
Digest access authentication
Encyclopedia
Digest access authentication is one of the agreed upon methods a web server
can use to negotiate credentials with a user's web browser
. It uses encryption
to send the password
over the network which is safer than the Basic access authentication that sends plaintext
.
Technically digest authentication is an application of MD5
cryptographic hashing with usage of nonce
values to discourage cryptanalysis
. It uses the HTTP
protocol.
value. The authentication response is formed as follows (where HA1, HA2, A1, A2 are names of string variables):
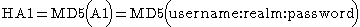
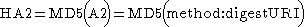
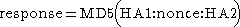
RFC 2069 was later replaced by RFC 2617 (HTTP Authentication: Basic and Digest Access Authentication). RFC 2617 introduced a number of optional security enhancements to digest authentication; "quality of protection" (qop), nonce counter incremented by client, and a client-generated random nonce. These enhancements are designed to protect against, for example, chosen-plaintext attack
cryptanalysis
.
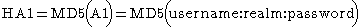
If the qop directive's value is "auth" or is unspecified, then HA2 is
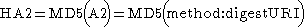
If the qop directive's value is "auth-int" , then HA2 is
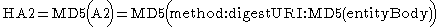
If the qop directive's value is "auth" or "auth-int" , then compute the response as follows:
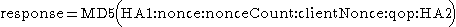
If the qop directive is unspecified, then compute the response as follows:
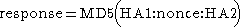
The above shows that when qop is not specified, the simpler RFC 2069 standard is followed.
", meaning that it should be difficult to determine the original input when only the output is known. If the password itself is too simple, however, then it may be possible to test all possible inputs and find a matching output (a brute-force attack) – perhaps aided by a dictionary or suitable look-up list.
The HTTP scheme was designed at CERN
in 1993 and does not incorporate subsequent improvements in authentication systems, such as the development of keyed-hash message authentication code (HMAC
). Although the cryptographic
construction that is used is based on the MD5
hash function, collision attack
s were in 2004 generally believed to not affect applications where the plaintext (i.e. password) is not known.
However, claims in 2006 (Kim, Biryukov2, Preneel, Hong, "On the Security of HMAC and NMAC Based on HAVAL MD4 MD5 SHA-0 and SHA-1") cause some doubt over other MD5 applications as well. So far, however, MD5 collision attacks have not been shown to pose a threat to digest authentication, and the RFC 2617 allows servers to implement mechanisms to detect some collision and replay attacks.
..." (RFC2617).
Some of the security strengths of HTTP digest authentication are:
or Kerberos authentication.
In terms of security, there are several drawbacks with digest access authentication:
Weak cleartext protocols are also often in use:
These weak cleartext protocols used together with HTTPS network encryption resolve many of the threats that digest access authentication is designed to prevent.
and Konqueror
web browser
s are known to support "auth-int" (authentication with integrity protection). Although the specification mentions HTTP version 1.1, the scheme can be successfully added to a version 1.0 server, as shown here.
This typical transaction consists of the following steps.
Note: A client may already have the required username and password without needing to prompt the user, e.g. if they have previously been stored by a web browser.
----
Client request (no authentication):
GET /dir/index.html HTTP/1.0
Host: localhost
(followed by a new line
, in the form of a carriage return
followed by a line feed).
Server response:
HTTP/1.0 401 Unauthorized
Server: HTTPd/0.9
Date: Sun, 10 Apr 2005 20:26:47 GMT
WWW-Authenticate: Digest realm="testrealm@host.com",
qop="auth,auth-int",
nonce="dcd98b7102dd2f0e8b11d0f600bfb0c093",
opaque="5ccc069c403ebaf9f0171e9517f40e41"
Content-Type: text/html
Content-Length: 311
"http://www.w3.org/TR/1999/REC-html401-19991224/loose.dtd">
Error
Client request (username "Mufasa", password "Circle Of Life"):
GET /dir/index.html HTTP/1.0
Host: localhost
Authorization: Digest username="Mufasa",
realm="testrealm@host.com",
nonce="dcd98b7102dd2f0e8b11d0f600bfb0c093",
uri="/dir/index.html",
qop=auth,
nc=00000001,
cnonce="0a4f113b",
response="6629fae49393a05397450978507c4ef1",
opaque="5ccc069c403ebaf9f0171e9517f40e41"
(followed by a blank line, as before).
