
Quantum cryptography
Encyclopedia
Quantum key distribution (QKD) uses quantum mechanics
to guarantee secure communication
. It enables two parties to produce a shared random
secret key
known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography
, as it is the most well known example of the group of quantum cryptographic tasks.
An important and unique property of quantum distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge
of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system
in general disturbs the system. A third party trying to eavesdrop
on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superposition
s or quantum entanglement
and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about), otherwise no secure key is possible and communication is aborted.
The security of quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional key distribution protocol which relies on the computational difficulty of certain mathematical functions
, and cannot provide any indication of eavesdropping or guarantee of key security.
Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad
, as it is provably secure when used with a secret, random key.
s, as opposed to classical communication's use of bit
s. Usually, photons are used for these quantum states. Quantum key distribution exploits certain properties of these quantum states to ensure its security. There are several different approaches to quantum key distribution, but they can be divided into two main categories depending on which property they exploit.
Prepare and measure protocols : In contrast to classical physics, the act of measurement is an integral part of quantum mechanics. In general, measuring an unknown quantum state changes that state in some way. This is known as quantum indeterminacy
, and underlies results such as the Heisenberg uncertainty principle, information-disturbance theorem and no cloning theorem
. This can be exploited in order to detect any eavesdropping on communication (which necessarily involves measurement) and, more importantly, to calculate the amount of information that has been intercepted.
Entanglement based protocols : The quantum states of two (or more) separate objects can become linked together in such a way that they must be described by a combined quantum state, not as individual objects. This is known as entanglement
and means that, for example, performing a measurement on one object affects the other. If an entangled pair of objects is shared between two parties, anyone intercepting either object alters the overall system, revealing the presence of the third party (and the amount of information they have gained).
These two approaches can each be further divided into three families of protocols; discrete variable, continuous variable and distributed phase reference coding. Discrete variable protocols were the first to be invented, and they remain the most widely implemented. The other two families are mainly concerned with overcoming practical limitations of experiments. The two protocols described below both use discrete variable coding.
after its inventors and year of publication, was originally described using photon polarization
states to transmit the information. However, any two pairs of conjugate
states can be used for the protocol, and many optical fibre based implementations described as BB84 use phase encoded states. The sender (traditionally referred to as Alice
) and the receiver (Bob) are connected by a quantum communication channel which allows quantum states to be transmitted. In the case of photons this channel is generally either an optical fibre or simply free space. In addition they communicate via a public classical channel, for example using broadcast radio or the internet. Neither of these channels need to be secure; the protocol is designed with the assumption that an eavesdropper (referred to as Eve) can interfere in any way with both.
The security of the protocol comes from encoding the information in non-orthogonal states
. Quantum indeterminacy
means that these states cannot in general be measured without disturbing the original state (see No cloning theorem
). BB84 uses two pairs of states, with each pair conjugate
to the other pair, and the two states within a pair orthogonal to each other. Pairs of orthogonal states are referred to as a basis
. The usual polarization state pairs used are either the rectilinear basis
of vertical (0°) and horizontal (90°), the diagonal basis
of 45° and 135° or the circular basis
of left- and right-handedness. Any two of these bases are conjugate to each other, and so any two can be used in the protocol. Below the rectilinear and diagonal bases are used.
The first step in BB84 is quantum transmission. Alice creates a random bit
(0 or 1) and then randomly selects one of her two bases (rectilinear or diagonal in this case) to transmit it in. She then prepares a photon polarization state depending both on the bit value and basis, as shown in the table to the left. So for example a 0 is encoded in the rectilinear basis (+) as a vertical polarization state, and a 1 is encoded in the diagonal basis (x) as a 135° state. Alice then transmits a single photon in the state specified to Bob, using the quantum channel. This process is then repeated from the random bit stage, with Alice recording the state, basis and time of each photon sent.
According to quantum mechanics (particularly quantum indeterminacy
), no possible measurement distinguishes between the 4 different polarization states, as they are not all orthogonal. The only possible measurement is between any two orthogonal states (a basis). So, for example, measuring in the rectilinear basis gives a result of horizontal or vertical. If the photon was created as horizontal or vertical (as a rectilinear eigenstate) then this measures the correct state, but if it was created as 45° or 135° (diagonal eigenstates) then the rectilinear measurement instead returns either horizontal or vertical at random. Furthermore, after this measurement the photon is polarized in the state it was measured in (horizontal or vertical), with all information about its initial polarization lost.
As Bob does not know the basis the photons were encoded in, all he can do is to select a basis at random to measure in, either rectilinear or diagonal. He does this for each photon he receives, recording the time, measurement basis used and measurement result. After Bob has measured all the photons, he communicates with Alice over the public classical channel. Alice broadcasts the basis each photon was sent in, and Bob the basis each was measured in. They both discard photon measurements (bits) where Bob used a different basis, which is half on average, leaving half the bits as a shared key.
To check for the presence of eavesdropping Alice and Bob now compare a certain subset of their remaining bit strings. If a third party (usually referred to as Eve, for 'eavesdropper') has gained any information about the photons' polarization, this introduces errors in Bobs' measurements. If more than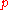 bits differ they abort the key and try again, possibly with a different quantum channel, as the security of the key cannot be guaranteed.
bits differ they abort the key and try again, possibly with a different quantum channel, as the security of the key cannot be guaranteed. 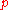 is chosen so that if the number of bits known to Eve is less than this, privacy amplification can be used to reduce Eve's knowledge of the key to an arbitrarily small amount, by reducing the length of the key.
is chosen so that if the number of bits known to Eve is less than this, privacy amplification can be used to reduce Eve's knowledge of the key to an arbitrarily small amount, by reducing the length of the key.
The scheme relies on two properties of entanglement. First, the entangled states are perfectly correlated in the sense that if Alice and Bob both measure whether their particles have vertical or horizontal polarizations, they always get the same answer with 100% probability. The same is true if they both measure any other pair of complementary (orthogonal) polarizations. However, the particular results are completely random; it is impossible for Alice to predict if she (and thus Bob) will get vertical polarization or horizontal polarization. Second, any attempt at eavesdropping by Eve destroys these correlations in a way that Alice and Bob can detect.
The original Ekert protocol consist of using three possible states and testing Bell inequality violation for detecting eavesdropping.
Information reconciliation is a form of error correction carried out between Alice and Bob's keys, in order to ensure both keys are identical. It is conducted over the public channel and as such it is vital to minimise the information sent about each key, as this can be read by Eve. A common protocol used for information reconciliation is the cascade protocol, proposed in 1994. This operates in several rounds, with both keys divided into blocks in each round and the parity of those blocks compared. If a difference in parity is found then a binary search is performed to find and correct the error. If an error is found in a block from a previous round that had correct parity then another error must be contained in that block; this error is found and corrected as before. This process is repeated recursively, which is the source of the cascade name. After all blocks have been compared, Alice and Bob both reorder their keys in the same random way, and a new round begins. At the end of multiple rounds Alice and Bob have identical keys with high probability, however Eve has additional information about the key from the parity information exchanged.
