Session Initiation Protocol
Encyclopedia
The Session Initiation Protocol (SIP) is an IETF-defined signaling
protocol
widely used for controlling communication sessions such as voice and video
calls over Internet Protocol
(IP). The protocol can be used for creating, modifying and terminating two-party (unicast
) or multiparty (multicast
) sessions. Sessions may consist of one or several media streams
.
Other SIP applications include video conferencing, streaming multimedia distribution, instant messaging
, presence information
, file transfer
and online game
s.
The SIP protocol is an Application Layer
protocol designed to be independent of the underlying Transport Layer
; it can run on Transmission Control Protocol
(TCP), User Datagram Protocol
(UDP), or Stream Control Transmission Protocol
(SCTP). It is a text-based protocol, incorporating many elements of the Hypertext Transfer Protocol
(HTTP) and the Simple Mail Transfer Protocol
(SMTP).
and Mark Handley
in 1996. In November 2000, SIP was accepted as a 3GPP
signaling protocol and permanent element of the IP Multimedia Subsystem
(IMS) architecture for IP-based streaming multimedia services in cellular systems. The latest version of the specification is RFC 3261 from the IETF Network Working Group published in June 2002.
The free software community
started to provide more and more of the SIP technology required to build both end points as well as proxy and registrar servers leading to a commodification of the technology, which has accelerated global adoption. As an example, the open source community at SIPfoundry
actively develops a variety of SIP stacks, client applications and SDKs, in addition to entire private branch exchange (IP PBX
) solutions that compete in the market against mostly proprietary
IP PBX
implementations from established vendors.
The National Institute of Standards and Technology
(NIST), Advanced Networking Technologies Division provides a public domain implementation of the JAVA Standard for SIP which serves as a reference implementation
for the standard. The stack can work in proxy server or user agent scenarios and has been used in numerous commercial and research projects. It supports RFC 3261 in full and a number of extension RFCs including RFC 3265 (Subscribe / Notify) and RFC 3262 (Provisional Reliable Responses) etc.
SIP works in concert with several other protocols and is only involved in the signaling portion of a communication session. SIP clients typically use TCP or UDP on port numbers 5060 and/or 5061 to connect to SIP servers and other SIP endpoints. Port 5060 is commonly used for non-encrypted signaling traffic whereas port 5061 is typically used for traffic encrypted with Transport Layer Security
(TLS). SIP is primarily used in setting up and tearing down voice or video calls. It also allows modification of existing calls. The modification can involve changing addresses or ports
, inviting more participants, and adding or deleting media streams. SIP has also found applications in messaging applications, such as instant messaging, and event subscription and notification. There are a large number of SIP-related Internet Engineering Task Force
(IETF) documents that define behavior for such applications. The voice and video stream communications in SIP applications are carried over another application protocol, the Real-time Transport Protocol
(RTP). Parameters (port numbers, protocols, codecs) for these media streams are defined and negotiated using the Session Description Protocol
(SDP) which is transported in the SIP packet body.
A motivating goal for SIP was to provide a signaling and call setup protocol for IP-based communications that can support a superset of the call processing functions and features present in the public switched telephone network
(PSTN). SIP by itself does not define these features; rather, its focus is call-setup and signaling. The features that permit familiar telephone-like operations: dialing a number, causing a phone to ring, hearing ringback tones or a busy signal - are performed by proxy servers and user agents. Implementation and terminology are different in the SIP world but to the end-user, the behavior is similar.
SIP-enabled telephony networks can also implement many of the more advanced call processing features present in Signaling System 7 (SS7), though the two protocols themselves are very different. SS7 is a centralized protocol, characterized by a complex central network architecture and dumb endpoints (traditional telephone handsets). SIP is a peer-to-peer
protocol, thus it requires only a simple (and thus scalable) core network with intelligence distributed to the network edge, embedded in endpoints (terminating devices built in either hardware or software). SIP features are implemented in the communicating endpoints (i.e. at the edge of the network) contrary to traditional SS7 features, which are implemented in the network.
Although several other VoIP signaling protocols exist (such as BICC, H.323
, MGCP, MEGACO), SIP is distinguished by its proponents for having roots in the IP community rather than the telecommunications industry. SIP has been standardized and governed primarily by the IETF, while other protocols, such as H.323, have traditionally been associated with the International Telecommunication Union
(ITU).
The first proposed standard version (SIP 1.0) was defined by RFC 2543. This version of the protocol was further refined to version 2.0 and clarified in RFC 3261, although some implementations are still relying on the older definitions.
A SIP phone is a SIP user agent that provides the traditional call functions of a telephone, such as dial, answer, reject, hold/unhold, and call transfer.
