
NProtect GameGuard Personal 2007
Encyclopedia
nProtect GameGuard Personal 2007 (often referred to as nProtect GGP2007) is an Anti-Virus security suite for Microsoft Windows 2000, XP
, and Vista
developed by INCA Internet
and designed for users playing online computer games. nProtect GameGuard Personal 2007 includes real-time protection from most forms of malware
, including viruses
, trojans
, spyware
, worms
, keyloggers and rootkits as well as a game optimization feature. Users can also encrypt/decrypt important files and permanently delete a file so that restoration is not possible. In addition, the program includes basic maintenance tools, including a disk optimizer and registry cleaner. Like many other security products, nProtect GameGuard Personal 2007 can cause collisions when executed along other security products simultaneous. Known products that are incompatible with nProtect are Kaspersky Internet Security 6.0/7.0
, AVAST! 4 Home, Avira
AntiVir Personal, Norton Antivirus
2004, ALYac, V3Pro2004, and V3 Internet Security 2007. The collisions mainly occur when running the on-access scanning (real-time scanning) simultaneously.
nProtect GameGuard Personal 2007 is available both in a free and a non-free edition, the former lacking treatment abilities for some malware.
are composed of different variations of plug-ins.

Windows XP
Windows XP is an operating system produced by Microsoft for use on personal computers, including home and business desktops, laptops and media centers. First released to computer manufacturers on August 24, 2001, it is the second most popular version of Windows, based on installed user base...
, and Vista
Windows Vista
Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs...
developed by INCA Internet
INCA Internet
INCA Internet Corporation , also known as nProtect, is a corporation which sells computer software. INCA Internet was founded by Young Heum Joo, the current CEO and President of INCA Internet, in 2000. It offers anti-virus, anti-spyware, game security, and unified corporate security...
and designed for users playing online computer games. nProtect GameGuard Personal 2007 includes real-time protection from most forms of malware
Malware
Malware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
, including viruses
Computer virus
A computer virus is a computer program that can replicate itself and spread from one computer to another. The term "virus" is also commonly but erroneously used to refer to other types of malware, including but not limited to adware and spyware programs that do not have the reproductive ability...
, trojans
Trojan horse (computing)
A Trojan horse, or Trojan, is software that appears to perform a desirable function for the user prior to run or install, but steals information or harms the system. The term is derived from the Trojan Horse story in Greek mythology.-Malware:A destructive program that masquerades as a benign...
, spyware
Spyware
Spyware is a type of malware that can be installed on computers, and which collects small pieces of information about users without their knowledge. The presence of spyware is typically hidden from the user, and can be difficult to detect. Typically, spyware is secretly installed on the user's...
, worms
Computer worm
A computer worm is a self-replicating malware computer program, which uses a computer network to send copies of itself to other nodes and it may do so without any user intervention. This is due to security shortcomings on the target computer. Unlike a computer virus, it does not need to attach...
, keyloggers and rootkits as well as a game optimization feature. Users can also encrypt/decrypt important files and permanently delete a file so that restoration is not possible. In addition, the program includes basic maintenance tools, including a disk optimizer and registry cleaner. Like many other security products, nProtect GameGuard Personal 2007 can cause collisions when executed along other security products simultaneous. Known products that are incompatible with nProtect are Kaspersky Internet Security 6.0/7.0
Kaspersky Internet Security
Kaspersky Internet Security or KIS is an Internet security suite developed by Kaspersky Lab compatible with Microsoft Windows. KIS supports the detection and remidition of malware, as well as e-mail spam, phishing attempts, and data leaks....
, AVAST! 4 Home, Avira
Avira
Avira Operations GmbH & Co. KG is a German antivirus software company. When founded, the company was called "H+BEDV Datentechnik GmbH". Its antivirus applications are based on the AntiVir scan engine also known as "Luke Filewalker" , first launched in 1988. For aesthetic reasons, the name was...
AntiVir Personal, Norton Antivirus
Norton AntiVirus
Norton AntiVirus, developed and distributed by Symantec Corporation, provides malware prevention and removal during a subscription period. It uses signatures and heuristics to identify viruses. Other features include e-mail spam filtering and phishing protection.Symantec distributes the product as...
2004, ALYac, V3Pro2004, and V3 Internet Security 2007. The collisions mainly occur when running the on-access scanning (real-time scanning) simultaneously.
nProtect GameGuard Personal 2007 is available both in a free and a non-free edition, the former lacking treatment abilities for some malware.