Privacy Amplification is a method for reducing (and effectively eliminating) Eve's partial information about Alice and Bob's key. This partial information could have been gained both by eavesdropping on the quantum channel during key transmission (thus introducing detectable errors), and on the public channel during information reconciliation (where it is assumed Eve gains all possible parity information). Privacy amplification uses Alice and Bob's key to produce a new, shorter key, in such a way that Eve has only negligible information about the new key. This can be done using a universal hash function
, chosen at random from a publicly known set of such functions, which takes as its input a binary string of length equal to the key and outputs a binary string of a chosen shorter length. The amount by which this new key is shortened is calculated, based on how much information Eve could have gained about the old key (which is known due to the errors this would introduce), in order to reduce the probability of Eve having any knowledge of the new key to a very low value.
and Toshiba
using the BB84
protocol with decoy pulses.
the longest distance over which quantum key distribution has been demonstrated using optic fibre is 148.7 km, achieved by Los Alamos National Laboratory
/NIST using the BB84 protocol. Significantly, this distance is long enough for almost all the spans found in today's fibre networks. The distance record for free space QKD is 144 km between two of the Canary Islands
, achieved by a European collaboration using entangled photons (the Ekert scheme) in 2006, and using BB84
enhanced with decoy states in 2007. The experiments suggest transmission to satellites is possible, due to the lower atmospheric density at higher altitudes. For example although the minimum distance from the International Space Station
to the ESA Space Debris Telescope
is about 400 km, the atmospheric thickness is about an order of magnitude less than in the European experiment, thus yielding less attenuation compared to this experiment.
(Geneva), MagiQ Technologies (New York), SmartQuantum (France) and Quintessence Labs (Australia). Several other companies also have active research programmes, including Toshiba
, HP
, IBM
, Mitsubishi
, NEC
and NTT
(See External links for direct research links).
Quantum encryption technology provided by the Swiss company Id Quantique
was used in the Swiss canton (state) of Geneva to transmit ballot results to the capitol in the national election occurring on October 21, 2007.
In 2004, the world's first bank transfer using quantum key distribution was carried in Vienna
, Austria
. An important cheque, which needed absolute security, was transmitted from the Mayor of the city to an Austrian bank.
, a 10-node quantum key distribution network, has been running since 2004 in Massachusetts, USA. It is being developed by BBN Technologies
, Harvard University
, Boston University
and QinetiQ
.
protected by quantum key distribution was implemented in October 2008, at a scientific conference in Vienna. The name of this network is SECOQC
(Secure Communication Based on Quantum Cryptography) and EU funded this project. The network used 200 km of standard fibre optic cable to interconnect six locations across Vienna and the town of St Poelten located 69 km to the west.
, Mitsubishi Electric
, NTT
and NICT from Japan, and participation from Europe by Toshiba
Research Europe Ltd. (UK), Id Quantique
(Switzerland) and All Vienna (Austria). "All Vienna" is represented by researchers from the Austrian Institute of Technology (AIT), the Institute for Quantum Optics and Quantum Information
(IQOQI) and the University of Vienna
.
The probability Eve chooses the incorrect basis is 50% (assuming Alice chooses randomly), and if Bob measures this intercepted photon in the basis Alice sent he gets a random result, i.e., an incorrect result with probability of 50%. The probability an intercepted photon generates an error in the key string is then 50% × 50% = 25%. If Alice and Bob publicly compare of their key bits (thus discarding them as key bits, as they are no longer secret) the probability they find disagreement and identify the presence of Eve is
of their key bits (thus discarding them as key bits, as they are no longer secret) the probability they find disagreement and identify the presence of Eve is

So to detect an eavesdropper with probability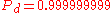 Alice and Bob need to compare
Alice and Bob need to compare  key bits.
key bits.
when used without authentication to the same extent as any classical protocol, since no known principle of quantum mechanics can distinguish friend from foe. As in the classical case, Alice and Bob cannot authenticate each other and establish a secure connection without some means of verifying each other's identities (such as an initial shared secret). If Alice and Bob have an initial shared secret then they can use an unconditionally secure authentication scheme (such as Carter-Wegman,) along with quantum key distribution to exponentially expand this key, using a small amount of the new key to authenticate the next session. Several methods to create this initial shared secret have been proposed, for example using a 3rd party or chaos theory. Nevertheless only "almost strongly universal" family of hash functions can be used for unconditionally secure authentication.
protocol Alice sends quantum states to Bob using single photons. In practice many implementations use laser pulses attenuated to a very low level to send the quantum states. These laser pulses contain a very small number of photons, for example 0.2 photons per pulse, which are distributed according to a Poissonian distribution. This means most pulses actually contain no photons (no pulse is sent), some pulses contain 1 photon (which is desired) and a few pulses contain 2 or more photons. If the pulse contains more than one photon, then Eve can split off the extra photons and transmit the remaining single photon to Bob. This is the basis of the photon number splitting attack, where Eve stores these extra photons in a quantum memory until Bob detects the remaining single photon and Alice reveals the encoding basis. Eve can then measure her photons in the correct basis and obtain information on the key without introducing detectable errors.
Even with the possibility of a PNS attack a secure key can still be generated, as shown in the GLLP security proof, however a much higher amount of privacy amplification is needed reducing the secure key rate significantly (with PNS the rate scales as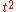 as compared to
as compared to  for a single photon sources, where
for a single photon sources, where  is the transmittance of the quantum channel).
is the transmittance of the quantum channel).
There are several solutions to this problem. The most obvious is to use a true single photon
source instead of an attenuated laser. While such sources are still at a developmental stage QKD has been carried out successfully with them. However as current sources operate at a low efficiency and frequency key rates and transmission distances are limited. Another solution is to modify the BB84 protocol, as is done for example in the SARG04
protocol, in which the secure key rate scales as . The most promising solution is the decoy state idea, in which Alice randomly sends some of her laser pulses with a lower average photon number. These decoy states can be used to detect a PNS attack, as Eve has no way to tell which pulses are signal and which decoy. Using this idea the secure key rate scales as
. The most promising solution is the decoy state idea, in which Alice randomly sends some of her laser pulses with a lower average photon number. These decoy states can be used to detect a PNS attack, as Eve has no way to tell which pulses are signal and which decoy. Using this idea the secure key rate scales as  , the same as for a single photon source. This idea has been implemented successfully first at University of Toronto, and in several follow-up QKD experiments, allowing for high key rates secure against all known attacks.
, the same as for a single photon source. This idea has been implemented successfully first at University of Toronto, and in several follow-up QKD experiments, allowing for high key rates secure against all known attacks.
. Another common class of attacks is the Trojan horse
attack which does not require physical access to the endpoints: rather than attempt to read Alice and Bob's single photons, Mallory sends a large pulse of light back to Alice in between transmitted photons. Alice's equipment reflects some of Mallory's light, revealing the state of Alice's polarizer. This attack is easy to avoid, for example using an optical isolator to prevent light from entering Alice's system, and all other hacking attacks can similarly be defeated by modifying the implementation. Apart from Trojan horse there are several other known attacks including faked-state attacks, phase remapping attacks and time-shift attacks. The time-shift attack has even been successfully demonstrated on a commercial quantum crypto-system. This is the first successful demonstration of quantum hacking against a non-homemade quantum key distribution system. Later on, the phase-remapping attack has also been demonstrated on a commercial QKD system (made and sold by the Swiss company Id Quantique
).. It is one of the first successful ‘intercept-and-resend’ attacks on top of a widely used QKD implementation in commercial QKD systems. This work has been widely reported by many medias. .
