
Bombe
Encyclopedia
The bombe was an electromechanical device used by British
cryptologists to help decipher German
Enigma
-machine-encrypted signals during World War II
. The US Navy
and US Army
later produced machines to the same functional specification, but engineered differently.
The initial design of the bombe was produced in 1939 at the UK Government Code and Cypher School at Bletchley Park
by Alan Turing
, with an important refinement devised in 1940 by Gordon Welchman
. The engineering design and construction was the work of Harold Keen
of the British Tabulating Machine Company
. It was a substantial development from a device that had been designed in 1938 by Polish Cipher Bureau cryptologist Marian Rejewski
, and known as the "cryptologic bomb
" (Polish
: "bomba kryptologiczna").
The function of the bombe was to discover some of the daily settings of the Enigma machines on the various German military networks
: specifically, the set of rotors in use and their positions in the machine; the rotor core start positions for the message—the message key
—and one of the wirings of the plugboard.

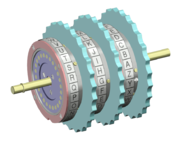 The Enigma was an electro-mechanical
The Enigma was an electro-mechanical
rotor machine
used for the encryption
and decryption of secret messages. It was developed in Germany in the 1920s. The repeated changes of the electrical pathway from the keyboard to the lampboard, implemented a polyalphabetic substitution
cipher, which turned plaintext
into ciphertext
and back again. Used properly, this provided a very high degree of security. The Enigma's scrambler contained rotors with 26 electrical contacts on each side, whose wiring diverted the current to a different position on the two sides. On depressing a key on the keyboard, an electrical current flowed through an entry drum at the right-hand end of the scrambler, then through the set of rotors to a reflecting drum (or reflector) which turned it back though the rotors and entry drum, and out to cause one lamp on the lampboard to be illuminated.
At each key depression, at least one of the rotors (the right-hand or "fast" rotor) advanced one position, which caused the encipherment to alter. At a certain point, the right-hand rotor caused the middle rotor to advance and in a similar way, the middle rotor caused the left-hand (or "slow") rotor to advance. Each rotor caused the "turnover" of the rotor to its left after a full rotation. The Enigma operator could rotate the wheels by hand to change the letter of the alphabet showing through a window, to set the start position of the rotors for enciphering a message. This three-letter sequence was "message key". There were 26 × 26 × 26 17,576 possible positions of the set of three rotors, and hence different message keys. By opening the lid of the machine and releasing a compression bar, the set of three rotors on their spindle could be removed from the machine and their sequence (called the "wheel order" at Bletchley Park) could be altered. Multiplying 17,576 by the six possible wheel orders gives 105,456 different ways that the scrambler could be set up.
 In 1930 an additional security feature was introduced for the military Enigmas. This was a plugboard (Steckerbrett in German, shortened to "Stecker") that further scrambled the letters. Letters were swapped in pairs: if A was transformed into R then R was transformed into A. This regularity was exploited by Welchman's "diagonal board" enhancement to the bombe, which vastly increased its efficiency. With six plug leads in use (leaving 14 letters "unsteckered") this gives 100,391,791,500 possible ways of setting up the plugboard.
In 1930 an additional security feature was introduced for the military Enigmas. This was a plugboard (Steckerbrett in German, shortened to "Stecker") that further scrambled the letters. Letters were swapped in pairs: if A was transformed into R then R was transformed into A. This regularity was exploited by Welchman's "diagonal board" enhancement to the bombe, which vastly increased its efficiency. With six plug leads in use (leaving 14 letters "unsteckered") this gives 100,391,791,500 possible ways of setting up the plugboard.
An important feature of the machine from a cryptanalyst's point of view, and indeed Enigma's Achilles' heel
, was that the reflector in the scrambler meant that a letter was never enciphered as itself. Any putative solution that gave, for any location, the same letter in the proposed plaintext and the ciphertext, could therefore be eliminated.
In the lead up to World War II
, the Germans made successive improvements to their military Enigma machines. By January 1939, additional rotors had been introduced so that there was a choice of three from five (i.e. 60 wheel orders) for the army and airforce Enigmas, and three out of eight (336 wheel orders) for the navy machines. In addition, ten leads were used on the plugboard leaving only six letters unsteckered. This meant that the airforce and army Enigmas could be set up 150 million, million, million ways. In 1941 the German navy introduced a version of Enigma with rotatable reflector (the M4 or Four-rotor Enigma) for communicating with its U-boat
s. This could be set up in 1,800 million, million, million different ways.
, combined with intelligence reports, convinced Admiral Karl Dönitz
that the Allies could read German Navy communications, and a thin fourth rotor with unknown wiring was added to German Navy Enigmas used for U-boat communications, to produce the Triton system, known at Bletchley Park as Shark. The Triton had a lock-out that allowed it to remain compatible with three-rotor machines when necessary. As before, the unknown wiring would prevent unauthorized reading of messages. Fortunately for the Allies, in December 1941, before the machine went into official service, a submarine accidentally sent a message using four rotors, then the same message again using only three, thus disclosing the wiring of the extra rotor. In February 1942 the change in number of rotors used became official, and British ability to read German submarines' messages largely ceased until new equipment became available that could use the information about the fourth-rotor wiring.
The first half of 1942 was the "second happy time
" for the German U-boats, with renewed success in attacking Allied shipping. This was due to the security of the new Enigma, and their ability to read convoy messages sent in Allied Naval Cipher No. 3. Between January and March 1942, German submarines sank 216 ships off the US East Coast. In May 1942 the US began using the convoy system and requiring a blackout of coastal cities so that ships would not be silhouetted against their lights, but this yielded only slightly improved security for Allied shipping.
Internal settings (that required the lid of the Enigma machine to be opened)
External settings (that could be changed without opening the machine)
The bombe identified possible initial positions of the rotor cores, and the stecker partner of a specified letter for a set of wheel orders. Manual techniques were then used to complete the decryption process. In the words of Gordon Welchman
"... the task of the bombe was simply to reduce the assumptions of wheel order and scrambler positions that required 'further analysis' to a manageable number."
s wired together. A standard German Enigma employed, at any one time, a set of three rotors
each of which could be set in any of 26 positions. The standard British bombe contained thirty six Enigma-equivalents, each with three drums wired to produce the same scrambling effect as the Enigma rotors. A bombe could run two or three jobs simultaneously.
Each job would have a menu that had to be run against a number of different wheel orders. If the menu contained 12 or fewer letters, three different wheel orders could be run on one bombe; if more than 12 letters, only two.
Unlike Enigma rotors, the bombe drums had two sets of input and output contacts, so that they could be connected together in series. Each drum had 104 wire brushes which made contact with the plate onto which they were loaded. The brushes and the corresponding set of contacts on the plate, were arranged in four concentric circles of 26. The outer pair of circles (input and output) were equivalent to the current in an Enigma passing in one direction through the scrambler, and the inner pair equivalent to the current flowing in the opposite direction.
The interconnections within the drums between the two sets of input and output contacts were both identical to those of the relevant Enigma rotor. There was permanent wiring between the inner two sets of contacts of the three input/output plates. From there, the circuit continued to a plugboard located on the left-hand end panel which was wired to imitate an Enigma reflector, and then back thought the outer pair of contacts. At each end of the "double-ended Enigma", there were sockets on the back of the machine into which 26-way cables could be plugged.
The bombe drums were arranged with the top one of the three simulating the left-hand rotor of the Enigma scrambler, the middle one the middle rotor, and the bottom one the right-hand rotor. The top drums were all driven in synchrony by an electric motor. For each full rotation of the top drums, the middle drums were incremented by one position, and likewise for the middle and bottom drums, giving the total of 26 × 26 × 26 = 17,576 positions of the 3-rotor Enigma scrambler.
The drums were colour-coded according to which Enigma rotor they emulated: I Red; II Maroon; III Green; IV Yellow; V Brown; VI Cobalt (Blue); VII Jet (Black); VIII Silver.
At each position of the rotors, an electrical current would or would not flow in each of the 26 wires, and this would be tested in the bombe's comparator unit. For a large number of positions, the test would lead to a logical contradiction
, ruling out that setting. If the test did not lead to a contradiction, the machine would stop.
