ANSI ASC X9.95 Standard
Encyclopedia
The ANSI X9.95 standard for trusted timestamps
expands on the widely used RFC 3161 - Internet X.509 Public Key Infrastructure Time-Stamp Protocol by adding data-level security requirements that can ensure data integrity
against a reliable time source that is provable to any third party. Applicable to both unsigned and digitally signed
data, this newer standard has been used by financial institutions and regulatory bodies to create trustworthy timestamp
s that cannot be altered without detection and to sustain an evidentiary trail of authenticity. Timestamps based on the X9.95 standard can be used to provide:
A superset of the IETF's RFC 3161 protocol, the X9.95 standard includes definitions for specific data objects, message protocols
, and trusted timestamp methods, such as digital signature
, MAC
, linked token
, linked-and-signature and transient-key methods. X9.95 compliance can be achieved via several technological approaches, such as transient-key cryptography
. Several vendors market X9.95-compliant systems.
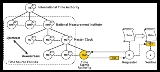
 In an X9.95 trusted timestamp scheme, there are five entities: the time source entity, the Time Stamp Authority, the requestor, the verifier, and a relying party.
In an X9.95 trusted timestamp scheme, there are five entities: the time source entity, the Time Stamp Authority, the requestor, the verifier, and a relying party.
 Before a timestamp-service commences operations, the Time Stamp Authority calibrates its clock(s) with an upstream time source entity, such as a legally defined master clock for the jurisdiction the TSA is time-stamping evidence for. When trusted time
Before a timestamp-service commences operations, the Time Stamp Authority calibrates its clock(s) with an upstream time source entity, such as a legally defined master clock for the jurisdiction the TSA is time-stamping evidence for. When trusted time
has been acquired, the TSA can issue timestamps for unsigned and digitally signed
data based on all of the jurisdictions it maintains timing solutions for.
Applications using timestamps on unsigned data can provide evidence to a verifier that the underlying digital data has existed since the timestamp was generated.
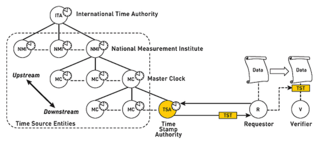
When a requestor requires a timestamp for a dataset
, it creates a cryptographic or arithmetic hash function
of the data. The Hash Function produces a unique string of data which represents the totality of the content in a compact form, i.e. it forms a snapshot of the content. The hash is transmitted through a network connection to the TSA and the time-stamp is issued as a secured digital token token
, which is returned to the requestor for association with the data sent to the TSA to memorialize.
For applications using digitally signed data, the requestor signs the digital hash with its private key and submits the digital signature to the TSA, which performs the same operations as in the previous example: bind the submitted data with a timestamp using its cryptographic binding and return the results to the requestor.
When the requestor receives the timestamp token from the TSA, it also optionally signs the token with its private key. The requestor now has evidence that the data existed at the time issued by the TSA. When verified by a verifier or relying party, the timestamp token also provides evidence that digital signature has existed since the timestamp was issued, provided that no challenges to the digital signature's authenticity repudiate that claim.
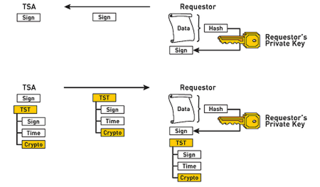 Timestamp tokens in open timestamping models can be obtained from different TSAs on the same data and can be verified at any time by a third party.
Timestamp tokens in open timestamping models can be obtained from different TSAs on the same data and can be verified at any time by a third party.
These three verifications provide non-repudiable evidence of who signed the data (authentication), when it was signed (timeliness) and what data was signed (integrity). Since public keys are used to decrypt the tokens, this evidence can be provided to any third party.
The American National Standard X9.95-2005 Trusted Time Stamps was developed based on RFC 3161 protocol [TSP] and the ISO/IEC 18014
standards [ISO] yet extends its analysis and offerings. The X9.95 standard can be applied to authenticating digitally signed data for financial transactions, regulatory compliance, and legal evidence.
Timestamp
A timestamp is a sequence of characters, denoting the date or time at which a certain event occurred. A timestamp is the time at which an event is recorded by a computer, not the time of the event itself...
expands on the widely used RFC 3161 - Internet X.509 Public Key Infrastructure Time-Stamp Protocol by adding data-level security requirements that can ensure data integrity
Data integrity
Data Integrity in its broadest meaning refers to the trustworthiness of system resources over their entire life cycle. In more analytic terms, it is "the representational faithfulness of information to the true state of the object that the information represents, where representational faithfulness...
against a reliable time source that is provable to any third party. Applicable to both unsigned and digitally signed
Digital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
data, this newer standard has been used by financial institutions and regulatory bodies to create trustworthy timestamp
Timestamp
A timestamp is a sequence of characters, denoting the date or time at which a certain event occurred. A timestamp is the time at which an event is recorded by a computer, not the time of the event itself...
s that cannot be altered without detection and to sustain an evidentiary trail of authenticity. Timestamps based on the X9.95 standard can be used to provide:
- authenticity: trusted, non-refutable time when data was digitally signed
- integrity: protection of the timestamp from tampering without detection
- timeliness: proof that the time of the digital signature was in fact the actual time
- an evidentiary trail of authenticity for legal sufficiency
A superset of the IETF's RFC 3161 protocol, the X9.95 standard includes definitions for specific data objects, message protocols
Communications protocol
A communications protocol is a system of digital message formats and rules for exchanging those messages in or between computing systems and in telecommunications...
, and trusted timestamp methods, such as digital signature
Digital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
, MAC
Message authentication code
In cryptography, a message authentication code is a short piece of information used to authenticate a message.A MAC algorithm, sometimes called a keyed hash function, accepts as input a secret key and an arbitrary-length message to be authenticated, and outputs a MAC...
, linked token
Security token
A security token may be a physical device that an authorized user of computer services is given to ease authentication...
, linked-and-signature and transient-key methods. X9.95 compliance can be achieved via several technological approaches, such as transient-key cryptography
Transient-key cryptography
Transient-key cryptography is a form of public-key cryptography wherein keypairs are generated and assigned to brief intervals of time instead of to individuals or organizations...
. Several vendors market X9.95-compliant systems.
Definitions