In a new (and what turned out to be actually, even an earlier) claim, it has now been experimentally shown that the detectors of two commercial devices could be fully remote-controlled using specially tailored bright illumination, which makes it possible to tracelessly acquire the full secret key. In a spree of publications thereafter, this collaboration between the Norwegian University of Science and Technology
in Norway and Max Planck Institute for the Science of Light in Germany, has now demonstrated several methods to successfully eavesdrop on commercial QKD systems based on Avalanche photodiodes (APDs) operating in gated mode.
, which would route communication via alternate links in case of disruption.
. Fortunately such measurements can be detected because they delay the arrival of the photons slightly. However, as weak measurement becomes perfected it will be necessary for the QKD protocols to check for these time delays.
, then at Columbia University in New York, who, in the early 1970s, introduced the concept of quantum conjugate coding. His seminal paper titled "Conjugate Coding" was rejected by IEEE Information Theory but was eventually published in 1983 in SIGACT News (15:1 pp. 78–88, 1983). In this paper he showed how to store or transmit two messages by encoding them in two “conjugate observables”, such as linear and circular polarization of light, so that either, but not both, of which may be received and decoded. He illustrated his idea with a design of unforgeable bank notes. A decade later, building upon this work, Charles H. Bennett
, of the IBM Thomas J. Watson Research Center
, and Gilles Brassard
, of the Université de Montréal, proposed a method for secure communication based on Wiesner’s “conjugate observables”. In 1990, independently and initially unaware of the earlier work, Artur Ekert
, then a Ph.D. student at Wolfson College, University of Oxford
, developed a different approach to quantum key distribution based on peculiar quantum correlations known as quantum entanglement.
Factors preventing wide adoption of quantum key distribution outside high security areas include the cost of equipment, and the lack of a demonstrated threat to existing key exchange protocols. However, with optic fibre networks already present in many countries the infrastructure is in place for a more widespread use.
Quantum mechanics
Quantum mechanics, also known as quantum physics or quantum theory, is a branch of physics providing a mathematical description of much of the dual particle-like and wave-like behavior and interactions of energy and matter. It departs from classical mechanics primarily at the atomic and subatomic...
to guarantee secure communication
Secure communication
When two entities are communicating and do not want a third party to listen in, they need to communicate in a way not susceptible to eavesdropping or interception. This is known as communicating in a secure manner or secure communication...
. It enables two parties to produce a shared random
Randomness
Randomness has somewhat differing meanings as used in various fields. It also has common meanings which are connected to the notion of predictability of events....
secret key
Key (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography
Quantum cryptography
Quantum key distribution uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages...
, as it is the most well known example of the group of quantum cryptographic tasks.
An important and unique property of quantum distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge
Information theory
Information theory is a branch of applied mathematics and electrical engineering involving the quantification of information. Information theory was developed by Claude E. Shannon to find fundamental limits on signal processing operations such as compressing data and on reliably storing and...
of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system
Physical system
In physics, the word system has a technical meaning, namely, it is the portion of the physical universe chosen for analysis. Everything outside the system is known as the environment, which in analysis is ignored except for its effects on the system. The cut between system and the world is a free...
in general disturbs the system. A third party trying to eavesdrop
Eavesdrop
To eavesdrop, used as a verb, refers to eavesdropping, the act of surreptitiously listening to a private conversation.As a noun, in architecture, it can refer to:...
on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superposition
Quantum superposition
Quantum superposition is a fundamental principle of quantum mechanics. It holds that a physical system exists in all its particular, theoretically possible states simultaneously; but, when measured, it gives a result corresponding to only one of the possible configurations.Mathematically, it...
s or quantum entanglement
Quantum entanglement
Quantum entanglement occurs when electrons, molecules even as large as "buckyballs", photons, etc., interact physically and then become separated; the type of interaction is such that each resulting member of a pair is properly described by the same quantum mechanical description , which is...
and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about), otherwise no secure key is possible and communication is aborted.
The security of quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional key distribution protocol which relies on the computational difficulty of certain mathematical functions
One-way function
In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here "easy" and "hard" are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems...
, and cannot provide any indication of eavesdropping or guarantee of key security.
Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad
One-time pad
In cryptography, the one-time pad is a type of encryption, which has been proven to be impossible to crack if used correctly. Each bit or character from the plaintext is encrypted by a modular addition with a bit or character from a secret random key of the same length as the plaintext, resulting...
, as it is provably secure when used with a secret, random key.
Quantum key exchange
Quantum communication involves encoding information in quantum states, or qubitQubit
In quantum computing, a qubit or quantum bit is a unit of quantum information—the quantum analogue of the classical bit—with additional dimensions associated to the quantum properties of a physical atom....
s, as opposed to classical communication's use of bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
s. Usually, photons are used for these quantum states. Quantum key distribution exploits certain properties of these quantum states to ensure its security. There are several different approaches to quantum key distribution, but they can be divided into two main categories depending on which property they exploit.
Prepare and measure protocols : In contrast to classical physics, the act of measurement is an integral part of quantum mechanics. In general, measuring an unknown quantum state changes that state in some way. This is known as quantum indeterminacy
Quantum indeterminacy
Quantum indeterminacy is the apparent necessary incompleteness in the description of a physical system, that has become one of the characteristics of the standard description of quantum physics...
, and underlies results such as the Heisenberg uncertainty principle, information-disturbance theorem and no cloning theorem
No cloning theorem
The no-cloning theorem is a result of quantum mechanics that forbids the creation of identical copies of an arbitrary unknown quantum state. It was stated by Wootters, Zurek, and Dieks in 1982, and has profound implications in quantum computing and related fields.The state of one system can be...
. This can be exploited in order to detect any eavesdropping on communication (which necessarily involves measurement) and, more importantly, to calculate the amount of information that has been intercepted.
Entanglement based protocols : The quantum states of two (or more) separate objects can become linked together in such a way that they must be described by a combined quantum state, not as individual objects. This is known as entanglement
Quantum entanglement
Quantum entanglement occurs when electrons, molecules even as large as "buckyballs", photons, etc., interact physically and then become separated; the type of interaction is such that each resulting member of a pair is properly described by the same quantum mechanical description , which is...
and means that, for example, performing a measurement on one object affects the other. If an entangled pair of objects is shared between two parties, anyone intercepting either object alters the overall system, revealing the presence of the third party (and the amount of information they have gained).
These two approaches can each be further divided into three families of protocols; discrete variable, continuous variable and distributed phase reference coding. Discrete variable protocols were the first to be invented, and they remain the most widely implemented. The other two families are mainly concerned with overcoming practical limitations of experiments. The two protocols described below both use discrete variable coding.
