SHA hash functions
Encyclopedia
In cryptography, SHA-1 is a cryptographic hash function
designed by the United States National Security Agency
and published by the United States NIST
as a U.S. Federal Information Processing Standard
. SHA stands for "secure hash algorithm
". The three SHA algorithm
s are structured differently and are distinguished as SHA-0, SHA-1, and SHA-2
. SHA-1 is very similar to SHA-0, but corrects an error in the original SHA hash specification that led to significant weaknesses. The SHA-0 algorithm was not adopted by many applications. SHA-2 on the other hand significantly differs from the SHA-1 hash function.
SHA-1 is the most widely used of the existing SHA hash functions, and is employed in several widely used security applications and protocols. In 2005, security flaws were identified in SHA-1, namely that a mathematical weakness might exist, indicating that a stronger hash function would be desirable. Although no successful attacks have yet been reported on the SHA-2 variants, they are algorithmically similar to SHA-1 and so efforts are underway to develop improved alternatives. A new hash standard, SHA-3, is currently under development — an ongoing NIST hash function competition
is scheduled to end with the selection of a winning function in 2012.
 SHA-1 produces a 160-bit message digest based on principles similar to those used by Ronald L. Rivest
SHA-1 produces a 160-bit message digest based on principles similar to those used by Ronald L. Rivest
of MIT
in the design of the MD4
and MD5
message digest algorithms, but has a more conservative design.
The original specification of the algorithm was published in 1993 as the Secure Hash Standard, FIPS
PUB 180, by US government standards agency NIST (National Institute of Standards and Technology). This version is now often referred to as SHA-0. It was withdrawn by NSA shortly after publication and was superseded by the revised version, published in 1995 in FIPS PUB 180-1 and commonly referred to as SHA-1. SHA-1 differs from SHA-0 only by a single bitwise rotation in the message schedule of its compression function; this was done, according to NSA, to correct a flaw in the original algorithm which reduced its cryptographic security. However, NSA did not provide any further explanation or identify the flaw that was corrected. Weaknesses have subsequently been reported in both SHA-0 and SHA-1. SHA-1 appears to provide greater resistance to attacks, supporting the NSA’s assertion that the change increased the security.
and SSL, PGP
, SSH
, S/MIME
, and IPsec
. Those applications can also use MD5
; both MD5 and SHA-1 are descended from MD4
. SHA-1 hashing is also used in distributed revision control
systems such as Git
, Mercurial
, and Monotone
to identify revisions, and to detect data corruption
or tampering. The algorithm has also been used on Nintendo's
Wii
gaming console for signature verification when booting
, but a significant implementation flaw allows for an attacker to bypass the system's security scheme.
SHA-1 and SHA-2 are the secure hash algorithms required by law for use in certain U.S. Government applications, including use within other cryptographic algorithms and protocols, for the protection of sensitive unclassified information. FIPS PUB 180-1 also encouraged adoption and use of SHA-1 by private and commercial organizations. SHA-1 is being retired for most government uses; the U.S. National Institute of Standards and Technology says, "Federal agencies should stop using SHA-1 for...applications that require collision resistance as soon as practical, and must use the SHA-2
family of hash functions for these applications after 2010" (emphasis in original).
A prime motivation for the publication of the Secure Hash Algorithm was the Digital Signature Standard
, in which it is incorporated.
The SHA hash functions have been used as the basis for the SHACAL
block cipher
s.
and may or may not be practical depending on L and the particular computing environment. The second criterion, finding two different messages that produce the same message digest, known as a collision, requires on average only 2L/2 evaluations using a birthday attack
. For the latter reason the strength of a hash function is usually compared to a symmetric cipher of half the message digest length. Thus SHA-1 was originally thought to have 80-bit strength.
Cryptographers have produced collision pairs for SHA-0 and have found algorithms that should produce SHA-1 collisions in far fewer than the originally expected 280 evaluations.
In terms of practical security, a major concern about these new attacks is that they might pave the way to more efficient ones. Whether this is the case is yet to be seen, but a migration to stronger hashes is believed to be prudent. Some of the applications that use cryptographic hashes, such as password storage, are only minimally affected by a collision attack. Constructing a password that works for a given account requires a preimage attack
, as well as access to the hash of the original password, which may or may not be trivial. Reversing password encryption (e.g. to obtain a password to try against a user's account elsewhere) is not made possible by the attacks. (However, even a secure password hash can't prevent brute-force attacks on weak passwords
.)
In the case of document signing, an attacker could not simply fake a signature from an existing document—the attacker would have to produce a pair of documents, one innocuous and one damaging, and get the private key holder to sign the innocuous document. There are practical circumstances in which this is possible; until the end of 2008, it was possible to create forged SSL
certificates using an MD5
collision.
Due to the block and iterative structure of the algorithms and the absence of additional final steps, all SHA functions are vulnerable to length-extension and partial-message collision attacks. These attacks allow an attacker to forge a message, signed only by a keyed hash - or
or  - by extending the message and recalculating the hash without knowing the key. The simplest improvement to prevent these attacks is to hash twice -
- by extending the message and recalculating the hash without knowing the key. The simplest improvement to prevent these attacks is to hash twice - 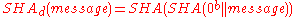 (
( - zero block, length is equal to block size of hash function).
- zero block, length is equal to block size of hash function).
98, two French researchers, Florent Chabaud and Antoine Joux, presented an attack on SHA-0 (Chabaud and Joux, 1998): collisions
can be found with complexity 261, fewer than the 280 for an ideal hash function of the same size.
In 2004, Biham
and Chen found near-collisions for SHA-0—two messages that hash to nearly the same value; in this case, 142 out of the 160 bits are equal. They also found full collisions of SHA-0 reduced to 62 out of its 80 rounds.
Subsequently, on 12 August 2004, a collision for the full SHA-0 algorithm was announced by Joux, Carribault, Lemuet, and Jalby. This was done by using a generalization of the Chabaud and Joux attack. Finding the collision had complexity 251 and took about 80,000 CPU hours on a supercomputer
with 256 Itanium 2 processors. (Equivalent to 13 days of full-time use of the computer.)
On 17 August 2004, at the Rump Session of CRYPTO 2004, preliminary results were announced by Wang
, Feng, Lai, and Yu, about an attack on MD5
, SHA-0 and other hash functions. The complexity of their attack on SHA-0 is 240, significantly better than the attack by Joux et al.