The operator would record the candidate solution by reading the positions of the indicator drums and the indicator unit on the Bombe's right-hand end panel. The operator then re-started the run. The candidate solutions, stops as they were called, were processed further to eliminate as many false stops as possible. Typically, there were many false bombe stops before the correct one was found.
The candidate solutions for the set of wheel orders, were subject to extensive further cryptanalytical work. This progressively eliminated the false stops, built up the set of plugboard connections and established the positions of the rotor alphabet rings. Eventually, the result would be tested on a Typex
machine that had been modified to replicate an Enigma, to see if that decryption produced German language
.
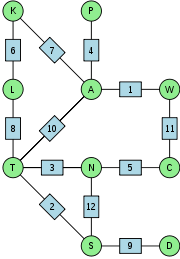 A bombe run involved a cryptanalyst first obtaining a crib — a section of plaintext
A bombe run involved a cryptanalyst first obtaining a crib — a section of plaintext
that was thought to correspond to the ciphertext
. Finding cribs was not at all straightforward; it required considerable familiarity with German military jargon and the communication habits of the operators. However, the codebreakers were aided by the fact that the Enigma would never encrypt a letter to itself. This helped in testing a possible crib against the ciphertext, as it could rule out a number of cribs and positions, where the same letter occurred in the same position in both the plaintext and the ciphertext. This was termed a crash at Bletchley Park.
Once a suitable crib had been decided upon, the cryptanalyst would produce a menu for wiring up the bombe to test the crib against the ciphertext. The following is a simplified explanation of the process of constructing a menu. Suppose that the crib is ATTACKATDAWN to be tested against a certain stretch of ciphertext, say, WSNPNLKLSTCS.The letters of the crib and the ciphertext were compared to establish pairings between the ciphertext and the crib plaintext. These were then graphed to as in the diagram. It should be borne in mind that the relationships are reciprocal so that A in the plaintext associated with W in the ciphertext is the same as W in the plaintext associated with A in the ciphertext. At position 1 of the plaintext-ciphertext comparison, the letter A is associated with W, but A is also associated with P at position 4, K at position 7 and T at position 10. Building up these relationships into such a diagram provided the menu from which the bombe connections and drum start positions would be set up.
In the illustration, there are three sequences of letters which form loops (or cycles or closures), ATLK, TNS and TAWCN. The more loops in the menu, the more candidate rotor settings the bombe could reject, and hence the fewer false stops.
Alan Turing conducted a very substantial analysis (without any electronic aids) to estimate how many bombe stops would be expected according to the number of letters in the menu and the number of loops. Some of his results are given in the following table. Recent bombe simulations have shown similar results.
machine modified to replicate Enigma, could be set up and the crib letter A encrypted on it, and compared with the ciphertext, W. If they matched, the next letter would be tried, checking that T encrypted to S and so on for the entire length of the crib. If at any point the letters failed to match, the initial rotor setting would be rejected; most incorrect settings would be ruled out after testing just two letters. This test could be readily mechanised and applied to all 17,576 settings of the rotors.
However, with the plugboard, it was much harder to perform trial encryptions because it was unknown what the crib and ciphertext letters were transformed to by the plugboard. For example, in the first position, A and W were unknown because the plugboard settings were unknown.
Turing's solution to working out the stecker values (plugboard connections) was to note that, even though the values for, say, A or W, were unknown, the crib still provided known relationships amongst these values; that is, the values after the plugboard transformation. Using these relationships, a cryptanalyst could reason from one to another and, potentially, derive a logical contradiction, in which case the rotor setting under consideration could be ruled out.
A worked example of such reasoning might go as follows: a cryptanalyst might suppose that AY. Looking at position 10 of the crib:ciphertext comparison, we observe that A encrypts to T, or, expressed as a formula:
Because the function is its own inverse, we can apply it to both sides of the equation and obtain the following:
This gives us a relationship between A and T. If A = Y, and for the rotor setting under consideration Y = Q (say), we can deduce that
While the crib does not allow us to determine what the values after the plugboard are, it does provide a constraint between them. In this case, it shows how T is completely determined if A is known.
Likewise, we can also observe that T encrypts to L at position 8. Using , we can deduce the steckered value for L as well using a similar argument, to get, say,
Similarly, in position 6, K encrypts to L. As the Enigma machine is self-reciprocal, this means that at the same position L would also encrypt to K. Knowing this, we can apply the argument once more to deduce a value for P(K, which might be:
And again, the same sort of reasoning applies at position 7 to get:
However, in this case, we have derived a contradiction
, since, by hypothesis, we assumed that A = Y at the outset. This means that the initial assumption must have been incorrect, and so that (for this rotor setting) A ≠ Y (this type of argument is termed reductio ad absurdum
or "proof by contradiction").
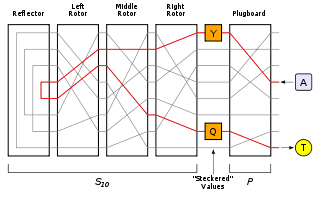 The cryptanalyst hypothesised one plugboard interconnection for the bombe to test. The other stecker values and the ring settings were worked out by hand methods.
The cryptanalyst hypothesised one plugboard interconnection for the bombe to test. The other stecker values and the ring settings were worked out by hand methods.
While Turing's bombe worked in theory, it required impractically long cribs to rule out sufficiently large numbers of settings. Gordon Welchman
came up with a way of using the symmetry of the Enigma stecker to increase the power of the bombe. His suggestion was an attachment called the diagonal board that further improved the bombe's effectiveness.
(Polish: bomba kryptologiczna) had been useful only as long as three conditions were met. First, the form of the indicator
had to include the repetition of the message key; second, the number of rotors available had to be limited to three, giving six different "wheel orders" (the three rotors and their order within the machine); and third, the number of plug-board leads had to remain relatively small so that the majority of letters were unsteckered. Six machines were built, one for each possible rotor order. They were delivered in November 1938, but barely a month later the Germans introduced two additional rotors for loading into the Enigma scrambler, increasing the number of wheel orders by a factor of ten. Building a further 54 bomby was beyond the Poles' resources. Also, on 1 January 1939, the number of plug-board leads was increased to ten. The Poles had therefore had to return to manual methods, the Zygalski sheets.
Alan Turing
designed the British bombe on a more general principle, the assumption of the presence of text, called a crib, that cryptanalysts could predict was likely to be present at a defined point in the message. This technique is termed a known plaintext attack and had been used to a limited extent by the Poles, e.g., the Germans' use of "ANX" — German for "To," followed by "X" as a spacer.
The bombes were built by the British Tabulating Machine Company
at Letchworth
under the direction of Harold 'Doc' Keen
. Each machine was about 7 feet (2.1 m) wide, 6 in 6 in (1.98 m) tall, 2 foot (0.6096 m) deep and weighed about a ton. On the front of each bombe were 108 places where drums could be mounted. The drums were in three groups of 12 triplets. Each triplet, arranged vertically, corresponded to the three rotors of an Enigma scrambler. The bombe drums' input and output contacts went to cable connectors, allowing the bombe to be wired up according to the menu. The 'fast' drum rotated at a speed of 50.4 rpm in the first models and 120 rpm in later ones, when the time to set up and run through all 17,576 possible positions for one rotor order was about 20 minutes.
The first bombe, which was based on Turing's original design and so lacked a diagonal board, was installed at Bletchley Park on 18 March 1940 and was named "Victory". The second bombe, named "Agnus dei", later shortened to "Agnes", or "Aggie", was equipped with Welchman's diagonal board, and was installed on 8 August 1940; "Victory" was later returned to Letchworth to have a diagonal board fitted.
During 1940, 178 messages were broken on the two machines, nearly all successfully. Because of the danger of bombes at Bletchley Park being lost if there were to be a bombing raid, five bombe outstations were established, at Adstock
, Gayhurst
, Wavendon
, Stanmore
, and Eastcote
. The bombe was referred to by Group Captain Winterbotham as a "Bronze Goddess" because its case was made of bronze. The devices were more prosaically described by operators as being "like great big metal bookcases".
Production of bombes by BTM at Letchworth in wartime conditions, was nowhere near as rapid as the Americans later achieved at NCR in Dayton, Ohio.