BB84 protocol: Charles H. Bennett and Gilles Brassard (1984)
This protocol, known as BB84BB84
BB84 is a quantum key distribution scheme developed by Charles Bennett and Gilles Brassard in 1984. It is the first quantum cryptography protocol. The protocol is provably secure, relying on the quantum property that information gain is only possible at the expense of disturbing the signal if the...
after its inventors and year of publication, was originally described using photon polarization
Photon polarization
Photon polarization is the quantum mechanical description of the classical polarized sinusoidal plane electromagnetic wave. Individual photons are completely polarized...
states to transmit the information. However, any two pairs of conjugate
Conjugate variables
Conjugate variables are pairs of variables mathematically defined in such a way that they become Fourier transform duals of one-another, or more generally are related through Pontryagin duality. The duality relations lead naturally to an uncertainty in physics called the Heisenberg uncertainty...
states can be used for the protocol, and many optical fibre based implementations described as BB84 use phase encoded states. The sender (traditionally referred to as Alice
Alice and Bob
The names Alice and Bob are commonly used placeholder names for archetypal characters in fields such as cryptography and physics. The names are used for convenience; for example, "Alice sends a message to Bob encrypted with his public key" is easier to follow than "Party A sends a message to Party...
) and the receiver (Bob) are connected by a quantum communication channel which allows quantum states to be transmitted. In the case of photons this channel is generally either an optical fibre or simply free space. In addition they communicate via a public classical channel, for example using broadcast radio or the internet. Neither of these channels need to be secure; the protocol is designed with the assumption that an eavesdropper (referred to as Eve) can interfere in any way with both.
The security of the protocol comes from encoding the information in non-orthogonal states
Orthogonality
Orthogonality occurs when two things can vary independently, they are uncorrelated, or they are perpendicular.-Mathematics:In mathematics, two vectors are orthogonal if they are perpendicular, i.e., they form a right angle...
. Quantum indeterminacy
Quantum indeterminacy
Quantum indeterminacy is the apparent necessary incompleteness in the description of a physical system, that has become one of the characteristics of the standard description of quantum physics...
means that these states cannot in general be measured without disturbing the original state (see No cloning theorem
No cloning theorem
The no-cloning theorem is a result of quantum mechanics that forbids the creation of identical copies of an arbitrary unknown quantum state. It was stated by Wootters, Zurek, and Dieks in 1982, and has profound implications in quantum computing and related fields.The state of one system can be...
). BB84 uses two pairs of states, with each pair conjugate
Conjugate variables
Conjugate variables are pairs of variables mathematically defined in such a way that they become Fourier transform duals of one-another, or more generally are related through Pontryagin duality. The duality relations lead naturally to an uncertainty in physics called the Heisenberg uncertainty...
to the other pair, and the two states within a pair orthogonal to each other. Pairs of orthogonal states are referred to as a basis
Basis (linear algebra)
In linear algebra, a basis is a set of linearly independent vectors that, in a linear combination, can represent every vector in a given vector space or free module, or, more simply put, which define a "coordinate system"...
. The usual polarization state pairs used are either the rectilinear basis
Linear polarization
In electrodynamics, linear polarization or plane polarization of electromagnetic radiation is a confinement of the electric field vector or magnetic field vector to a given plane along the direction of propagation...
of vertical (0°) and horizontal (90°), the diagonal basis
Linear polarization
In electrodynamics, linear polarization or plane polarization of electromagnetic radiation is a confinement of the electric field vector or magnetic field vector to a given plane along the direction of propagation...
of 45° and 135° or the circular basis
Circular polarization
In electrodynamics, circular polarization of an electromagnetic wave is a polarization in which the electric field of the passing wave does not change strength but only changes direction in a rotary type manner....
of left- and right-handedness. Any two of these bases are conjugate to each other, and so any two can be used in the protocol. Below the rectilinear and diagonal bases are used.
| Basis | 0 | 1 |
|---|---|---|
 |
 |
 |
 |
 |
 |
The first step in BB84 is quantum transmission. Alice creates a random bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
(0 or 1) and then randomly selects one of her two bases (rectilinear or diagonal in this case) to transmit it in. She then prepares a photon polarization state depending both on the bit value and basis, as shown in the table to the left. So for example a 0 is encoded in the rectilinear basis (+) as a vertical polarization state, and a 1 is encoded in the diagonal basis (x) as a 135° state. Alice then transmits a single photon in the state specified to Bob, using the quantum channel. This process is then repeated from the random bit stage, with Alice recording the state, basis and time of each photon sent.
According to quantum mechanics (particularly quantum indeterminacy
Quantum indeterminacy
Quantum indeterminacy is the apparent necessary incompleteness in the description of a physical system, that has become one of the characteristics of the standard description of quantum physics...
), no possible measurement distinguishes between the 4 different polarization states, as they are not all orthogonal. The only possible measurement is between any two orthogonal states (a basis). So, for example, measuring in the rectilinear basis gives a result of horizontal or vertical. If the photon was created as horizontal or vertical (as a rectilinear eigenstate) then this measures the correct state, but if it was created as 45° or 135° (diagonal eigenstates) then the rectilinear measurement instead returns either horizontal or vertical at random. Furthermore, after this measurement the photon is polarized in the state it was measured in (horizontal or vertical), with all information about its initial polarization lost.
As Bob does not know the basis the photons were encoded in, all he can do is to select a basis at random to measure in, either rectilinear or diagonal. He does this for each photon he receives, recording the time, measurement basis used and measurement result. After Bob has measured all the photons, he communicates with Alice over the public classical channel. Alice broadcasts the basis each photon was sent in, and Bob the basis each was measured in. They both discard photon measurements (bits) where Bob used a different basis, which is half on average, leaving half the bits as a shared key.
| Alice's random bit | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 1 |
|---|---|---|---|---|---|---|---|---|
| Alice's random sending basis |  |
 |
 |
 |
 |
 |
 |
 |
| Photon polarization Alice sends |  |
 |
 |
 |
 |
 |
 |
 |
| Bob's random measuring basis |  |
 |
 |
 |
 |
 |
 |
 |
| Photon polarization Bob measures | 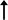 |
 |
 |
 |
 |
 |
 |
 |
| PUBLIC DISCUSSION OF BASIS | ||||||||
| Shared secret key | 0 | 1 | 0 | 1 | ||||
To check for the presence of eavesdropping Alice and Bob now compare a certain subset of their remaining bit strings. If a third party (usually referred to as Eve, for 'eavesdropper') has gained any information about the photons' polarization, this introduces errors in Bobs' measurements. If more than
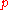 bits differ they abort the key and try again, possibly with a different quantum channel, as the security of the key cannot be guaranteed.
bits differ they abort the key and try again, possibly with a different quantum channel, as the security of the key cannot be guaranteed. 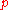 is chosen so that if the number of bits known to Eve is less than this, privacy amplification can be used to reduce Eve's knowledge of the key to an arbitrarily small amount, by reducing the length of the key.
is chosen so that if the number of bits known to Eve is less than this, privacy amplification can be used to reduce Eve's knowledge of the key to an arbitrarily small amount, by reducing the length of the key.E91 protocol: Artur Ekert (1991)
The Ekert scheme uses entangled pairs of photons. These can be created by Alice, by Bob, or by some source separate from both of them, including eavesdropper Eve. The photons are distributed so that Alice and Bob each end up with one photon from each pair.The scheme relies on two properties of entanglement. First, the entangled states are perfectly correlated in the sense that if Alice and Bob both measure whether their particles have vertical or horizontal polarizations, they always get the same answer with 100% probability. The same is true if they both measure any other pair of complementary (orthogonal) polarizations. However, the particular results are completely random; it is impossible for Alice to predict if she (and thus Bob) will get vertical polarization or horizontal polarization. Second, any attempt at eavesdropping by Eve destroys these correlations in a way that Alice and Bob can detect.