Plug-Ins
nProtect GameGuard Personal 2007 is composed of five modules called plug-ins. Each plug-in provides a unique function and different products of nProtectINCA Internet
INCA Internet Corporation , also known as nProtect, is a corporation which sells computer software. INCA Internet was founded by Young Heum Joo, the current CEO and President of INCA Internet, in 2000. It offers anti-virus, anti-spyware, game security, and unified corporate security...
are composed of different variations of plug-ins.
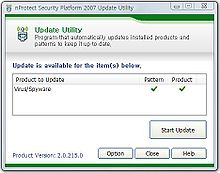
- Security Center: The Security Center shows the security status of each product in the nProtect Security Platform 2007 and gives easy access to update and product registration. The Security Center also provides password configuration and self protection for the program configuration protection. It shows the overall security status and settings of your system. You may enable and disable security options and view the latest security information of virusesComputer virusA computer virus is a computer program that can replicate itself and spread from one computer to another. The term "virus" is also commonly but erroneously used to refer to other types of malware, including but not limited to adware and spyware programs that do not have the reproductive ability...
and spywareSpywareSpyware is a type of malware that can be installed on computers, and which collects small pieces of information about users without their knowledge. The presence of spyware is typically hidden from the user, and can be difficult to detect. Typically, spyware is secretly installed on the user's...
. It also allows you to perform updatesPatch (computing)A patch is a piece of software designed to fix problems with, or update a computer program or its supporting data. This includes fixing security vulnerabilities and other bugs, and improving the usability or performance...
, set a unique password, use the support tool, and change your license to further optimize the service.

- Virus/Spyware: nProtect Anti-Virus/Spyware uses a dual engine (nProtect developed engine + BitDefenderBitDefenderBitDefender is an antivirus software suite developed by Romania-based software company Softwin. It was launched in November 2001, and is currently in its 15 build version...
engine) and a real-time component to protect your system various types of malware including virusesComputer virusA computer virus is a computer program that can replicate itself and spread from one computer to another. The term "virus" is also commonly but erroneously used to refer to other types of malware, including but not limited to adware and spyware programs that do not have the reproductive ability...
, trojansTrojan horse (computing)A Trojan horse, or Trojan, is software that appears to perform a desirable function for the user prior to run or install, but steals information or harms the system. The term is derived from the Trojan Horse story in Greek mythology.-Malware:A destructive program that masquerades as a benign...
, spywareSpywareSpyware is a type of malware that can be installed on computers, and which collects small pieces of information about users without their knowledge. The presence of spyware is typically hidden from the user, and can be difficult to detect. Typically, spyware is secretly installed on the user's...
, wormsComputer wormA computer worm is a self-replicating malware computer program, which uses a computer network to send copies of itself to other nodes and it may do so without any user intervention. This is due to security shortcomings on the target computer. Unlike a computer virus, it does not need to attach...
, keyloggers and rootkits and other known threats to the user. It allows you to enable or disable the real-time scan, adjust the real-time scan level, perform custom scans, and view product information. nProtect GameGuard Personal 2007 also allows modification of startup entries and Internet ExplorerInternet ExplorerWindows Internet Explorer is a series of graphical web browsers developed by Microsoft and included as part of the Microsoft Windows line of operating systems, starting in 1995. It was first released as part of the add-on package Plus! for Windows 95 that year...
preferences.
- Game Optimization: Optimizes your PC environment for a faster and more efficient game execution, game speed enhancement, efficient game environment setup for gamers to use their system in the optimal state. Game Optimization also includes automatic gaming detection and conversion to GameMode to disable any disturbances to the user while gaming. The automatic gaming conversion to GameMode detects most online games and even full screen modes such as during Power Point presentations. When in GameMode, all notices, updates, and schedules scans are performed in the desktop background so that it does not disturb users during a game. You can also view your system information and optimization settings of the network and provides a list of areas the you could optimize memory by deleting unnecessary files. The network speed and memory optimization is suited to provide the optimal environment for online games.
- File Management: File Management allows you to manage important files containing sensitive information through file encryption/decryption and Secure Deletion. File Encryption encrypts files and folders to secure from unauthorized data collection and safeguard the information even if the file is leaked. You may choose from five different encryption algorithms (DESData Encryption StandardThe Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
-64bit, 3DESTriple DESIn cryptography, Triple DES is the common name for the Triple Data Encryption Algorithm block cipher, which applies the Data Encryption Standard cipher algorithm three times to each data block....
-192bit, AESAdvanced Encryption StandardAdvanced Encryption Standard is a specification for the encryption of electronic data. It has been adopted by the U.S. government and is now used worldwide. It supersedes DES...