After World War II, some fifty bombes were retained at Eastcote
, while the rest were destroyed. The surviving bombes were put to work, possibly on Eastern bloc
ciphers. The official history of the bombe states that "some of these machines were to be stored away but others were required to run new jobs and sixteen machines were kept comparatively busy on menus. It is interesting to note that most of the jobs came up and the operating, checking and other times maintained were faster than the best times during the war periods."
A team led by John Harper conducted a 13-year project to reconstruct a working bombe. This was successful, and the reconstructed bombe can be seen at Bletchley Park
Museum. In March 2009 it won an Engineering Heritage Award.
to design much faster bombes that could decrypt the four-rotor system in a reasonable time. There were two streams of development. One, with an electronic sensing unit, was produced by Charles Wynn-Williams
of the Telecommunications Research Establishment
(TRE) at Malvern. The other was designed by Harold Keen
at BTM
, Letchworth. Initial delivery was scheduled for August or September 1942.
Unlike the situation at Bletchley Park, the United States armed services did not share a combined cryptanalytical service. Indeed there was considerable rivalry between the US Army's
facility, the Signals Intelligence Service (SIS)
, and that of the US Navy
known as OP-20-G
. Before the US joined the war, there was collaboration with Britain, albeit with a considerable amount of caution on Britain's side because of the extreme importance of Germany and her allies not learning that its codes were being broken. Despite some worthwhile collaboration amongst the cryptanalysts, their superiors took some time to achieve a trusting relationship in which both British and American bombes were used to mutual benefit.
In February 1941, Captain Abe Sinkov and Lieutenant Leo Rosen of the US Army, and US Naval Lieutenants Robert Weeks and Prescott Currier, arrived at Bletchley Park bringing, amongst other things, a replica of the 'Purple' cipher machine for the Bletchley Park's Japanese section in Hut 7
. The four returned to America after ten weeks, with a naval radio direction finding
unit and many documents including a 'paper Enigma'.
Currier later wrote:
The main response to the Four-rotor Enigma was the US Navy bombe, which was manufactured in much less constrained facilities than were available in wartime Britain.
) in April 1942 and recognised America's vital interest in deciphering U-boat traffic. The urgent need, doubts about the British engineering workload and slow progress, prompted the US to start investigating designs for a Navy bombe, based on the full blueprint
s and wiring diagrams received by US Naval Lieutenants Robert Ely and Joseph Eachus at Bletchley Park in July 1942. Funding for a full, $2 million, navy development effort was requested on 3 September 1942 and approved the following day.
 Commander Edward Travis
Commander Edward Travis
, Deputy Director and Frank Birch
, Head of the German Naval Section travelled from Bletchley Park to Washington in September 1942. With Carl Frederick Holden
, US Director of Naval Communications they established, on 2 October 1942, a UK:US accord which may have "a stronger claim than BRUSA
to being the forerunner of the UKUSA Agreement
," being the first agreement "to establish the special Sigint relationship between the two countries," and "it set the pattern for UKUSA, in that the United States was very much the senior partner in the alliance." It established a relationship of "full collaboration" between Bletchley Park and OP-20-G.
An all electronic solution to the problem of a fast bombe was considered, but rejected for pragmatic reasons, and a contract was let with the National Cash Register Corporation
(NCR) in Dayton, Ohio
. This established the United States Naval Computing Machine Laboratory
. Engineering development was led by NCR's Joseph Desch
.
Alan Turing
, who had written a memorandum to OP-20-G (probably in 1941), was seconded to the British Joint Staff Mission in Washington in December 1942, because of his exceptionally wide knowledge about the bombes and the methods of their use. He was asked to look at the bombes that were being built by NCR and at the security of certain speech cipher equipment under development at Bell Labs. He visited OP-20-G, and went to NCR in Dayton on the 21 December. He was able to show that it was not necessary to build 336 Bombes, one for each possible rotor order, by utilising techniques such as Banburismus
. The initial order was scaled down to 96 machines.
The US Navy bombes used drums for the Enigma rotors in much the same way as the British bombes. They had eight Enigma-equivalents on the front and eight on the back. The fast drum rotated at 1,725 rpm
, 34 times the speed of the early British bombes. 'Stops' were detected electronically using thermionic valves
(vacuum tubes)—mostly thyratron
s—for the high speed circuits. When a 'stop' was found the machine over-ran as it slowed, reversed to the position found and printed it out before re-starting. The running time for a 4-rotor run was about 20 minutes, and for a 3-rotor run, about 50 seconds. Each machine was 10 feet (3 m) wide, 7 feet (2.1 m) high, 2 foot (0.6096 m) deep and weighed 2.5 tons.
The first machine was completed and tested on 3 May 1943. By 22 June, the first two machines, called 'Adam' and 'Eve' broke a particularly difficult German naval cipher, the Offizier settings for 9 and 10 June. A P Mahon, who had joined the Naval Section in Hut 8 in 1941, reported in his official 1945 "History of Hut Eight 1939-1945":
These bombes were faster, and soon more available, than the British bombes at Bletchley Park and its outstations. Consequently they were put to use for Hut 6 as well as Hut 8 work. In Alexander's "Cryptographic History of Work on German Naval Enigma", he wrote as follows.
Production was stopped in September 1944 after 121 bombes had been made. The last-manufactured US Navy bombe is on display at the US National Cryptologic Museum
. Jack Ingram, former Curator of the museum, describes being told of the existence of a second bombe and searching for it but not finding it whole. Whether it remains in storage in pieces, waiting to be discovered, or no longer exists, is unknown.
on 30 September 1942. The machine was designed to analyse 3-rotor, not 4-rotor traffic. It did not use drums to represent the Enigma rotors, using instead telephone-type relays. It could, however, handle one problem that the bombes with drums could not. The set of ten bombes consisted of a total of 144 Enigma-equivalents, each mounted on a rack approximately 7 feet (2.1 m) long 8 feet (2.4 m) high and 6 inches (152.4 mm) wide. There were 12 control stations which could allocate any of the Enigma-equivalents into the desired configuration by means of plugboards. Rotor order changes did not require the mechanical process of changing drums, but was achieved in about half a minute by means of push buttons. A 3-rotor run took about 10 minutes.
United Kingdom
The United Kingdom of Great Britain and Northern IrelandIn the United Kingdom and Dependencies, other languages have been officially recognised as legitimate autochthonous languages under the European Charter for Regional or Minority Languages...
cryptologists to help decipher German
Germany
Germany , officially the Federal Republic of Germany , is a federal parliamentary republic in Europe. The country consists of 16 states while the capital and largest city is Berlin. Germany covers an area of 357,021 km2 and has a largely temperate seasonal climate...
Enigma
Enigma machine
An Enigma machine is any of a family of related electro-mechanical rotor cipher machines used for the encryption and decryption of secret messages. Enigma was invented by German engineer Arthur Scherbius at the end of World War I...
-machine-encrypted signals during World War II
World War II
World War II, or the Second World War , was a global conflict lasting from 1939 to 1945, involving most of the world's nations—including all of the great powers—eventually forming two opposing military alliances: the Allies and the Axis...
. The US Navy
United States Navy
The United States Navy is the naval warfare service branch of the United States Armed Forces and one of the seven uniformed services of the United States. The U.S. Navy is the largest in the world; its battle fleet tonnage is greater than that of the next 13 largest navies combined. The U.S...
and US Army
United States Army
The United States Army is the main branch of the United States Armed Forces responsible for land-based military operations. It is the largest and oldest established branch of the U.S. military, and is one of seven U.S. uniformed services...
later produced machines to the same functional specification, but engineered differently.
The initial design of the bombe was produced in 1939 at the UK Government Code and Cypher School at Bletchley Park
Bletchley Park
Bletchley Park is an estate located in the town of Bletchley, in Buckinghamshire, England, which currently houses the National Museum of Computing...
by Alan Turing
Alan Turing
Alan Mathison Turing, OBE, FRS , was an English mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, providing a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which played a...
, with an important refinement devised in 1940 by Gordon Welchman
Gordon Welchman
Gordon Welchman was a British-American mathematician, university professor, World War II codebreaker at Bletchley Park, and author.-Education and early career:...
. The engineering design and construction was the work of Harold Keen
Harold Keen
Harold Hall "Doc" Keen was a British engineer who produced the engineering design, and oversaw the construction of, the British bombe, a codebreaking machine used in World War II to read German messages sent using the Enigma machine. He was known as "Doc" Keen because of his habit of carrying...
of the British Tabulating Machine Company
British Tabulating Machine Company
The British Tabulating Machine Company was a firm which manufactured and sold Hollerith unit record equipment and other data-processing equipment...