Server response:
HTTP/1.0 200 OK
Server: HTTPd/0.9
Date: Sun, 10 Apr 2005 20:27:03 GMT
Content-Type: text/html
Content-Length: 7984
(followed by a blank line and HTML text of the restricted page).
----
The "response" value is calculated in three steps, as follows. Where values are combined, they are delimited
by colon
symbols.
Since the server has the same information as the client, the response can be checked by performing the same calculation. In the example given above the result is formed as follows, where
Completing the example given in RFC 2617 gives the following results for each step.
HA1 = MD5( "Mufasa:testrealm@host.com:Circle Of Life" )
= 939e7578ed9e3c518a452acee763bce9
HA2 = MD5( "GET:/dir/index.html" )
= 39aff3a2bab6126f332b942af96d3366
Response = MD5( "939e7578ed9e3c518a452acee763bce9:\
dcd98b7102dd2f0e8b11d0f600bfb0c093:\
00000001:0a4f113b:auth:\
39aff3a2bab6126f332b942af96d3366" )
= 6629fae49393a05397450978507c4ef1
At this point the client may make another request, reusing the server nonce value (the server only issues a new nonce for each "401" response) but providing a new client nonce (cnonce). For subsequent requests, the hexadecimal request counter (nc) must be greater than the last value it used – otherwise an attacker could simply "replay
" an old request with the same credentials. It is up to the server to ensure that the counter increases for each of the nonce values that it has issued, rejecting any bad requests appropriately. Obviously changing the method, URI and/or counter value will result in a different response value.
The server should remember nonce values that it has recently generated. It may also remember when each nonce value was issued, expiring them after a certain amount of time. If an expired value is used, the server should respond with the "401" status code and add
The server does not need to keep any expired nonce values – it can simply assume that any unrecognised values have expired. It is also possible for the server to only allow each nonce value to be returned once, although this forces the client to repeat every request. Note that expiring a server nonce immediately will not work, as the client would never get a chance to use it.
uses basically the same digest authentication algorithm. It is specified by RFC 3261.
Web server
Web server can refer to either the hardware or the software that helps to deliver content that can be accessed through the Internet....
can use to negotiate credentials with a user's web browser
Web browser
A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier and may be a web page, image, video, or other piece of content...
. It uses encryption
Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
to send the password
Password
A password is a secret word or string of characters that is used for authentication, to prove identity or gain access to a resource . The password should be kept secret from those not allowed access....
over the network which is safer than the Basic access authentication that sends plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
.
Technically digest authentication is an application of MD5
MD5
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
cryptographic hashing with usage of nonce
Cryptographic nonce
In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
values to discourage cryptanalysis
Cryptanalysis
Cryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key...
. It uses the HTTP
Hypertext Transfer Protocol
The Hypertext Transfer Protocol is a networking protocol for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web....
protocol.
Overview
Digest access authentication was originally specified by RFC 2069 (An Extension to HTTP: Digest Access Authentication). RFC 2069 specifies roughly a traditional digest authentication scheme with security maintained by a server-generated nonceCryptographic nonce
In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
value. The authentication response is formed as follows (where HA1, HA2, A1, A2 are names of string variables):
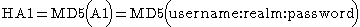
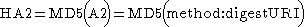
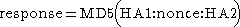
RFC 2069 was later replaced by RFC 2617 (HTTP Authentication: Basic and Digest Access Authentication). RFC 2617 introduced a number of optional security enhancements to digest authentication; "quality of protection" (qop), nonce counter incremented by client, and a client-generated random nonce. These enhancements are designed to protect against, for example, chosen-plaintext attack
Chosen-plaintext attack
A chosen-plaintext attack is an attack model for cryptanalysis which presumes that the attacker has the capability to choose arbitrary plaintexts to be encrypted and obtain the corresponding ciphertexts. The goal of the attack is to gain some further information which reduces the security of the...
cryptanalysis
Cryptanalysis
Cryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key...
