, such as microcode differences, branches introduced by compilers, and power consumption variations in multipliers, also commonly lead to SPA vulnerabilities.
Differential power analysis is more difficult to prevent, since even small biases in the power consumption can lead to exploitable weaknesses. Some countermeasure strategies involve algorithmic modifications such that the cryptographic operations occur on data that is related to the actual value by some mathematical relationship that survives the cryptographic operation. One approach involves blinding
Blinding (cryptography)
In cryptography, blinding is a technique by which an agent can provide a service to a client in an encoded form without knowing either the real input or the real output. Blinding techniques also have applications to preventing side-channel attacks on encryption devices.More precisely, Alice has...
parameters to randomize their value. Other countermeasure strategies to reduce the effectiveness of DPA attacks involve hardware modifications: varying the chip internal clock frequency has been considered to desynchronize electric signals, which lead in return to algorithmic enhancements of traditional DPA. ,
Patents
U.S. and international patents covering countermeasures to power analysis attacks are licensed by Cryptography ResearchCryptography Research
Cryptography Research, Inc.. is a San Francisco based cryptography company specializing in applied cryptographic engineering, including technologies for building tamper-resistant semiconductors. It was purchased on June 6, 2011 by Rambus for more than $250M in cash and stock. The company licenses...
.