. It was a substantial development from a device that had been designed in 1938 by Polish Cipher Bureau cryptologist Marian Rejewski
Marian Rejewski
Marian Adam Rejewski was a Polish mathematician and cryptologist who in 1932 solved the plugboard-equipped Enigma machine, the main cipher device used by Germany...
, and known as the "cryptologic bomb
Bomba (cryptography)
The bomba, or bomba kryptologiczna was a special-purpose machine designed about October 1938 by Polish Cipher Bureau cryptologist Marian Rejewski to break German Enigma-machine ciphers....
" (Polish
Polish language
Polish is a language of the Lechitic subgroup of West Slavic languages, used throughout Poland and by Polish minorities in other countries...
: "bomba kryptologiczna").
The function of the bombe was to discover some of the daily settings of the Enigma machines on the various German military networks
Telecommunications network
A telecommunications network is a collection of terminals, links and nodes which connect together to enable telecommunication between users of the terminals. Networks may use circuit switching or message switching. Each terminal in the network must have a unique address so messages or connections...
: specifically, the set of rotors in use and their positions in the machine; the rotor core start positions for the message—the message key
Key (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
—and one of the wirings of the plugboard.
The Enigma machine


Electromechanics
In engineering, electromechanics combines the sciences of electromagnetism, of electrical engineering and mechanics. Mechanical engineering in this context refers to the larger discipline which includes chemical engineering, and other related disciplines. Electrical engineering in this context...
rotor machine
Rotor machine
In cryptography, a rotor machine is an electro-mechanical device used for encrypting and decrypting secret messages. Rotor machines were the cryptographic state-of-the-art for a prominent period of history; they were in widespread use in the 1920s–1970s...
used for the encryption
Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
and decryption of secret messages. It was developed in Germany in the 1920s. The repeated changes of the electrical pathway from the keyboard to the lampboard, implemented a polyalphabetic substitution
Polyalphabetic cipher
A polyalphabetic cipher is any cipher based on substitution, using multiple substitution alphabets. The Vigenère cipher is probably the best-known example of a polyalphabetic cipher, though it is a simplified special case...
cipher, which turned plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
into ciphertext
Ciphertext
In cryptography, ciphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher...
and back again. Used properly, this provided a very high degree of security. The Enigma's scrambler contained rotors with 26 electrical contacts on each side, whose wiring diverted the current to a different position on the two sides. On depressing a key on the keyboard, an electrical current flowed through an entry drum at the right-hand end of the scrambler, then through the set of rotors to a reflecting drum (or reflector) which turned it back though the rotors and entry drum, and out to cause one lamp on the lampboard to be illuminated.
At each key depression, at least one of the rotors (the right-hand or "fast" rotor) advanced one position, which caused the encipherment to alter. At a certain point, the right-hand rotor caused the middle rotor to advance and in a similar way, the middle rotor caused the left-hand (or "slow") rotor to advance. Each rotor caused the "turnover" of the rotor to its left after a full rotation. The Enigma operator could rotate the wheels by hand to change the letter of the alphabet showing through a window, to set the start position of the rotors for enciphering a message. This three-letter sequence was "message key". There were 26 × 26 × 26 17,576 possible positions of the set of three rotors, and hence different message keys. By opening the lid of the machine and releasing a compression bar, the set of three rotors on their spindle could be removed from the machine and their sequence (called the "wheel order" at Bletchley Park) could be altered. Multiplying 17,576 by the six possible wheel orders gives 105,456 different ways that the scrambler could be set up.

An important feature of the machine from a cryptanalyst's point of view, and indeed Enigma's Achilles' heel
Achilles' heel
An Achilles’ heel is a deadly weakness in spite of overall strength, that can actually or potentially lead to downfall. While the mythological origin refers to a physical vulnerability, metaphorical references to other attributes or qualities that can lead to downfall are common.- Origin :In Greek...
, was that the reflector in the scrambler meant that a letter was never enciphered as itself. Any putative solution that gave, for any location, the same letter in the proposed plaintext and the ciphertext, could therefore be eliminated.
In the lead up to World War II
World War II
World War II, or the Second World War , was a global conflict lasting from 1939 to 1945, involving most of the world's nations—including all of the great powers—eventually forming two opposing military alliances: the Allies and the Axis...
, the Germans made successive improvements to their military Enigma machines. By January 1939, additional rotors had been introduced so that there was a choice of three from five (i.e. 60 wheel orders) for the army and airforce Enigmas, and three out of eight (336 wheel orders) for the navy machines. In addition, ten leads were used on the plugboard leaving only six letters unsteckered. This meant that the airforce and army Enigmas could be set up 150 million, million, million ways. In 1941 the German navy introduced a version of Enigma with rotatable reflector (the M4 or Four-rotor Enigma) for communicating with its U-boat
U-boat
U-boat is the anglicized version of the German word U-Boot , itself an abbreviation of Unterseeboot , and refers to military submarines operated by Germany, particularly in World War I and World War II...
s. This could be set up in 1,800 million, million, million different ways.
Four-rotor Enigma
By late 1941 the change in German Navy fortunes in the Battle of the AtlanticBattle of the Atlantic
Battle of the Atlantic may refer to either of two naval campaigns:* The Atlantic U-boat Campaign during the First World War * The Battle of the Atlantic during the Second World War...
, combined with intelligence reports, convinced Admiral Karl Dönitz
Karl Dönitz
Karl Dönitz was a German naval commander during World War II. He started his career in the German Navy during World War I. In 1918, while he was in command of , the submarine was sunk by British forces and Dönitz was taken prisoner...
that the Allies could read German Navy communications, and a thin fourth rotor with unknown wiring was added to German Navy Enigmas used for U-boat communications, to produce the Triton system, known at Bletchley Park as Shark. The Triton had a lock-out that allowed it to remain compatible with three-rotor machines when necessary. As before, the unknown wiring would prevent unauthorized reading of messages. Fortunately for the Allies, in December 1941, before the machine went into official service, a submarine accidentally sent a message using four rotors, then the same message again using only three, thus disclosing the wiring of the extra rotor. In February 1942 the change in number of rotors used became official, and British ability to read German submarines' messages largely ceased until new equipment became available that could use the information about the fourth-rotor wiring.
The first half of 1942 was the "second happy time
Second happy time
The Second Happy Time , also known among German submarine commanders as the "American shooting season" was the informal name for a phase in the Second Battle of the Atlantic during which Axis submarines attacked merchant shipping along the east coast of North America...
" for the German U-boats, with renewed success in attacking Allied shipping. This was due to the security of the new Enigma, and their ability to read convoy messages sent in Allied Naval Cipher No. 3. Between January and March 1942, German submarines sank 216 ships off the US East Coast. In May 1942 the US began using the convoy system and requiring a blackout of coastal cities so that ships would not be silhouetted against their lights, but this yielded only slightly improved security for Allied shipping.
The principle of the bombe
To decipher German military Enigma messages required that the following settings of the machine were discovered. Once these were known, all the messages for that network for that day (or pair of days in the case of the German navy) could be decrypted.Internal settings (that required the lid of the Enigma machine to be opened)
- The selection of rotors in use in the Enigma's scrambler, and their positions on the spindle (Walzenlage or "wheel order"). Possible wheel orders numbered 60 (three rotors from a choice of five) for army and air force networks and 336 (three rotors from a choice of eight) for the naval networks.
- The positions of the alphabet ring's turnover notch in relation to the core of each rotor in use (Ringstellung or "ring settings"). There are 26 possible ring-settings for each rotor.
External settings (that could be changed without opening the machine)
- The plugboard connections (Steckerverbindungen or "stecker values"). The ten leads could be arranged in some 150 million million ways.
- The scrambler rotor positions at the start of enciphering the message key (the Grundstellung or "indicator-setting") — up to May 1940; or thereafter the initial positions of each rotor at the start of enciphering the message (the "message key") from which the indicator-setting could be derived. There are 17,576 possible three letter keys.
The bombe identified possible initial positions of the rotor cores, and the stecker partner of a specified letter for a set of wheel orders. Manual techniques were then used to complete the decryption process. In the words of Gordon Welchman
Gordon Welchman
Gordon Welchman was a British-American mathematician, university professor, World War II codebreaker at Bletchley Park, and author.-Education and early career:...