In February 2005, an attack by Xiaoyun Wang, Yiqun Lisa Yin, and Hongbo Yu was announced which could find collisions in SHA-0 in 239 operations.
s should be reconsidered. After the CRYPTO 2004 results were published, NIST announced that they planned to phase out the use of SHA-1 by 2010 in favor of the SHA-2 variants.
In early 2005, Rijmen
and Oswald published an attack on a reduced version of SHA-1—53 out of 80 rounds—which finds collisions with a computational effort of fewer than 280 operations.
In February 2005, an attack by Xiaoyun Wang
, Yiqun Lisa Yin, Bayarjargal, and Hongbo Yu was announced. The attacks can find collisions in the full version of SHA-1, requiring fewer than 269 operations. (A brute-force search
would require 280 operations.)
The authors write:
"In particular, our analysis is built upon the original differential attack on SHA-0 [sic], the near collision attack on SHA-0, the multiblock collision techniques, as well as the message modification techniques used in the collision search attack on MD5. Breaking SHA-1 would not be possible without these powerful analytical techniques." The authors have presented a collision for 58-round SHA-1, found with 233 hash operations.
The paper with the full attack description was published in August 2005 at the CRYPTO conference.
In an interview, Yin states that, "Roughly, we exploit the following two weaknesses: One is that the file preprocessing step is not complicated enough; another is that certain math operations in the first 20 rounds have unexpected security problems."
On 17 August 2005, an improvement on the SHA-1 attack was announced on behalf of Xiaoyun Wang, Andrew Yao
and Frances Yao
at the CRYPTO 2005 rump session, lowering the complexity required for finding a collision in SHA-1 to 263. On 18 December 2007 the details of this result were explained and verified by Martin Cochran.
Christophe De Cannière and Christian Rechberger further improved the attack on SHA-1 in "Finding SHA-1 Characteristics: General Results and Applications," receiving the Best Paper Award at ASIACRYPT
2006. A two-block collision for 64-round SHA-1 was presented, found using unoptimized methods with 235 compression function evaluations. As this attack requires the equivalent of about 235 evaluations, it is considered to be a significant theoretical break. Their attack was extended further to 73 rounds (of 80) in 2010 by Grechnikov. In order to find an actual collision in the full 80 rounds of the hash function, however, massive amounts of computer time are required. To that end, a collision search for SHA-1 using the distributed computing platform BOINC began August 8, 2007, organized by the Graz University of Technology
. The effort was abandoned May 12, 2009 due to lack of progress.
At the Rump Session of CRYPTO 2006, Christian Rechberger and Christophe De Cannière claimed to have discovered a collision attack on SHA-1 that would allow an attacker to select at least parts of the message.
In 2008, an attack methodology by Stéphane Manuel may produce hash collisions with an estimated theoretical complexity of 251 to 257 operations.
Cameron McDonald, Philip Hawkes and Josef Pieprzyk presented a hash collision attack with claimed complexity 252 at the Rump session of Eurocrypt 2009. However, the accompanying paper, "Differential Path for SHA-1 with complexity O
(252)" has been withdrawn due to the authors' discovery that their estimate was incorrect.
Marc Stevens runs a project called HashClash, implementing a differential path attack against SHA-1. On 8 November 2010, he claimed he had a fully working near-collision attack against full SHA-1 working with an estimated complexity equivalent to 257.5 SHA-1 compressions.
(NIST) and the Communications Security Establishment
(CSE). For informal verification, a package to generate a high number of test vectors is made available for download on the NIST site; the resulting verification however does not replace, in any way, the formal CMVP validation, which is required by law for certain applications.
, there are nearly 1400 validated implementations of SHA-1, with around a dozen of them capable of handling messages with a length in bits not a multiple of eight (see SHS Validation List).
encoding is used for all messages.
SHA1("The quick brown fox jumps over the lazy dog
")
= 2fd4e1c6 7a2d28fc ed849ee1 bb76e739 1b93eb12
Even a small change in the message will, with overwhelming probability, result in a completely different hash due to the avalanche effect
. For example, changing
SHA1("The quick brown fox jumps over the lazy cog")
= de9f2c7f d25e1b3a fad3e85a 0bd17d9b 100db4b3
The hash of the zero-length string is:
SHA1("")
= da39a3ee 5e6b4b0d 3255bfef 95601890 afd80709
for the SHA-1 algorithm follows:
Note 1: All variables are unsigned 32 bits and wrap modulo 232 when calculating
Note 2: All constants in this pseudo code are in big endian
.
Within each word, the most significant byte is stored in the leftmost byte position
Initialize variables:
h0 = 0x67452301
h1 = 0xEFCDAB89
h2 = 0x98BADCFE
h3 = 0x10325476
h4 = 0xC3D2E1F0
Pre-processing:
append the bit '1' to the message
append 0 ≤ k < 512 bits '0', so that the resulting message length (in bits)
is congruent
to 448 (mod 512)
append length of message (before pre-processing), in bits, as 64-bit big-endian
integer
Process the message in successive 512-bit chunks:
break message into 512-bit chunks
for each chunk
break chunk into sixteen 32-bit big-endian words w[i], 0 ≤ i ≤ 15
Extend the sixteen 32-bit words into eighty 32-bit words:
for i from 16 to 79
w[i] = (w[i-3] xor w[i-8] xor w[i-14] xor w[i-16]) leftrotate
1
Initialize hash value for this chunk:
a = h0
b = h1
c = h2
d = h3
e = h4
Main loop:
for i from 0 to 79
if 0 ≤ i ≤ 19 then
f = (b and c) or ((not b) and d)
k = 0x5A827999
else if 20 ≤ i ≤ 39
f = b xor c xor d
k = 0x6ED9EBA1
else if 40 ≤ i ≤ 59
f = (b and c) or (b and d) or (c and d)
k = 0x8F1BBCDC
else if 60 ≤ i ≤ 79
f = b xor c xor d
k = 0xCA62C1D6
temp = (a leftrotate 5) + f + e + k + w[i]
e = d
d = c
c = b leftrotate 30
b = a
a = temp
Add this chunk's hash to result so far:
h0 = h0 + a
h1 = h1 + b
h2 = h2 + c
h3 = h3 + d
h4 = h4 + e
Produce the final hash value (big-endian):
digest = hash = h0 append h1 append h2 append h3 append h4
The constant values used are chosen as nothing up my sleeve number
s: the four round constants
Instead of the formulation from the original FIPS PUB 180-1 shown, the following equivalent expressions may be used to compute
(0 ≤ i ≤ 19): f = d xor (b and (c xor d)) (alternative 1)
(0 ≤ i ≤ 19): f = (b and c) xor ((not b) and d) (alternative 2)
(0 ≤ i ≤ 19): f = (b and c) + ((not b) and d) (alternative 3)
(0 ≤ i ≤ 19): f = vec_sel(d, c, b) (alternative 4)
(40 ≤ i ≤ 59): f = (b and c) or (d and (b or c)) (alternative 1)
(40 ≤ i ≤ 59): f = (b and c) or (d and (b xor c)) (alternative 2)
(40 ≤ i ≤ 59): f = (b and c) + (d and (b xor c)) (alternative 3)
(40 ≤ i ≤ 59): f = (b and c) xor (b and d) xor (c and d) (alternative 4)
Max Locktyukhin has also shown that for the rounds 32–79 the computation of:
w[i] = (w[i-3] xor w[i-8] xor w[i-14] xor w[i-16]) leftrotate
1
can be replaced with:
w[i] = (w[i-6] xor w[i-16] xor w[i-28] xor w[i-32]) leftrotate
2
This transformation keeps all operands 64-bit aligned and, by removing the dependency of
instructions.
