Trusted timestamping
Encyclopedia
Trusted timestamping is the process of securely
keeping track of the creation and modification time of a document. Security
here means that no one — not even the owner of the document — should be able to change it once it has been recorded provided that the timestamper's integrity is never compromised.
The administrative aspect involves setting up a publicly available, trusted timestamp management infrastructure to collect, process and renew timestamps.
discovered Hooke's law
in 1660, he did not want to publish it yet, but wanted to be able to claim priority. So he published the anagram
ceiiinosssttuv and later published the translation ut tensio sic vis (Latin for "as is the extension, so is the force"). Similarly, Galileo
first published his discovery of the phases of Venus in the anagram form. A modern example is the case of an industrial research organization that may later need to prove, for patent purposes, that they made a particular discovery on a particular date; since magnetic media can be altered easily, this may be a nontrivial issue. One possible solution is for a researcher to compute and record in a hardcopy laboratory notebook a cryptographic hash of the relevant data file. In the future, should there be a need to prove the version of this file retrieved from a backup tape has not been altered, the hash function could be recomputed and compared with the hash value recorded in that paper notebook.
Coverage in standards:
For systematic classification and evaluation of timestamping schemes see works by Masashi Une.
 According to the RFC 3161 standard, a trusted timestamp is a timestamp
According to the RFC 3161 standard, a trusted timestamp is a timestamp
issued by a trusted third party
(TTP) acting as a Time Stamping Authority (TSA). It is used to prove the existence of certain data before a certain point (e.g. contracts, research data, medical records,...) without the possibility that the owner can backdate the timestamps. Multiple TSAs can be used to increase reliability and reduce vulnerability.
The newer ANSI ASC X9.95 Standard
for trusted timestamps
augments the RFC 3161 standard with data-level security requirements to ensure data integrity
against a reliable time source that is provable to any third party. This standard has been applied to authenticating digitally signed data for regulatory compliance, financial transactions, and legal evidence.
with the private key of the TSA. This signed hash + the timestamp is sent back to the requester of the timestamp who stores these with the original data (see diagram).
Since the original data cannot be calculated from the hash (because the hash function
is a one way function), the TSA never gets to see the original data, which allows the use of this method for confidential data.
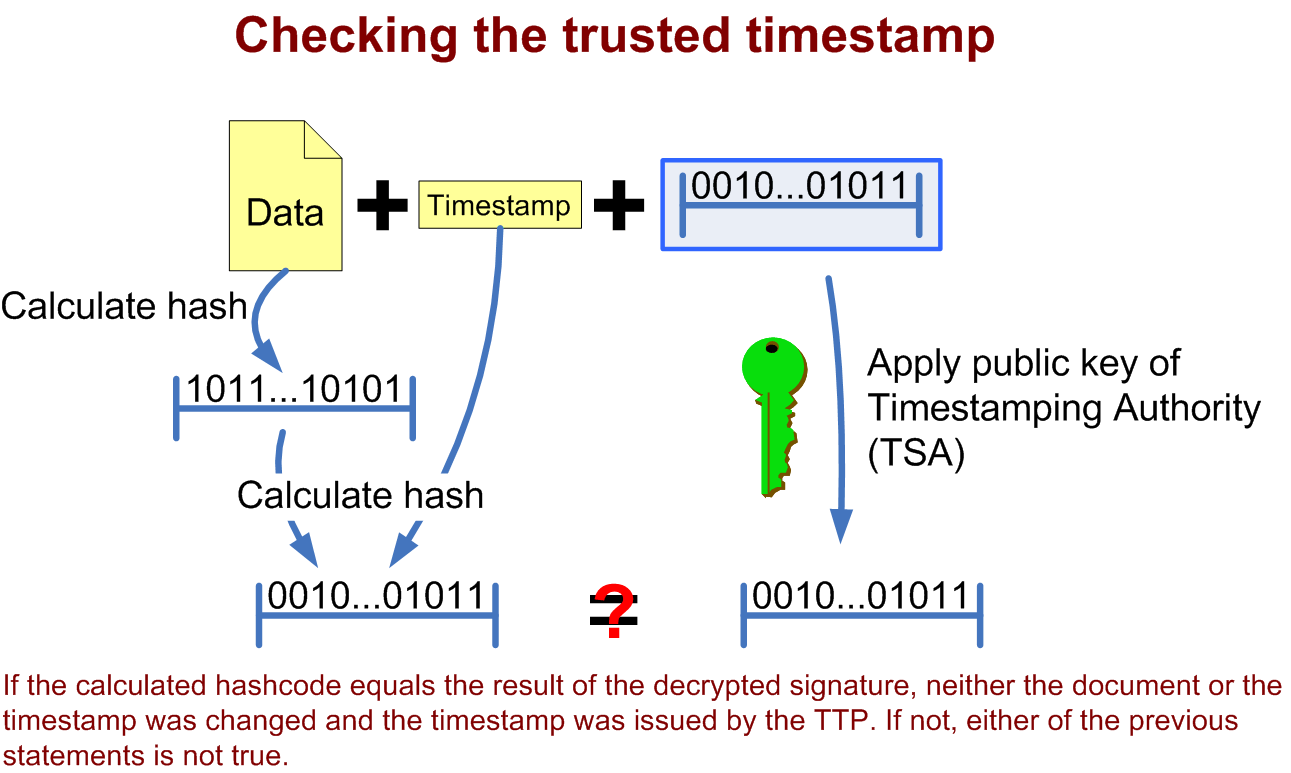 Anyone trusting the timestamper can then verify that the document was not created after the date that the timestamper vouches. It can also no longer be repudiated that the requester of the timestamp was in possession of the original data at the time given by the timestamp. To prove this (see diagram) the hash
Anyone trusting the timestamper can then verify that the document was not created after the date that the timestamper vouches. It can also no longer be repudiated that the requester of the timestamp was in possession of the original data at the time given by the timestamp. To prove this (see diagram) the hash