SIP phones may be implemented as a hardware device or as a softphone
. As vendors increasingly implement SIP as a standard telephony platform, often driven by 4G
efforts, the distinction between hardware-based and software-based SIP phones is being blurred and SIP elements are implemented in the basic firmware functions of many IP-capable devices. Examples are devices from Nokia
and Research in Motion
.
Each resource of a SIP network, such as a User Agent or a voicemail box, is identified by a Uniform Resource Identifier
(URI), based on the general standard syntax also used in Web services and e-mail. A typical SIP URI is of the form:
used for SIP is
is required, the scheme
(TLS).
In SIP, as in HTTP, the user agent
may identify itself using a message header field 'User-Agent', containing a text description of the software/hardware/product involved. The User-Agent field is sent in request messages, which means that the receiving SIP server can see this information. SIP network elements sometimes store this information, and it can be useful in diagnosing SIP compatibility problems.
SIP also defines server network elements. Although two SIP endpoints can communicate without any intervening SIP infrastructure, which is why the protocol is described as peer-to-peer, this approach is often impractical for a public service. RFC 3261 defines these server elements.
Proxy server: An intermediary entity that acts as both a server and a client for the purpose of making requests on behalf of other clients. A proxy server primarily plays the role of routing, which means its job is to ensure that a request is sent to another entity "closer" to the targeted user. Proxies are also useful for enforcing policy (for example, making sure a user is allowed to make a call). A proxy interprets, and, if necessary, rewrites specific parts of a request message before forwarding it.
Registrar: A server that accepts REGISTER requests and places the information it receives in those requests into the location service for the domain it handles which registers one or more IP addresses to a certain SIP URI
, indicated by the sip: scheme, although other protocol schemes are possible (such as tel:). More than one user agent
can register at the same URI, with the result that all registered user agents will receive a call to the SIP URI.
Redirect server: A user agent server that generates 3xx (Redirection) responses to requests it receives, directing the client to contact an alternate set of URIs. The redirect server allows proxy servers to direct SIP session invitations to external domains.
Other SIP-related network elements include.
Session border controller
s (SBC): Serve as middle boxes between UA and SIP server for various types of functions, including network topology hiding, and assistance in NAT traversal
.
gateways
: Devices that exist at the edge between a SIP network and other networks (as a phone network).
For SIP requests, RFC 3261 defines the following methods:
The SIP response types defined in RFC 3261 fall in one of the following categories:
Transactions are further categorized as either Invite or Non-Invite. Invite transactions differ in that they can establish a long-running conversation, referred to as a Dialog in SIP, and so include an acknowledgment (ACK) of any non-failing final response (e.g. 200 OK).
Because of these transactional mechanisms, SIP can make use of un-reliable transports such as User Datagram Protocol
(UDP).
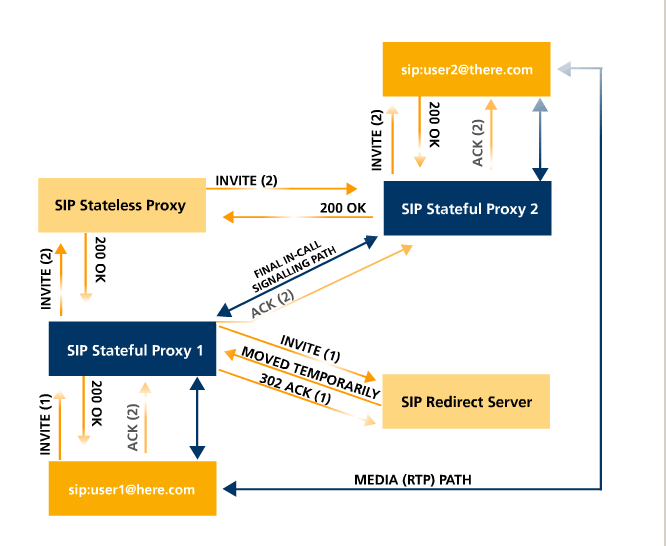 If we take the above example, User1’s UAC uses an Invite Client Transaction to send the initial INVITE (1) message. If no response is received after a timer controlled wait period the UAC may have chosen to terminate the transaction or retransmit the INVITE. However, once a response was received, User1 was confident the INVITE was delivered reliably. User1’s UAC then must acknowledge the response. On delivery of the ACK (2) both sides of the transaction are complete. And in this case, a Dialog may have been established.
If we take the above example, User1’s UAC uses an Invite Client Transaction to send the initial INVITE (1) message. If no response is received after a timer controlled wait period the UAC may have chosen to terminate the transaction or retransmit the INVITE. However, once a response was received, User1 was confident the INVITE was delivered reliably. User1’s UAC then must acknowledge the response. On delivery of the ACK (2) both sides of the transaction are complete. And in this case, a Dialog may have been established.