.
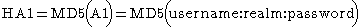
If the qop directive's value is "auth" or is unspecified, then HA2 is
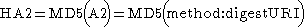
If the qop directive's value is "auth-int" , then HA2 is
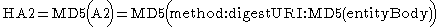
If the qop directive's value is "auth" or "auth-int" , then compute the response as follows:
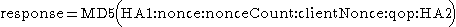
If the qop directive is unspecified, then compute the response as follows:
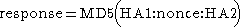
The above shows that when qop is not specified, the simpler RFC 2069 standard is followed.
Impact of MD5 security on digest authentication
The MD5 calculations used in HTTP digest authentication is intended to be "one wayOne-way function
In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here "easy" and "hard" are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems...
", meaning that it should be difficult to determine the original input when only the output is known. If the password itself is too simple, however, then it may be possible to test all possible inputs and find a matching output (a brute-force attack) – perhaps aided by a dictionary or suitable look-up list.
The HTTP scheme was designed at CERN
CERN
The European Organization for Nuclear Research , known as CERN , is an international organization whose purpose is to operate the world's largest particle physics laboratory, which is situated in the northwest suburbs of Geneva on the Franco–Swiss border...
in 1993 and does not incorporate subsequent improvements in authentication systems, such as the development of keyed-hash message authentication code (HMAC
HMAC
In cryptography, HMAC is a specific construction for calculating a message authentication code involving a cryptographic hash function in combination with a secret key. As with any MAC, it may be used to simultaneously verify both the data integrity and the authenticity of a message...
). Although the cryptographic
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
construction that is used is based on the MD5
MD5
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
hash function, collision attack
Collision attack
In cryptography, a collision attack on a cryptographic hash tries to find two arbitrary inputs that will produce the same hash value, i.e. a hash collision...
s were in 2004 generally believed to not affect applications where the plaintext (i.e. password) is not known.
However, claims in 2006 (Kim, Biryukov2, Preneel, Hong, "On the Security of HMAC and NMAC Based on HAVAL MD4 MD5 SHA-0 and SHA-1") cause some doubt over other MD5 applications as well. So far, however, MD5 collision attacks have not been shown to pose a threat to digest authentication, and the RFC 2617 allows servers to implement mechanisms to detect some collision and replay attacks.
Advantages
HTTP digest authentication is designed to be more secure than traditional digest authentication schemes; e.g., "significantly stronger than (e.g.) CRAM-MD5CRAM-MD5
In cryptography, CRAM-MD5 is achallenge-response authentication mechanism defined in RFC 2195 based on theHMAC-MD5 MACalgorithm...
..." (RFC2617).
Some of the security strengths of HTTP digest authentication are:
- The password is not used directly in the digest, but rather HA1 = MD5(username:realm:password). This allows some implementations (e.g. JBossJBossJBoss Application Server is an open-source Java EE-based application server. An important distinction for this class of software is that it not only implements a server that runs on Java, but it actually implements the Java EE part of Java...
DIGESTAuth) to store HA1 rather than the cleartext password. - Client nonceCryptographic nonceIn security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
was introduced in RFC2617, which allows the client to prevent Chosen-plaintext attackChosen-plaintext attackA chosen-plaintext attack is an attack model for cryptanalysis which presumes that the attacker has the capability to choose arbitrary plaintexts to be encrypted and obtain the corresponding ciphertexts. The goal of the attack is to gain some further information which reduces the security of the...
s (which otherwise makes e.g. rainbow tableRainbow tableA rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering the plaintext password, up to a certain length consisting of a limited set of characters. It is a form of time-memory tradeoff, using less...
s a threat to digest authentication schemes). - Server nonce is allowed to contain timestamps. Therefore the server may inspect nonce attributes submitted by clients, to prevent replay attacks.
- Server is also allowed to maintain a list of recently issued or used server nonce values to prevent reuse.