"... the task of the bombe was simply to reduce the assumptions of wheel order and scrambler positions that required 'further analysis' to a manageable number."
Structure
The bombe was an electro-mechanical device that replicated the action of several Enigma machineEnigma machine
An Enigma machine is any of a family of related electro-mechanical rotor cipher machines used for the encryption and decryption of secret messages. Enigma was invented by German engineer Arthur Scherbius at the end of World War I...
s wired together. A standard German Enigma employed, at any one time, a set of three rotors
Rotor machine
In cryptography, a rotor machine is an electro-mechanical device used for encrypting and decrypting secret messages. Rotor machines were the cryptographic state-of-the-art for a prominent period of history; they were in widespread use in the 1920s–1970s...
each of which could be set in any of 26 positions. The standard British bombe contained thirty six Enigma-equivalents, each with three drums wired to produce the same scrambling effect as the Enigma rotors. A bombe could run two or three jobs simultaneously.
Each job would have a menu that had to be run against a number of different wheel orders. If the menu contained 12 or fewer letters, three different wheel orders could be run on one bombe; if more than 12 letters, only two.
Unlike Enigma rotors, the bombe drums had two sets of input and output contacts, so that they could be connected together in series. Each drum had 104 wire brushes which made contact with the plate onto which they were loaded. The brushes and the corresponding set of contacts on the plate, were arranged in four concentric circles of 26. The outer pair of circles (input and output) were equivalent to the current in an Enigma passing in one direction through the scrambler, and the inner pair equivalent to the current flowing in the opposite direction.
The interconnections within the drums between the two sets of input and output contacts were both identical to those of the relevant Enigma rotor. There was permanent wiring between the inner two sets of contacts of the three input/output plates. From there, the circuit continued to a plugboard located on the left-hand end panel which was wired to imitate an Enigma reflector, and then back thought the outer pair of contacts. At each end of the "double-ended Enigma", there were sockets on the back of the machine into which 26-way cables could be plugged.
The bombe drums were arranged with the top one of the three simulating the left-hand rotor of the Enigma scrambler, the middle one the middle rotor, and the bottom one the right-hand rotor. The top drums were all driven in synchrony by an electric motor. For each full rotation of the top drums, the middle drums were incremented by one position, and likewise for the middle and bottom drums, giving the total of 26 × 26 × 26 = 17,576 positions of the 3-rotor Enigma scrambler.
The drums were colour-coded according to which Enigma rotor they emulated: I Red; II Maroon; III Green; IV Yellow; V Brown; VI Cobalt (Blue); VII Jet (Black); VIII Silver.
At each position of the rotors, an electrical current would or would not flow in each of the 26 wires, and this would be tested in the bombe's comparator unit. For a large number of positions, the test would lead to a logical contradiction
Contradiction
In classical logic, a contradiction consists of a logical incompatibility between two or more propositions. It occurs when the propositions, taken together, yield two conclusions which form the logical, usually opposite inversions of each other...
, ruling out that setting. If the test did not lead to a contradiction, the machine would stop.
The operator would record the candidate solution by reading the positions of the indicator drums and the indicator unit on the Bombe's right-hand end panel. The operator then re-started the run. The candidate solutions, stops as they were called, were processed further to eliminate as many false stops as possible. Typically, there were many false bombe stops before the correct one was found.
The candidate solutions for the set of wheel orders, were subject to extensive further cryptanalytical work. This progressively eliminated the false stops, built up the set of plugboard connections and established the positions of the rotor alphabet rings. Eventually, the result would be tested on a Typex
Typex
In the history of cryptography, Typex machines were British cipher machines used from 1937. It was an adaptation of the commercial German Enigma with a number of enhancements that greatly increased its security....
machine that had been modified to replicate an Enigma, to see if that decryption produced German language
German language
German is a West Germanic language, related to and classified alongside English and Dutch. With an estimated 90 – 98 million native speakers, German is one of the world's major languages and is the most widely-spoken first language in the European Union....
.
Bombe menu

Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
that was thought to correspond to the ciphertext
Ciphertext
In cryptography, ciphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher...
. Finding cribs was not at all straightforward; it required considerable familiarity with German military jargon and the communication habits of the operators. However, the codebreakers were aided by the fact that the Enigma would never encrypt a letter to itself. This helped in testing a possible crib against the ciphertext, as it could rule out a number of cribs and positions, where the same letter occurred in the same position in both the plaintext and the ciphertext. This was termed a crash at Bletchley Park.
Once a suitable crib had been decided upon, the cryptanalyst would produce a menu for wiring up the bombe to test the crib against the ciphertext. The following is a simplified explanation of the process of constructing a menu. Suppose that the crib is ATTACKATDAWN to be tested against a certain stretch of ciphertext, say, WSNPNLKLSTCS.The letters of the crib and the ciphertext were compared to establish pairings between the ciphertext and the crib plaintext. These were then graphed to as in the diagram. It should be borne in mind that the relationships are reciprocal so that A in the plaintext associated with W in the ciphertext is the same as W in the plaintext associated with A in the ciphertext. At position 1 of the plaintext-ciphertext comparison, the letter A is associated with W, but A is also associated with P at position 4, K at position 7 and T at position 10. Building up these relationships into such a diagram provided the menu from which the bombe connections and drum start positions would be set up.
| Ciphertext | W | S | N | P | N | L | K | L | S | T | C | S |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Plaintext "Crib" | A | T | T | A | C | K | A | T | D | A | W | N |
| Message Position | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| Upper Drum Setting | Z | Z | Z | Z | Z | Z | Z | Z | Z | Z | Z | Z |
| Middle Drum Setting | Z | Z | Z | Z | Z | Z | Z | Z | Z | Z | Z | Z |
| Lower Drum Setting | A | B | C | D | E | F | G | H | I | J | K | L |
In the illustration, there are three sequences of letters which form loops (or cycles or closures), ATLK, TNS and TAWCN. The more loops in the menu, the more candidate rotor settings the bombe could reject, and hence the fewer false stops.
Alan Turing conducted a very substantial analysis (without any electronic aids) to estimate how many bombe stops would be expected according to the number of letters in the menu and the number of loops. Some of his results are given in the following table. Recent bombe simulations have shown similar results.
| Number of letters on the menu | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| Loops | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
| 3 | 2.2 | 1.1 | 0.42 | 0.14 | 0.04 | <0.01 | <0.01 | <0.01 | <0.01 |
| 2 | 58 | 28 | 11 | 3.8 | 1.2 | 0.30 | 0.06 | <0.01 | <0.01 |
| 1 | 1500 | 720 | 280 | 100 | 31 | 7.7 | 1.6 | 0.28 | 0.04 |
| 0 | 40,000 | 19,000 | 7300 | 2700 | 820 | 200 | 43 | 7.3 | 1.0 |
Stecker values
The German military Enigma included a plugboard (Steckerbrett in German) which swapped letters (indicated here by ) before and after the main scrambler's change (indicated by ). The plugboard connections were known to the cryptanalysts as Stecker values. If there had been no plugboard, it would have been relatively straightforward to test a rotor setting; a TypexTypex
In the history of cryptography, Typex machines were British cipher machines used from 1937. It was an adaptation of the commercial German Enigma with a number of enhancements that greatly increased its security....
machine modified to replicate Enigma, could be set up and the crib letter A encrypted on it, and compared with the ciphertext, W. If they matched, the next letter would be tried, checking that T encrypted to S and so on for the entire length of the crib. If at any point the letters failed to match, the initial rotor setting would be rejected; most incorrect settings would be ruled out after testing just two letters. This test could be readily mechanised and applied to all 17,576 settings of the rotors.
However, with the plugboard, it was much harder to perform trial encryptions because it was unknown what the crib and ciphertext letters were transformed to by the plugboard. For example, in the first position, A and W were unknown because the plugboard settings were unknown.
Turing's solution to working out the stecker values (plugboard connections) was to note that, even though the values for, say, A or W, were unknown, the crib still provided known relationships amongst these values; that is, the values after the plugboard transformation. Using these relationships, a cryptanalyst could reason from one to another and, potentially, derive a logical contradiction, in which case the rotor setting under consideration could be ruled out.