The original Ekert protocol consist of using three possible states and testing Bell inequality violation for detecting eavesdropping.
Privacy amplification and information reconciliation
The quantum key distribution protocols described above provide Alice and Bob with nearly identical shared keys, and also with an estimate of the discrepancy between the keys. These differences can be caused by eavesdropping, but also by imperfections in the transmission line and detectors. As it is impossible to distinguish between these two types of errors, guaranteed security requires the assumption that all errors are due to eavesdropping. Provided the error rate between the keys is lower than a certain threshold (20% as of April 2007), two steps can be performed to first remove the erroneous bits and then reduce Eve's knowledge of the key to an arbitrary small value. These two steps are known as information reconciliation and privacy amplification respectively, and were first described in 1992.Information reconciliation is a form of error correction carried out between Alice and Bob's keys, in order to ensure both keys are identical. It is conducted over the public channel and as such it is vital to minimise the information sent about each key, as this can be read by Eve. A common protocol used for information reconciliation is the cascade protocol, proposed in 1994. This operates in several rounds, with both keys divided into blocks in each round and the parity of those blocks compared. If a difference in parity is found then a binary search is performed to find and correct the error. If an error is found in a block from a previous round that had correct parity then another error must be contained in that block; this error is found and corrected as before. This process is repeated recursively, which is the source of the cascade name. After all blocks have been compared, Alice and Bob both reorder their keys in the same random way, and a new round begins. At the end of multiple rounds Alice and Bob have identical keys with high probability, however Eve has additional information about the key from the parity information exchanged.
Privacy Amplification is a method for reducing (and effectively eliminating) Eve's partial information about Alice and Bob's key. This partial information could have been gained both by eavesdropping on the quantum channel during key transmission (thus introducing detectable errors), and on the public channel during information reconciliation (where it is assumed Eve gains all possible parity information). Privacy amplification uses Alice and Bob's key to produce a new, shorter key, in such a way that Eve has only negligible information about the new key. This can be done using a universal hash function
Universal hashing
Using universal hashing refers to selecting a hash function at random from a family of hash functions with a certain mathematical property . This guarantees a low number of collisions in expectation, even if the data is chosen by an adversary...
, chosen at random from a publicly known set of such functions, which takes as its input a binary string of length equal to the key and outputs a binary string of a chosen shorter length. The amount by which this new key is shortened is calculated, based on how much information Eve could have gained about the old key (which is known due to the errors this would introduce), in order to reduce the probability of Eve having any knowledge of the new key to a very low value.
Experimental
The highest bit rate system currently demonstrated exchanges secure keys at 1 Mbit/s (over 20 km of optical fibre) and 10 kbit/s (over 100 km of fibre), achieved by a collaboration between the University of CambridgeUniversity of Cambridge
The University of Cambridge is a public research university located in Cambridge, United Kingdom. It is the second-oldest university in both the United Kingdom and the English-speaking world , and the seventh-oldest globally...
and Toshiba
Toshiba
is a multinational electronics and electrical equipment corporation headquartered in Tokyo, Japan. It is a diversified manufacturer and marketer of electrical products, spanning information & communications equipment and systems, Internet-based solutions and services, electronic components and...
using the BB84
BB84
BB84 is a quantum key distribution scheme developed by Charles Bennett and Gilles Brassard in 1984. It is the first quantum cryptography protocol. The protocol is provably secure, relying on the quantum property that information gain is only possible at the expense of disturbing the signal if the...
protocol with decoy pulses.
the longest distance over which quantum key distribution has been demonstrated using optic fibre is 148.7 km, achieved by Los Alamos National Laboratory
Los Alamos National Laboratory
Los Alamos National Laboratory is a United States Department of Energy national laboratory, managed and operated by Los Alamos National Security , located in Los Alamos, New Mexico...
/NIST using the BB84 protocol. Significantly, this distance is long enough for almost all the spans found in today's fibre networks. The distance record for free space QKD is 144 km between two of the Canary Islands
Canary Islands
The Canary Islands , also known as the Canaries , is a Spanish archipelago located just off the northwest coast of mainland Africa, 100 km west of the border between Morocco and the Western Sahara. The Canaries are a Spanish autonomous community and an outermost region of the European Union...
, achieved by a European collaboration using entangled photons (the Ekert scheme) in 2006, and using BB84
BB84
BB84 is a quantum key distribution scheme developed by Charles Bennett and Gilles Brassard in 1984. It is the first quantum cryptography protocol. The protocol is provably secure, relying on the quantum property that information gain is only possible at the expense of disturbing the signal if the...
enhanced with decoy states in 2007. The experiments suggest transmission to satellites is possible, due to the lower atmospheric density at higher altitudes. For example although the minimum distance from the International Space Station
International Space Station
The International Space Station is a habitable, artificial satellite in low Earth orbit. The ISS follows the Salyut, Almaz, Cosmos, Skylab, and Mir space stations, as the 11th space station launched, not including the Genesis I and II prototypes...
to the ESA Space Debris Telescope
ESA Space Debris Telescope
The ESA Space Debris Telescope is located at the Teide Observatory on the island of Tenerife, Spain. The telescope is ESA's Optical Ground Station forming a part of the Artemis experiment...
is about 400 km, the atmospheric thickness is about an order of magnitude less than in the European experiment, thus yielding less attenuation compared to this experiment.
Commercial
There are currently four companies offering commercial quantum key distribution systems; id QuantiqueId Quantique
id Quantique is a small company located in Geneva, Switzerland. It sells quantum key distribution systems, single photon counters, and physical random number generators...
(Geneva), MagiQ Technologies (New York), SmartQuantum (France) and Quintessence Labs (Australia). Several other companies also have active research programmes, including Toshiba
Toshiba
is a multinational electronics and electrical equipment corporation headquartered in Tokyo, Japan. It is a diversified manufacturer and marketer of electrical products, spanning information & communications equipment and systems, Internet-based solutions and services, electronic components and...
, HP
Hewlett-Packard
Hewlett-Packard Company or HP is an American multinational information technology corporation headquartered in Palo Alto, California, USA that provides products, technologies, softwares, solutions and services to consumers, small- and medium-sized businesses and large enterprises, including...
, IBM
IBM
International Business Machines Corporation or IBM is an American multinational technology and consulting corporation headquartered in Armonk, New York, United States. IBM manufactures and sells computer hardware and software, and it offers infrastructure, hosting and consulting services in areas...
, Mitsubishi
Mitsubishi
The Mitsubishi Group , Mitsubishi Group of Companies, or Mitsubishi Companies is a Japanese multinational conglomerate company that consists of a range of autonomous businesses which share the Mitsubishi brand, trademark and legacy...