(SIMPLE) is the SIP-based suite of standards for instant messaging
and presence information
. MSRP (Message Session Relay Protocol
) allows instant message sessions and file transfer.
test specification language is used for the purposes of specifying conformance tests for SIP implementations. SIP test suite is developed by a Specialist Task Force at ETSI (STF 196). The SIP developer community meets regularly at the SIP Forum SIPit events to test interoperability and test implementations of new RFCs.
Many VoIP phone companies allow customers to use their own SIP devices, such as SIP-capable telephone sets, or softphone
s.
SIP-enabled video surveillance cameras can make calls to alert the owner or operator that an event has occurred, for example to notify that motion has been detected out-of-hours in a protected area.
SIP is used in audio over IP
for broadcasting
applications where it provides an interoperable means for audio interfaces from different manufacturers to make connections with one another.
, is a protocol used to create, modify, and terminate communication sessions based on ISUP using SIP and IP networks. Services using SIP-I include voice, video telephony, fax and data. SIP-I and SIP-T are two protocols with similar features, notably to allow ISUP messages to be transported over SIP networks. This preserves all of the detail available in the ISUP header, which is important as there are many country-specific variants of ISUP that have been implemented over the last 30 years, and it is not always possible to express all of the same detail using a native SIP message. SIP-I was defined by the ITU-T, where SIP-T was defined via the IETF RFC
route.
Signalling (telecommunications)
In telecommunication, signaling has the following meanings:*the use of signals for controlling communications...
protocol
Communications protocol
A communications protocol is a system of digital message formats and rules for exchanging those messages in or between computing systems and in telecommunications...
widely used for controlling communication sessions such as voice and video
Video
Video is the technology of electronically capturing, recording, processing, storing, transmitting, and reconstructing a sequence of still images representing scenes in motion.- History :...
calls over Internet Protocol
Internet Protocol
The Internet Protocol is the principal communications protocol used for relaying datagrams across an internetwork using the Internet Protocol Suite...
(IP). The protocol can be used for creating, modifying and terminating two-party (unicast
Unicast
right|200pxIn computer networking, unicast transmission is the sending of messages to a single network destination identified by a unique address.-Addressing methodologies:...
) or multiparty (multicast
Multicast
In computer networking, multicast is the delivery of a message or information to a group of destination computers simultaneously in a single transmission from the source creating copies automatically in other network elements, such as routers, only when the topology of the network requires...
) sessions. Sessions may consist of one or several media streams
Streaming media
Streaming media is multimedia that is constantly received by and presented to an end-user while being delivered by a streaming provider.The term "presented" is used in this article in a general sense that includes audio or video playback. The name refers to the delivery method of the medium rather...
.
Other SIP applications include video conferencing, streaming multimedia distribution, instant messaging
Instant messaging
Instant Messaging is a form of real-time direct text-based chatting communication in push mode between two or more people using personal computers or other devices, along with shared clients. The user's text is conveyed over a network, such as the Internet...
, presence information
Presence information
In computer and telecommunications networks, presence information is a status indicator that conveys ability and willingness of a potential communication partner—for example a user--to communicate...
, file transfer
File transfer
File transfer is a generic term for the act of transmitting files over a computer network or the Internet. There are numerous ways and protocols to transfer files over a network. Computers which provide a file transfer service are often called file servers. Depending on the client's perspective the...
and online game
Online game
An online game is a game played over some form of computer network. This almost always means the Internet or equivalent technology, but games have always used whatever technology was current: modems before the Internet, and hard wired terminals before modems...
s.
The SIP protocol is an Application Layer
Application layer
The Internet protocol suite and the Open Systems Interconnection model of computer networking each specify a group of protocols and methods identified by the name application layer....
protocol designed to be independent of the underlying Transport Layer
Transport layer
In computer networking, the transport layer or layer 4 provides end-to-end communication services for applications within a layered architecture of network components and protocols...
; it can run on Transmission Control Protocol
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
(TCP), User Datagram Protocol
User Datagram Protocol
The User Datagram Protocol is one of the core members of the Internet Protocol Suite, the set of network protocols used for the Internet. With UDP, computer applications can send messages, in this case referred to as datagrams, to other hosts on an Internet Protocol network without requiring...
(UDP), or Stream Control Transmission Protocol
Stream Control Transmission Protocol
In computer networking, the Stream Control Transmission Protocol is a Transport Layer protocol, serving in a similar role to the popular protocols Transmission Control Protocol and User Datagram Protocol...
(SCTP). It is a text-based protocol, incorporating many elements of the Hypertext Transfer Protocol
Hypertext Transfer Protocol
The Hypertext Transfer Protocol is a networking protocol for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web....
(HTTP) and the Simple Mail Transfer Protocol
Simple Mail Transfer Protocol
Simple Mail Transfer Protocol is an Internet standard for electronic mail transmission across Internet Protocol networks. SMTP was first defined by RFC 821 , and last updated by RFC 5321 which includes the extended SMTP additions, and is the protocol in widespread use today...
