Intelligence cycle management
Encyclopedia
-
- This article is at the top level of a series of articles about Intelligence Cycle Management.
The intelligence cycle is a investigation process used by end users (commander of a task force or supervisor of an investigation unit), which allows that user to gather specific information, understand the possibilities of that information, and the limitations of the intelligence process.
Within the context of government
Government
Government refers to the legislators, administrators, and arbitrators in the administrative bureaucracy who control a state at a given time, and to the system of government by which they are organized...
, military and business affairs, intelligence
Intelligence (information gathering)
Intelligence assessment is the development of forecasts of behaviour or recommended courses of action to the leadership of an organization, based on a wide range of available information sources both overt and covert. Assessments are developed in response to requirements declared by the leadership...
(the gathering and analysis
Analysis
Analysis is the process of breaking a complex topic or substance into smaller parts to gain a better understanding of it. The technique has been applied in the study of mathematics and logic since before Aristotle , though analysis as a formal concept is a relatively recent development.The word is...
of accurate, reliable information
Information
Information in its most restricted technical sense is a message or collection of messages that consists of an ordered sequence of symbols, or it is the meaning that can be interpreted from such a message or collection of messages. Information can be recorded or transmitted. It can be recorded as...
) is intended to help decision-makers at every level to make informed decisions.
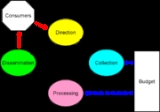
The intelligence cycle is the continuous process by which:
- a) intelligence priorities are set,
- b) raw information is collected,
- c) this information is analyzed,
- d) the processed information is disseminated, and
- e) the next set of priorities is determined.
Subcycles also exist: e.g., an analyst (c) may require more information (b).
The related field of counterintelligence is tasked with impeding the intelligence efforts of others.
An intelligence "consumer" might be:
-
- an infantry officer who wants to know what is on the other side of the next hill, or
- a head of government who wants to know the probability that a foreign leader will go to war over a certain point, or
- a marketing executive who wants to know what his or her competitors are planning.
Intelligence organizations are not, nor can they be expected to be, infallible (intelligence reports are often referred to as "estimates", and often include measures of confidence and reliability), but when properly managed and tasked, can be among the most valuable tools of management
Management
Management in all business and organizational activities is the act of getting people together to accomplish desired goals and objectives using available resources efficiently and effectively...
and government.
In at least one documented case, for example, intelligence services (and sensors
Measurement and Signature Intelligence
Measurement and signature intelligence is a branch of intelligence gathering activities.MASINT, may have aspects of intelligence analysis management, since certain aspects of MASINT, such as the analysis of electromagnetic radiation received by signals intelligence are more of an analysis...
managed by intelligence specialists) have provided information and analysis that let operational commanders determine that a nuclear attack
Nuclear warfare
Nuclear warfare, or atomic warfare, is a military conflict or political strategy in which nuclear weaponry is detonated on an opponent. Compared to conventional warfare, nuclear warfare can be vastly more destructive in range and extent of damage...
was not in progress, thereby preventing the launch of an unnecessary "counterstrike" (reprisal) and resultant nuclear war
Doomsday event
A doomsday event is a specific, plausibly verifiable or hypothetical occurrence which has an exceptionally destructive effect on the human race...
. For another example, during the late 20th century, French aerospace and biomedical firms were able to keep up with their competitors despite spending a fraction of their competitors' research and development budgets by gaining access to recordings of conversations made in the first-class cabins of Air France flights.
There are a number of ways in which intelligence management can fail. Leaders can pervert the function of intelligence (failures in direction), such as demanding or considering only that information which supports a policy already decided, or directing intelligence organizations to violate civil liberties. Failures in collection can cause analysts to draw the wrong conclusions. Failures in dissemination, often caused by excessive concern with security, can prevent timely and accurate intelligence from reaching the operational personnel who can act on it.
The principles of intelligence have been discussed and developed from the earliest writers on warfare
to the most recent on technology
. Despite the most powerful computers
Supercomputer
A supercomputer is a computer at the frontline of current processing capacity, particularly speed of calculation.Supercomputers are used for highly calculation-intensive tasks such as problems including quantum physics, weather forecasting, climate research, molecular modeling A supercomputer is a...
, however, the human mind remains at the core of intelligence: discerning patterns and extracting meaning from a flood of correct, incorrect, and sometimes deliberately misleading information (also known as disinformation
Disinformation
Disinformation is intentionally false or inaccurate information that is spread deliberately. For this reason, it is synonymous with and sometimes called black propaganda. It is an act of deception and false statements to convince someone of untruth...
).
This is the top of a hierarchy of articles which discuss the four major parts of the intelligence cycle: tasking, collection
Intelligence collection management
Intelligence Collection Management is the process of managing and organizing the collection of intelligence information from various sources. The collection department of an intelligence organization may attempt basic validation of that which it collects, but is not intended to analyze its...
, analysis
Intelligence analysis management
Intelligence Analysis Management is the process of managing and organizing the analytical processing of raw intelligence information into finished intelligence. The terms "analysis", "production", and "processing" all are used in this phase that is informally called "connecting the dots". ...
, and dissemination
Intelligence dissemination management
It is a classic maxim of intelligence that intelligence agencies do not make policy, but advise policymakers. Nevertheless, with an increasingly fast pace of operations, intelligence analysts may include choices of actions, with some projection of consequences from each. Intelligence consumers and...
. Tasking, since it is so intimately associated with the management of the cycle, is the subject of the present article.
"Intelligence" defined
Johnston's ethnographic study of analytic culture established the following "consensus" definitions for intelligence, intelligence analysis, and intelligence errors:- Definition 1: Intelligence is secret state or group activity to understand or influence foreign or domestic entities.
- Definition 2: Intelligence analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context.
- Definition 3: Intelligence errors are factual inaccuracies in analysis resulting from poor or missing data; intelligence failure is systemic organizational surprise resulting from incorrect, missing, discarded, or inadequate hypotheses.
Management of the intelligence cycle
One basic model of the intelligence process is called the intelligence cycle. This model can be applied. Like all basic models, it does not reflect the fullness of real-world operations. Nevertheless, it is worth introducing, then pointing out some of its failures, and then presenting more real-world models. Once reasonable real-world models can be refined, the activities making it up can be discussed. Intelligence is processed information. The activities of the intelligence cycle obtain and assemble information, convert it into intelligence and make it available to its users. The intelligence cycle comprises five phases:- Planning and Direction: Deciding what is to be monitored and analyzed
- CollectionIntelligence collection managementIntelligence Collection Management is the process of managing and organizing the collection of intelligence information from various sources. The collection department of an intelligence organization may attempt basic validation of that which it collects, but is not intended to analyze its...