of the original data is calculated, the timestamp given by the TSA is appended to it and the hash of the result of this concatenation is calculated, call this hash A.
Then the digital signature
of the TSA needs to be validated. This can be done by checking that the signed hash provided by the TSA was indeed signed with their private key by digital signature
verification. The hash A is compared with the hash B inside the signed TSA message to confirm they are equal, proving that the timestamp and message is unaltered and was issued by the TSA. If not, then either the timestamp was altered or the timestamp was not issued by the TSA.
Computer security
Computer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
keeping track of the creation and modification time of a document. Security
here means that no one — not even the owner of the document — should be able to change it once it has been recorded provided that the timestamper's integrity is never compromised.
The administrative aspect involves setting up a publicly available, trusted timestamp management infrastructure to collect, process and renew timestamps.
History
The idea of timestamping information is actually centuries old. For example, when Robert HookeRobert Hooke
Robert Hooke FRS was an English natural philosopher, architect and polymath.His adult life comprised three distinct periods: as a scientific inquirer lacking money; achieving great wealth and standing through his reputation for hard work and scrupulous honesty following the great fire of 1666, but...
discovered Hooke's law
Hooke's law
In mechanics, and physics, Hooke's law of elasticity is an approximation that states that the extension of a spring is in direct proportion with the load applied to it. Many materials obey this law as long as the load does not exceed the material's elastic limit. Materials for which Hooke's law...
in 1660, he did not want to publish it yet, but wanted to be able to claim priority. So he published the anagram
Anagram
An anagram is a type of word play, the result of rearranging the letters of a word or phrase to produce a new word or phrase, using all the original letters exactly once; e.g., orchestra = carthorse, A decimal point = I'm a dot in place, Tom Marvolo Riddle = I am Lord Voldemort. Someone who...
ceiiinosssttuv and later published the translation ut tensio sic vis (Latin for "as is the extension, so is the force"). Similarly, Galileo
Galileo Galilei
Galileo Galilei , was an Italian physicist, mathematician, astronomer, and philosopher who played a major role in the Scientific Revolution. His achievements include improvements to the telescope and consequent astronomical observations and support for Copernicanism...
first published his discovery of the phases of Venus in the anagram form. A modern example is the case of an industrial research organization that may later need to prove, for patent purposes, that they made a particular discovery on a particular date; since magnetic media can be altered easily, this may be a nontrivial issue. One possible solution is for a researcher to compute and record in a hardcopy laboratory notebook a cryptographic hash of the relevant data file. In the future, should there be a need to prove the version of this file retrieved from a backup tape has not been altered, the hash function could be recomputed and compared with the hash value recorded in that paper notebook.