Disadvantages
Digest access authentication is intended as a security trade-off. It is intended to replace unencrypted HTTP basic access authentication. It is not, however, intended to replace strong authentication protocols, such as public-keyPublic-key cryptography
Public-key cryptography refers to a cryptographic system requiring two separate keys, one to lock or encrypt the plaintext, and one to unlock or decrypt the cyphertext. Neither key will do both functions. One of these keys is published or public and the other is kept private...
or Kerberos authentication.
In terms of security, there are several drawbacks with digest access authentication:
- Many of the security options in RFC 2617 are optional. If quality-of-protection (qop) is not specified by the server, the client will operate in a security-reduced legacy RFC 2069 mode.
- Digest access authentication is vulnerable to a man-in-the-middle (MitM) attackMan-in-the-middle attackIn cryptography, the man-in-the-middle attack , bucket-brigade attack, or sometimes Janus attack, is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other...
. For example, a MitM attacker could tell clients to use basic access authentication or legacy RFC2069 digest access authentication mode. To extend this further, digest access authentication provides no mechanism for clients to verify the server's identity. - Some servers require passwords to be stored using reversible encryption. However, it is possible to instead store the digested value of the username, realm, and password.
Alternative authentication protocols
Some strong authentication protocols for web-based applications include:- Public key authentication (usually implemented with HTTPSHttpsHypertext Transfer Protocol Secure is a combination of the Hypertext Transfer Protocol with SSL/TLS protocol to provide encrypted communication and secure identification of a network web server...
/ SSL client certificates). - Kerberos or SPNEGOSPNEGOSPNEGO is a GSSAPI "pseudo mechanism" that is used to negotiate one of a number of possible real mechanisms....
authentication, primarily employed by Microsoft IIS running configured for Integrated Windows AuthenticationIntegrated Windows AuthenticationIntegrated Windows Authentication is a term associated with Microsoft products that refers to the SPNEGO, Kerberos, and NTLMSSP authentication protocols with respect to SSPI functionality introduced with Microsoft Windows 2000 and included with later Windows NT-based operating systems...
(IWA). - Secure Remote Password protocolSecure remote password protocolThe Secure Remote Password protocol is a password-authenticated key agreement protocol.- Overview :The SRP protocol has a number of desirable properties: it allows a user to authenticate themselves to a server, it is resistant to dictionary attacks mounted by an eavesdropper, and it does not...
(preferably within the HTTPSHttpsHypertext Transfer Protocol Secure is a combination of the Hypertext Transfer Protocol with SSL/TLS protocol to provide encrypted communication and secure identification of a network web server...
/ TLSTransport Layer SecurityTransport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
layer).
Weak cleartext protocols are also often in use:
- Basic access authentication scheme
- HTTP+HTML form-based authentication
These weak cleartext protocols used together with HTTPS network encryption resolve many of the threats that digest access authentication is designed to prevent.
Example with explanation
The following example was originally given in RFC 2617 and is expanded here to show the full text expected for each request and response. Note that only the "auth" (authentication) quality of protection code is covered – at the time of writing, only the OperaOpera (web browser)
Opera is a web browser and Internet suite developed by Opera Software with over 200 million users worldwide. The browser handles common Internet-related tasks such as displaying web sites, sending and receiving e-mail messages, managing contacts, chatting on IRC, downloading files via BitTorrent,...
and Konqueror
Konqueror
Not to be confused with the Conqueror web browser.Konqueror is a web browser and file manager that provides file-viewer functionality for file systems such as local files, files on a remote ftp server and files in a disk image. It is a core part of the KDE desktop environment...
web browser
Web browser
A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier and may be a web page, image, video, or other piece of content...
s are known to support "auth-int" (authentication with integrity protection). Although the specification mentions HTTP version 1.1, the scheme can be successfully added to a version 1.0 server, as shown here.
This typical transaction consists of the following steps.
- The client asks for a page that requires authentication but does not provide a username and password. Typically this is because the user simply entered the address or followed a linkHyperlinkIn computing, a hyperlink is a reference to data that the reader can directly follow, or that is followed automatically. A hyperlink points to a whole document or to a specific element within a document. Hypertext is text with hyperlinks...
to the page. - The server responds with the 401 "client-error" response code, providing the authentication realm and a randomly-generated, single-use value called a nonceCryptographic nonceIn security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
. - At this point, the client will present the authentication realm (typically a description of the computer or system being accessed) to the user and prompt for a username and password. The user may decide to cancel at this point.
