FEAL
Encyclopedia
In cryptography
, FEAL (the Fast data Encipherment ALgorithm) is a block cipher
proposed as an alternative to the Data Encryption Standard
(DES), and designed to be much faster in software. The Feistel
based algorithm was first published in 1987 by Akihiro Shimizu and Shoji Miyaguchi from NTT
. The cipher is susceptible to various forms of cryptanalysis
, and has acted as a catalyst in the discovery of differential
and linear cryptanalysis
.
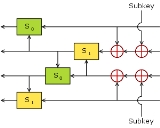
There have been several different revisions of FEAL, though all are Feistel cipher
s, and make use of the same basic round function and operate on a 64-bit block
. One of the earliest designs is now termed FEAL-4, which has four rounds and a 64-bit key
.
Unfortunately, problems were found with FEAL-4 from the start: Bert den Boer related a weakness in an unpublished rump session at the same conference where the cipher was first presented. A later paper (den Boer, 1988) describes an attack requiring 100–10000 chosen plaintexts, and Sean Murphy (1990) found an improvement that needs only 20 chosen plaintexts. Murphy and den Boer's methods contain elements similar to those used in differential cryptanalysis
.
The designers countered by doubling the number of rounds, FEAL-8 (Shimizu and Miyaguchi, 1988). However, eight rounds also proved to be insufficient — in 1989, at the Securicom conference, Eli Biham
and Adi Shamir
described a differential attack on the cipher, mentioned in (Miyaguchi, 1989). Gilbert and Chassé (1990) subsequently published a statistical attack similar to differential cryptanalysis which requires 10000 pairs of chosen plaintexts.
In response, the designers introduced a variable-round cipher, FEAL-N (Miyaguchi, 1990), where "N" was chosen by the user, together with FEAL-NX, which had a larger 128-bit key. Biham and Shamir's differential cryptanalysis (1991) showed that both FEAL-N and FEAL-NX could be broken faster than exhaustive search for N ≤ 31. Later attacks, precursors to linear cryptanalysis, could break versions under the known plaintext assumption, first (Tardy-Corfdir and Gilbert, 1991) and then (Matsui and Yamagishi, 1992), the latter breaking FEAL-4 with 5 known plaintexts, FEAL-6 with 100, and FEAL-8 with 215.
In 1994, Ohta and Aoki presented a linear cryptanalytic attack against FEAL-8 that required 212 known plaintexts.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, FEAL (the Fast data Encipherment ALgorithm) is a block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
proposed as an alternative to the Data Encryption Standard
Data Encryption Standard
The Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
(DES), and designed to be much faster in software. The Feistel
Feistel cipher
In cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German-born physicist and cryptographer Horst Feistel who did pioneering research while working for IBM ; it is also commonly known as a Feistel network. A large proportion of block...
based algorithm was first published in 1987 by Akihiro Shimizu and Shoji Miyaguchi from NTT
Nippon Telegraph and Telephone
, commonly known as NTT, is a Japanese telecommunications company headquartered in Tokyo, Japan. Ranked the 31st in Fortune Global 500, NTT is the largest telecommunications company in Asia, and the second-largest in the world in terms of revenue....
. The cipher is susceptible to various forms of cryptanalysis
Cryptanalysis
Cryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key...
, and has acted as a catalyst in the discovery of differential
Differential cryptanalysis
Differential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash functions. In the broadest sense, it is the study of how differences in an input can affect the resultant difference at the output...
and linear cryptanalysis
Linear cryptanalysis
In cryptography, linear cryptanalysis is a general form of cryptanalysis based on finding affine approximations to the action of a cipher. Attacks have been developed for block ciphers and stream ciphers...
.
There have been several different revisions of FEAL, though all are Feistel cipher
Feistel cipher
In cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German-born physicist and cryptographer Horst Feistel who did pioneering research while working for IBM ; it is also commonly known as a Feistel network. A large proportion of block...
s, and make use of the same basic round function and operate on a 64-bit block
Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
. One of the earliest designs is now termed FEAL-4, which has four rounds and a 64-bit key
Key (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
.
Unfortunately, problems were found with FEAL-4 from the start: Bert den Boer related a weakness in an unpublished rump session at the same conference where the cipher was first presented. A later paper (den Boer, 1988) describes an attack requiring 100–10000 chosen plaintexts, and Sean Murphy (1990) found an improvement that needs only 20 chosen plaintexts. Murphy and den Boer's methods contain elements similar to those used in differential cryptanalysis
Differential cryptanalysis
Differential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash functions. In the broadest sense, it is the study of how differences in an input can affect the resultant difference at the output...
.
The designers countered by doubling the number of rounds, FEAL-8 (Shimizu and Miyaguchi, 1988). However, eight rounds also proved to be insufficient — in 1989, at the Securicom conference, Eli Biham
Eli Biham
Eli Biham is an Israeli cryptographer and cryptanalyst, currently a professor at the Technion Israeli Institute of Technology Computer Science department. Starting from October 2008, Biham is the dean of the Technion Computer Science department, after serving for two years as chief of CS graduate...
and Adi Shamir
Adi Shamir
Adi Shamir is an Israeli cryptographer. He is a co-inventor of the RSA algorithm , a co-inventor of the Feige–Fiat–Shamir identification scheme , one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography and computer...
described a differential attack on the cipher, mentioned in (Miyaguchi, 1989). Gilbert and Chassé (1990) subsequently published a statistical attack similar to differential cryptanalysis which requires 10000 pairs of chosen plaintexts.
In response, the designers introduced a variable-round cipher, FEAL-N (Miyaguchi, 1990), where "N" was chosen by the user, together with FEAL-NX, which had a larger 128-bit key. Biham and Shamir's differential cryptanalysis (1991) showed that both FEAL-N and FEAL-NX could be broken faster than exhaustive search for N ≤ 31. Later attacks, precursors to linear cryptanalysis, could break versions under the known plaintext assumption, first (Tardy-Corfdir and Gilbert, 1991) and then (Matsui and Yamagishi, 1992), the latter breaking FEAL-4 with 5 known plaintexts, FEAL-6 with 100, and FEAL-8 with 215.
In 1994, Ohta and Aoki presented a linear cryptanalytic attack against FEAL-8 that required 212 known plaintexts.