: A general purpose cryptographic library based on the code from GNU Privacy Guard
.
OpenSSL
: The widely used OpenSSL
, open-source
– implementations of SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512
cryptlib
: an open source
cross-platform software security toolkit library
Crypto++
: A public domain C++ class library of cryptographic schemes, including implementations of the SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512 algorithms.
Bouncy Castle
: The Bouncy Castle Library is a free Java and C# class library that contains implementations of the SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512 algorithms as well as other algorithms like Whirlpool, Tiger
, RIPEMD
, GOST-3411, MD2, MD4
and MD5
.
jsSHA: A cross-browser JavaScript
library for client-side calculation of SHA digests, despite the fact that JavaScript does not natively support the 64-bit operations required for SHA-384 and SHA-512.
LibTomCrypt: A portable ISO C cryptographic toolkit, Public Domain.
Intel: Fast implementation of SHA-1 using Intel Supplemental SSE3 extensions, free for commercial or non-commercial use.
md5deep
: A set of programs to compute MD5, SHA-1, SHA-256, Tiger, or Whirlpool cryptographic message digests on an arbitrary number of files. It is used in computer security, system administration and computer forensics communities for purposes of running large numbers of files through any of several different cryptographic digests. It is similar to the md5sum
.
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
designed by the United States National Security Agency
National Security Agency
The National Security Agency/Central Security Service is a cryptologic intelligence agency of the United States Department of Defense responsible for the collection and analysis of foreign communications and foreign signals intelligence, as well as protecting U.S...
and published by the United States NIST
National Institute of Standards and Technology
The National Institute of Standards and Technology , known between 1901 and 1988 as the National Bureau of Standards , is a measurement standards laboratory, otherwise known as a National Metrological Institute , which is a non-regulatory agency of the United States Department of Commerce...
as a U.S. Federal Information Processing Standard
Federal Information Processing Standard
A Federal Information Processing Standard is a publicly announced standardization developed by the United States federal government for use in computer systems by all non-military government agencies and by government contractors, when properly invoked and tailored on a contract...
. SHA stands for "secure hash algorithm
Secure Hash Algorithm
The Secure Hash Algorithm is one of a number of cryptographic hash functions published by the National Institute of Standards and Technology as a U.S. Federal Information Processing Standard :...
". The three SHA algorithm
Algorithm
In mathematics and computer science, an algorithm is an effective method expressed as a finite list of well-defined instructions for calculating a function. Algorithms are used for calculation, data processing, and automated reasoning...
s are structured differently and are distinguished as SHA-0, SHA-1, and SHA-2
SHA-2
In cryptography, SHA-2 is a set of cryptographic hash functions designed by the National Security Agency and published in 2001 by the NIST as a U.S. Federal Information Processing Standard. SHA stands for Secure Hash Algorithm. SHA-2 includes a significant number of changes from its predecessor,...
. SHA-1 is very similar to SHA-0, but corrects an error in the original SHA hash specification that led to significant weaknesses. The SHA-0 algorithm was not adopted by many applications. SHA-2 on the other hand significantly differs from the SHA-1 hash function.
SHA-1 is the most widely used of the existing SHA hash functions, and is employed in several widely used security applications and protocols. In 2005, security flaws were identified in SHA-1, namely that a mathematical weakness might exist, indicating that a stronger hash function would be desirable. Although no successful attacks have yet been reported on the SHA-2 variants, they are algorithmically similar to SHA-1 and so efforts are underway to develop improved alternatives. A new hash standard, SHA-3, is currently under development — an ongoing NIST hash function competition
NIST hash function competition
The NIST hash function competition is an open competition held by the US National Institute of Standards and Technology for a new SHA-3 function to replace the older SHA-1 and SHA-2, which was formally announced in the Federal Register on November 2, 2007...
is scheduled to end with the selection of a winning function in 2012.
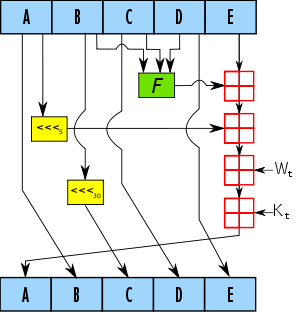
The SHA-1 hash function

Ron Rivest
Ronald Linn Rivest is a cryptographer. He is the Andrew and Erna Viterbi Professor of Computer Science at MIT's Department of Electrical Engineering and Computer Science and a member of MIT's Computer Science and Artificial Intelligence Laboratory...
of MIT
Massachusetts Institute of Technology
The Massachusetts Institute of Technology is a private research university located in Cambridge, Massachusetts. MIT has five schools and one college, containing a total of 32 academic departments, with a strong emphasis on scientific and technological education and research.Founded in 1861 in...
in the design of the MD4
MD4
The MD4 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1990. The digest length is 128 bits. The algorithm has influenced later designs, such as the MD5, SHA-1 and RIPEMD algorithms....
and MD5
MD5
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
message digest algorithms, but has a more conservative design.