(SMTP).
History
SIP was originally designed by Henning SchulzrinneHenning Schulzrinne
Henning Schulzrinne is chair of the Computer Science department at Columbia University. He is a co-chair of the Internet Technical Committee of the IEEE Communications Society...
and Mark Handley
Mark Handley (computer scientist)
Mark Handley is Professor of Networked Systems in the Department of Computer Science of University College London since 2003, where he leads the Networks Research Group...
in 1996. In November 2000, SIP was accepted as a 3GPP
3GPP
The 3rd Generation Partnership Project is a collaboration between groups of telecommunications associations, known as the Organizational Partners...
signaling protocol and permanent element of the IP Multimedia Subsystem
IP Multimedia Subsystem
The IP Multimedia Subsystem or IP Multimedia Core Network Subsystem is an architectural framework for delivering Internet Protocol multimedia services. It was originally designed by the wireless standards body 3rd Generation Partnership Project , as a part of the vision for evolving mobile...
(IMS) architecture for IP-based streaming multimedia services in cellular systems. The latest version of the specification is RFC 3261 from the IETF Network Working Group published in June 2002.
The free software community
Free software community
The free-software community is an informal term that refers to the users and developers of free software as well as supporters of the free-software movement. The movement is sometimes referred to as the open-source software community or a subset thereof...
started to provide more and more of the SIP technology required to build both end points as well as proxy and registrar servers leading to a commodification of the technology, which has accelerated global adoption. As an example, the open source community at SIPfoundry
SIPfoundry
SIPfoundry is a not-for-profit open source community, whose mission is to promote and advance Session Initiation Protocol - related open source projects...
actively develops a variety of SIP stacks, client applications and SDKs, in addition to entire private branch exchange (IP PBX
IP PBX
An IP PBX is a business telephone system designed to deliver voice or video over a data network and interoperate with the normal Public Switched Telephone Network ....
) solutions that compete in the market against mostly proprietary
Proprietary software
Proprietary software is computer software licensed under exclusive legal right of the copyright holder. The licensee is given the right to use the software under certain conditions, while restricted from other uses, such as modification, further distribution, or reverse engineering.Complementary...
IP PBX
IP PBX
An IP PBX is a business telephone system designed to deliver voice or video over a data network and interoperate with the normal Public Switched Telephone Network ....
implementations from established vendors.
The National Institute of Standards and Technology
National Institute of Standards and Technology
The National Institute of Standards and Technology , known between 1901 and 1988 as the National Bureau of Standards , is a measurement standards laboratory, otherwise known as a National Metrological Institute , which is a non-regulatory agency of the United States Department of Commerce...
(NIST), Advanced Networking Technologies Division provides a public domain implementation of the JAVA Standard for SIP which serves as a reference implementation
Reference implementation
In the software development process, a reference implementation is the standard from which all other implementations, with their attendant customizations, are measured, and to which all improvements are added...
for the standard. The stack can work in proxy server or user agent scenarios and has been used in numerous commercial and research projects. It supports RFC 3261 in full and a number of extension RFCs including RFC 3265 (Subscribe / Notify) and RFC 3262 (Provisional Reliable Responses) etc.
Protocol design
SIP employs design elements similar to the HTTP request/response transaction model. Each transaction consists of a client request that invokes a particular method or function on the server and at least one response. SIP reuses most of the header fields, encoding rules and status codes of HTTP, providing a readable text-based format.SIP works in concert with several other protocols and is only involved in the signaling portion of a communication session. SIP clients typically use TCP or UDP on port numbers 5060 and/or 5061 to connect to SIP servers and other SIP endpoints. Port 5060 is commonly used for non-encrypted signaling traffic whereas port 5061 is typically used for traffic encrypted with Transport Layer Security
Transport Layer Security
Transport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
(TLS). SIP is primarily used in setting up and tearing down voice or video calls. It also allows modification of existing calls. The modification can involve changing addresses or ports
Computer port (software)
In computer programming, port has a wide range of meanings.A software port is a virtual/logical data connection that can be used by programs to exchange data directly, instead of going through a file or other temporary storage location...
, inviting more participants, and adding or deleting media streams. SIP has also found applications in messaging applications, such as instant messaging, and event subscription and notification. There are a large number of SIP-related Internet Engineering Task Force
Internet Engineering Task Force
The Internet Engineering Task Force develops and promotes Internet standards, cooperating closely with the W3C and ISO/IEC standards bodies and dealing in particular with standards of the TCP/IP and Internet protocol suite...
(IETF) documents that define behavior for such applications. The voice and video stream communications in SIP applications are carried over another application protocol, the Real-time Transport Protocol
Real-time Transport Protocol
The Real-time Transport Protocol defines a standardized packet format for delivering audio and video over IP networks. RTP is used extensively in communication and entertainment systems that involve streaming media, such as telephony, video teleconference applications, television services and...