-256bit, SEEDSEEDSEED is a block cipher developed by the Korean Information Security Agency. It is used broadly throughout South Korean industry, but seldom found elsewhere. It gained popularity in Korea because 40 bit SSL was not considered strong enough , so the Korean Information Security Agency developed its...
-128bit, and ARIAARIA (cipher)In cryptography, ARIA is a block cipher designed in 2003 by a large group of South Korean researchers. In 2004, the Korean Agency for Technology and Standards selected it as a standard cryptographic technique....
-128bit). The encryptions key is needed to decrypt the file, therefore the file is protected even if it is leaked. Secure Deletion permanently deletesData erasureData erasure is a software-based method of overwriting data that completely destroys all electronic data residing on a hard disk drive or other digital media. Permanent data erasure goes beyond basic file deletion commands, which only remove direct pointers to data disk sectors and make data...
a file so that the file cannot be recovered in any way after the deletion. You may choose from four different deletion algorithms (Pseudo Random, US DoD 5220.22-M 3-pass, US DoD 5220.22-M ECE 7-pass, and Peter Gutmann's AlgorithmGutmann methodThe Gutmann method is an algorithm for securely erasing the contents of computer hard drives, such as files. Devised by Peter Gutmann and Colin Plumb, it does so by writing a series of 35 patterns over the region to be erased....
).
- Log and Alert: Users can view logs concerning program events, virus scans and detections, and quarantines and malwareMalwareMalware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
treatments are. Users have the option to be alerted when a particular activity is logged.
Additional Features
- Dual Engine: nProtect GameGuard Personal 2007 uses a dual-engine, the Tachyon engine and BitDefenderBitDefenderBitDefender is an antivirus software suite developed by Romania-based software company Softwin. It was launched in November 2001, and is currently in its 15 build version...
engine. As of June 2007, BitDefenderBitDefenderBitDefender is an antivirus software suite developed by Romania-based software company Softwin. It was launched in November 2001, and is currently in its 15 build version...
has passed Virus BulletinVirus BulletinVirus Bulletin is a magazine about the prevention, detection and removal of malware and spam. It regularly features analyses of the latest virus threats, articles exploring new developments in the fight against viruses, interviews with anti-virus experts, and evaluations of current anti-malware...
's VB100 independent tests 14 times out of 18 since first tested in 2002. An independent testing organization, AV-Test.org, Germany, placed the BitDefenderBitDefenderBitDefender is an antivirus software suite developed by Romania-based software company Softwin. It was launched in November 2001, and is currently in its 15 build version...
engine as 1st place among all security products in August 2007 following a comparative analysis of top data security solutions with a 99.51% detection rate. The Tachyon engine was created by the current CEO of INCA InternetINCA InternetINCA Internet Corporation , also known as nProtect, is a corporation which sells computer software. INCA Internet was founded by Young Heum Joo, the current CEO and President of INCA Internet, in 2000. It offers anti-virus, anti-spyware, game security, and unified corporate security...
through Chollian, a Korean internet portal site. Because of the Dual Engine feature, nProtect GameGuard Personal 2007 can detect all malwareMalwareMalware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
detected through the BitDefenderBitDefenderBitDefender is an antivirus software suite developed by Romania-based software company Softwin. It was launched in November 2001, and is currently in its 15 build version...
engine, and scan with an additional 20% definition engine through the Tachyon engine.

- Automatic Update: Automatic Update of the product mainly updates the anti-virus engines of nProtect GameGuard Personal 2007 to keep the engine up-to-date and provide protection to the latest security threats. The engine's virusComputer virusA computer virus is a computer program that can replicate itself and spread from one computer to another. The term "virus" is also commonly but erroneously used to refer to other types of malware, including but not limited to adware and spyware programs that do not have the reproductive ability...
(malwareMalwareMalware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
) definitions are updated 2 to 3 times per day and an average of 10,000 to 30,000 new malwareMalwareMalware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
definitions per week.
- Quarantine Station: Before you repair or delete malwareMalwareMalware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
, you can copy the original malwareMalwareMalware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
and store it in the Quarantine Station. You may restore, delete, move to another folder or send to INCA InternetINCA InternetINCA Internet Corporation , also known as nProtect, is a corporation which sells computer software. INCA Internet was founded by Young Heum Joo, the current CEO and President of INCA Internet, in 2000. It offers anti-virus, anti-spyware, game security, and unified corporate security...
Virus Analysis Center, the stored files in the Quarantine Station. MalwareMalwareMalware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
kept in the Quarantine Station cannot be executed and there does not pose a threat to the system.