The original specification of the algorithm was published in 1993 as the Secure Hash Standard, FIPS
Federal Information Processing Standard
A Federal Information Processing Standard is a publicly announced standardization developed by the United States federal government for use in computer systems by all non-military government agencies and by government contractors, when properly invoked and tailored on a contract...
PUB 180, by US government standards agency NIST (National Institute of Standards and Technology). This version is now often referred to as SHA-0. It was withdrawn by NSA shortly after publication and was superseded by the revised version, published in 1995 in FIPS PUB 180-1 and commonly referred to as SHA-1. SHA-1 differs from SHA-0 only by a single bitwise rotation in the message schedule of its compression function; this was done, according to NSA, to correct a flaw in the original algorithm which reduced its cryptographic security. However, NSA did not provide any further explanation or identify the flaw that was corrected. Weaknesses have subsequently been reported in both SHA-0 and SHA-1. SHA-1 appears to provide greater resistance to attacks, supporting the NSA’s assertion that the change increased the security.
Comparison of SHA functions
In the table below, internal state means the “internal hash sum” after each compression of a data block.| Algorithm and variant | Output size (bits) |
Internal state size (bits) |
Block size (bits) |
Max message size (bits) |
Word size (bits) |
Rounds | Operations | Collisions Hash collision Not to be confused with wireless packet collision.In computer science, a collision or clash is a situation that occurs when two distinct pieces of data have the same hash value, checksum, fingerprint, or cryptographic digest.... found? |
|
|---|---|---|---|---|---|---|---|---|---|
| SHA-0 | 160 | 160 | 512 | 264 − 1 | 32 | 80 | add, and, or, xor, rotate, mod | Yes | |
| SHA-1 | Theoretical attack (251) | ||||||||
| SHA-2 | SHA-256/224 | 256/224 | 256 | 512 | 264 − 1 | 32 | 64 | add, and, or, xor, shift, rotate, mod | No |
| SHA-512/384 | 512/384 | 512 | 1024 | 2128 − 1 | 64 | 80 | |||
Applications
SHA-1 forms part of several widely used security applications and protocols, including TLSTransport Layer Security
Transport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
and SSL, PGP
Pretty Good Privacy
Pretty Good Privacy is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security...
, SSH
Secure Shell
Secure Shell is a network protocol for secure data communication, remote shell services or command execution and other secure network services between two networked computers that it connects via a secure channel over an insecure network: a server and a client...
, S/MIME
S/MIME
S/MIME is a standard for public key encryption and signing of MIME data. S/MIME is on an IETF standards track and defined in a number of documents, most importantly RFCs. S/MIME was originally developed by RSA Data Security Inc...
, and IPsec
IPsec
Internet Protocol Security is a protocol suite for securing Internet Protocol communications by authenticating and encrypting each IP packet of a communication session...
. Those applications can also use MD5
MD5
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
; both MD5 and SHA-1 are descended from MD4
MD4
The MD4 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1990. The digest length is 128 bits. The algorithm has influenced later designs, such as the MD5, SHA-1 and RIPEMD algorithms....
. SHA-1 hashing is also used in distributed revision control
Distributed revision control
A distributed revision control system , distributed version control or decentralized version control keeps track of software revisions and allows many developers to work on a given project without necessarily being connected to a common network.-Distributed vs...
systems such as Git
Git (software)
Git is a distributed revision control system with an emphasis on speed. Git was initially designed and developed by Linus Torvalds for Linux kernel development. Every Git working directory is a full-fledged repository with complete history and full revision tracking capabilities, not dependent on...
, Mercurial
Mercurial (software)
Mercurial is a cross-platform, distributed revision control tool for software developers. It is mainly implemented using the Python programming language, but includes a binary diff implementation written in C. It is supported on Windows and Unix-like systems, such as FreeBSD, Mac OS X and Linux...
, and Monotone
Monotone (software)
Monotone is an open source software tool for distributed revision control. Monotone tracks revisions to files, groups sets of revisions into changesets, and tracks history across renames.The focus of the project is on integrity over performance...
to identify revisions, and to detect data corruption
Data corruption
Data corruption refers to errors in computer data that occur during writing, reading, storage, transmission, or processing, which introduce unintended changes to the original data...
or tampering. The algorithm has also been used on Nintendo's
Nintendo
is a multinational corporation located in Kyoto, Japan. Founded on September 23, 1889 by Fusajiro Yamauchi, it produced handmade hanafuda cards. By 1963, the company had tried several small niche businesses, such as a cab company and a love hotel....
Wii
Wii
The Wii is a home video game console released by Nintendo on November 19, 2006. As a seventh-generation console, the Wii primarily competes with Microsoft's Xbox 360 and Sony's PlayStation 3. Nintendo states that its console targets a broader demographic than that of the two others...
gaming console for signature verification when booting
Booting
In computing, booting is a process that begins when a user turns on a computer system and prepares the computer to perform its normal operations. On modern computers, this typically involves loading and starting an operating system. The boot sequence is the initial set of operations that the...
, but a significant implementation flaw allows for an attacker to bypass the system's security scheme.
SHA-1 and SHA-2 are the secure hash algorithms required by law for use in certain U.S. Government applications, including use within other cryptographic algorithms and protocols, for the protection of sensitive unclassified information. FIPS PUB 180-1 also encouraged adoption and use of SHA-1 by private and commercial organizations. SHA-1 is being retired for most government uses; the U.S. National Institute of Standards and Technology says, "Federal agencies should stop using SHA-1 for...applications that require collision resistance as soon as practical, and must use the SHA-2
SHA-2
In cryptography, SHA-2 is a set of cryptographic hash functions designed by the National Security Agency and published in 2001 by the NIST as a U.S. Federal Information Processing Standard. SHA stands for Secure Hash Algorithm. SHA-2 includes a significant number of changes from its predecessor,...
family of hash functions for these applications after 2010" (emphasis in original).
A prime motivation for the publication of the Secure Hash Algorithm was the Digital Signature Standard
Digital Signature Algorithm
The Digital Signature Algorithm is a United States Federal Government standard or FIPS for digital signatures. It was proposed by the National Institute of Standards and Technology in August 1991 for use in their Digital Signature Standard , specified in FIPS 186, adopted in 1993. A minor...
, in which it is incorporated.
The SHA hash functions have been used as the basis for the SHACAL
SHACAL
SHACAL-1 is a 160-bit block cipher based on SHA-1, and supports keys from 128-bit to 512-bit. SHACAL-2 is a 256-bit block cipher based upon the larger hash function SHA-256....
block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
s.