(RTP). Parameters (port numbers, protocols, codecs) for these media streams are defined and negotiated using the Session Description Protocol
Session Description Protocol
The Session Description Protocol is a format for describing streaming media initialization parameters. The IETF published the original specification as an IETF Proposed Standard in April 1998, and subsequently published a revised specification as an IETF Proposed Standard as RFC 4566 in July...
(SDP) which is transported in the SIP packet body.
A motivating goal for SIP was to provide a signaling and call setup protocol for IP-based communications that can support a superset of the call processing functions and features present in the public switched telephone network
Public switched telephone network
The public switched telephone network is the network of the world's public circuit-switched telephone networks. It consists of telephone lines, fiber optic cables, microwave transmission links, cellular networks, communications satellites, and undersea telephone cables, all inter-connected by...
(PSTN). SIP by itself does not define these features; rather, its focus is call-setup and signaling. The features that permit familiar telephone-like operations: dialing a number, causing a phone to ring, hearing ringback tones or a busy signal - are performed by proxy servers and user agents. Implementation and terminology are different in the SIP world but to the end-user, the behavior is similar.
SIP-enabled telephony networks can also implement many of the more advanced call processing features present in Signaling System 7 (SS7), though the two protocols themselves are very different. SS7 is a centralized protocol, characterized by a complex central network architecture and dumb endpoints (traditional telephone handsets). SIP is a peer-to-peer
Peer-to-peer
Peer-to-peer computing or networking is a distributed application architecture that partitions tasks or workloads among peers. Peers are equally privileged, equipotent participants in the application...
protocol, thus it requires only a simple (and thus scalable) core network with intelligence distributed to the network edge, embedded in endpoints (terminating devices built in either hardware or software). SIP features are implemented in the communicating endpoints (i.e. at the edge of the network) contrary to traditional SS7 features, which are implemented in the network.
Although several other VoIP signaling protocols exist (such as BICC, H.323
H.323
H.323 is a recommendation from the ITU Telecommunication Standardization Sector that defines the protocols to provide audio-visual communication sessions on any packet network...
, MGCP, MEGACO), SIP is distinguished by its proponents for having roots in the IP community rather than the telecommunications industry. SIP has been standardized and governed primarily by the IETF, while other protocols, such as H.323, have traditionally been associated with the International Telecommunication Union
International Telecommunication Union
The International Telecommunication Union is the specialized agency of the United Nations which is responsible for information and communication technologies...
(ITU).
The first proposed standard version (SIP 1.0) was defined by RFC 2543. This version of the protocol was further refined to version 2.0 and clarified in RFC 3261, although some implementations are still relying on the older definitions.
Network elements
A SIP user agent (UA) is a logical network end-point used to create or receive SIP messages and thereby manage a SIP session. A SIP UA can perform the role of a User Agent Client (UAC), which sends SIP requests, and the User Agent Server (UAS), which receives the requests and returns a SIP response. These roles of UAC and UAS only last for the duration of a SIP transaction.A SIP phone is a SIP user agent that provides the traditional call functions of a telephone, such as dial, answer, reject, hold/unhold, and call transfer.
SIP phones may be implemented as a hardware device or as a softphone
Softphone
A softphone is a software program for making telephone calls over the Internet using a general purpose computer, rather than using dedicated hardware. Often a softphone is designed to behave like a traditional telephone, sometimes appearing as an image of a phone, with a display panel and buttons...
. As vendors increasingly implement SIP as a standard telephony platform, often driven by 4G
4G
In telecommunications, 4G is the fourth generation of cellular wireless standards. It is a successor to the 3G and 2G families of standards. In 2009, the ITU-R organization specified the IMT-Advanced requirements for 4G standards, setting peak speed requirements for 4G service at 100 Mbit/s...
efforts, the distinction between hardware-based and software-based SIP phones is being blurred and SIP elements are implemented in the basic firmware functions of many IP-capable devices. Examples are devices from Nokia
Nokia
Nokia Corporation is a Finnish multinational communications corporation that is headquartered in Keilaniemi, Espoo, a city neighbouring Finland's capital Helsinki...
and Research in Motion
Research In Motion
Research In Motion Limited or RIM is a Canadian multinational telecommunications company headquartered in Waterloo, Ontario, Canada that designs, manufactures and markets wireless solutions for the worldwide mobile communications market...
.
Each resource of a SIP network, such as a User Agent or a voicemail box, is identified by a Uniform Resource Identifier
Uniform Resource Identifier
In computing, a uniform resource identifier is a string of characters used to identify a name or a resource on the Internet. Such identification enables interaction with representations of the resource over a network using specific protocols...