: The obtaining of raw information using a variety of collection disciplines - ProcessingIntelligence analysis managementIntelligence Analysis Management is the process of managing and organizing the analytical processing of raw intelligence information into finished intelligence. The terms "analysis", "production", and "processing" all are used in this phase that is informally called "connecting the dots". ...
: Refining and analyzing the information - Analysis and productionIntelligence analysis managementIntelligence Analysis Management is the process of managing and organizing the analytical processing of raw intelligence information into finished intelligence. The terms "analysis", "production", and "processing" all are used in this phase that is informally called "connecting the dots". ...
: the data that have been processed are translated into a finished intelligence product, which includes integrating, collating, evaluating, and analyzing all the data. - DisseminationIntelligence dissemination managementIt is a classic maxim of intelligence that intelligence agencies do not make policy, but advise policymakers. Nevertheless, with an increasingly fast pace of operations, intelligence analysts may include choices of actions, with some projection of consequences from each. Intelligence consumers and...
: Providing the results of processing to consumers, including consumers in the intelligence community, including use of intelligence information in net assessment and strategic gaming.
A distinct Intelligence officer
Intelligence officer
An intelligence officer is a person employed by an organization to collect, compile and/or analyze information which is of use to that organization...
is often entrusted with managing each level of the process.
In some organisations, such as the UK Military, these phases are reduced to four, with the "Analysis and Production" being incorporated in "Processing." These phases are the absolute minimum to describe the process of intelligence, but, minimally, several other activities should be considered. Remember that the output of the intelligence cycle, if accepted, drives operations, which, in turn, produce new material to go into another iteration of the intelligence cycle. Consumers should give the intelligence organization broad directions, and the highest level will set budgets.
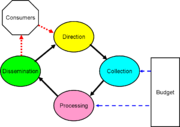
Representative Failures in Exercising the Cycle
Any circular cycle is as weak as its weakest component. At one time or another, a national or organizational intelligenceOrganizational Intelligence
Organizational Intelligence is the capability of an organization to comprehend and conclude knowledge relevant to its business purpose.* an ability to make sense of complex situations and act effectively...
process has broken down, thus causing failure in the cycle
Failure in the intelligence cycle
For the album see Intelligence FailureFailure in the intelligence cycle or intelligence failure, is the outcome of the inadequacies within the intelligence cycle. The intelligence cycle itself consists of six steps that are constantly in motion...
.
Each of the four main categories has, in different countries and at different times, failed terribly. Policymakers have denied the services direction to work on critical matters. Intelligence services have failed to collect critical information. The services have analyzed data incorrectly. There have been failures to disseminate intelligence quickly enough, or to the right decisionmakers.
There have been failures to protect the intelligence process itself from opposing intelligence services.
A major problem, in several aspects of the enhanced cycle, is stovepiping
Stovepiping
Stovepiping is a metaphorical term which recalls a stovepipe's function as an isolated vertical conduit, and has been used, in the context of intelligence, to describe several ways in which raw intelligence information may be presented without proper context...
. In the traditional intelligence use of the term, stovepiping keeps the output of different collection systems separated from one another. This has several negative effects. First, it prevents one discipline from cross-checking another. In World War II, both sides doubled clandestine agents and used them to send disinformation back to their own countries . While the content of the human intelligence (HUMINT
HUMINT
HUMINT, a syllabic abbreviation of the words HUMan INTelligence, refers to intelligence gathering by means of interpersonal contact, as opposed to the more technical intelligence gathering disciplines such as SIGINT, IMINT and MASINT...
) they sent might seem reasonable, direction finding, a discipline of signals intelligence (SIGINT) might have shown they were transmitting from Gestapo or MI5 headquarters. Measurement and signature analysis (MASINT) on the style of their radio procedure could have indicated that an impostor, or perhaps the real agent but under duress, was sending.
Second, a newer usage of stovepiping is bypassing the regular analysis of raw intelligence, and sending only raw intelligence that supports a particular position to the highest national leadership.
Failures in Direction
The highest policy levels of government set, in the broadest sense, intelligence priorities and policies. In some cases, heads of government give quite specific orders, but illegal ones. Others may be more on the level of "Do what you gotta do". Of course, in certain countries, the law is merely what the dictatorDictatorship
A dictatorship is defined as an autocratic form of government in which the government is ruled by an individual, the dictator. It has three possible meanings:...
decrees.
Stalin forbids investigation of German invasion plans
Stalin received a warning document, in May 1939, about The Future Plans of Aggression by nazi Germany, based on a German briefing obtained by Soviet spiesChronology of Soviet secret police agencies
There was a succession of Soviet secret police agencies over time. The first secret police after the Russian Revolution, created by Vladimir Lenin's decree on December 20, 1917, was called "Cheka"...
in Warsaw. A Soviet agent first reported that Hitler planned to declare war on the Soviet Union in March 1941, and refined the estimate, by February 28, to May 20.
This intelligence was corroborated by sources in Bucharest, Budapest, Sofia and Rome, to say nothing of the information provided by the spy Richard Sorge
Richard Sorge
Richard Sorge was a German communist and spy who worked for the Soviet Union. He has gained great fame among espionage enthusiasts for his intelligence gathering during World War II. He worked as a journalist in both Germany and Japan, where he was imprisoned for spying and eventually hanged....
(code-named Ramsay) in Tokyo in which the authors detail the undercover operations of the spy ring headed by Richard Sorge and Hotsumi Ozaki
Hotsumi Ozaki
was a Japanese journalist working for the Asahi Shinbun newspaper, communist, spy, and an advisor to Prime Minister Fumimaro Konoe. The only Japanese person to be hanged for treason by the Japanese government during World War II, Ozaki is well known as an informant of the spy Richard Sorge...
which transmitted highly secret information from Tokyo to the Soviet Union between 1933 and 1941. On April 17 a Prague informant predicted a German invasion in the second half of June. The precise date and time of the invasion were revealed by a reliable source in Berlin fully three days before the Germans attacked.
All of this Stalin ignored. Typically, he scrawled on the bottom of the Prague report: English provocation! Investigate! On May 19, Sorge predicted that 150 divisions were being readied by the Germans for an invasion of the Soviet Union. Stalin retorted with an expletive.