A worked example of such reasoning might go as follows: a cryptanalyst might suppose that AY. Looking at position 10 of the crib:ciphertext comparison, we observe that A encrypts to T, or, expressed as a formula:
-
- T = A
Because the function is its own inverse, we can apply it to both sides of the equation and obtain the following:
-
- TA
This gives us a relationship between A and T. If A = Y, and for the rotor setting under consideration Y = Q (say), we can deduce that
-
- T = AY = Q
While the crib does not allow us to determine what the values after the plugboard are, it does provide a constraint between them. In this case, it shows how T is completely determined if A is known.
Likewise, we can also observe that T encrypts to L at position 8. Using , we can deduce the steckered value for L as well using a similar argument, to get, say,
-
- L = TQ = G
Similarly, in position 6, K encrypts to L. As the Enigma machine is self-reciprocal, this means that at the same position L would also encrypt to K. Knowing this, we can apply the argument once more to deduce a value for P(K, which might be:
-
- K = LG = F
And again, the same sort of reasoning applies at position 7 to get:
-
- A = KF = N
However, in this case, we have derived a contradiction
Contradiction
In classical logic, a contradiction consists of a logical incompatibility between two or more propositions. It occurs when the propositions, taken together, yield two conclusions which form the logical, usually opposite inversions of each other...
, since, by hypothesis, we assumed that A = Y at the outset. This means that the initial assumption must have been incorrect, and so that (for this rotor setting) A ≠ Y (this type of argument is termed reductio ad absurdum
Reductio ad absurdum
In logic, proof by contradiction is a form of proof that establishes the truth or validity of a proposition by showing that the proposition's being false would imply a contradiction...
or "proof by contradiction").

Automated deduction
To automate these logical deductions, the bombe took the form of an electrical circuit. Current flowed around the circuit near-instantaneously, and represented all the possible logical deductions which could be made at that position. To form this circuit, the bombe used several sets of Enigma rotor stacks wired up together according to the instructions given on a menu, derived from a crib. Because each Enigma machine had 26 inputs and outputs, the replica Enigma stacks are connected to each other using 26-way cables. In addition, each Enigma stack rotor setting is offset a number of places as determined by its position in the crib; for example, an Enigma stack corresponding to the fifth letter in the crib would be four places further on than that corresponding to the first letter.In practice
Practical bombes used several stacks of rotors spinning together to test multiple hypotheses about possible setups of the Enigma machine, such as the order of the rotors in the stack.While Turing's bombe worked in theory, it required impractically long cribs to rule out sufficiently large numbers of settings. Gordon Welchman
Gordon Welchman
Gordon Welchman was a British-American mathematician, university professor, World War II codebreaker at Bletchley Park, and author.-Education and early career:...
came up with a way of using the symmetry of the Enigma stecker to increase the power of the bombe. His suggestion was an attachment called the diagonal board that further improved the bombe's effectiveness.
The British bombe
The Polish cryptologic bombBomba (cryptography)
The bomba, or bomba kryptologiczna was a special-purpose machine designed about October 1938 by Polish Cipher Bureau cryptologist Marian Rejewski to break German Enigma-machine ciphers....
(Polish: bomba kryptologiczna) had been useful only as long as three conditions were met. First, the form of the indicator
Indicator
Indicator may mean:In chemistry:* pH indicator, a chemical detector for protons in acid-base titrations* Redox indicator, a chemical detector for redox titrations* Complexometric indicator, a chemical detector for metal ions in complexometric titrations...
had to include the repetition of the message key; second, the number of rotors available had to be limited to three, giving six different "wheel orders" (the three rotors and their order within the machine); and third, the number of plug-board leads had to remain relatively small so that the majority of letters were unsteckered. Six machines were built, one for each possible rotor order. They were delivered in November 1938, but barely a month later the Germans introduced two additional rotors for loading into the Enigma scrambler, increasing the number of wheel orders by a factor of ten. Building a further 54 bomby was beyond the Poles' resources. Also, on 1 January 1939, the number of plug-board leads was increased to ten. The Poles had therefore had to return to manual methods, the Zygalski sheets.
Alan Turing
Alan Turing
Alan Mathison Turing, OBE, FRS , was an English mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, providing a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which played a...
designed the British bombe on a more general principle, the assumption of the presence of text, called a crib, that cryptanalysts could predict was likely to be present at a defined point in the message. This technique is termed a known plaintext attack and had been used to a limited extent by the Poles, e.g., the Germans' use of "ANX" — German for "To," followed by "X" as a spacer.
The bombes were built by the British Tabulating Machine Company
British Tabulating Machine Company
The British Tabulating Machine Company was a firm which manufactured and sold Hollerith unit record equipment and other data-processing equipment...
at Letchworth
Letchworth
Letchworth Garden City, commonly known as Letchworth, is a town and civil parish in Hertfordshire, England. The town's name is taken from one of the three villages it surrounded - all of which featured in the Domesday Book. The land used was first purchased by Quakers who had intended to farm the...
under the direction of Harold 'Doc' Keen
Harold Keen
Harold Hall "Doc" Keen was a British engineer who produced the engineering design, and oversaw the construction of, the British bombe, a codebreaking machine used in World War II to read German messages sent using the Enigma machine. He was known as "Doc" Keen because of his habit of carrying...
. Each machine was about 7 feet (2.1 m) wide, 6 in 6 in (1.98 m) tall, 2 foot (0.6096 m) deep and weighed about a ton. On the front of each bombe were 108 places where drums could be mounted. The drums were in three groups of 12 triplets. Each triplet, arranged vertically, corresponded to the three rotors of an Enigma scrambler. The bombe drums' input and output contacts went to cable connectors, allowing the bombe to be wired up according to the menu. The 'fast' drum rotated at a speed of 50.4 rpm in the first models and 120 rpm in later ones, when the time to set up and run through all 17,576 possible positions for one rotor order was about 20 minutes.
The first bombe, which was based on Turing's original design and so lacked a diagonal board, was installed at Bletchley Park on 18 March 1940 and was named "Victory". The second bombe, named "Agnus dei", later shortened to "Agnes", or "Aggie", was equipped with Welchman's diagonal board, and was installed on 8 August 1940; "Victory" was later returned to Letchworth to have a diagonal board fitted.
During 1940, 178 messages were broken on the two machines, nearly all successfully. Because of the danger of bombes at Bletchley Park being lost if there were to be a bombing raid, five bombe outstations were established, at Adstock
Adstock
Adstock is a village and civil parish about northwest of Winslow and southeast of Buckingham in the Aylesbury Vale district of Buckinghamshire. The 2001 Census recorded a parish population of 415....
, Gayhurst
Gayhurst
Gayhurst is a village and civil parish in the Borough of Milton Keynes, ceremonial Buckinghamshire in England. It is about two and a half miles NNW of Newport Pagnell....
, Wavendon
Wavendon
Wavendon is a village and civil parish in the south east of the Borough of Milton Keynes and ceremonial county of Buckinghamshire, England. The village name is an Old English language word, and means 'Wafa's hill'. In the Anglo-Saxon Chronicle in 969 the village was recorded as Wafandun. The...
, Stanmore
Stanmore
Stanmore is a suburban area of the London Borough of Harrow, in northwest London. It is situated northwest of Charing Cross. The area is home to Stanmore Hill, one of the highest points of London, high.-Toponymy:...
, and Eastcote
Eastcote
Eastcote is a suburban area established around an old village in Greater London, and is part of the London Borough of Hillingdon.In the Middle Ages, Eastcote was one of the three areas that made up the parish of Ruislip, under the name of Ascot...