(URI), based on the general standard syntax also used in Web services and e-mail. A typical SIP URI is of the form:
sip:username:password@host:port. The URI schemeURI scheme
In the field of computer networking, a URI scheme is the top level of the Uniform Resource Identifier naming structure. All URIs and absolute URI references are formed with a scheme name, followed by a colon character , and the remainder of the URI called the scheme-specific part...
used for SIP is
sip:. If secure transmissionSecure transmission
In computer science, Secure Transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. Many secure transmission methods require a type of encryption. The most common email encryption is called PKI...
is required, the scheme
sips: is used and SIP messages must be transported over Transport Layer SecurityTransport Layer Security
Transport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
(TLS).
In SIP, as in HTTP, the user agent
User agent
In computing, a user agent is a client application implementing a network protocol used in communications within a client–server distributed computing system...
may identify itself using a message header field 'User-Agent', containing a text description of the software/hardware/product involved. The User-Agent field is sent in request messages, which means that the receiving SIP server can see this information. SIP network elements sometimes store this information, and it can be useful in diagnosing SIP compatibility problems.
SIP also defines server network elements. Although two SIP endpoints can communicate without any intervening SIP infrastructure, which is why the protocol is described as peer-to-peer, this approach is often impractical for a public service. RFC 3261 defines these server elements.
Proxy server: An intermediary entity that acts as both a server and a client for the purpose of making requests on behalf of other clients. A proxy server primarily plays the role of routing, which means its job is to ensure that a request is sent to another entity "closer" to the targeted user. Proxies are also useful for enforcing policy (for example, making sure a user is allowed to make a call). A proxy interprets, and, if necessary, rewrites specific parts of a request message before forwarding it.
Registrar: A server that accepts REGISTER requests and places the information it receives in those requests into the location service for the domain it handles which registers one or more IP addresses to a certain SIP URI
Úri
Úriis a village and commune in the comitatus of Pest in Hungary....
, indicated by the sip: scheme, although other protocol schemes are possible (such as tel:). More than one user agent
User agent
In computing, a user agent is a client application implementing a network protocol used in communications within a client–server distributed computing system...
can register at the same URI, with the result that all registered user agents will receive a call to the SIP URI.
- SIP registrars are logical elements, and are commonly co-located with SIP proxies. But it is also possible and often good for network scalability to place this location service with a redirect server.
Redirect server: A user agent server that generates 3xx (Redirection) responses to requests it receives, directing the client to contact an alternate set of URIs. The redirect server allows proxy servers to direct SIP session invitations to external domains.
Other SIP-related network elements include.
Session border controller
Session Border Controller
A session border controller is a device regularly deployed in Voice over Internet Protocol networks to exert control over the signaling and usually also the media streams involved in setting up, conducting, and tearing down telephone calls or other interactive media communications.SBC's original...
s (SBC): Serve as middle boxes between UA and SIP server for various types of functions, including network topology hiding, and assistance in NAT traversal
NAT traversal
NAT traversal is a general term for techniques that establish and maintain Internet protocol connections traversing network address translation gateways. Network address translation breaks end-to-end connectivity. Intercepting and modifying traffic can only be performed transparently in the...
.
gateways
Gateway (telecommunications)
In telecommunications, the term gateway has the following meaning:*In a communications network, a network node equipped for interfacing with another network that uses different protocols....
: Devices that exist at the edge between a SIP network and other networks (as a phone network).
SIP messages
SIP is a text-based protocol with syntax similar to that of HTTP. There are two different types of SIP messages: requests and responses. The first line of a request has a method, defining the nature of the request, and a Request-URI, indicating where the request should be sent. The first line of a response has a response code.For SIP requests, RFC 3261 defines the following methods:
- REGISTER: Used by a UA to indicate its current IP address and the URLs for which it would like to receive calls.
- INVITE: Used to establish a media session between user agents.
- ACK: Confirms reliable message exchanges.
- CANCEL: Terminates a pending request.
- BYE: Terminates a session between two users in a conference.
- OPTIONS: Requests information about the capabilities of a caller, without setting up a call.
- PRACK (Provisional Response Acknowledgement): PRACK improves network reliability by adding an acknowledgement system to the provisional Responses (1xx). PRACK is sent in response to provisional response (1xx).
The SIP response types defined in RFC 3261 fall in one of the following categories:
- Provisional (1xx): Request received and being processed.
- Success (2xx): The action was successfully received, understood, and accepted.
- Redirection (3xx): Further action needs to be taken (typically by sender) to complete the request.
- Client Error (4xx): The request contains bad syntax or cannot be fulfilled at the server.
- Server Error (5xx): The server failed to fulfill an apparently valid request.
- Global Failure (6xx): The request cannot be fulfilled at any server.