The result was that literally nothing was done to prepare for the German assault. Soviet planes were not camouflaged. Troops were not in defensive positions; indeed they were ordered not to occupy such positions, for fear of provoking the Germans. Worse, Stalin responded to the gathering storm with yet another purge of suspected threats to his own authority.
Political conflict
In democracies with a check-and-balance system, it may be that the legislative branch, or the parliamentary opposition (especially if a government fell over something that might be intelligence-related), will review the role of the government in a failure. In totalitarian systems, there still may be checks and balances, as in the Soviet Union relying on the Party and the Army to check the "Organs of State Security".Sometimes, this process may be a partisan witch-hunt rather than an unbiased exploration. In the United States, some of the investigations of intelligence agency activities by independent bipartisan commissions have tended to be more objective than the legislative committees with the majority party in control. This is not to suggest that all American congressional reviews have been partisan; some have been quite professional. One example is the Senate Select Committee on Intelligence's investigation that determined that the National Security Agency NSA had placed a "back door" into the Data Encryption Standard
Data Encryption Standard
The Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
.
UK Government and Iraq
A CIA study assessing the report of the Parliamentary inquiry committee chaired by Lord Butler of Brockwell, "Review of Intelligence on Weapons of Mass Destruction" said"The language of the Butler report was likewise comparatively understated. It avoided the often hectoring and accusatory tone of the Senate Select Committee report on US prewar intelligence on Iraq, stayed away from personalizing blame, and examined the Iraq failure chiefly in terms of the “collective responsibility” ethos of Britain’s ... government and the collegiality of the UK Joint Intelligence Committee
UK Joint Intelligence Committee
The Joint Intelligence Committee is the part of the British Cabinet Office responsible for directing the national intelligence organisations of the United Kingdom on behalf of the Cabinet of the United Kingdom and providing advice to the Cabinet related to security, defence and foreign affairs...
(JIC) system... But it also has to be said that intelligence analysis (or assessment, in UK parlance) is generally the least appreciated and least addressed aspect of the intelligence process in the UK. On the one hand, this is because assessment is scholarly rather than sexy; on the other, as has been pointed out in a number of forums elsewhere, assessment is viewed in the UK as a government function and not specifically as an intelligence function.
"The conclusions reached by Butler’s review team were also less hostile than those of the Senate Select Committee. To be sure, they found that a measure of groupthink had been at work— in looking for evidence to corroborate the suspicions that the JIC had insisted on sustaining despite a lack of hard evidence (a long-recognized, inherent risk of the JIC system’s collegial methods) and a tendency to overcompensate for the optimistic assessments of the limits of Iraqi nuclear developments discredited after the first Gulf War.
"[Lord Butler] expressed a number of concerns regarding the effectiveness of the intelligence validation components of the Secret Intelligence Service’s management structure—the “Requirements” side of SIS. One of the factors behind the failure of UK Iraq assessments was the practice of placing “greater weight” upon a number of human intelligence (HUMINT) reports “than they could reasonably bear,”
Observations on oversight in the UK and in the US
Paul Pillar, National Intelligence Officer for the Middle East between 2000 and 2005, observed "Intelligence affects the nation's interests through its effect on policy. No matter how much the process of intelligence gathering itself is fixed, the changes will do no good if the role of intelligence in the policymaking process is not also addressed.... But a few steps, based on the recognition that the intelligence-policy relationship is indeed broken, could reduce the likelihood that such a breakdown will recur."On this point, the United States should emulate the United Kingdom, where discussion of this issue has been more forthright, by declaring once and for all that its intelligence services should not be part of public advocacy of policies still under debate. In the United Kingdom, Prime Minister Tony Blair accepted a commission of inquiry's conclusions that intelligence and policy had been improperly commingled in such exercises as the publication of the "dodgy dossier," the British counterpart to the United States' Iraqi WMD white paper, and that in the future there should be a clear delineation between intelligence and policy. An American declaration should take the form of a congressional resolution and be seconded by a statement from the White House. Although it would not have legal force, such a statement would discourage future administrations from attempting to pull the intelligence community into policy advocacy. It would also give some leverage to intelligence officers in resisting any such future attempts.
"The proper relationship between intelligence gathering and policymaking sharply separates the two functions....Congress, not the administration, asked for the now-infamous October 2002 National Intelligence Estimate (NIE) on Iraq's unconventional weapons programs, although few members of Congress actually read it. (According to several congressional aides responsible for safeguarding the classified material, no more than six senators and only a handful of House members got beyond the five-page executive summary.) As the national intelligence officer for the Middle East, I was in charge of coordinating all of the intelligence community's assessments regarding Iraq; the first request I received from any administration policymaker for any such assessment was not until a year into the war.
"The legislative branch is the appropriate place for monitoring the intelligence-policy relationship. But the oversight should be conducted by a nonpartisan office modeled on the Government Accountability Office (GAO) and the Congressional Budget Office (CBO). Such an office would have a staff, smaller than that of the GAO or the CBO, of officers experienced in intelligence and with the necessary clearances and access to examine questions about both the politicization of classified intelligence work and the public use of intelligence. As with the GAO, this office could conduct inquiries at the request of members of Congress. It would make its results public as much as possible, consistent with security requirements, and it would avoid duplicating the many other functions of intelligence oversight, which would remain the responsibility of the House and Senate intelligence committees."
Failures in Collection
In the WWII UK Double Cross SystemDouble Cross System
The Double Cross System, or XX System, was a World War II anti-espionage and deception operation of the British military intelligence arm, MI5. Nazi agents in Britain - real and false - were captured, turned themselves in or simply announced themselves and were then used by the British to broadcast...
, all German spies in the British Isles were captured, and given a choice between execution and becoming a double agent
Double agent
A double agent, commonly abbreviated referral of double secret agent, is a counterintelligence term used to designate an employee of a secret service or organization, whose primary aim is to spy on the target organization, but who in fact is a member of that same target organization oneself. They...
. The British-controlled double agents were part of a larger strategic deception
Deception
Deception, beguilement, deceit, bluff, mystification, bad faith, and subterfuge are acts to propagate beliefs that are not true, or not the whole truth . Deception can involve dissimulation, propaganda, and sleight of hand. It can employ distraction, camouflage or concealment...
operation, the principal intention of which was to make the Germans believe that the main Allied invasion would come at some place other than the actual beaches of Normandy.