Classification
There are many timestamping schemes with different security goals, below is a short list. The rest of this article is dedicated to PKI-based timestamping.- PKI-based - Timestamp token is protected using PKI digital signatureDigital signatureA digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
. - Linking-based schemesLinked TimestampingLinking-based time-stamping is a type of trusted timestamping where issued time-stamps are related to each other.-Description:Linking-based time-stamping creates time-stamp tokens which are dependent on each other, entangled into some authenticated data structure. Later modification of issued...
- timestamps is generated such a way that it is related to other timestamps. - Distributed schemes - timestamp is generated in cooperation of multiple parties.
- Transient keyTransient-key cryptographyTransient-key cryptography is a form of public-key cryptography wherein keypairs are generated and assigned to brief intervals of time instead of to individuals or organizations...
scheme - variant of PKI with short-living signing keys. - MACMessage authentication codeIn cryptography, a message authentication code is a short piece of information used to authenticate a message.A MAC algorithm, sometimes called a keyed hash function, accepts as input a secret key and an arbitrary-length message to be authenticated, and outputs a MAC...
- simple secret key based scheme, found in ANSI ASC X9.95 Standard. - Database - Document hashes are stored in trusted archive; there is online lookup service for verification.
- Hybrid schemes - Linked and Signed Method is prevailing, see X9.95ANSI ASC X9.95 StandardThe ANSI X9.95 standard for trusted timestamps expands on the widely used by adding data-level security requirements that can ensure data integrity against a reliable time source that is provable to any third party...
.
Coverage in standards:
| Scheme | RFC 3161 | X9.95 ANSI ASC X9.95 Standard The ANSI X9.95 standard for trusted timestamps expands on the widely used by adding data-level security requirements that can ensure data integrity against a reliable time source that is provable to any third party... |
ISO/IEC 18014 |
|---|---|---|---|
| PKI | |||
| Linked | |||
| MAC | |||
| Database | |||
| Transient key | |||
| Linked and signed |
For systematic classification and evaluation of timestamping schemes see works by Masashi Une.
Trusted (digital) timestamping

Timestamp
A timestamp is a sequence of characters, denoting the date or time at which a certain event occurred. A timestamp is the time at which an event is recorded by a computer, not the time of the event itself...
issued by a trusted third party
Trusted third party
In cryptography, a trusted third party is an entity which facilitates interactions between two parties who both trust the third party; The Third Party reviews all critical transaction communications between the parties, based on the ease of creating fraudulent digital content. In TTP models, the...
(TTP) acting as a Time Stamping Authority (TSA). It is used to prove the existence of certain data before a certain point (e.g. contracts, research data, medical records,...) without the possibility that the owner can backdate the timestamps. Multiple TSAs can be used to increase reliability and reduce vulnerability.
The newer ANSI ASC X9.95 Standard
ANSI ASC X9.95 Standard
The ANSI X9.95 standard for trusted timestamps expands on the widely used by adding data-level security requirements that can ensure data integrity against a reliable time source that is provable to any third party...
for trusted timestamps
Timestamp
A timestamp is a sequence of characters, denoting the date or time at which a certain event occurred. A timestamp is the time at which an event is recorded by a computer, not the time of the event itself...
augments the RFC 3161 standard with data-level security requirements to ensure data integrity
Data integrity
Data Integrity in its broadest meaning refers to the trustworthiness of system resources over their entire life cycle. In more analytic terms, it is "the representational faithfulness of information to the true state of the object that the information represents, where representational faithfulness...
against a reliable time source that is provable to any third party. This standard has been applied to authenticating digitally signed data for regulatory compliance, financial transactions, and legal evidence.