- Once a username and password have been supplied, the client re-sends the same request but adds an authentication header that includes the response code.
- In this example, the server accepts the authentication and the page is returned. If the username is invalid and/or the password is incorrect, the server might return the "401" response code and the client would prompt the user again.
Note: A client may already have the required username and password without needing to prompt the user, e.g. if they have previously been stored by a web browser.
----
Client request (no authentication):
GET /dir/index.html HTTP/1.0
Host: localhost
(followed by a new line
Newline
In computing, a newline, also known as a line break or end-of-line marker, is a special character or sequence of characters signifying the end of a line of text. The name comes from the fact that the next character after the newline will appear on a new line—that is, on the next line below the...
, in the form of a carriage return
Carriage return
Carriage return, often shortened to return, refers to a control character or mechanism used to start a new line of text.Originally, the term "carriage return" referred to a mechanism or lever on a typewriter...
followed by a line feed).
Server response:
HTTP/1.0 401 Unauthorized
Server: HTTPd/0.9
Date: Sun, 10 Apr 2005 20:26:47 GMT
WWW-Authenticate: Digest realm="testrealm@host.com",
qop="auth,auth-int",
nonce="dcd98b7102dd2f0e8b11d0f600bfb0c093",
opaque="5ccc069c403ebaf9f0171e9517f40e41"
Content-Type: text/html
Content-Length: 311
"http://www.w3.org/TR/1999/REC-html401-19991224/loose.dtd">
401 Unauthorized.
Client request (username "Mufasa", password "Circle Of Life"):
GET /dir/index.html HTTP/1.0
Host: localhost
Authorization: Digest username="Mufasa",
realm="testrealm@host.com",
nonce="dcd98b7102dd2f0e8b11d0f600bfb0c093",
uri="/dir/index.html",
qop=auth,
nc=00000001,
cnonce="0a4f113b",
response="6629fae49393a05397450978507c4ef1",
opaque="5ccc069c403ebaf9f0171e9517f40e41"
(followed by a blank line, as before).
Server response:
HTTP/1.0 200 OK
Server: HTTPd/0.9
Date: Sun, 10 Apr 2005 20:27:03 GMT
Content-Type: text/html
Content-Length: 7984
(followed by a blank line and HTML text of the restricted page).
----
The "response" value is calculated in three steps, as follows. Where values are combined, they are delimited
Delimiter
A delimiter is a sequence of one or more characters used to specify the boundary between separate, independent regions in plain text or other data streams. An example of a delimiter is the comma character, which acts as a field delimiter in a sequence of comma-separated values.Delimiters represent...
by colon
Colon (punctuation)
The colon is a punctuation mark consisting of two equally sized dots centered on the same vertical line.-Usage:A colon informs the reader that what follows the mark proves, explains, or lists elements of what preceded the mark....
symbols.
- The MD5 hash of the combined username, authentication realm and password is calculated. The result is referred to as HA1.
- The MD5 hash of the combined method and digest URIUniform Resource IdentifierIn computing, a uniform resource identifier is a string of characters used to identify a name or a resource on the Internet. Such identification enables interaction with representations of the resource over a network using specific protocols...
is calculated, e.g. of"GET"and"/dir/index.html". The result is referred to as HA2. - The MD5 hash of the combined HA1 result, server nonce (nonce), request counter (nc), client nonce (cnonce), quality of protection code (qop) and HA2 result is calculated. The result is the "response" value provided by the client.
Since the server has the same information as the client, the response can be checked by performing the same calculation. In the example given above the result is formed as follows, where
MD5 represents a function used to calculate an MD5 hash, backslashes represent a continuation and the quotes shown are not used in the calculation.Completing the example given in RFC 2617 gives the following results for each step.