Only those German reconnaissance aircraft that would pass over appropriately arranged decoys were allowed to complete their missions, and the Allies generated dummy signals corresponding to imaginary units whose organization and position was supportive of the overall deception plans. HUMINT, IMINT, and SIGINT were all collecting plausible data and returning it to the Germans. The Germans were unable to use collection techniques that revealed the real Allied plan.
Due to limited resources, the US and South Koreans did not give a high priority to a potential attack, in 1950, by the North Koreans. COMINT on North Korea was only an incidental by-product of monitoring the Chinese and Soviets. The main attack came as a surprise.
Failures in Analysis
There have been analytical failures, sometimes of imagination and sometimes of interpretation, since the beginning of modern intelligence. Prior to Pearl Harbor, US Navy intelligence did not adequately consider the British air strike against Italian capital ships in Taranto Harbor, but there was an assumption that torpedo nets were not needed at Pearl Harbor. It is not clear if the Pacific Fleet intelligence officers had clear reporting on Taranto, or if they considered it at all. At the time, there were organizational relations we would consider odd today, such as COMINT being in the Office of Naval Communications rather than the Office of Naval Intelligence. Weapons capabilities seemed restricted to the Bureau of Ordnance.During the war in Vietnam, there were constant analytic disputes among the Military Assistance Command Vietnam, the Office of the Secretary of Defense
Office of the Secretary of Defense
The Office of the Secretary of Defense is a headquarters-level staff of the Department of Defense of the United States of America. It is the principal civilian staff element of the Secretary of Defense, and it assists the Secretary in carrying out authority, direction and control of the Department...
, and the Central Intelligence Agency
Central Intelligence Agency
The Central Intelligence Agency is a civilian intelligence agency of the United States government. It is an executive agency and reports directly to the Director of National Intelligence, responsible for providing national security intelligence assessment to senior United States policymakers...
. That the intelligence organizations in the military command were more optimistic is unsurprising, and not even indicative of something being seriously wrong—as long as there are independent intelligence organizations to cross-check.
Even within these organizations, there were disputes. "Skepticism and pessimism about Vietnam were present chiefly among those officers who produced finished intelligence in the form of National Intelligence Estimates and in Intelligence Directorate (then the DDI) publications: that is, analysts in the Office of National Estimates (ONE), the Office of [Economic] Research and Reports, and the South Vietnam Branch of the Office of Current Intelligence (OCI). Such views were generally a bit less evident among officers of the North Vietnam Branch of OCI..."
Another serious problem to be avoided is mindset or "groupthink." Any intelligence agency can fall into the trap of not questioning basic assumptions that affect much subsequent analysis. It is essential that competitive or redundant analysis be encouraged. Currently and historically, less than a tenth of what the United States spends on intelligence is devoted to analysis; it is the least expensive dimension of intelligence. Not all duplication is wasteful. This has been a continuing issue with Bomb damage assessment
Bomb damage assessment
Bomb, or battle damage assessment, often referred to as BDA, is the practice of assessing damage inflicted on a target by an air campaign. It is part of the larger discipline of combat assessment...
, going back to the beginnings of aerial bombardment. Even with considerably improved sensors in 1991, it remains a problem, and, as with the Vietnam case, there tended to be increasingly more pessimistic analyses in the theater command, the Department of Defense, and the CIA. It may well be that increasing weapon precision, UAV followup, and even such things as the towed video link following a Tactical Tomahawk into the target, which this is finally coming under control.
Failures in Dissemination
Perhaps the most studied failure of a country to respond to a threat, because the operational commanders did not receive the warning circulating among analysts and policymakers, is the Pearl Harbor attack. It was clear that Japan was preparing to break diplomatic relations, often an immediate prelude to war. Only the last part of the diplomatic dispatch seemed a war warning.Even though US intelligence literally had the strategic warning in hand before the less skilled Japanese diplomats allowed to handle the dispatch, there were failures in transmitting the warnings to the field. This was due to a combination of factors, including Army-Navy rivalry, a less sophisticated communications system that did not confirm reception by the right commands, and reluctance to micromanage field commanders.
Failures in Acceptance
"What was Josef Stalin thinking when he allied himself with Adolf Hitler for nearly two years at the beginning of World War II? What did Stalin know about Hitler's intentions to turn on him, and when did he know it?".In his book, David E. Murphy, former chief of CIA Soviet Operations,
makes two points of significance in response to Ferguson The first is the extent to which the Soviet spy network in Europe continued to deliver first-rate intelligence, despite Stalin's best efforts to purge it out of existence. It was not just the British establishment the Soviets managed to penetrate; there were agents in the German economics ministry, air ministry and foreign ministry, not to mention the American Embassy in Moscow.
Germany told the Soviets that their troops were being massed on the Soviet borders to keep them clear of British air raids, that dozens of German planes were violating Soviet airspace merely because their pilots were inexperienced and that talk of a German invasion plan was a cynical British smear designed to provoke a Nazi-Soviet war. It is odd that the Soviets, so adept at maskirovka, were so deceived by deception rather than secrecy.
Failures in Counterintelligence
No intelligence organization is immune to having its personnel subverted. See Counter-intelligenceCounter-intelligence
Counterintelligence or counter-intelligence refers to efforts made by intelligence organizations to prevent hostile or enemy intelligence organizations from successfully gathering and collecting intelligence against them. National intelligence programs, and, by extension, the overall defenses of...
.
Models of Intelligence and Information
The intelligence cycle is only a model. Budgetary and policy direction are hierarchically above it. In reality, it is not a cycle, but a series of parallel activities. "Collection and analysis, which are supposed to work in tandem, in fact work more properly in parallel. Finally, the idea that decision makers wait for the delivery of intelligence before making policy decisions is equally incorrect. In the modern era, policy officials seem to want intelligence to support policy rather than to inform it. The Intelligence Cycle also fails to consider either counter-intelligence or covert action." The OODA loop
OODA Loop
The OODA loop is a concept originally applied to the combat operations process, often at the strategic level in military operations. It is now also often applied to understand commercial operations and learning processes...
developed by John Boyd
John Boyd (military strategist)
Colonel John Boyd was a United States Air Force fighter pilot and Pentagon consultant of the late 20th century, whose theories have been highly influential in the military, sports, and business.-Biography:...
, discussed in the context of the Intelligence Cycle below, may come somewhat closer, as OODA is action-oriented and spiraling, rather than a continuing circle.