. The bombe was referred to by Group Captain Winterbotham as a "Bronze Goddess" because its case was made of bronze. The devices were more prosaically described by operators as being "like great big metal bookcases".
| Type | Number of Enigma-equivalents | Mechanism | Number built |
|---|---|---|---|
| Original standard | 36 (30 in pre-production) | 3-rotor Enigma-equivalents | 73 |
| Jumbo | 36 | 3-rotor Enigma-equivalents plus an additional mechanism to check each stop and print the results (dubbed the "machine gun" because of the noise it made) | 14 |
| Mammoth | (?)36 | 4-rotor Enigma-equivalents built by Harold Keen Harold Keen Harold Hall "Doc" Keen was a British engineer who produced the engineering design, and oversaw the construction of, the British bombe, a codebreaking machine used in World War II to read German messages sent using the Enigma machine. He was known as "Doc" Keen because of his habit of carrying... with high-speed relays to sense stops |
57 |
| Cobra | 36 | 4-rotor Enigma-equivalents with an electronic sensing unit designed by C. E. Wynn-Williams of the TRE Telecommunications Research Establishment The Telecommunications Research Establishment was the main United Kingdom research and development organization for radio navigation, radar, infra-red detection for heat seeking missiles, and related work for the Royal Air Force during World War II and the years that followed. The name was... (this machine was unreliable) |
12 |
| 'New' standard | 36 | 3-rotor Enigma-equivalents (with high-speed Siemens-type sense relays) | 68 |
Production of bombes by BTM at Letchworth in wartime conditions, was nowhere near as rapid as the Americans later achieved at NCR in Dayton, Ohio.
| Year | Month | Number |
|---|---|---|
| 1941 | December | 12 |
| 1942 | December | 40 |
| 1943 | June | 72 |
| 1943 | December | 87 |
| 1944 | December | 152 |
| 1945 | May | 152 |
After World War II, some fifty bombes were retained at Eastcote
Eastcote
Eastcote is a suburban area established around an old village in Greater London, and is part of the London Borough of Hillingdon.In the Middle Ages, Eastcote was one of the three areas that made up the parish of Ruislip, under the name of Ascot...
, while the rest were destroyed. The surviving bombes were put to work, possibly on Eastern bloc
Eastern bloc
The term Eastern Bloc or Communist Bloc refers to the former communist states of Eastern and Central Europe, generally the Soviet Union and the countries of the Warsaw Pact...
ciphers. The official history of the bombe states that "some of these machines were to be stored away but others were required to run new jobs and sixteen machines were kept comparatively busy on menus. It is interesting to note that most of the jobs came up and the operating, checking and other times maintained were faster than the best times during the war periods."
A team led by John Harper conducted a 13-year project to reconstruct a working bombe. This was successful, and the reconstructed bombe can be seen at Bletchley Park
Bletchley Park
Bletchley Park is an estate located in the town of Bletchley, in Buckinghamshire, England, which currently houses the National Museum of Computing...
Museum. In March 2009 it won an Engineering Heritage Award.
Response to the Four-rotor Enigma
A program was initiated by Bletchley ParkBletchley Park
Bletchley Park is an estate located in the town of Bletchley, in Buckinghamshire, England, which currently houses the National Museum of Computing...
to design much faster bombes that could decrypt the four-rotor system in a reasonable time. There were two streams of development. One, with an electronic sensing unit, was produced by Charles Wynn-Williams
Charles Wynn-Williams
-Early life and studies:He was the elder child of William Williams, a physics teacher and later divisional inspector of schools for north and mid-Wales. His mother was Mary Ellen Wynn, known as Nell, daughter of Robert Wynn, a shopkeeper at Llanrwst. Liberal in politics and a fluent Welsh speaker,...
of the Telecommunications Research Establishment
Telecommunications Research Establishment
The Telecommunications Research Establishment was the main United Kingdom research and development organization for radio navigation, radar, infra-red detection for heat seeking missiles, and related work for the Royal Air Force during World War II and the years that followed. The name was...
(TRE) at Malvern. The other was designed by Harold Keen
Harold Keen
Harold Hall "Doc" Keen was a British engineer who produced the engineering design, and oversaw the construction of, the British bombe, a codebreaking machine used in World War II to read German messages sent using the Enigma machine. He was known as "Doc" Keen because of his habit of carrying...
at BTM
British Tabulating Machine Company
The British Tabulating Machine Company was a firm which manufactured and sold Hollerith unit record equipment and other data-processing equipment...
, Letchworth. Initial delivery was scheduled for August or September 1942.
Unlike the situation at Bletchley Park, the United States armed services did not share a combined cryptanalytical service. Indeed there was considerable rivalry between the US Army's
United States Army
The United States Army is the main branch of the United States Armed Forces responsible for land-based military operations. It is the largest and oldest established branch of the U.S. military, and is one of seven U.S. uniformed services...
facility, the Signals Intelligence Service (SIS)
Signals Intelligence Service
The Signals Intelligence Service was the United States Army codebreaking division, headquartered at Arlington Hall. It was a part of the Signal Corps so secret that outside the office of the Chief Signal officer, it did not officially exist. William Friedman began the division with three "junior...
, and that of the US Navy
United States Navy
The United States Navy is the naval warfare service branch of the United States Armed Forces and one of the seven uniformed services of the United States. The U.S. Navy is the largest in the world; its battle fleet tonnage is greater than that of the next 13 largest navies combined. The U.S...
known as OP-20-G
OP-20-G
OP-20-G or "Office of Chief Of Naval Operations , 20th Division of the Office of Naval Communications, G Section / Communications Security", was the US Navy's signals intelligence and cryptanalysis group during World War II. Its mission was to intercept, decrypt, and analyze naval communications...
. Before the US joined the war, there was collaboration with Britain, albeit with a considerable amount of caution on Britain's side because of the extreme importance of Germany and her allies not learning that its codes were being broken. Despite some worthwhile collaboration amongst the cryptanalysts, their superiors took some time to achieve a trusting relationship in which both British and American bombes were used to mutual benefit.
In February 1941, Captain Abe Sinkov and Lieutenant Leo Rosen of the US Army, and US Naval Lieutenants Robert Weeks and Prescott Currier, arrived at Bletchley Park bringing, amongst other things, a replica of the 'Purple' cipher machine for the Bletchley Park's Japanese section in Hut 7
Hut 7
Hut 7 was a wartime section of the Government Code and Cypher School in Bletchley Park tasked with the solution of Japanese naval codes such as JN4, JN11, JN40, and JN25...
. The four returned to America after ten weeks, with a naval radio direction finding
Direction finding
Direction finding refers to the establishment of the direction from which a received signal was transmitted. This can refer to radio or other forms of wireless communication...
unit and many documents including a 'paper Enigma'.
Currier later wrote:
The main response to the Four-rotor Enigma was the US Navy bombe, which was manufactured in much less constrained facilities than were available in wartime Britain.
| Year | Month | Number |
|---|---|---|
| 1943 | June | 4 |
| 1943 | December | 95 |
| 1944 | December | 160 |
| 1945 | May | 180 |
US Navy Bombe
Colonel John Tiltman, who later became Deputy Director at Bletchley Park, visited the US Navy cryptanalysis office (OP-20-GOP-20-G
OP-20-G or "Office of Chief Of Naval Operations , 20th Division of the Office of Naval Communications, G Section / Communications Security", was the US Navy's signals intelligence and cryptanalysis group during World War II. Its mission was to intercept, decrypt, and analyze naval communications...
) in April 1942 and recognised America's vital interest in deciphering U-boat traffic. The urgent need, doubts about the British engineering workload and slow progress, prompted the US to start investigating designs for a Navy bombe, based on the full blueprint
Blueprint
A blueprint is a type of paper-based reproduction usually of a technical drawing, documenting an architecture or an engineering design. More generally, the term "blueprint" has come to be used to refer to any detailed plan....
s and wiring diagrams received by US Naval Lieutenants Robert Ely and Joseph Eachus at Bletchley Park in July 1942. Funding for a full, $2 million, navy development effort was requested on 3 September 1942 and approved the following day.

Edward Travis
Sir Edward Wilfred Harry Travis KCMG CBE was a British cryptographer and intelligence officer, becoming the operational head of Bletchley Park during World War II, and later the head of GCHQ.-Career:...
, Deputy Director and Frank Birch
Francis Birch (cryptographer)
Francis Lyall Birch was a British cryptographer. He was educated at Eton and King’s College, Cambridge. He was awarded an OBE in 1919 and CMG in 1945....
, Head of the German Naval Section travelled from Bletchley Park to Washington in September 1942. With Carl Frederick Holden
Carl Frederick Holden
Carl Frederick Holden was an officer of the United States Navy who retired with the rank of Vice Admiral.Born in Bangor, Maine, Holden graduated from the United States Naval Academy at Annapolis in 1917. He saw service in World War I on destroyers based in Queenstown, Ireland. Lieutenant Commander...