Transactions
SIP makes use of transactions to control the exchanges between participants and deliver messages reliably. The transactions maintain an internal state and make use of timers. Client Transactions send requests and Server Transactions respond to those requests with one-or-more responses. The responses may include zero-or-more Provisional (1xx) responses and one-or-more final (2xx-6xx) responses.Transactions are further categorized as either Invite or Non-Invite. Invite transactions differ in that they can establish a long-running conversation, referred to as a Dialog in SIP, and so include an acknowledgment (ACK) of any non-failing final response (e.g. 200 OK).
Because of these transactional mechanisms, SIP can make use of un-reliable transports such as User Datagram Protocol
User Datagram Protocol
The User Datagram Protocol is one of the core members of the Internet Protocol Suite, the set of network protocols used for the Internet. With UDP, computer applications can send messages, in this case referred to as datagrams, to other hosts on an Internet Protocol network without requiring...
(UDP).

Instant messaging and presence
The Session Initiation Protocol for Instant Messaging and Presence Leveraging ExtensionsSIMPLE
SIMPLE, the Session Initiation Protocol for Instant Messaging and Presence Leveraging Extensions, is an instant messaging and presence protocol suite based on Session Initiation Protocol managed by the IETF...
(SIMPLE) is the SIP-based suite of standards for instant messaging
Instant messaging
Instant Messaging is a form of real-time direct text-based chatting communication in push mode between two or more people using personal computers or other devices, along with shared clients. The user's text is conveyed over a network, such as the Internet...
and presence information
Presence information
In computer and telecommunications networks, presence information is a status indicator that conveys ability and willingness of a potential communication partner—for example a user--to communicate...
. MSRP (Message Session Relay Protocol
Message Session Relay Protocol
In computer networking, the Message Session Relay Protocol is a protocol for transmitting a series of related instant messages in the context of a communications session. An application instantiates the session with the Session Initiation Protocol or other rendez-vous methods.The MSRP protocol is...
) allows instant message sessions and file transfer.
Conformance testing
TTCN-3TTCN-3
TTCN-3 is a strongly typed test scripting language used in conformance testing of communicating systems and a specification of test infrastructure interfaces that glue abstract test scripts with concrete communication environments. TTCN-3 has been developed by ETSI and its predecessor is TTCN-2...
test specification language is used for the purposes of specifying conformance tests for SIP implementations. SIP test suite is developed by a Specialist Task Force at ETSI (STF 196). The SIP developer community meets regularly at the SIP Forum SIPit events to test interoperability and test implementations of new RFCs.
Applications
The market for consumer SIP devices continues to expand, there are many devices such as SIP Terminal Adapters, SIP Gateways, and SIP Trunking services providing replacements for ISDN telephone lines.Many VoIP phone companies allow customers to use their own SIP devices, such as SIP-capable telephone sets, or softphone
Softphone
A softphone is a software program for making telephone calls over the Internet using a general purpose computer, rather than using dedicated hardware. Often a softphone is designed to behave like a traditional telephone, sometimes appearing as an image of a phone, with a display panel and buttons...
s.
SIP-enabled video surveillance cameras can make calls to alert the owner or operator that an event has occurred, for example to notify that motion has been detected out-of-hours in a protected area.
SIP is used in audio over IP
Audio over IP
Streaming audio over IP networks is being increasingly used by broadcasting companies, among others, to provide high-quality audio feeds over distance across an IP network such as the Internet. The application is also known as audio contribution over IP in reference to the programming...
for broadcasting
Broadcasting
Broadcasting is the distribution of audio and video content to a dispersed audience via any audio visual medium. Receiving parties may include the general public or a relatively large subset of thereof...
applications where it provides an interoperable means for audio interfaces from different manufacturers to make connections with one another.
SIP-ISUP interworking
SIP-I, or the Session Initiation Protocol with encapsulated ISUPISDN User Part
The ISDN User Part or ISUP is part of the Signaling System #7 which is used to set up telephone calls in Public Switched Telephone Networks...
, is a protocol used to create, modify, and terminate communication sessions based on ISUP using SIP and IP networks. Services using SIP-I include voice, video telephony, fax and data. SIP-I and SIP-T are two protocols with similar features, notably to allow ISUP messages to be transported over SIP networks. This preserves all of the detail available in the ISUP header, which is important as there are many country-specific variants of ISUP that have been implemented over the last 30 years, and it is not always possible to express all of the same detail using a native SIP message. SIP-I was defined by the ITU-T, where SIP-T was defined via the IETF RFC
Request for Comments
In computer network engineering, a Request for Comments is a memorandum published by the Internet Engineering Task Force describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems.Through the Internet Society, engineers and...
route.
See also
- Computer telephony integrationComputer telephony integrationComputer telephony integration, also called computer–telephone integration or CTI, is a common name for any technology that allows interactions on a telephone and a computer to be integrated or coordinated...
