.gif)
Acegi security framework (Java)
Encyclopedia
Spring Security is a Java
/Java EE framework that provides authentication
, authorization
and other security features for enterprise applications. The project was started in late 2003 as 'Acegi Security' by Ben Alex, with it being publicly released under the Apache License
in March 2004. Subsequently, Acegi was incorporated into the Spring portfolio as Spring Security, an official Spring sub-project. The first public release under the new name was Spring Security 2.0.0 in April 2008, with commercial support and training available from SpringSource.
Java (programming language)
Java is a programming language originally developed by James Gosling at Sun Microsystems and released in 1995 as a core component of Sun Microsystems' Java platform. The language derives much of its syntax from C and C++ but has a simpler object model and fewer low-level facilities...
/Java EE framework that provides authentication
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
, authorization
Authorization
Authorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy...
and other security features for enterprise applications. The project was started in late 2003 as 'Acegi Security' by Ben Alex, with it being publicly released under the Apache License
Apache License
The Apache License is a copyfree free software license authored by the Apache Software Foundation . The Apache License requires preservation of the copyright notice and disclaimer....
in March 2004. Subsequently, Acegi was incorporated into the Spring portfolio as Spring Security, an official Spring sub-project. The first public release under the new name was Spring Security 2.0.0 in April 2008, with commercial support and training available from SpringSource.
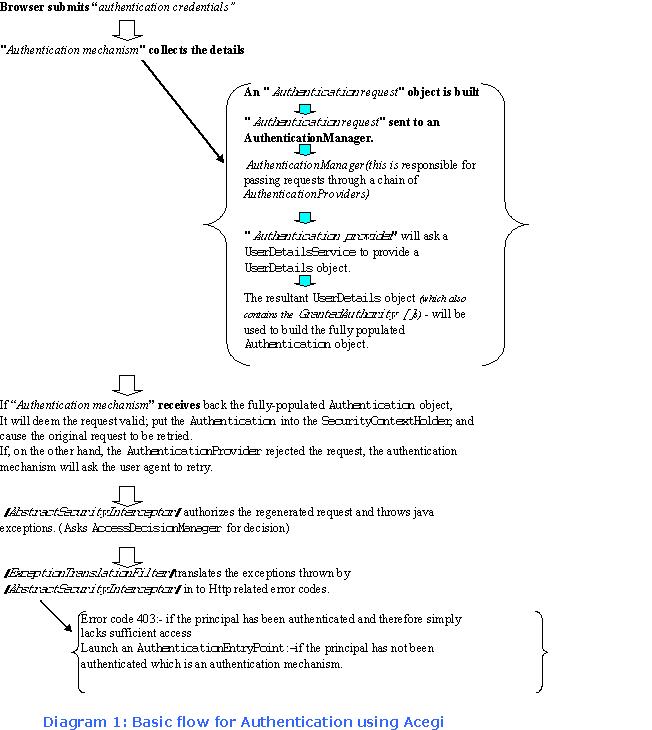
Authentication flow
Diagram1 shows the basic flow of an authentication request using the Spring Security system. It shows the different filters and how they interact from the initial browser request, to either a successful authentication or an HTTP 403 error.
Key authentication features
- LDAPLightweight Directory Access ProtocolThe Lightweight Directory Access Protocol is an application protocol for accessing and maintaining distributed directory information services over an Internet Protocol network...
(using both bind-based and password comparison strategies) for centralization of authentication information. - Single sign-onSingle sign-onSingle sign-on is a property of access control of multiple related, but independent software systems. With this property a user logs in once and gains access to all systems without being prompted to log in again at each of them...
capabilities using the popular Central Authentication ServiceCentral Authentication ServiceThe Central Authentication Service is a single sign-on protocol for the web. Its purpose is to permit a user to access multiple applications while providing their credentials only once. It also allows web applications to authenticate users without gaining access to a user's security credentials,...
. - Java Authentication and Authorization ServiceJava Authentication and Authorization ServiceJava Authentication and Authorization Service, or JAAS, pronounced "Jazz", is a Java security framework for user-centric security to augment the Java code-based security...
(JAAS) LoginModule, a standards-based method for authentication used within Java. Note this feature is only a delegation to a JAAS Loginmodule. - Basic access authentication as defined through the IETF Request for CommentsRequest for CommentsIn computer network engineering, a Request for Comments is a memorandum published by the Internet Engineering Task Force describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems.Through the Internet Society, engineers and...
1945 standard. - Digest access authenticationDigest access authenticationDigest access authentication is one of the agreed upon methods a web server can use to negotiate credentials with a user's web browser. It uses encryption to send the password over the network which is safer than the Basic access authentication that sends plaintext.Technically digest...
as defined through the IETF Request for CommentsRequest for CommentsIn computer network engineering, a Request for Comments is a memorandum published by the Internet Engineering Task Force describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems.Through the Internet Society, engineers and...
2617 and RFC 2069 standard. - X.509X.509In cryptography, X.509 is an ITU-T standard for a public key infrastructure and Privilege Management Infrastructure . X.509 specifies, amongst other things, standard formats for public key certificates, certificate revocation lists, attribute certificates, and a certification path validation...
client certificate presentation over the Secure Sockets Layer standard. - CA, Inc SiteMinder for authentication (a popular commercial access management product).