, US Director of Naval Communications they established, on 2 October 1942, a UK:US accord which may have "a stronger claim than BRUSA
1943 BRUSA Agreement
The 1943 BRUSA Agreement was an agreement between the British and US governments to facilitate co-operation between the US War Department and the British Government Code and Cypher School...
to being the forerunner of the UKUSA Agreement
UK–USA Security Agreement
The United Kingdom – United States of America Agreement is a multilateral agreement for cooperation in signals intelligence among the United Kingdom, the United States, Canada, Australia, and New Zealand. It was first signed in March 1946 by the United Kingdom and the United States and later...
," being the first agreement "to establish the special Sigint relationship between the two countries," and "it set the pattern for UKUSA, in that the United States was very much the senior partner in the alliance." It established a relationship of "full collaboration" between Bletchley Park and OP-20-G.
An all electronic solution to the problem of a fast bombe was considered, but rejected for pragmatic reasons, and a contract was let with the National Cash Register Corporation
NCR Corporation
NCR Corporation is an American technology company specializing in kiosk products for the retail, financial, travel, healthcare, food service, entertainment, gaming and public sector industries. Its main products are self-service kiosks, point-of-sale terminals, automated teller machines, check...
(NCR) in Dayton, Ohio
Dayton, Ohio
Dayton is the 6th largest city in the U.S. state of Ohio and the county seat of Montgomery County, the fifth most populous county in the state. The population was 141,527 at the 2010 census. The Dayton Metropolitan Statistical Area had a population of 841,502 in the 2010 census...
. This established the United States Naval Computing Machine Laboratory
United States Naval Computing Machine Laboratory
The United States Naval Computing Machine Laboratory was a highly secret design and manufacturing site for code-breaking machinery located in Building 26 of the National Cash Register company in Dayton, Ohio and operated by the United States Navy during World War II...
. Engineering development was led by NCR's Joseph Desch
Joseph Desch
Joseph Raymond Desch was an American electrical engineer and inventor. During World War II, he was Research Director of the project to design and manufacture the US Navy version of the bombe, a cryptanalytic machine designed to read communications enciphered by the German Enigma.-Early life:Desch...
.
Alan Turing
Alan Turing
Alan Mathison Turing, OBE, FRS , was an English mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, providing a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which played a...
, who had written a memorandum to OP-20-G (probably in 1941), was seconded to the British Joint Staff Mission in Washington in December 1942, because of his exceptionally wide knowledge about the bombes and the methods of their use. He was asked to look at the bombes that were being built by NCR and at the security of certain speech cipher equipment under development at Bell Labs. He visited OP-20-G, and went to NCR in Dayton on the 21 December. He was able to show that it was not necessary to build 336 Bombes, one for each possible rotor order, by utilising techniques such as Banburismus
Banburismus
Banburismus was a cryptanalytic process developed by Alan Turing at Bletchley Park in England during the Second World War. It was used by Bletchley Park's Hut 8 to help break German Kriegsmarine messages enciphered on Enigma machines. The process used sequential conditional probability to infer...
. The initial order was scaled down to 96 machines.
The US Navy bombes used drums for the Enigma rotors in much the same way as the British bombes. They had eight Enigma-equivalents on the front and eight on the back. The fast drum rotated at 1,725 rpm
Revolutions per minute
Revolutions per minute is a measure of the frequency of a rotation. It annotates the number of full rotations completed in one minute around a fixed axis...
, 34 times the speed of the early British bombes. 'Stops' were detected electronically using thermionic valves
Vacuum tube
In electronics, a vacuum tube, electron tube , or thermionic valve , reduced to simply "tube" or "valve" in everyday parlance, is a device that relies on the flow of electric current through a vacuum...
(vacuum tubes)—mostly thyratron
Thyratron
A thyratron is a type of gas filled tube used as a high energy electrical switch and controlled rectifier. Triode, tetrode and pentode variations of the thyratron have been manufactured in the past, though most are of the triode design...
s—for the high speed circuits. When a 'stop' was found the machine over-ran as it slowed, reversed to the position found and printed it out before re-starting. The running time for a 4-rotor run was about 20 minutes, and for a 3-rotor run, about 50 seconds. Each machine was 10 feet (3 m) wide, 7 feet (2.1 m) high, 2 foot (0.6096 m) deep and weighed 2.5 tons.
The first machine was completed and tested on 3 May 1943. By 22 June, the first two machines, called 'Adam' and 'Eve' broke a particularly difficult German naval cipher, the Offizier settings for 9 and 10 June. A P Mahon, who had joined the Naval Section in Hut 8 in 1941, reported in his official 1945 "History of Hut Eight 1939-1945":
These bombes were faster, and soon more available, than the British bombes at Bletchley Park and its outstations. Consequently they were put to use for Hut 6 as well as Hut 8 work. In Alexander's "Cryptographic History of Work on German Naval Enigma", he wrote as follows.
Production was stopped in September 1944 after 121 bombes had been made. The last-manufactured US Navy bombe is on display at the US National Cryptologic Museum
National Cryptologic Museum
The National Cryptologic Museum is an American museum of cryptologic history that is affiliated with the National Security Agency . The first public museum in the U.S. Intelligence Community, NCM is located in the former Colony Seven Motel, just two blocks from the NSA headquarters at Fort...
. Jack Ingram, former Curator of the museum, describes being told of the existence of a second bombe and searching for it but not finding it whole. Whether it remains in storage in pieces, waiting to be discovered, or no longer exists, is unknown.
US Army Bombe
The US Army Bombe was physically very different from the British and US Navy bombes. A contract was signed with Bell LabsBell Labs
Bell Laboratories is the research and development subsidiary of the French-owned Alcatel-Lucent and previously of the American Telephone & Telegraph Company , half-owned through its Western Electric manufacturing subsidiary.Bell Laboratories operates its...
on 30 September 1942. The machine was designed to analyse 3-rotor, not 4-rotor traffic. It did not use drums to represent the Enigma rotors, using instead telephone-type relays. It could, however, handle one problem that the bombes with drums could not. The set of ten bombes consisted of a total of 144 Enigma-equivalents, each mounted on a rack approximately 7 feet (2.1 m) long 8 feet (2.4 m) high and 6 inches (152.4 mm) wide. There were 12 control stations which could allocate any of the Enigma-equivalents into the desired configuration by means of plugboards. Rotor order changes did not require the mechanical process of changing drums, but was achieved in about half a minute by means of push buttons. A 3-rotor run took about 10 minutes.
See also
- Cryptanalysis of the EnigmaCryptanalysis of the EnigmaCryptanalysis of the Enigma enabled the western Allies in World War II to read substantial amounts of secret Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military intelligence which, along with that from other decrypted Axis radio...
- Colossus computerColossus computerNot to be confused with the fictional computer of the same name in the movie Colossus: The Forbin Project.Colossus was the world's first electronic, digital, programmable computer. Colossus and its successors were used by British codebreakers to help read encrypted German messages during World War II...
- Heath RobinsonHeath Robinson (codebreaking machine)Heath Robinson was a machine used by British codebreakers at Bletchley Park during World War II to solve messages in the German teleprinter cipher used by the Lorenz SZ40/42 cipher machine; the cipher and machine were called "Tunny" by the codebreakers, who named different German teleprinter...
- Jean Valentine (bombe operator)Jean Valentine (bombe operator)Jean Valentine was an operator of the bombe decryption device in Hut 11 at Bletchley Park in England, designed by Alan Turing and others during World War II. She was a member of the "Wrens" . She was one of a number of women that worked at Bletchley Park. During this time, she lived in Steeple ...
External links
- A bombe simulator (in Javascript)
- Museum of Learning - Bombe: The Challenge Of The Four Rotor Enigma Machine
- Enigma and the Turing Bombe by N. Shaylor, April 17, 1997. Includes a simulator (a Java appletJava appletA Java applet is an applet delivered to users in the form of Java bytecode. Java applets can run in a Web browser using a Java Virtual Machine , or in Sun's AppletViewer, a stand-alone tool for testing applets...
and CC (programming language)C is a general-purpose computer programming language developed between 1969 and 1973 by Dennis Ritchie at the Bell Telephone Laboratories for use with the Unix operating system....
) - Dayton Codebreakers — documentary on the US Navy's Bombe; information on Desch, personnel of the US Naval Computing Machine Laboratory.