HA1 = MD5( "Mufasa:testrealm@host.com:Circle Of Life" )
= 939e7578ed9e3c518a452acee763bce9
HA2 = MD5( "GET:/dir/index.html" )
= 39aff3a2bab6126f332b942af96d3366
Response = MD5( "939e7578ed9e3c518a452acee763bce9:\
dcd98b7102dd2f0e8b11d0f600bfb0c093:\
00000001:0a4f113b:auth:\
39aff3a2bab6126f332b942af96d3366" )
= 6629fae49393a05397450978507c4ef1
At this point the client may make another request, reusing the server nonce value (the server only issues a new nonce for each "401" response) but providing a new client nonce (cnonce). For subsequent requests, the hexadecimal request counter (nc) must be greater than the last value it used – otherwise an attacker could simply "replay
Replay attack
A replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and retransmits it, possibly as part of a masquerade attack by IP packet...
" an old request with the same credentials. It is up to the server to ensure that the counter increases for each of the nonce values that it has issued, rejecting any bad requests appropriately. Obviously changing the method, URI and/or counter value will result in a different response value.
The server should remember nonce values that it has recently generated. It may also remember when each nonce value was issued, expiring them after a certain amount of time. If an expired value is used, the server should respond with the "401" status code and add
stale=TRUE to the authentication header, indicating that the client should re-send with the new nonce provided, without prompting the user for another username and password.The server does not need to keep any expired nonce values – it can simply assume that any unrecognised values have expired. It is also possible for the server to only allow each nonce value to be returned once, although this forces the client to repeat every request. Note that expiring a server nonce immediately will not work, as the client would never get a chance to use it.
SIP digest authentication
SIPSession Initiation Protocol
The Session Initiation Protocol is an IETF-defined signaling protocol widely used for controlling communication sessions such as voice and video calls over Internet Protocol . The protocol can be used for creating, modifying and terminating two-party or multiparty sessions...
uses basically the same digest authentication algorithm. It is specified by RFC 3261.
Browser implementation
Most browsers have substantially implemented the spec, some barring certain features such as auth-int checking or the MD5-sess algorithm. If the server requires that these optional features be handled, clients may not be able to authenticate (though note mod_auth_digest for Apache does not fully implement RFC 2617 either).- AmayaAmaya (web browser)Amaya is a free and open source WYSIWYG web authoring tool with browsing abilities, created by a structured editor project at the INRIA, a French national research institution, and later adopted by the World Wide Web Consortium . Amaya is used as a testbed for web standards and replaced the Arena...
- GeckoGecko (layout engine)Gecko is a free and open source layout engine used in many applications developed by Mozilla Foundation and the Mozilla Corporation , as well as in many other open source software projects....
-based: (not including auth-int: https://bugzilla.mozilla.org/show_bug.cgi?id=168942)- Mozilla Application SuiteMozilla Application SuiteThe Mozilla Application Suite is a cross-platform integrated Internet suite. Its development was initiated by Netscape Communications Corporation, before their acquisition by AOL. It is based on the source code of Netscape Communicator...
- Mozilla FirefoxMozilla FirefoxMozilla Firefox is a free and open source web browser descended from the Mozilla Application Suite and managed by Mozilla Corporation. , Firefox is the second most widely used browser, with approximately 25% of worldwide usage share of web browsers...
- Netscape 7+
- Mozilla Application Suite
- iCab 3.0.3+ICabiCab is a web browser for the Macintosh by Alexander Clauss, derived from Crystal Atari Browser for Atari TOS compatible computers. It is the most recently actively developed browser for 68k-based Macintoshes that features tabbed browsing and one of a very few browsers that was still updated in...
- KHTMLKHTMLKHTML is the HTML layout engine developed by the KDE project. It is the engine used by the Konqueror web browser. A forked version of KHTML called WebKit is used by several web browsers, among them Safari and Google Chrome...
- and WebKitWebKitWebKit is a layout engine designed to allow web browsers to render web pages. WebKit powers Google Chrome and Apple Safari and by October 2011 held over 33% of the browser market share between them. It is also used as the basis for the experimental browser included with the Amazon Kindle ebook...
-based: (not including auth-int http://www.vsecurity.com/download/papers/HTTPDigestIntegrity.pdf)- iCabICabiCab is a web browser for the Macintosh by Alexander Clauss, derived from Crystal Atari Browser for Atari TOS compatible computers. It is the most recently actively developed browser for 68k-based Macintoshes that features tabbed browsing and one of a very few browsers that was still updated in...