, NEC
NEC
, a Japanese multinational IT company, has its headquarters in Minato, Tokyo, Japan. NEC, part of the Sumitomo Group, provides information technology and network solutions to business enterprises, communications services providers and government....
and NTT
Nippon Telegraph and Telephone
, commonly known as NTT, is a Japanese telecommunications company headquartered in Tokyo, Japan. Ranked the 31st in Fortune Global 500, NTT is the largest telecommunications company in Asia, and the second-largest in the world in terms of revenue....
(See External links for direct research links).
Quantum encryption technology provided by the Swiss company Id Quantique
Id Quantique
id Quantique is a small company located in Geneva, Switzerland. It sells quantum key distribution systems, single photon counters, and physical random number generators...
was used in the Swiss canton (state) of Geneva to transmit ballot results to the capitol in the national election occurring on October 21, 2007.
In 2004, the world's first bank transfer using quantum key distribution was carried in Vienna
Vienna
Vienna is the capital and largest city of the Republic of Austria and one of the nine states of Austria. Vienna is Austria's primary city, with a population of about 1.723 million , and is by far the largest city in Austria, as well as its cultural, economic, and political centre...
, Austria
Austria
Austria , officially the Republic of Austria , is a landlocked country of roughly 8.4 million people in Central Europe. It is bordered by the Czech Republic and Germany to the north, Slovakia and Hungary to the east, Slovenia and Italy to the south, and Switzerland and Liechtenstein to the...
. An important cheque, which needed absolute security, was transmitted from the Mayor of the city to an Austrian bank.
DARPA
The DARPA Quantum networkQuantum network
Quantum networks descend from the study of Quantum cryptography. The idea of a quantum network emerged after successful experiments on quantum teleportation...
, a 10-node quantum key distribution network, has been running since 2004 in Massachusetts, USA. It is being developed by BBN Technologies
BBN Technologies
BBN Technologies is a high-technology company which provides research and development services. BBN is based next to Fresh Pond in Cambridge, Massachusetts, USA...
, Harvard University
Harvard University
Harvard University is a private Ivy League university located in Cambridge, Massachusetts, United States, established in 1636 by the Massachusetts legislature. Harvard is the oldest institution of higher learning in the United States and the first corporation chartered in the country...
, Boston University
Boston University
Boston University is a private research university located in Boston, Massachusetts. With more than 4,000 faculty members and more than 31,000 students, Boston University is one of the largest private universities in the United States and one of Boston's largest employers...
and QinetiQ
QinetiQ
Qinetiq is a British global defence technology company, formed from the greater part of the former UK government agency, Defence Evaluation and Research Agency , when it was split up in June 2001...
.
SECOQC
The world's first computer networkComputer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
protected by quantum key distribution was implemented in October 2008, at a scientific conference in Vienna. The name of this network is SECOQC
Secure Communication based on Quantum Cryptography
Secure Communication based on Quantum Cryptography is a project that aims to develop quantum cryptography . The European Union decided in 2004 to invest 11 million EUR in the project as a way of circumventing espionage attempts by ECHELON...
(Secure Communication Based on Quantum Cryptography) and EU funded this project. The network used 200 km of standard fibre optic cable to interconnect six locations across Vienna and the town of St Poelten located 69 km to the west.
Tokyo QKD Network
The Tokyo QKD Network was inaugurated on the first day of the UQCC2010 conference. The network involves an international collaboration between 7 partners; NECNEC
, a Japanese multinational IT company, has its headquarters in Minato, Tokyo, Japan. NEC, part of the Sumitomo Group, provides information technology and network solutions to business enterprises, communications services providers and government....
, Mitsubishi Electric
Mitsubishi Electric
is a multinational electronics and information technology company headquartered in Tokyo, Japan. It is one of the core companies of the Mitsubishi Group....
, NTT
Nippon Telegraph and Telephone
, commonly known as NTT, is a Japanese telecommunications company headquartered in Tokyo, Japan. Ranked the 31st in Fortune Global 500, NTT is the largest telecommunications company in Asia, and the second-largest in the world in terms of revenue....
and NICT from Japan, and participation from Europe by Toshiba
Toshiba
is a multinational electronics and electrical equipment corporation headquartered in Tokyo, Japan. It is a diversified manufacturer and marketer of electrical products, spanning information & communications equipment and systems, Internet-based solutions and services, electronic components and...
Research Europe Ltd. (UK), Id Quantique
Id Quantique
id Quantique is a small company located in Geneva, Switzerland. It sells quantum key distribution systems, single photon counters, and physical random number generators...
(Switzerland) and All Vienna (Austria). "All Vienna" is represented by researchers from the Austrian Institute of Technology (AIT), the Institute for Quantum Optics and Quantum Information
Institute for Quantum Optics and Quantum Information
The Institute for Quantum Optics and Quantum Information is an child institute of the Austrian Academy of Sciences and was founded in November 2003...
(IQOQI) and the University of Vienna
University of Vienna
The University of Vienna is a public university located in Vienna, Austria. It was founded by Duke Rudolph IV in 1365 and is the oldest university in the German-speaking world...
.
Example: Intercept and resend
The simplest type of possible attack is the intercept-resend attack, where Eve measures the quantum states (photons) sent by Alice and then sends replacement states to Bob, prepared in the state she measures. In the BB84 protocol, this produces errors in the key Alice and Bob share. As Eve has no knowledge of the basis a state sent by Alice is encoded in, she can only guess which basis to measure in, in the same way as Bob. If she chooses correctly, she measures the correct photon polarization state as sent by Alice, and resends the correct state to Bob. However, if she chooses incorrectly, the state she measures is random, and the state sent to Bob cannot be the same as the state sent by Alice. If Bob then measures this state in the same basis Alice sent, he too gets a random result—as Eve has sent him a state in the opposite basis— with a 50% chance of an erroneous result (instead of the correct result he would get without the presence of Eve). The table below shows an example of this type of attack.| Alice's random bit | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 1 |
|---|---|---|---|---|---|---|---|---|
| Alice's random sending basis |  |
 |
 |
 |
 |
 |
 |
 |
| Photon polarization Alice sends | 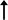 |
 |
 |
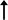 |
 |
 |
 |
 |
| Eve's random measuring basis |  |
 |
 |
 |
 |
 |
 |
 |
| Polarization Eve measures and sends | 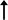 |
 |
 |
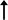 |
 |
 |
 |
 |
| Bob's random measuring basis |  |
 |
 |
 |
 |
 |
 |
 |
| Photon polarization Bob measures | 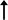 |
 |
 |
 |
 |
 |
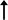 |
 |
| PUBLIC DISCUSSION OF BASIS | ||||||||
| Shared secret key | 0 | 0 | 0 | 1 | ||||
| Errors in key | ||||||||
The probability Eve chooses the incorrect basis is 50% (assuming Alice chooses randomly), and if Bob measures this intercepted photon in the basis Alice sent he gets a random result, i.e., an incorrect result with probability of 50%. The probability an intercepted photon generates an error in the key string is then 50% × 50% = 25%. If Alice and Bob publicly compare
 of their key bits (thus discarding them as key bits, as they are no longer secret) the probability they find disagreement and identify the presence of Eve is
of their key bits (thus discarding them as key bits, as they are no longer secret) the probability they find disagreement and identify the presence of Eve is
So to detect an eavesdropper with probability
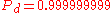 Alice and Bob need to compare
Alice and Bob need to compare  key bits.
key bits.Security Proofs
The above is just a simple example of an attack. If Eve is assumed to have unlimited resources, for example classical and quantum computing power, there are many more attacks possible. BB84 has been proven secure against any attacks allowed by quantum mechanics, both for sending information using an ideal photon source which only ever emits a single photon at a time, and also using practical photon sources which sometimes emit multiphoton pulses. These proofs are unconditionally secure in the sense that no conditions are imposed on the resources available to the Eavesdropper, however there are other conditions required:- Eve cannot access Alice and Bob's encoding and decoding devices.