- Time source entity - Most countries have an official source of time and this has been codified over the last hundred years through any number of Mutual Recognition Agreement's and Legal Metrological Agreements (see http://www.oiml.org for more information on Legal Metrology). Why this is important is now that the Internet has made it possible to reach directly into the laboratory that operates the official source of time for that jurisdiction, the many layers of "middlemen” who stood between the end-user and the source of time are now gone. As such, time that can be shown as traceable to the specific national measurement institute or master clock of that jurisdiction is the only source that provides the approved "Time Calibration Source" for X9.95. Examples include NIST in the US and Bureau International des Poids et Mesures (BIPM). Other regulatory frameworks also require that time that is moved through the Network Time Protocol ntpNetwork Time ProtocolThe Network Time Protocol is a protocol and software implementation for synchronizing the clocks of computer systems over packet-switched, variable-latency data networks. Originally designed by David L...
is properly certified and authenticated meaning unauthenticated use of time from any provider will fail X9.95 requirements for obtaining time in a provable manner.
- Time Stamp Authority (TSA) - The issuer of timestamps, which can be internal to an organization or a third party or external (as in an Internet based service). The TSA receives its provable "trusted time" from one or more reliable time sources and generates the timestamps requested from it according to the X9.95 scheme.
- requestor - The entity requesting a timestamp.
- verifier - The entity that verifies a timestamp. A verifier can be a relying party, regulatory body, or entity that employs a third-party verification service.
- relying party - The entity receiving the timestamp. The relying party uses the time stamp token in operations.
Creating a timestamp

Trusted time
Trusted time data is time data from a provable source. Because of how time is moved through networks over the Network Time Protocol time sources should generallty only be used which are local to the user no matter how good the network performance is...
has been acquired, the TSA can issue timestamps for unsigned and digitally signed
Digital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
data based on all of the jurisdictions it maintains timing solutions for.
Applications using timestamps on unsigned data can provide evidence to a verifier that the underlying digital data has existed since the timestamp was generated.
When a requestor requires a timestamp for a dataset
Data set
A data set is a collection of data, usually presented in tabular form. Each column represents a particular variable. Each row corresponds to a given member of the data set in question. Its values for each of the variables, such as height and weight of an object or values of random numbers. Each...
, it creates a cryptographic or arithmetic hash function
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
of the data. The Hash Function produces a unique string of data which represents the totality of the content in a compact form, i.e. it forms a snapshot of the content. The hash is transmitted through a network connection to the TSA and the time-stamp is issued as a secured digital token token
Security token
A security token may be a physical device that an authorized user of computer services is given to ease authentication...
, which is returned to the requestor for association with the data sent to the TSA to memorialize.
For applications using digitally signed data, the requestor signs the digital hash with its private key and submits the digital signature to the TSA, which performs the same operations as in the previous example: bind the submitted data with a timestamp using its cryptographic binding and return the results to the requestor.
When the requestor receives the timestamp token from the TSA, it also optionally signs the token with its private key. The requestor now has evidence that the data existed at the time issued by the TSA. When verified by a verifier or relying party, the timestamp token also provides evidence that digital signature has existed since the timestamp was issued, provided that no challenges to the digital signature's authenticity repudiate that claim.

Verifying a timestamp
When verification is needed, the verifier uses the RSA public key for the purported interval to decrypt the timestamp token. If the original digital hash inside the token matches a hash generated on the spot, then the verifier has verified:- The hash in the time stamp token matches the data
- The TSAs cryptographic binding
- The requestor's digital signature
These three verifications provide non-repudiable evidence of who signed the data (authentication), when it was signed (timeliness) and what data was signed (integrity). Since public keys are used to decrypt the tokens, this evidence can be provided to any third party.
The American National Standard X9.95-2005 Trusted Time Stamps was developed based on RFC 3161 protocol [TSP] and the ISO/IEC 18014
ISO 18014
ISO/IEC 18014 Information technology — Security techniques — Time-stamping services is an international standard that specifies time-stamping techniques...
standards [ISO] yet extends its analysis and offerings. The X9.95 standard can be applied to authenticating digitally signed data for financial transactions, regulatory compliance, and legal evidence.
External links
- X9.95 Standard for Trusted Time Stamps
- Certichron's Trusted Time Sources for x9.95 compliance
- GPS-L1 Time Sources are too unreliable to produce legally admissible evidence
- RSA Laboratories - What is digital timestamping?
- Stuart Haber & W. Scott Stornetta “How to Time-stamp a Digital Document” 1991.
- The Trouble with Timestamps