In principle, within the cycle, "intelligence agencies are faced with the task of determining intelligence priorities, a process known as threat assessment. Experts and policymakers gather periodically to evaluate the perils that confront the United States and establish a ladder of priorities from the most dangerous (Tiers 1A and 1B) to the least (Tier 4). Bias and guesswork enter the picture, along with the limitations caused by the uncertainty that surrounds the future. Where should one place China in the threat assessment? What about Russia, or Cuba? The outcome of these debates shapes the priorities for some $44 billion worth of intelligence spending each year. It also determines the areas U.S. spies will [try to] infiltrate, sets the orbits for surveillance satellites, and establishes the flight patterns of reconnaissance aircraft. To improve the threat assessment process, the United States has undertaken nine major inquiries into its intelligence apparatus since the end of the Cold War. Each has found a failure to clearly delineate priorities
.
National/Strategic
"Establishing the intelligence requirements of the policy makers...is management of the entire intelligence cycle, from identifying the need for data to delivering an intelligence product to a consumer. It is the beginning and the end of the cycle—the beginning because it involves drawing up specific collection requirements and the end because finished intelligence, which supports policy decisions, generates new requirements."The whole process depends on guidance from public officials. Policymakers-- the President, his aides, the National Security Council, and other major departments and agencies of government--initiate requests for intelligence. Issue coordinators interact with these public officials to establish their core concerns and related information requirements. These needs are then used to guide collection strategies and the production of appropriate intelligence products".
Military/operational
Intelligence requirements are determined by the CommanderCommander
Commander is a naval rank which is also sometimes used as a military title depending on the individual customs of a given military service. Commander is also used as a rank or title in some organizations outside of the armed forces, particularly in police and law enforcement.-Commander as a naval...
to support his operational needs. The commander's requirement (sometimes called Essential Elements of Intelligence (EEIs)) initiates the Intelligence cycle. Operational and tactical intelligence always should help the commander select an action.
Each intelligence source has different characteristics which can be used but which may also be limiting. IMINT, for instance, may depend on weather, satellite orbits or the ability of aircraft to elude ground defenses, and time for analysis. Other sources may take considerable time to collect the necessary information. MASINT depends on having built a library of signatures of normal sensor readings, such that deviations stand out.
In rare cases, intelligence is taken from such extremely sensitive sources that it cannot be used without exposing the methods or persons providing such intelligence. One of the strengths of the British penetration of the German Enigma
Enigma machine
An Enigma machine is any of a family of related electro-mechanical rotor cipher machines used for the encryption and decryption of secret messages. Enigma was invented by German engineer Arthur Scherbius at the end of World War I...
cryptosystem was that no information learned from it was ever used for operations, unless there was a plausible cover story that the Germans believed was the reason for Allied victories. If, for example, the movement of a ship was learned through Enigma COMINT, a reconnaissance aircraft was sent into the same area, and allowed to be seen by the Axis, so they thought the resulting sinking was due to IMINT.
CCIRM
The Collection Coordination Intelligence Requirements Management (CCIRM) system is the NATO doctrine for intelligence collection management, although it differs from US doctrine. From the US perspective, CCIRM manages requests for information (RFI) rather than the collection itself, which caused some friction when working with US collection assets. Within NATO, requests for information flowed through the chain of command to the CCIRM manager. Where the US sees collection management as a "push" or proactive process, NATO sees this as "pull" or reactive.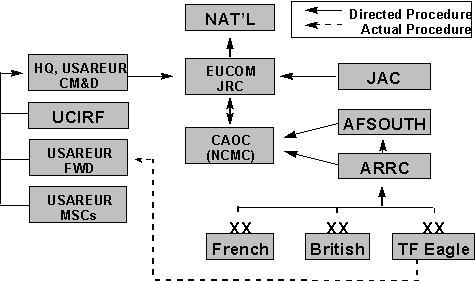
Experience in Bosnia and Kosovo demonstrated strain between CCIRM and US procedures, although the organizations learned by experience. Operation Joint Endeavor, began in 1995, with Operation Deliberate Force going to a much higher level of combat. Operation Allied Force, a more intense combat situation in Kosovo, began on 24 March 1999.
Intelligence Friction in Bosnia
Things worked better in Bosnia than Kosovo. "The majority of intelligence that the United States produced was tailored, timely, and releasable to IFOR. The U.S. intelligence community consistently disseminated actionable intelligence without divulging sensitive sources and methods." The early phases were more typical of peace operations, and an efficient liaison system worked well.Perhaps a major reason for Bosnian success was deployment of adequate intelligence management organizations. When NATO interoperability and security restrictions became a problem, national component capabilities often worked around the difficulties. Two U.S. theater-level analysis centers supported the U.S. and IFOR
IFOR
The Implementation Force was a NATO-led multinational peacekeeping force in Bosnia and Herzegovina under a one-year mandate from 20 December 1995 to 20 December 1996 under the codename Operation Joint Endeavour. Its task was to implement the military Annexes of The General Framework Agreement for...
requests for information. The USAREUR Combat Intelligence Readiness Facility (UCIRF) in Germany, had all-source capability, while the USEUCOM Joint Analysis Center (JAC) in England, integrated imagery and other intelligence and inserted releasable information into the coalition-wide system.
A wide range of technological intelligence systems were used, from NATO, UK, French and German and US organizations Manned aerial sensors, including the U-2
Lockheed U-2
The Lockheed U-2, nicknamed "Dragon Lady", is a single-engine, very high-altitude reconnaissance aircraft operated by the United States Air Force and previously flown by the Central Intelligence Agency . It provides day and night, very high-altitude , all-weather intelligence gathering...
, P-3s, JSTARS, RC-135 RIVET JOINT, and the NATO E-3s (and to a lesser extent the U.S. E-2Cs). These systems could respond to changing conditions by modifying their mission while in flight. These systems had one disadvantage in that they put personnel at risk so the standoff requirements tended to limit the depth of the sensor capabilities.
The unmanned aerial vehicles (UAVs) did not put personnel at risk, provided reduced detection (smaller cross-section), and supplied a broad range of collection technologies (SIGINT, ELINT, Electro-optical MASINT
Electro-optical MASINT
Electro-optical MASINT is a subdiscipline of Measurement and Signature Intelligence, and refers to intelligence gathering activities which bring together disparate elements that do not fit within the definitions of Signals Intelligence , Imagery Intelligence , or Human Intelligence...
, Electro-optical infrared, and live video). Their greatest limitation was their lack of flexibility; they either needed to be pre-programmed or controlled by personnel within line of sight.