- The random number generators used by Alice and Bob must be trusted and truly random (for example a Quantum random number generatorHardware random number generatorIn computing, a hardware random number generator is an apparatus that generates random numbers from a physical process. Such devices are often based on microscopic phenomena that generate a low-level, statistically random "noise" signal, such as thermal noise or the photoelectric effect or other...
). - The classical communication channel must be authenticated using an unconditionally secure authentication scheme.
- The message must be sent encrypted by correctly used one-time padOne-time padIn cryptography, the one-time pad is a type of encryption, which has been proven to be impossible to crack if used correctly. Each bit or character from the plaintext is encrypted by a modular addition with a bit or character from a secret random key of the same length as the plaintext, resulting...
(unconditionally secure encryption) scheme.
Man-in-the-middle attack
Quantum key distribution is vulnerable to a man-in-the-middle attackMan-in-the-middle attack
In cryptography, the man-in-the-middle attack , bucket-brigade attack, or sometimes Janus attack, is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other...
when used without authentication to the same extent as any classical protocol, since no known principle of quantum mechanics can distinguish friend from foe. As in the classical case, Alice and Bob cannot authenticate each other and establish a secure connection without some means of verifying each other's identities (such as an initial shared secret). If Alice and Bob have an initial shared secret then they can use an unconditionally secure authentication scheme (such as Carter-Wegman,) along with quantum key distribution to exponentially expand this key, using a small amount of the new key to authenticate the next session. Several methods to create this initial shared secret have been proposed, for example using a 3rd party or chaos theory. Nevertheless only "almost strongly universal" family of hash functions can be used for unconditionally secure authentication.
Photon number splitting attack
In the BB84BB84
BB84 is a quantum key distribution scheme developed by Charles Bennett and Gilles Brassard in 1984. It is the first quantum cryptography protocol. The protocol is provably secure, relying on the quantum property that information gain is only possible at the expense of disturbing the signal if the...
protocol Alice sends quantum states to Bob using single photons. In practice many implementations use laser pulses attenuated to a very low level to send the quantum states. These laser pulses contain a very small number of photons, for example 0.2 photons per pulse, which are distributed according to a Poissonian distribution. This means most pulses actually contain no photons (no pulse is sent), some pulses contain 1 photon (which is desired) and a few pulses contain 2 or more photons. If the pulse contains more than one photon, then Eve can split off the extra photons and transmit the remaining single photon to Bob. This is the basis of the photon number splitting attack, where Eve stores these extra photons in a quantum memory until Bob detects the remaining single photon and Alice reveals the encoding basis. Eve can then measure her photons in the correct basis and obtain information on the key without introducing detectable errors.
Even with the possibility of a PNS attack a secure key can still be generated, as shown in the GLLP security proof, however a much higher amount of privacy amplification is needed reducing the secure key rate significantly (with PNS the rate scales as
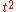 as compared to
as compared to  for a single photon sources, where
for a single photon sources, where  is the transmittance of the quantum channel).
is the transmittance of the quantum channel).There are several solutions to this problem. The most obvious is to use a true single photon
source instead of an attenuated laser. While such sources are still at a developmental stage QKD has been carried out successfully with them. However as current sources operate at a low efficiency and frequency key rates and transmission distances are limited. Another solution is to modify the BB84 protocol, as is done for example in the SARG04
SARG04
SARG04 is a quantum cryptography protocol derived from the first protocol of that kind, BB84.-Origin:Researchers built SARG04 when they noticed that by using the four states of BB84 with a different information encoding they could develop a new protocol which would be more robust when attenuated...
protocol, in which the secure key rate scales as
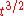 . The most promising solution is the decoy state idea, in which Alice randomly sends some of her laser pulses with a lower average photon number. These decoy states can be used to detect a PNS attack, as Eve has no way to tell which pulses are signal and which decoy. Using this idea the secure key rate scales as
. The most promising solution is the decoy state idea, in which Alice randomly sends some of her laser pulses with a lower average photon number. These decoy states can be used to detect a PNS attack, as Eve has no way to tell which pulses are signal and which decoy. Using this idea the secure key rate scales as  , the same as for a single photon source. This idea has been implemented successfully first at University of Toronto, and in several follow-up QKD experiments, allowing for high key rates secure against all known attacks.
, the same as for a single photon source. This idea has been implemented successfully first at University of Toronto, and in several follow-up QKD experiments, allowing for high key rates secure against all known attacks.Hacking attacks
Hacking attacks target imperfections in the implementation of the protocol or deficiencies in the components of the physical device. If the equipment used in quantum key distribution can be tampered with, it could be made to generate keys that were not secure using a random number generator attackRandom number generator attack
The security of cryptographic systems depends on some secret data that is known to authorized persons but unknown and unpredictable to others. To achieve this unpredictability, some randomization is typically employed...
. Another common class of attacks is the Trojan horse
Trojan Horse
The Trojan Horse is a tale from the Trojan War about the stratagem that allowed the Greeks finally to enter the city of Troy and end the conflict. In the canonical version, after a fruitless 10-year siege, the Greeks constructed a huge wooden horse, and hid a select force of men inside...
attack which does not require physical access to the endpoints: rather than attempt to read Alice and Bob's single photons, Mallory sends a large pulse of light back to Alice in between transmitted photons. Alice's equipment reflects some of Mallory's light, revealing the state of Alice's polarizer. This attack is easy to avoid, for example using an optical isolator to prevent light from entering Alice's system, and all other hacking attacks can similarly be defeated by modifying the implementation. Apart from Trojan horse there are several other known attacks including faked-state attacks, phase remapping attacks and time-shift attacks. The time-shift attack has even been successfully demonstrated on a commercial quantum crypto-system. This is the first successful demonstration of quantum hacking against a non-homemade quantum key distribution system. Later on, the phase-remapping attack has also been demonstrated on a commercial QKD system (made and sold by the Swiss company Id Quantique
Id Quantique
id Quantique is a small company located in Geneva, Switzerland. It sells quantum key distribution systems, single photon counters, and physical random number generators...
).. It is one of the first successful ‘intercept-and-resend’ attacks on top of a widely used QKD implementation in commercial QKD systems. This work has been widely reported by many medias. .