Cryptanalysis and validation
For a hash function for which L is the number of bits in the message digest, finding a message that corresponds to a given message digest can always be done using a brute force search in 2L evaluations. This is called a preimage attackPreimage attack
In cryptography, the preimage attack is a classification of attacks on hash functions for finding a message that has a specific hash value.There are two types of preimage attacks:...
and may or may not be practical depending on L and the particular computing environment. The second criterion, finding two different messages that produce the same message digest, known as a collision, requires on average only 2L/2 evaluations using a birthday attack
Birthday attack
A birthday attack is a type of cryptographic attack that exploits the mathematics behind the birthday problem in probability theory. This attack can be used to abuse communication between two or more parties...
. For the latter reason the strength of a hash function is usually compared to a symmetric cipher of half the message digest length. Thus SHA-1 was originally thought to have 80-bit strength.
Cryptographers have produced collision pairs for SHA-0 and have found algorithms that should produce SHA-1 collisions in far fewer than the originally expected 280 evaluations.
In terms of practical security, a major concern about these new attacks is that they might pave the way to more efficient ones. Whether this is the case is yet to be seen, but a migration to stronger hashes is believed to be prudent. Some of the applications that use cryptographic hashes, such as password storage, are only minimally affected by a collision attack. Constructing a password that works for a given account requires a preimage attack
Preimage attack
In cryptography, the preimage attack is a classification of attacks on hash functions for finding a message that has a specific hash value.There are two types of preimage attacks:...
, as well as access to the hash of the original password, which may or may not be trivial. Reversing password encryption (e.g. to obtain a password to try against a user's account elsewhere) is not made possible by the attacks. (However, even a secure password hash can't prevent brute-force attacks on weak passwords
Password strength
Password strength is a measure of the effectiveness of a password in resisting guessing and brute-force attacks. In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly...
.)
In the case of document signing, an attacker could not simply fake a signature from an existing document—the attacker would have to produce a pair of documents, one innocuous and one damaging, and get the private key holder to sign the innocuous document. There are practical circumstances in which this is possible; until the end of 2008, it was possible to create forged SSL
Transport Layer Security
Transport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
certificates using an MD5
MD5
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
collision.
Due to the block and iterative structure of the algorithms and the absence of additional final steps, all SHA functions are vulnerable to length-extension and partial-message collision attacks. These attacks allow an attacker to forge a message, signed only by a keyed hash -
 or
or  - by extending the message and recalculating the hash without knowing the key. The simplest improvement to prevent these attacks is to hash twice -
- by extending the message and recalculating the hash without knowing the key. The simplest improvement to prevent these attacks is to hash twice - 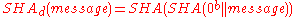 (
( - zero block, length is equal to block size of hash function).
- zero block, length is equal to block size of hash function).SHA-0
At CRYPTOCRYPTO (conference)
CRYPTO, the International Cryptology Conference, is one of the largest academic conferences in cryptography and cryptanalysis. It is organized by the International Association for Cryptologic Research , and it is held yearly in August in Santa Barbara, California at the University of California,...
98, two French researchers, Florent Chabaud and Antoine Joux, presented an attack on SHA-0 (Chabaud and Joux, 1998): collisions
Hash collision
Not to be confused with wireless packet collision.In computer science, a collision or clash is a situation that occurs when two distinct pieces of data have the same hash value, checksum, fingerprint, or cryptographic digest....
can be found with complexity 261, fewer than the 280 for an ideal hash function of the same size.
In 2004, Biham
Eli Biham
Eli Biham is an Israeli cryptographer and cryptanalyst, currently a professor at the Technion Israeli Institute of Technology Computer Science department. Starting from October 2008, Biham is the dean of the Technion Computer Science department, after serving for two years as chief of CS graduate...
and Chen found near-collisions for SHA-0—two messages that hash to nearly the same value; in this case, 142 out of the 160 bits are equal. They also found full collisions of SHA-0 reduced to 62 out of its 80 rounds.
Subsequently, on 12 August 2004, a collision for the full SHA-0 algorithm was announced by Joux, Carribault, Lemuet, and Jalby. This was done by using a generalization of the Chabaud and Joux attack. Finding the collision had complexity 251 and took about 80,000 CPU hours on a supercomputer
Supercomputer
A supercomputer is a computer at the frontline of current processing capacity, particularly speed of calculation.Supercomputers are used for highly calculation-intensive tasks such as problems including quantum physics, weather forecasting, climate research, molecular modeling A supercomputer is a...
with 256 Itanium 2 processors. (Equivalent to 13 days of full-time use of the computer.)
On 17 August 2004, at the Rump Session of CRYPTO 2004, preliminary results were announced by Wang
Xiaoyun Wang
Wang Xiaoyun is a researcher and professor in the Department of Mathematics and System Science, Shandong University, Shandong, China....
, Feng, Lai, and Yu, about an attack on MD5
MD5
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
, SHA-0 and other hash functions. The complexity of their attack on SHA-0 is 240, significantly better than the attack by Joux et al.
In February 2005, an attack by Xiaoyun Wang, Yiqun Lisa Yin, and Hongbo Yu was announced which could find collisions in SHA-0 in 239 operations.
SHA-1
In light of the results for SHA-0, some experts suggested that plans for the use of SHA-1 in new cryptosystemCryptosystem
There are two different meanings of the word cryptosystem. One is used by the cryptographic community, while the other is the meaning understood by the public.- General meaning :...
s should be reconsidered. After the CRYPTO 2004 results were published, NIST announced that they planned to phase out the use of SHA-1 by 2010 in favor of the SHA-2 variants.
In early 2005, Rijmen
Vincent Rijmen
Vincent Rijmen is a Belgian cryptographer and one of the two designers of the Rijndael, the Advanced Encryption Standard. Rijmen is also the co-designer of the WHIRLPOOL cryptographic hash function, and the block ciphers Anubis, KHAZAD, Square, NOEKEON and SHARK.In 1993, Rijmen obtained a degree...
and Oswald published an attack on a reduced version of SHA-1—53 out of 80 rounds—which finds collisions with a computational effort of fewer than 280 operations.
In February 2005, an attack by Xiaoyun Wang
Xiaoyun Wang
Wang Xiaoyun is a researcher and professor in the Department of Mathematics and System Science, Shandong University, Shandong, China....