French and British HUMINT
HUMINT
HUMINT, a syllabic abbreviation of the words HUMan INTelligence, refers to intelligence gathering by means of interpersonal contact, as opposed to the more technical intelligence gathering disciplines such as SIGINT, IMINT and MASINT...
was strong, along with US Special Operations Forces. OSINT (open source intelligence) provided indications and warning of increased tensions in local areas, supported predictive analysis efforts, and helped focus and queue other collection efforts. MASINT (Measurement and Signature Intelligence) was used to support treaty compliance, early warning, and force protection. Dissemination of OSINT material helped establish common understandings.
Intelligence Friction in Kosovo
In the Kosovo operation, a relatively small Battlefield Coordination Detachment, intended to be part of a larger organization including all-source air and ground intelligence cells, was split from a Combined Air Operations Center in Macedonia, and dispatched with an ad hoc unit,"In Kosovo, a US Battlefield Coordination Element (BCE) is an Echelons above Corps
Echelons above Corps
Echelons above corps , in US and NATO practice, refer to higher headquarters, of purpose-built organization, which involve a greater number of troops than would be in an army corps. They may be standing organizations with a regional responsibility, or may be established for a particular operational...
organization now called a battlefield coordination detachment (BCD)...The BCE was already deployed with a combined air operations center (CAOC) ... in support of Task Force (TF) Able Sentry in the Republic of Macedonia
Republic of Macedonia
Macedonia , officially the Republic of Macedonia , is a country located in the central Balkan peninsula in Southeast Europe. It is one of the successor states of the former Yugoslavia, from which it declared independence in 1991...
. The BCD was the only intelligence augmentation to TF Hawk, a V (US) Corps contingency force consisting of attack aviation, a multiple-launch rocket system (MLRS) battalion...and maneuver forces.". Under US doctrine for a combined task force (CTF) operation, "the air component (ACC) and land component (LCC) headquarters work hand-in-hand. The LCC has the intelligence support structure needed to develop the enemy ground order of battle, identify enemy vulnerabilities and offer possible courses of action. The ground commander pushes the intelligence to the CFACC through the BCE intelligence section, providing clarity of the enemy ground situation. The LCC drives the focus for collecting, tracking, targeting and attacking enemy ground forces.
"The air component headquarters... traditionally runs the air campaign. Its intelligence support structure focuses on developing fixed targets for air assets to service..." In this operation, the CAOC did not have the ground intelligence structure to perform detailed Intelligence Preparation of the Battlefield (IPB) and relied on the analyzed intelligence relayed through the BCE from the LCC’s organic intelligence element.
Because TF Hawk's BCD was the only all-source US intelligence unit in the operation, it was unable to provide the services that it could have if in the larger intelligence center for which it was intended. Not only was there no all-source US ground intelligence, but the TF Hawk Ground Analysis Cell (ACE)...controlled who could access specific pieces of information within US-Only channels. The coalition Ground Analysis Cell could not use US-only data, depriving the coalition commander of a common enemy ground picture. Not only specialized data could not be shared, the doctrine did not support the use of the Hunter UAV.
UAVs have tremendous potential in combat, but before TF Hawk gained control of the Hunter, all US and NATO UAVs and drones were run by the National Collection Management Cell (NCMC), with full IMINT access. Using CCIRM, it deconflicted US theater, national and NATO targets. Thus [national-level] process ensured efficient, non-redundant coverage and maximum support available for theater collection.
When TF Hawk gained control of the RQ-5 Hunter
RQ-5 Hunter
The RQ-5 Hunter unmanned aerial vehicle was originally intended to serve as the United States Army's Short Range UAV system for division and corps commanders. It took off and landed on runways. It used a gimbaled EO/IR sensor to relay its video in real time via a second airborne Hunter over a...
UAV, the Hunter sorties were no longer synchronized with the NATO and US-only surveillance and deconfliction systems. This both prevented continuous coverage of key targets, but also led to circumstances where a target, identified by Hunter, could not be attacked because the UAV that found the target was on a different schedule than were strike resources.
UAV resources need to be controlled at a level that permits deconfliction and synchronization. The controlling headquarters certainly should be responsive to the needs of the tactical commander, but there are control issues that should not be of concern at the tactical level.
Boyd OODA Loop
John BoydJohn Boyd (military strategist)
Colonel John Boyd was a United States Air Force fighter pilot and Pentagon consultant of the late 20th century, whose theories have been highly influential in the military, sports, and business.-Biography:...
created a model of decision and action, originally for air-to-air fighter combat, but which has proven useful in many areas of conflict. His model has four phases, which, while not usually stated in terms of the intelligence cycle, do relate to that cycle:
-
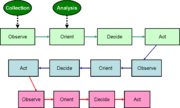
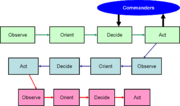
- Observe: become aware of a threat or opportunity
- Orient: put the observation into the context of other information
- Decide: make the best possible action plan that can be carried out in a timely manner
- Act: carry out the plan.
After the action, the actor observes again, to see the effects of the action. If the cycle works properly, the actor has initiative, and can orient, decide, and act even faster in the second and subsequent iterations of the Boyd loop.
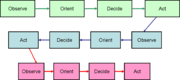
While Boyd treated his cycle as self-contained, it is reasonable to extend it to meeting the intelligence cycle. Observation can be an output of the collection phase, while orientation is an output of analysis.
Tasking and Direction
At the highest level of direction, rational policies, the effects of personalities, and culture can dominate the assignments given to the intelligence services.Policy Factors
Western governments tend to have, at best, creative tension among their law enforcement and national security organizations, foreign-oriented versus domestic-oriented organizations, and public versus private interests. There is usually a conflict between clandestine intelligence and covert action, which may compete for resources in the same organization.Balancing Law Enforcement and National Security; Foreign vs. Domestic Orientation
The first opposition is law enforcement versus intelligence. The two are very different worlds. Intelligence is oriented toward the future and seeks to inform policy makers. It lives in a blizzard of uncertainty where the "truth" will never be known for certain. Because intelligence strives above all to protect its sources and methods, intelligence officials want desperately to stay out of the chain of evidence so they will never have to testify in court. By contrast, law enforcement is not interested in policy. Rather, its business is the prosecution of cases. And law enforcement knows that if it is to make a case, it must be prepared to reveal something of how it knows what it knows.The Council on Foreign Relations recommended that "foreign policy ought to take precedence over law enforcement when it comes to overseas operations. The bulk of U.S. intelligence efforts overseas are devoted to traditional national security concerns; as a result, law enforcement must ordinarily be a secondary concern. FBI and DEA
Drug Enforcement Administration
The Drug Enforcement Administration is a federal law enforcement agency under the United States Department of Justice, tasked with combating drug smuggling and use within the United States...
agents operating abroad should not be allowed to act independently of either the ambassador or the CIA lest pursuit of evidence or individuals for prosecution cause major foreign policy problems or complicate ongoing intelligence and diplomatic activities. (The same should hold for any Defense Department personnel involved in intelligence activity overseas.) There are likely to be exceptions, and a degree of case-by-case decision-making will be inevitable. What is needed most is a Washington-based interagency mechanism involving officials from intelligence, law enforcement, and foreign policy to sort out individual cases. One now exists; the challenge is to make it work.