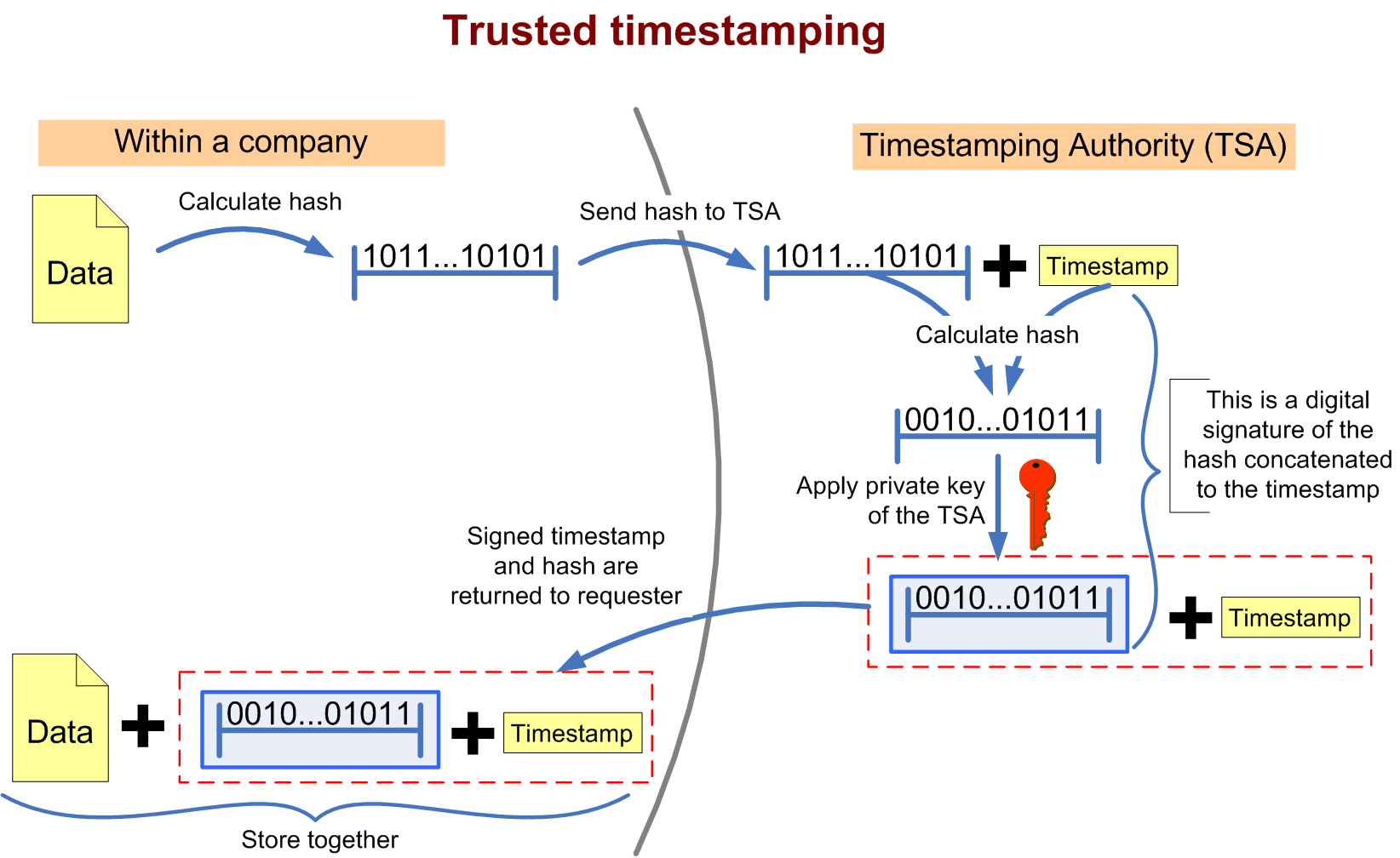
Creating a timestamp
The technique is based on digital signatures and hash functions. First a hash is calculated from the data. A hash is a sort of digital fingerprint of the original data: a string of bits that is different for each set of data. If the original data is changed then this will result in a completely different hash. This hash is sent to the TSA. The TSA concatenates a timestamp to the hash and calculates the hash of this concatenation. This hash is in turn digitally signedDigital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
with the private key of the TSA. This signed hash + the timestamp is sent back to the requester of the timestamp who stores these with the original data (see diagram).