, Yiqun Lisa Yin, Bayarjargal, and Hongbo Yu was announced. The attacks can find collisions in the full version of SHA-1, requiring fewer than 269 operations. (A brute-force search
Brute-force search
In computer science, brute-force search or exhaustive search, also known as generate and test, is a trivial but very general problem-solving technique that consists of systematically enumerating all possible candidates for the solution and checking whether each candidate satisfies the problem's...
would require 280 operations.)
The authors write:
"In particular, our analysis is built upon the original differential attack on SHA-0 [sic], the near collision attack on SHA-0, the multiblock collision techniques, as well as the message modification techniques used in the collision search attack on MD5. Breaking SHA-1 would not be possible without these powerful analytical techniques." The authors have presented a collision for 58-round SHA-1, found with 233 hash operations.
The paper with the full attack description was published in August 2005 at the CRYPTO conference.
In an interview, Yin states that, "Roughly, we exploit the following two weaknesses: One is that the file preprocessing step is not complicated enough; another is that certain math operations in the first 20 rounds have unexpected security problems."
On 17 August 2005, an improvement on the SHA-1 attack was announced on behalf of Xiaoyun Wang, Andrew Yao
Andrew Yao
Andrew Chi-Chih Yao is a prominent computer scientist and computational theorist. Yao used the minimax theorem to prove what is now known as Yao's Principle.Yao was born in Shanghai, China...
and Frances Yao
Frances Yao
Frances Foong Yao is professor and head of the department of computer science at the City University of Hong Kong.After receiving a B.S. in mathematics from National Taiwan University in 1969, Yao did her Ph.D. studies under the supervision of Michael J. Fischer at the Massachusetts Institute of...
at the CRYPTO 2005 rump session, lowering the complexity required for finding a collision in SHA-1 to 263. On 18 December 2007 the details of this result were explained and verified by Martin Cochran.
Christophe De Cannière and Christian Rechberger further improved the attack on SHA-1 in "Finding SHA-1 Characteristics: General Results and Applications," receiving the Best Paper Award at ASIACRYPT
Asiacrypt
Asiacrypt is an important international conference for cryptography research. The full name of the conference is currently International Conference on the Theory and Application of Cryptology and Information Security, though this has varied over time...
2006. A two-block collision for 64-round SHA-1 was presented, found using unoptimized methods with 235 compression function evaluations. As this attack requires the equivalent of about 235 evaluations, it is considered to be a significant theoretical break. Their attack was extended further to 73 rounds (of 80) in 2010 by Grechnikov. In order to find an actual collision in the full 80 rounds of the hash function, however, massive amounts of computer time are required. To that end, a collision search for SHA-1 using the distributed computing platform BOINC began August 8, 2007, organized by the Graz University of Technology
Graz University of Technology
The Graz University of Technology is the second largest university in Styria, Austria, after the University of Graz. Austria has three universities of technology – in Graz, in Leoben, and in Vienna. The Graz University of Technology was founded in 1811 by Archduke John of Austria. TUG, as the...
. The effort was abandoned May 12, 2009 due to lack of progress.
At the Rump Session of CRYPTO 2006, Christian Rechberger and Christophe De Cannière claimed to have discovered a collision attack on SHA-1 that would allow an attacker to select at least parts of the message.
In 2008, an attack methodology by Stéphane Manuel may produce hash collisions with an estimated theoretical complexity of 251 to 257 operations.
Cameron McDonald, Philip Hawkes and Josef Pieprzyk presented a hash collision attack with claimed complexity 252 at the Rump session of Eurocrypt 2009. However, the accompanying paper, "Differential Path for SHA-1 with complexity O
Big O notation
In mathematics, big O notation is used to describe the limiting behavior of a function when the argument tends towards a particular value or infinity, usually in terms of simpler functions. It is a member of a larger family of notations that is called Landau notation, Bachmann-Landau notation, or...
(252)" has been withdrawn due to the authors' discovery that their estimate was incorrect.
Marc Stevens runs a project called HashClash, implementing a differential path attack against SHA-1. On 8 November 2010, he claimed he had a fully working near-collision attack against full SHA-1 working with an estimated complexity equivalent to 257.5 SHA-1 compressions.
Official validation
Implementations of all FIPS-approved security functions can be officially validated through the CMVP program, jointly run by the National Institute of Standards and TechnologyNational Institute of Standards and Technology
The National Institute of Standards and Technology , known between 1901 and 1988 as the National Bureau of Standards , is a measurement standards laboratory, otherwise known as a National Metrological Institute , which is a non-regulatory agency of the United States Department of Commerce...
(NIST) and the Communications Security Establishment
Communications Security Establishment
The Communications Security Establishment Canada is the Canadian government's national cryptologic agency. Administered under the Department of National Defence , it is charged with the duty of keeping track of foreign signals intelligence , and protecting Canadian government electronic...
(CSE). For informal verification, a package to generate a high number of test vectors is made available for download on the NIST site; the resulting verification however does not replace, in any way, the formal CMVP validation, which is required by law for certain applications.
, there are nearly 1400 validated implementations of SHA-1, with around a dozen of them capable of handling messages with a length in bits not a multiple of eight (see SHS Validation List).
Example hashes
These are examples of SHA-1 digests. ASCIIASCII
The American Standard Code for Information Interchange is a character-encoding scheme based on the ordering of the English alphabet. ASCII codes represent text in computers, communications equipment, and other devices that use text...
encoding is used for all messages.
SHA1("The quick brown fox jumps over the lazy dog
The quick brown fox jumps over the lazy dog
"The quick brown fox jumps over the lazy dog" is an English-language pangram, that is, a phrase that contains all of the letters of the alphabet. It has been used to test typewriters and computer keyboards, and in other applications involving all of the letters in the English alphabet...
")
= 2fd4e1c6 7a2d28fc ed849ee1 bb76e739 1b93eb12
Even a small change in the message will, with overwhelming probability, result in a completely different hash due to the avalanche effect
Avalanche effect
In cryptography, the avalanche effect refers to a desirable property of cryptographic algorithms, typically block ciphers and cryptographic hash functions. The avalanche effect is evident if, when an input is changed slightly the output changes significantly...