"At home, law enforcement should have priority and the intelligence community should continue to face restraints in what it can do vis-à-vis American citizens." The protection of civil liberties remains essential. National organizations intended for foreign operations, or military support, should operate within the home country only under specific authorization and when there is no other way to achieve the desired result. ... Regardless, the ability of intelligence agencies to give law enforcement incidentally acquired information on U.S. citizens at home or overseas ought to be continued. There should be no prohibition (other than those based on policy) on the intelligence community collecting information against foreign persons or entities. The question of what to do with the information, however, should be put before policymakers if it raises foreign policy concerns.
President Harry Truman had legitimate concerns about creating a "Gestapo", so insisted that the new CIA not have law enforcement or domestic authority. In an era of transnational terrorism and organized crime, there may not be clean distinctions between domestic and foreign activities.
Public versus Private
"During the Cold War, national security was a federal government monopoly. To be sure, private citizens and corporations were involved, but there was a neat correspondence between the threat as defined and the federal government's national security machinery that was developed to meet that threat. The war against terrorism and homeland security will be much less a federal government monopoly. Citizens of democracies and the economy are already suffering the inconvenience and higher business costs of much tighter security. And tragically, more ordinary citizens are likely to die from transnational terrorism."Public and private interests can both complement and conflict when it comes to economic intelligence. Multination corporations usually have capable intelligence capabilities in their core business, although they may not call them such. Lloyds of London has superb knowledge of maritime affairs. Oil companies have extensive information on world resources and energy demands. Investment banks can track capital flow.
This becomes especially difficult when private organizations seek to use national capabilities for their private benefit. Sometimes, a quid pro quo may be involved. Collection of secret economic information can be by several means-mostly SIGINT and HUMINT. The more sensitive reconnaissance satellites may not be needed to get substantially correct imagery; earth resources satellites may give adequate, or even better detail—reconnaissance satellites tend not to have the multispectral scanners that are best for agricultural or other economic information.
The private sector may already have good information on trade policy, resources, foreign exchange, and other economic factors. This may not be "open source" in the sense of being published, but can be bought, reliably, from research firms that need not have the overhead of all-source security. The intelligence agencies can use their all-source capability for verification rather than original collection. Intelligence agencies, working with national economic and diplomatic employees, can develop policy alternatives for negotiators.
One subtle aspect of the role of economic intelligence is the interdependence of the continental and world economies. The economic health of Mexico clearly affects the United States, just as the Turkish economy is of concern to the European Community. In a post-cold-war environment, the roles of Russia and China are still evolving. Japan, with a history of blurred lines between industry and government, may regard a policy, perfectly ethical for them, which would be questionable in North America or Eastern Europe. New groupings such as the Shanghai Cooperative Organization are principally economic. Economic measures also may be used to pressure specific countries, as, for example, South Africa while it sustained a policy of apartheid, or Sudan while there is widespread persecution in Darfur
Darfur
Darfur is a region in western Sudan. An independent sultanate for several hundred years, it was incorporated into Sudan by Anglo-Egyptian forces in 1916. The region is divided into three federal states: West Darfur, South Darfur, and North Darfur...
.
Clandestine Intelligence versus Covert Action
Clandestine and covert operations share many attributes, but also have distinct differences. They may share, for example, a technical capability for cover and forgery, and need secret logistical support. The essence of covert action is that its sponsor cannot be proven. One term of art is that the sponsor has "plausible deniability." In some cases, such as sabotage, the target indeed may not be aware of the action. Assassinations, however, are immediately known, but, if the assassin escapes or is killed in the action, the sponsor may never be known other than to the sponsor.See a Congressional study, Special Operations Forces (SOF) and CIA Paramilitary Operations: Issues for Congress,
for one policy review.
Coordination of HUMINT and Covert Action
Experience has shown that some high level of government needs to be aware of both clandestine and covert field activities, to prevent them interfering with one another, and with secret activities that may not be in the field. For example, one WWII failure took place when Office of Strategic Services
Office of Strategic Services
The Office of Strategic Services was a United States intelligence agency formed during World War II. It was the wartime intelligence agency, and it was a predecessor of the Central Intelligence Agency...
(OSS) field agents broke into the Japanese Embassy in Lisbon, and stole cryptographic materials. Of course, this allowed past communications to be read. The net effect of this operation was disastrous, as the particular cryptosystem had been broken by cryptanalysis, who were reading the traffic in parallel with the intended recipients. The covert burglary—the Japanese did not catch the OSS team, so were not certain who did it—caused the Japanese to change cryptosystems, invalidating the clandestine work of the cryptanalysts. In World War II, the UK kept its Secret Intelligence Service
Secret Intelligence Service
The Secret Intelligence Service is responsible for supplying the British Government with foreign intelligence. Alongside the internal Security Service , the Government Communications Headquarters and the Defence Intelligence , it operates under the formal direction of the Joint Intelligence...
principally focused on HUMINT, while the Special Operations Executive
Special Operations Executive
The Special Operations Executive was a World War II organisation of the United Kingdom. It was officially formed by Prime Minister Winston Churchill and Minister of Economic Warfare Hugh Dalton on 22 July 1940, to conduct guerrilla warfare against the Axis powers and to instruct and aid local...
was created for direct action and support of resistance movements. The Political Warfare Executive
Political Warfare Executive
During World War II, the Political Warfare Executive was a British clandestine body created to produce and disseminate both white and black propaganda, with the aim of damaging enemy morale and sustaining the morale of the Occupied countries....
also was created, for psychological warfare.