Since the original data cannot be calculated from the hash (because the hash function
Hash function
A hash function is any algorithm or subroutine that maps large data sets to smaller data sets, called keys. For example, a single integer can serve as an index to an array...
is a one way function), the TSA never gets to see the original data, which allows the use of this method for confidential data.
Checking the timestamp

Hash
Hash may refer to:* Hash symbol, the glyph #* Hash mark , one of various symbols* Hash , a coarse mixture of ingredients* Hash chain, a method of producing many one-time keys from a single key or password...
of the original data is calculated, the timestamp given by the TSA is appended to it and the hash of the result of this concatenation is calculated, call this hash A.
Then the digital signature
Digital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
of the TSA needs to be validated. This can be done by checking that the signed hash provided by the TSA was indeed signed with their private key by digital signature
Digital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
verification. The hash A is compared with the hash B inside the signed TSA message to confirm they are equal, proving that the timestamp and message is unaltered and was issued by the TSA. If not, then either the timestamp was altered or the timestamp was not issued by the TSA.
See also
- TimestampTimestampA timestamp is a sequence of characters, denoting the date or time at which a certain event occurred. A timestamp is the time at which an event is recorded by a computer, not the time of the event itself...
- CryptographyCryptographyCryptography is the practice and study of techniques for secure communication in the presence of third parties...
- Computer securityComputer securityComputer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
- Digital signatureDigital signatureA digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
- Digital postmark
- Smart contract
- CAdES - CMS Advanced Electronic SignatureCAdES (computing)CAdES is a set of extensions to Cryptographic Message Syntax signed data making it suitable for advanced electronic signature.-Description:...
- PAdES - PDF Advanced Electronic SignaturePAdESFor the Romanian commune, see Padeş.PAdES is a set of restrictions and extensions to PDF and ISO 32000-1 making it suitable for advanced electronic signature...
- XAdES - XML Advanced Electronic SignatureXAdESXAdES is a set of extensions to XML-DSig recommendation making it suitable for advanced electronic signature.-Description:...
External links
- RFC 3161 Internet X.509 Public Key Infrastructure Time-Stamp Protocol (TSP)
- ANSI ASC X9.95 Standard for Trusted Time Stamps
- Stamper - a free timestamp service (JerseyJerseyJersey, officially the Bailiwick of Jersey is a British Crown Dependency off the coast of Normandy, France. As well as the island of Jersey itself, the bailiwick includes two groups of small islands that are no longer permanently inhabited, the Minquiers and Écréhous, and the Pierres de Lecq and...
based) - timeMarker.org Free OpenPGP timestamp service (RussiaRussiaRussia or , officially known as both Russia and the Russian Federation , is a country in northern Eurasia. It is a federal semi-presidential republic, comprising 83 federal subjects...
based) - RSA Laboratories - What is digital timestamping?
- How to Time-stamp a Digital Document (1991) Stuart Haber, W. Scott Stornetta, Lecture Notes in Computer Science
- VeriSign timestamping service URL for Authenticode: http://timestamp.verisign.com/scripts/timstamp.dll
- Comodo timestamping service for Authenticode only
- The Trouble with Timestamps
- Timestamp Service and Software Toolkits
- écrive.net - timestamping service
- SecuStamp.com - easy PDF time-stamping service
- Timestamping authority certified to comply with the European standard ETSI TS 102 023
- Securo.it - trusted timestamping mobile and web apps, ETSI TS 102 023 compliant