. For example, changing
dog to cog produces a hash with different values for 81 of the 160 bits:SHA1("The quick brown fox jumps over the lazy cog")
= de9f2c7f d25e1b3a fad3e85a 0bd17d9b 100db4b3
The hash of the zero-length string is:
SHA1("")
= da39a3ee 5e6b4b0d 3255bfef 95601890 afd80709
SHA-1 pseudocode
PseudocodePseudocode
In computer science and numerical computation, pseudocode is a compact and informal high-level description of the operating principle of a computer program or other algorithm. It uses the structural conventions of a programming language, but is intended for human reading rather than machine reading...
for the SHA-1 algorithm follows:
Note 1: All variables are unsigned 32 bits and wrap modulo 232 when calculating
Note 2: All constants in this pseudo code are in big endian
Endianness
In computing, the term endian or endianness refers to the ordering of individually addressable sub-components within the representation of a larger data item as stored in external memory . Each sub-component in the representation has a unique degree of significance, like the place value of digits...
.
Within each word, the most significant byte is stored in the leftmost byte position
Initialize variables:
h0 = 0x67452301
h1 = 0xEFCDAB89
h2 = 0x98BADCFE
h3 = 0x10325476
h4 = 0xC3D2E1F0
Pre-processing:
append the bit '1' to the message
append 0 ≤ k < 512 bits '0', so that the resulting message length (in bits)
is congruent
Modular arithmetic
In mathematics, modular arithmetic is a system of arithmetic for integers, where numbers "wrap around" after they reach a certain value—the modulus....
to 448 (mod 512)
append length of message (before pre-processing), in bits, as 64-bit big-endian
Endianness
In computing, the term endian or endianness refers to the ordering of individually addressable sub-components within the representation of a larger data item as stored in external memory . Each sub-component in the representation has a unique degree of significance, like the place value of digits...
integer
Process the message in successive 512-bit chunks:
break message into 512-bit chunks
for each chunk
break chunk into sixteen 32-bit big-endian words w[i], 0 ≤ i ≤ 15
Extend the sixteen 32-bit words into eighty 32-bit words:
for i from 16 to 79
w[i] = (w[i-3] xor w[i-8] xor w[i-14] xor w[i-16]) leftrotate
Circular shift
In combinatorial mathematics, a circular shift is the operation of rearranging the entries in a tuple, either by moving the final entry to the first position, while shifting all other entries to the next position, or by performing the inverse operation...
1
Initialize hash value for this chunk:
a = h0
b = h1
c = h2
d = h3
e = h4
Main loop:
for i from 0 to 79
if 0 ≤ i ≤ 19 then
f = (b and c) or ((not b) and d)
k = 0x5A827999
else if 20 ≤ i ≤ 39
f = b xor c xor d
k = 0x6ED9EBA1
else if 40 ≤ i ≤ 59
f = (b and c) or (b and d) or (c and d)
k = 0x8F1BBCDC
else if 60 ≤ i ≤ 79
f = b xor c xor d
k = 0xCA62C1D6
temp = (a leftrotate 5) + f + e + k + w[i]
e = d
d = c
c = b leftrotate 30
b = a
a = temp
Add this chunk's hash to result so far:
h0 = h0 + a
h1 = h1 + b
h2 = h2 + c
h3 = h3 + d
h4 = h4 + e
Produce the final hash value (big-endian):
digest = hash = h0 append h1 append h2 append h3 append h4
The constant values used are chosen as nothing up my sleeve number
Nothing up my sleeve number
In cryptography, nothing up my sleeve numbers are any numbers which, by their construction, are above suspicion of hidden properties. They are used in creating cryptographic functions such as hashes and ciphers. These algorithms often need randomized constants for mixing or initialization purposes...
s: the four round constants
k are 230 times the square roots of 2, 3, 5 and 10. The first four starting values for h0 through h3 are the same as the MD5 algorithm, and the fifth (for h4) is similar.Instead of the formulation from the original FIPS PUB 180-1 shown, the following equivalent expressions may be used to compute
f in the main loop above:(0 ≤ i ≤ 19): f = d xor (b and (c xor d)) (alternative 1)
(0 ≤ i ≤ 19): f = (b and c) xor ((not b) and d) (alternative 2)
(0 ≤ i ≤ 19): f = (b and c) + ((not b) and d) (alternative 3)
(0 ≤ i ≤ 19): f = vec_sel(d, c, b) (alternative 4)
(40 ≤ i ≤ 59): f = (b and c) or (d and (b or c)) (alternative 1)
(40 ≤ i ≤ 59): f = (b and c) or (d and (b xor c)) (alternative 2)
(40 ≤ i ≤ 59): f = (b and c) + (d and (b xor c)) (alternative 3)
(40 ≤ i ≤ 59): f = (b and c) xor (b and d) xor (c and d) (alternative 4)
Max Locktyukhin has also shown that for the rounds 32–79 the computation of:
w[i] = (w[i-3] xor w[i-8] xor w[i-14] xor w[i-16]) leftrotate
Circular shift
In combinatorial mathematics, a circular shift is the operation of rearranging the entries in a tuple, either by moving the final entry to the first position, while shifting all other entries to the next position, or by performing the inverse operation...
1
can be replaced with:
w[i] = (w[i-6] xor w[i-16] xor w[i-28] xor w[i-32]) leftrotate
Circular shift
In combinatorial mathematics, a circular shift is the operation of rearranging the entries in a tuple, either by moving the final entry to the first position, while shifting all other entries to the next position, or by performing the inverse operation...
2
This transformation keeps all operands 64-bit aligned and, by removing the dependency of
w[i] on w[i-3], allows efficient SIMD implementation with a vector length of 4 such as x86 SSEStreaming SIMD Extensions
In computing, Streaming SIMD Extensions is a SIMD instruction set extension to the x86 architecture, designed by Intel and introduced in 1999 in their Pentium III series processors as a reply to AMD's 3DNow! . SSE contains 70 new instructions, most of which work on single precision floating point...
instructions.
See also
- Comparison of cryptographic hash functionsComparison of cryptographic hash functionsThe following tables compare general and technical information for a number of cryptographic hash functions.- General information :Basic general information about the cryptographic hash functions: year, designer, references, etc.- Compression function :...
- Digital timestamping
- Hash collisionHash collisionNot to be confused with wireless packet collision.In computer science, a collision or clash is a situation that occurs when two distinct pieces of data have the same hash value, checksum, fingerprint, or cryptographic digest....
- HashcashHashcashHashcash is a proof-of-work system designed to limit email spam and denial-of-service attacks. It was proposed in March 1997 by Adam Back.-How it works:...