Even in democracies, HUMINT resources have been abused. In the case of the US, these have involved such things as Iran-Contra and support to the "plumbers unit" of the Nixon campaign and administration, as well as infiltrating legal groups using a justification of force protection. British actions in Northern Ireland, and against terror groups in Gibraltar and elsewhere, have been criticized, as have French actions against Greenpeace. "...Contrary to widespread impressions, one problem with the clandestine services has been a lack of initiative brought about by a fear of retroactive discipline and a lack of high-level support. This must be rectified if the intelligence community is to continue to produce the human intelligence that will surely be needed in the future."
For a detailed discussion, see Clandestine HUMINT and Covert Action
Clandestine HUMINT and Covert Action
National governments deal in both intelligence and military special operations functions that either should be completely secret , or simply cannot be linked to the sponsor...
.
Common Risks and Resources
Clandestine collection entails many more risks than the technical collection disciplines. Therefore, how and when it is used must be highly selective, responding to carefully screened and highest priority requirements...It cannot be kept "on the shelf" and called out whenever needed. There must be some minimal ongoing capability that can be expanded in response to consumer needs. This has become increasingly difficult for clandestine services, as diplomats, in response to budget pressures, has reduced its presence that could provide official cover.
The House Committee on Intelligence, in 1996, recommended a single Clandestine Service (CS) should include those components of the Defense HUMINT Service (DHS) that undertake clandestine collection as well. The congressional concern about strategic military HUMINT, however, may not apply to military special operations forces or to force protection. "This is not meant to preclude the Service Intelligence Chiefs from carrying out those clandestine collection activities specifically related to the tactical needs of their Military Departmental customers or field commanders.
Clandestine HUMINT and covert action involve the only part of governments that are required, on a routine basis, to break foreign laws. "As several former DCIs have pointed out, the clandestine services are also the DCI's most important "action arm," not only running covert action programs at the direction of the President (a function whose utility we believe will continue to be important), but also in managing most the IC's liaison with foreign government leaders and security services. A House staff report is of the opinion that analysis should be separate from both covert action and clandestine HUMINT, or other clandestine collection that breaks foreign laws. HUMINT is and should be part of a larger IC-wide collection plan.
Political Misuse
Nowhere has political abuse of intelligence services been greater than in totalitarian states, where the use of what the Soviets called the "organs of state security" would take on tasks far outside any intelligence mission.
"The danger of politicization-the potential for the intelligence community to distort information or judgment in order to please political authorities-is real. Moreover, the danger can never be eliminated if intelligence analysts are involved, as they must be, in the policy process. The challenge is to develop reasonable safeguards while permitting intelligence producers and policymaking consumers to interact.
Prioritization
Upper managers may order the collection department to focus on specific targets, and, on a longer term basis, especially for the technical collection disciplines, may prioritize the means of collection through budgeting resources for one discipline versus another, and, within a discipline, one system rather than another. Collection is not the only thing that must be prioritized; the analysts need to know where to start in what is often a flood of information."Intelligence collection priorities, while reflecting both national interests and broader policy priorities, need to be based on other considerations. First, there must be a demonstrated inadequacy of alternative sources; except in rare circumstances, the intelligence community does not need to confirm through intelligence what is already readily available." It is not an accident that in most intelligence and operations watch centers, a television set is always tuned to the Cable News Network. While initial news reports may be fragmentary, this particular part of OSINT is a powerful part of warning, but not necessarily of detailed analyses.
"Collection priorities must not only be those subjects that are policy-relevant but also involve information that the intelligence community can best (or uniquely) ascertain."
One other aspect of analysis merits mention, namely, the balance between current intelligence and long-term estimates. For years the culture of the intelligence community, in particular that of the CIA, favored the latter. But it is precisely in long- term analysis of familiar subjects and broad trends where secret information tends to be less critical and government analysts are for the most part no better and often not as good as their counterparts in academia and the private sector. Also, many estimates are likely to be less relevant to busy policymakers, who must focus on the immediate. To the extent long-term estimates are produced, they ought to be concise, written by individuals, and sources justifying conclusions ought to be shown as they would in any academic work. If the project is a group effort, differences among participants ought to be sharpened and prominently acknowledged. While it is valuable to point out consensus, it is more important that areas of dispute be highlighted than that all agencies be pressured to reach a conclusion that represents little more than a lowest common denominator.
Budgeting
While each nation has its own budgeting process, the major divisions of the US process are representative:- National intelligence, often excluding specifically national-level military intelligence,
- National-level military intelligence
- Military tactical intelligence
- Transnational intelligence, often involving law enforcement, for terrorism and organized crime
- Internal counterintelligence and antiterrorism.
Again depending on the nation, at some level of detail, budgetary information will be classified, as changes in budget indicate changes in priorities. After considerable debate, the US now publishes total budgets for the combination of its intelligence agencies. Depending on the sensitivity of a line item, it may be identified simply as "classified activity", not broken out but briefed to full oversight committees, or only revealed to a small number of officials.
"It should be possible to empower a committee composed of mid-level officials (or aides to senior officials) from the intelligence and policymaking communities to convene regularly to determine and revise priorities. The key is to try to get policymakers to provide guidance for both collection and analysis, to communicate not just what they want but also what they do not.
The CFR proposed a "market constraint" on consumers, in which they could only get a certain amount of intelligence from the intelligence community, before they had to provide additional funding. A different constraint would be that an agency, to get information on a new topic, must agree to stop or reduce coverage on something currently being monitored for it. Even with this consumer-oriented model, the intelligence community itself needs to have a certain amount of resources that it can direct itself, for building basic intelligence and identifying unusual threats.
"It is important that intelligence officers involved in articulating requirements represent both analysts and collectors, including those from the clandestine side. In addition, collection should be affected by the needs of policymakers and operators. All of this argues strongly against any organizational reforms that would isolate the collection agencies further or increase their autonomy.
Especially in nations with advanced technical sensors, there is an interaction between budgeting and technology. For example, the US has tended, in recent years, to use billion-dollar SIGINT satellites, where France has used "swarms" of "microsatellites". The quantity versus quality battle is as evident in intelligence technology as in weapons systems. The US has also fought a stovepipe
Stovepipe
A stovepipe is the chimney of a coal- or wood-burning stove.Stovepipe may also refer to:- Clothing :* Stovepipe hat, tall top hat with a consistent width* Stovepipe pants, style of slim-fit pants also known as drainpipes...
battle, in which SIGINT and IMINT satellites, in a given orbit, were launched by different agencies. New plans put SIGINT, MASINT, and IMINT sensors, appropriate to a type of orbit, on common platforms.