- Su (Unix)Su (Unix)The su command, also referred to as super user substitute user, spoof user, set user or switch user, allows a computer operator to change the current user account associated with the running virtual console....
-like support for switching principal identity over a HTTP or HTTPSHttpsHypertext Transfer Protocol Secure is a combination of the Hypertext Transfer Protocol with SSL/TLS protocol to provide encrypted communication and secure identification of a network web server...
connection. - CAPTCHACAPTCHAA CAPTCHA is a type of challenge-response test used in computing as an attempt to ensure that the response is generated by a person. The process usually involves one computer asking a user to complete a simple test which the computer is able to generate and grade...
support for detecting human users. - Central Authentication ServiceCentral Authentication ServiceThe Central Authentication Service is a single sign-on protocol for the web. Its purpose is to permit a user to access multiple applications while providing their credentials only once. It also allows web applications to authenticate users without gaining access to a user's security credentials,...
(CAS) single sign-on integration. - Run-as replacement, which enables an operation to assume a different security identity.
- Anonymous authentication, which means that even unauthenticated principals are allocated a security identity.
- Container adapter (custom realm) support for Apache TomcatApache TomcatApache Tomcat is an open source web server and servlet container developed by the Apache Software Foundation...
, Resin, JBossJBossJBoss Application Server is an open-source Java EE-based application server. An important distinction for this class of software is that it not only implements a server that runs on Java, but it actually implements the Java EE part of Java...
and Jetty (web server)Jetty (web server)Jetty is a pure Java-based HTTP client/server, WebSocket client/server and servlet container developed as a free and open source project as part of the Eclipse Foundation...
. - Windows NTLMNTLMIn a Windows network, NTLM is a suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users....
to enable browser integration (experimental). - Web form authentication, similar to the Servlet container specification.
- "Remember-me" support via HTTP CookieHTTP cookieA cookie, also known as an HTTP cookie, web cookie, or browser cookie, is used for an origin website to send state information to a user's browser and for the browser to return the state information to the origin site...
s. - Concurrent session support, which limits the number of simultaneous logins permitted by a principal.
- Full support for customization and plugging in custom authentication implementations.
Key authorization features
- AspectJAspectJAspectJ is an aspect-oriented extension created at PARC for the Java programming language. It is available in Eclipse Foundation open-source projects, both stand-alone and integrated into Eclipse. AspectJ has become the widely-used de-facto standard for AOP by emphasizing simplicity and usability...
method invocation authorization. - HTTP authorization of web request URLUniform Resource LocatorIn computing, a uniform resource locator or universal resource locator is a specific character string that constitutes a reference to an Internet resource....
s using a choice of Apache AntApache AntApache Ant is a software tool for automating software build processes. It is similar to Make but is implemented using the Java language, requires the Java platform, and is best suited to building Java projects....
paths or regular expressions.
Instance-based security features
- Used for specifying Access control listAccess control listAn access control list , with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject...
s applicable to domain objects. - Spring Security offers a repository for storing, retrieving, and modifying ACLs in a databaseDatabaseA database is an organized collection of data for one or more purposes, usually in digital form. The data are typically organized to model relevant aspects of reality , in a way that supports processes requiring this information...
. - AuthorizationAuthorizationAuthorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy...
features are provided to enforce policies before and after method invocations.
Other features
- Software localization so user interfaceUser interfaceThe user interface, in the industrial design field of human–machine interaction, is the space where interaction between humans and machines occurs. The goal of interaction between a human and a machine at the user interface is effective operation and control of the machine, and feedback from the...
messages can be in any language. - Channel security, to automatically switch between HTTP and HTTPSHttpsHypertext Transfer Protocol Secure is a combination of the Hypertext Transfer Protocol with SSL/TLS protocol to provide encrypted communication and secure identification of a network web server...
upon meeting particular rules. - CachingCacheIn computer engineering, a cache is a component that transparently stores data so that future requests for that data can be served faster. The data that is stored within a cache might be values that have been computed earlier or duplicates of original values that are stored elsewhere...
in all database-touching areas of the framework. - Publishing of messages to facilitate event-driven programmingEvent-driven programmingIn computer programming, event-driven programming or event-based programming is a programming paradigm in which the flow of the program is determined by events—i.e., sensor outputs or user actions or messages from other programs or threads.Event-driven programming can also be defined as an...
. - Support for performing integration testing via JUnitJUnitJUnit is a unit testing framework for the Java programming language. JUnit has been important in the development of test-driven development, and is one of a family of unit testing frameworks collectively known as xUnit that originated with SUnit....
. - Spring Security itself has comprehensive JUnitJUnitJUnit is a unit testing framework for the Java programming language. JUnit has been important in the development of test-driven development, and is one of a family of unit testing frameworks collectively known as xUnit that originated with SUnit....
isolation tests. - Several sample applications, detailed JavaDocsJavadocJavadoc is a documentation generator from Sun Microsystems for generating API documentation in HTML format from Java source code.The "doc comments" format used by Javadoc is the de facto industry standard for documenting Java classes. Some IDEs, such as Netbeans and Eclipse automatically generate...
and a reference guide. - Web framework independence.