In a new (and what turned out to be actually, even an earlier) claim, it has now been experimentally shown that the detectors of two commercial devices could be fully remote-controlled using specially tailored bright illumination, which makes it possible to tracelessly acquire the full secret key. In a spree of publications thereafter, this collaboration between the Norwegian University of Science and Technology
Norwegian University of Science and Technology
The Norwegian University of Science and Technology , commonly known as NTNU, is located in Trondheim. NTNU is the second largest of the eight universities in Norway, and, as its name suggests, has the main national responsibility for higher education in engineering and technology...
in Norway and Max Planck Institute for the Science of Light in Germany, has now demonstrated several methods to successfully eavesdrop on commercial QKD systems based on Avalanche photodiodes (APDs) operating in gated mode.
Denial of service
Because currently a dedicated fibre optic line (or line of sight in free space) is required between the two points linked by quantum key distribution, a denial of service attack can be mounted by simply cutting or blocking the line. This is one of the motivations for the development of quantum key distribution networksQuantum network
Quantum networks descend from the study of Quantum cryptography. The idea of a quantum network emerged after successful experiments on quantum teleportation...
, which would route communication via alternate links in case of disruption.
Weak measurement
It may be possible to measure the photons without disturbing them using Weak measurementWeak measurement
Weak measurements are a type of quantum measurement, where the measured system is very weakly coupled to the measuring device. After the measurement the measuring device pointer is shifted by what is called the "weak value". So that a pointer initially pointing at zero before the measurement would...
. Fortunately such measurements can be detected because they delay the arrival of the photons slightly. However, as weak measurement becomes perfected it will be necessary for the QKD protocols to check for these time delays.
History
Quantum cryptography was proposed first by Stephen WiesnerStephen Wiesner
Stephen J. Wiesner is a research physicist currently living in Israel. As a graduate student at Columbia University in New York in the late 1960s and early 1970s, he discovered several of the most important ideas in quantum information theory, including quantum money , quantum multiplexing...
, then at Columbia University in New York, who, in the early 1970s, introduced the concept of quantum conjugate coding. His seminal paper titled "Conjugate Coding" was rejected by IEEE Information Theory but was eventually published in 1983 in SIGACT News (15:1 pp. 78–88, 1983). In this paper he showed how to store or transmit two messages by encoding them in two “conjugate observables”, such as linear and circular polarization of light, so that either, but not both, of which may be received and decoded. He illustrated his idea with a design of unforgeable bank notes. A decade later, building upon this work, Charles H. Bennett
Charles H. Bennett (computer scientist)
Charles H. Bennett is an IBM Fellow at IBM Research. Bennett's recent work at IBM has concentrated on a re-examination of the physical basis of information, applying quantum physics to the problems surrounding information exchange...
, of the IBM Thomas J. Watson Research Center
Thomas J. Watson Research Center
The Thomas J. Watson Research Center is the headquarters for the IBM Research Division.The center is on three sites, with the main laboratory in Yorktown Heights, New York, 38 miles north of New York City, a building in Hawthorne, New York, and offices in Cambridge, Massachusetts.- Overview :The...
, and Gilles Brassard
Gilles Brassard
Gilles Brassard was born in Montreal, Canada, in 1955. He received a Masters degree from the Université de Montréal in 1975, and obtained his Ph.D. in Computer Science from Cornell University in 1979, working in the field of cryptography with John Hopcroft as his advisor...
, of the Université de Montréal, proposed a method for secure communication based on Wiesner’s “conjugate observables”. In 1990, independently and initially unaware of the earlier work, Artur Ekert
Artur Ekert
Artur Ekert is a Professor of Quantum Physics at the Mathematical Institute, University of Oxford, and a Lee Kong Chian Centennial Professor at the National University of Singapore and also the Director of CQT...
, then a Ph.D. student at Wolfson College, University of Oxford
Wolfson College, Oxford
Wolfson College is a constituent college of the University of Oxford in England. Located in north Oxford along the River Cherwell, Wolfson is an all-graduate college with over sixty governing body fellows, in addition to both research and junior research fellows. It caters to a wide range of...
, developed a different approach to quantum key distribution based on peculiar quantum correlations known as quantum entanglement.
Future
The current commercial systems are aimed mainly at governments and corporations with high security requirements. Key distribution by courier is typically used in such cases, where traditional key distribution schemes are not believed to offer enough guarantee. This has the advantage of not being intrinsically distance limited, and despite long travel times the transfer rate can be high due to the availability of large capacity portable storage devices. The major difference of quantum key distribution is the ability to detect any interception of the key, whereas with courier the key security cannot be proven or tested. QKD (Quantum Key Distribution) systems also have the advantage of being automatic, with greater reliability and lower operating costs than a secure human courier network.Factors preventing wide adoption of quantum key distribution outside high security areas include the cost of equipment, and the lack of a demonstrated threat to existing key exchange protocols. However, with optic fibre networks already present in many countries the infrastructure is in place for a more widespread use.
See also
- Quantum CryptographyQuantum cryptographyQuantum key distribution uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages...
- Quantum Computing
- Quantum Information ScienceQuantum information scienceQuantum information science is an area of study based on the idea that information science depends on quantum effects in physics. It includes theoretical issues in computational models as well as more experimental topics in quantum physics including what can and cannot be done with quantum...
- List of quantum key distribution protocols
- Quantum networkQuantum networkQuantum networks descend from the study of Quantum cryptography. The idea of a quantum network emerged after successful experiments on quantum teleportation...
External links
- General and Review
- Scientific American Magazine (January 2005 Issue) Best-Kept Secrets Non-technical article on quantum cryptography
- Physics World Magazine (March 2007 Issue) Non-technical article on current state and future of quantum communication
- arXiv:0802.4155 (quant-ph) February 2008 review of Quantum Cryptography
- arXiv:quant-ph/0702202v3 March 2007 review of Quantum Cryptography
- SECOQC White Paper on Quantum Key Distribution and Cryptography European project to create a large scale quantum cryptography network, includes discussion of current QKD approaches and comparison with classical cryptography
- The future of cryptography May 2003 Tomasz Grabowski
- ARDA Quantum Cryptography Roadmap
- Lectures at the Institut Henri Poincaré (slides and videos)
- Interactive quantum cryptography demonstration experiment with single photons for education
- More Specific Information
- Description of entanglement based quantum cryptography from Artur Ekert http://pass.maths.org.uk/issue35/features/ekert/index.html
- Description of BB84 protocol and privacy amplification http://www.ai.sri.com/~goldwate/quantum.html
- Original paper on the BB84 Protocol for Quantum Cryptography http://quantum.bbn.com/dscgi/ds.py/Get/File-18/BB84.pdf
- Original paper on Entanglement-based quantum cryptography http://quantum.bbn.com/dscgi/ds.py/Get/File-369/Ekert_-_QKD_Based_On_Bells_Theorem.pdf
- Further Information
- Quantum Cryptography Research Groups
- Companies selling quantum devices for cryptography
- id Quantique sells Quantum Key Distribution products
- MagiQ Technologies sells quantum devices for cryptography
- QuintessenceLabs Solutions based on continuous wave lasers
- Companies with quantum cryptography research programmes