System requirements
| Minimum Requirements | Standard Requirements | Recommended Requirements | |
|---|---|---|---|
| Operating System Operating system An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system... |
Windows 2000 Windows 2000 Windows 2000 is a line of operating systems produced by Microsoft for use on personal computers, business desktops, laptops, and servers. Windows 2000 was released to manufacturing on 15 December 1999 and launched to retail on 17 February 2000. It is the successor to Windows NT 4.0, and is the... |
Windows 2000 Windows 2000 Windows 2000 is a line of operating systems produced by Microsoft for use on personal computers, business desktops, laptops, and servers. Windows 2000 was released to manufacturing on 15 December 1999 and launched to retail on 17 February 2000. It is the successor to Windows NT 4.0, and is the... , Windows XP Windows XP Windows XP is an operating system produced by Microsoft for use on personal computers, including home and business desktops, laptops and media centers. First released to computer manufacturers on August 24, 2001, it is the second most popular version of Windows, based on installed user base... , Windows Vista Windows Vista Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs... |
Windows XP Windows XP Windows XP is an operating system produced by Microsoft for use on personal computers, including home and business desktops, laptops and media centers. First released to computer manufacturers on August 24, 2001, it is the second most popular version of Windows, based on installed user base... , Windows Vista Windows Vista Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs... (32-bit 32-bit The range of integer values that can be stored in 32 bits is 0 through 4,294,967,295. Hence, a processor with 32-bit memory addresses can directly access 4 GB of byte-addressable memory.... /64-bit 64-bit 64-bit is a word size that defines certain classes of computer architecture, buses, memory and CPUs, and by extension the software that runs on them. 64-bit CPUs have existed in supercomputers since the 1970s and in RISC-based workstations and servers since the early 1990s... ) |
| Processor (CPU) Central processing unit The central processing unit is the portion of a computer system that carries out the instructions of a computer program, to perform the basic arithmetical, logical, and input/output operations of the system. The CPU plays a role somewhat analogous to the brain in the computer. The term has been in... |
Intel Pentium II Pentium II The Pentium II brand refers to Intel's sixth-generation microarchitecture and x86-compatible microprocessors introduced on May 7, 1997. Containing 7.5 million transistors, the Pentium II featured an improved version of the first P6-generation core of the Pentium Pro, which contained 5.5 million... 266MHz or higher (or equivalent) |
Intel Pentium III Pentium III The Pentium III brand refers to Intel's 32-bit x86 desktop and mobile microprocessors based on the sixth-generation P6 microarchitecture introduced on February 26, 1999. The brand's initial processors were very similar to the earlier Pentium II-branded microprocessors... or higher (or equivalent) |
Intel Pentium III Pentium III The Pentium III brand refers to Intel's 32-bit x86 desktop and mobile microprocessors based on the sixth-generation P6 microarchitecture introduced on February 26, 1999. The brand's initial processors were very similar to the earlier Pentium II-branded microprocessors... 800 MHz or higher (or equivalent) |
| RAM | 128 MB | 256 MB | 256 MB or higher |
| Free hard drive space | 100 MB | 300 MB | 300 MB or higher |
| Web Browser Web browser A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier and may be a web page, image, video, or other piece of content... |
IE 4.0 Internet Explorer 4 Microsoft Internet Explorer 4 is a graphical web browser released in September 1997 by Microsoft, primarily for Microsoft Windows, but also with versions available for Apple Mac OS, Solaris, and HP-UX and marketed as "The Web the Way You Want It".It was one of the main participants of the first... |
IE 5.0 Internet Explorer 5 Microsoft Internet Explorer 5 was a graphical web browser released in March 1999 by Microsoft, primarily for Microsoft Windows, but initially with versions available for Apple Macintosh, Sun Solaris, and HP-UX. It was one of the main participants of the first browser war... |
IE 5.0 Internet Explorer 5 Microsoft Internet Explorer 5 was a graphical web browser released in March 1999 by Microsoft, primarily for Microsoft Windows, but initially with versions available for Apple Macintosh, Sun Solaris, and HP-UX. It was one of the main participants of the first browser war... or higher |
See also
- INCA Internet Co., Ltd.INCA InternetINCA Internet Corporation , also known as nProtect, is a corporation which sells computer software. INCA Internet was founded by Young Heum Joo, the current CEO and President of INCA Internet, in 2000. It offers anti-virus, anti-spyware, game security, and unified corporate security...
- nProtect GameGuardGameGuardnProtect GameGuard is an anti-cheating rootkit developed by INCA Internet. It is installed alongside many Asian massively multiplayer online roleplaying games such as Rohan: Blood Feud, Lineage II, 9Dragons, Cabal Online, Phantasy Star Universe, GunZ: The Duel, Flyff, Rappelz, Luna Online,...
- Anti-Virus Software