- International Association for Cryptologic ResearchInternational Association for Cryptologic ResearchThe International Association for Cryptologic Research is a non-profit scientific organization whose purpose is to further research in cryptology and related fields...
(IACR) - RIPEMD-160
- Secure Hash StandardSecure Hash StandardThe Secure Hash Standard is a set of cryptographically secure hash algorithms specified by the National Institute of Standards and Technology .The SHS standard specifies a number of Secure Hash Algorithms, for example SHA-1, SHA-256 and SHA-512....
- sha1sumSha1sumsha1sum is a computer program that calculates and verifies SHA-1 hashes. It is commonly used to verify the integrity of files. It is installed by default in most Unix-like operating systems...
- Tiger
- Whirlpool
Standards: SHA-1, SHA-2
- CSRC Cryptographic Toolkit – Official NISTNational Institute of Standards and TechnologyThe National Institute of Standards and Technology , known between 1901 and 1988 as the National Bureau of Standards , is a measurement standards laboratory, otherwise known as a National Metrological Institute , which is a non-regulatory agency of the United States Department of Commerce...
site for the Secure Hash Standard- FIPS 180-2: Secure Hash Standard (SHS) (PDFPortable Document FormatPortable Document Format is an open standard for document exchange. This file format, created by Adobe Systems in 1993, is used for representing documents in a manner independent of application software, hardware, and operating systems....
, 236 kB) – Current version of the Secure Hash Standard (SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512), 1 August 2002, amended 25 February 2004
- FIPS 180-2: Secure Hash Standard (SHS) (PDF
- RFC 3174 (with sample C implementation)
Cryptanalysis
- Interview with Yiqun Lisa Yin concerning the attack on SHA-1
- Lenstra's Summary of impact of the February 2005 cryptanalytic results
- Explanation of the successful attacks on SHA-1 (3 pages, 2006)
- Cryptography Research – Hash Collision Q&A
- Online SHA1 hash crack using Rainbow tables
- Hash Project Web Site: software- and hardware-based cryptanalysis of SHA-1
- HashClash - Framework for MD5 & SHA-1 Differential Path Construction and Chosen-Prefix Collisions for MD5
Implementations
LibgcryptLibgcrypt
libgcrypt is a cryptographic library developed as a separated module of GnuPG . It can also be used independently of GnuPG, although it requires its error-reporting library....
: A general purpose cryptographic library based on the code from GNU Privacy Guard
GNU Privacy Guard
GNU Privacy Guard is a GPL Licensed alternative to the PGP suite of cryptographic software. GnuPG is compliant with RFC 4880, which is the current IETF standards track specification of OpenPGP...
.
OpenSSL
OpenSSL
OpenSSL is an open source implementation of the SSL and TLS protocols. The core library implements the basic cryptographic functions and provides various utility functions...
: The widely used OpenSSL
crypto library includes freeFree software
Free software, software libre or libre software is software that can be used, studied, and modified without restriction, and which can be copied and redistributed in modified or unmodified form either without restriction, or with restrictions that only ensure that further recipients can also do...
, open-source
Open source
The term open source describes practices in production and development that promote access to the end product's source materials. Some consider open source a philosophy, others consider it a pragmatic methodology...
– implementations of SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512
cryptlib
Cryptlib
cryptlib is an open source cross-platform software security toolkit library. It is distributed under the Sleepycat License, a free software license compatible with the GNU General Public License...
: an open source
Open source
The term open source describes practices in production and development that promote access to the end product's source materials. Some consider open source a philosophy, others consider it a pragmatic methodology...
cross-platform software security toolkit library
Crypto++
Crypto++
Crypto++ is a free and open source C++ class library of cryptographic algorithms and schemes written by Wei Dai. Crypto++ has been widely used in academia, student projects, open source and non-commercial projects, as well as businesses...
: A public domain C++ class library of cryptographic schemes, including implementations of the SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512 algorithms.
Bouncy Castle
Bouncy castle (cryptography)
Bouncy Castle is a collection of APIs used in cryptography. It includes APIs for both the Java and the C# programming languages.Bouncy Castle is Australian in origin and thus American restrictions on the export of cryptographic software do not apply to it....
: The Bouncy Castle Library is a free Java and C# class library that contains implementations of the SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512 algorithms as well as other algorithms like Whirlpool, Tiger
Tiger (hash)
In cryptography, Tiger is a cryptographic hash function designed by Ross Anderson and Eli Biham in 1995 for efficiency on 64-bit platforms. The size of a Tiger hash value is 192 bits. Truncated versions can be used for compatibility with protocols assuming a particular hash size...
, RIPEMD
RIPEMD
RIPEMD-160 is a 160-bit message digest algorithm developed in Leuven, Belgium, by Hans Dobbertin, Antoon Bosselaers and Bart Preneel at the COSIC research group at the Katholieke Universiteit Leuven, and first published in 1996...
, GOST-3411, MD2, MD4
MD4
The MD4 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1990. The digest length is 128 bits. The algorithm has influenced later designs, such as the MD5, SHA-1 and RIPEMD algorithms....
and MD5
MD5
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit hash value. Specified in RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check data integrity...
.
jsSHA: A cross-browser JavaScript
JavaScript
JavaScript is a prototype-based scripting language that is dynamic, weakly typed and has first-class functions. It is a multi-paradigm language, supporting object-oriented, imperative, and functional programming styles....
library for client-side calculation of SHA digests, despite the fact that JavaScript does not natively support the 64-bit operations required for SHA-384 and SHA-512.
LibTomCrypt: A portable ISO C cryptographic toolkit, Public Domain.
Intel: Fast implementation of SHA-1 using Intel Supplemental SSE3 extensions, free for commercial or non-commercial use.
md5deep
Md5deep
md5deep is a software package used in the computer security, system administration and computer forensics communities for purposes of running large numbers of files through any of several different cryptographic digests...
: A set of programs to compute MD5, SHA-1, SHA-256, Tiger, or Whirlpool cryptographic message digests on an arbitrary number of files. It is used in computer security, system administration and computer forensics communities for purposes of running large numbers of files through any of several different cryptographic digests. It is similar to the md5sum
Md5sum
md5sum is a computer program that calculates and verifies 128-bit MD5 hashes, as described in RFC 1321. The MD5 hash functions as a compact digital fingerprint of a file. As with all such hashing algorithms, there is theoretically an unlimited number of files that will have any given MD5 hash...
.