(CTI) - Computer-supported telecommunications applicationsComputer-supported telecommunications applicationsComputer-supported telecommunications applications is an abstraction layer for telecommunications applications. It is independent of underlying protocols. It has a telephone device model that enables CTI applications to work with a wide range of telephone devices. Originally developed in 1992,...
(CSTA) - H.323H.323H.323 is a recommendation from the ITU Telecommunication Standardization Sector that defines the protocols to provide audio-visual communication sessions on any packet network...
protocols H.225.0H.225.0H.225.0 is part of the H.323 family of telecommunication protocols.The main objective of H.225.0 is the definition of messages and procedures for:* Call Signaling: establish, control and end an H.323 call...
and H.245H.245H.245 is a control channel protocol used with[in] e.g. H.323 and H.324 communication sessions, and involves the line transmission of non-telephone signals. It also offers the possibility to be tunneled within H.225.0 call signaling messages... - IP Multimedia SubsystemIP Multimedia SubsystemThe IP Multimedia Subsystem or IP Multimedia Core Network Subsystem is an architectural framework for delivering Internet Protocol multimedia services. It was originally designed by the wireless standards body 3rd Generation Partnership Project , as a part of the vision for evolving mobile...
(IMS) - IP phoneIP PhoneA VoIP phone uses voice over IP technologies allowing telephone calls to be made over an IP network such as the Internet instead of the ordinary PSTN system. Calls can traverse the Internet, or a private IP network such as that of a company...
- List of SIP software
- Media Gateway Control Protocol (MGCP)
- Message Session Relay ProtocolMessage Session Relay ProtocolIn computer networking, the Message Session Relay Protocol is a protocol for transmitting a series of related instant messages in the context of a communications session. An application instantiates the session with the Session Initiation Protocol or other rendez-vous methods.The MSRP protocol is...
(MSRP) - Mobile VoIPMobile VoIPMobile VoIP or simply mVoIP is an extension of mobility to a Voice over IP network. Two types of communication are generally supported: cordless/DECT/PCS protocols for short range or campus communications where all base stations are linked into the same LAN, and wider area communications using...
- MSCMLMSCMLThe Media Server Control Markup Language is a protocol used in conjunction with the Session Initiation Protocol to enable the delivery of advanced multimedia conferencing services over IP networks. The MSCML specification has been published by the IETF under RFC 4722, now obsoleted by the newer...
(Media Server Control Markup Language) - Network convergenceNetwork ConvergenceNetwork convergence refers to the provision of telephone, video and data communication services within a single network. In other words, one pipe is used to deliver all forms of communication services. The process of Network Convergence is primarily driven by development of technology and demand...
- RTP audio video profile
- Secure Real-time Transport ProtocolSecure Real-time Transport ProtocolThe Secure Real-time Transport Protocol defines a profile of RTP , intended to provide encryption, message authentication and integrity, and replay protection to the RTP data in both unicast and multicast applications...
(SRTP) - Session Initiation Protocol (Java)Session Initiation Protocol (Java)Session Initiation Protocol is an IETF standard protocol for IP-communication, enabling IP-Telephony gateways, client endpoints, PBXs and other communication systems or devices to communicate with each other...
- SIGTRANSIGTRANSIGTRAN is the name, derived from signaling transport, of the former Internet Engineering Task Force working group that produced specifications for a family of protocols that provide reliable datagram service and user layer adaptations for Signaling System 7 and ISDN communications protocols....
(Signaling Transport) - SIP TrunkingSIP TrunkingSIP trunking is a Voice over Internet Protocol service based on the Session Initiation Protocol by which Internet telephony service providers deliver telephone services and unified communication to customers equipped with private branch exchange facilities.-Domains:The architecture of SIP...
- Skinny Client Control ProtocolSkinny Client Control ProtocolThe Skinny Call Control Protocol is a proprietary network terminal control protocol originally developed by Selsius Systems....
(SCCP) - XIMSSXimssXML Interface to Messaging, Scheduling, and Signaling is an XML-based API for IP Communications.The XIMSS API was introduced by CommuniGate Systems in their CommuniGate Pro server starting with version 5.1 in Summer 2006...
(XML Interface to Messaging, Scheduling, and Signaling) - ZRTPZRTPZRTP is a cryptographic key-agreement protocol to negotiate the keys for encryption between two end points in a Voice over Internet Protocol phone telephony call based on the Real-time Transport Protocol. It uses Diffie-Hellman key exchange and the Secure Real-time Transport Protocol for...
External links
- Henning Schulzrinne's SIP homepage hosted by Columbia University
- SIP Latest specifications hosted by SIPKnowledge
- Some examples of SIP Use Cases (features)
- IANA: SIP Parameters
- IANA: SIP Event Types Namespace