4 - KonquerorKonquerorNot to be confused with the Conqueror web browser.Konqueror is a web browser and file manager that provides file-viewer functionality for file systems such as local files, files on a remote ftp server and files in a disk image. It is a core part of the KDE desktop environment...
- Google ChromeGoogle ChromeGoogle Chrome is a web browser developed by Google that uses the WebKit layout engine. It was first released as a beta version for Microsoft Windows on September 2, 2008, and the public stable release was on December 11, 2008. The name is derived from the graphical user interface frame, or...
- SafariSafari (web browser)Safari is a web browser developed by Apple Inc. and included with the Mac OS X and iOS operating systems. First released as a public beta on January 7, 2003 on the company's Mac OS X operating system, it became Apple's default browser beginning with Mac OS X v10.3 "Panther". Safari is also the...
- iCab
- TasmanTasman (layout engine)Tasman was a layout engine developed by Microsoft for inclusion in the Macintosh version of Internet Explorer 5. Tasman was an attempt to improve support for web standards, as defined by the World Wide Web Consortium. At the time of its release, Tasman was seen as the layout engine with the best...
-based:- Internet Explorer for MacInternet Explorer for MacInternet Explorer for Mac was a proprietary web browser developed by Microsoft for the Macintosh platform. Initial versions were developed from the same code base as Internet Explorer for Windows...
- Internet Explorer for Mac
- TridentTrident (layout engine)Trident is the name of the layout engine for the Microsoft Windows version of Internet Explorer.It was first introduced with the release of Internet Explorer version 4.0 in October 1997; it has been steadily upgraded and remains in use today...
-based:- Internet Explorer 7+Internet Explorer 7Windows Internet Explorer 7 is a web browser released by Microsoft in October 2006. Internet Explorer 7 is part of a long line of versions of Internet Explorer and was the first major update to the browser in more than 5 years...
(not including auth-int)
- Internet Explorer 7+
- PrestoPresto (layout engine)Presto is the layout engine for later versions of the Opera web browser . After several public betas and technical previews, it was released on January 28, 2003 in Opera 7 for Windows, and as of Opera 11 it is still in use. Presto is dynamic: the page or parts of it can be re-rendered in response...
-based:- OperaOpera (web browser)Opera is a web browser and Internet suite developed by Opera Software with over 200 million users worldwide. The browser handles common Internet-related tasks such as displaying web sites, sending and receiving e-mail messages, managing contacts, chatting on IRC, downloading files via BitTorrent,...
- Opera MobileOpera MobileOpera Mobile is a web browser for smartphones and PDA's developed by the Opera Software company. The first version was released in 2000 for the Psion Series 7 and netBook. Today, it is available for a variety of devices that run on Android, S60, Windows Mobile, Maemo , and MeeGo...
- Opera MiniOpera MiniOpera Mini is a web browser designed primarily for mobile phones, smartphones and personal digital assistants. Until version 4 it used the Java ME platform, requiring the mobile device to run Java ME applications. From version 5 it is also available as a native application for Android, iOS, Symbian...
- Nintendo DS BrowserNintendo DS BrowserThe Nintendo DS Browser is a version of the Opera web browser for use on the Nintendo DS, developed by Opera Software and Nintendo. The Nintendo DS Browser comes in separate versions for the Nintendo DS and the Nintendo DS Lite; this is due to differing physical size requirements for the memory...
- Nokia 770 Browser
- Sony Mylo 1Mylo (Sony)My Life Online is a device created and marketed by Sony for portable instant messaging and other Internet-based communications, browsing Internet web sites and playback and sharing of media files. The pocket-sized, tablet-shaped handheld device has a screen which slides up to reveal a QWERTY...
's Browser - WiiWiiThe Wii is a home video game console released by Nintendo on November 19, 2006. As a seventh-generation console, the Wii primarily competes with Microsoft's Xbox 360 and Sony's PlayStation 3. Nintendo states that its console targets a broader demographic than that of the two others...
Internet Channel Browser
- Opera

