Cryptomeria cipher
Encyclopedia
The Cryptomeria cipher, also called C2, is a proprietary
block cipher
defined and licensed by the 4C Entity
. It is the successor to CSS
algorithm (used for DVD-Video) and was designed for the CPRM/CPPM
digital rights management
scheme which are used by DRM-restricted Secure Digital card
s and DVD-Audio
discs.
. Like DES
, it has a key size
of 56 bits and a block size
of 64 bits. The encryption and decryption algorithms are available for peer review
, but implementations require the so-called "secret constant", the values of the substitution box
(S-box), which are only available under a license from the 4C Entity.
The 4C Entity licenses a different set of S-boxes for each application (such as DVD-Audio
, DVD-Video
and CPRM).
A paper by Julia Borghoff, Lars Knudsen
, Gregor Leander and Krystian Matusiewicz in 2009 breaks the full-round cipher in three different scenarios; it presents a 224 time complexity attack to recover the S-box in a chosen-key scenario, a 248 boomerang attack
to recover the key with a known S-box using 244 adaptively chosen plaintexts/ciphertexts, and a 253.5 attack when both the key and S-box are unknown.
broadcasters that they would start broadcasting programs with the copy-once broadcast flag
starting with 2004-04-05, a distributed Cryptomeria cipher brute force cracking effort was launched on 2003-12-21. To enforce the broadcast flag, digital video recorder
s employ CPRM-compatible storage devices, which the project aimed to circumvent. However, the project was ended and declared a failure on 2004-03-08 after searching the entire 56-bit keyspace, failing to turn up a valid key for unknown reasons.
Because the attack was based on S-box values from DVD-Audio
, it was suggested that CPRM may use different S-boxes.
Another brute force attack to recover DVD-Audio
CPPM device keys was mounted on 2009-05-06. The attack was intended to find any of 24570 secret device keys by testing MKB
file from Queen "The Game" DVD-Audio
disc. On 2009-10-20 such key for column 0 and row 24408 was discovered.
The similar brute force attack to recover DVD-VR
CPRM device keys was mounted on 2009-10-20. The attack was intended to find any of 3066 secret device keys by testing MKB
from Panasonic LM-AF120LE DVD-RAM
disc. On 2009-11-27 such key for column 0 and row 2630 was discovered.
By now the CPPM/CPRM protection scheme is deemed unreliable.
Proprietary software
Proprietary software is computer software licensed under exclusive legal right of the copyright holder. The licensee is given the right to use the software under certain conditions, while restricted from other uses, such as modification, further distribution, or reverse engineering.Complementary...
block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
defined and licensed by the 4C Entity
4C Entity
The 4C Entity is a consortium formed by IBM, Intel, Matsushita and Toshiba to establish a common platform for digital rights management schemes...
. It is the successor to CSS
Content Scramble System
Content Scramble System is a Digital Rights Management and encryption system employed on almost all commercially produced DVD-Video discs. CSS utilizes a proprietary 40-bit stream cipher algorithm...
algorithm (used for DVD-Video) and was designed for the CPRM/CPPM
Content Protection for Recordable Media
Content Protection for Recordable Media and Pre-Recorded Media is a mechanism for controlling the copying, moving and deletion of digital media on a host device, such as a personal computer, or other digital player...
digital rights management
Digital rights management
Digital rights management is a class of access control technologies that are used by hardware manufacturers, publishers, copyright holders and individuals with the intent to limit the use of digital content and devices after sale. DRM is any technology that inhibits uses of digital content that...
scheme which are used by DRM-restricted Secure Digital card
Secure Digital card
Secure Digital is a non-volatile memory card format developed by the SD Card Association for use in portable devices. The SD technology is used by more than 400 brands across dozens of product categories and more than 8,000 models, and is considered the de-facto industry standard.Secure Digital...
s and DVD-Audio
DVD-Audio
DVD-Audio is a digital format for delivering high-fidelity audio content on a DVD. DVD-Audio is not intended to be a video delivery format and is not the same as video DVDs containing concert films or music videos....
discs.
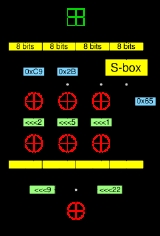
Cipher details
The C2 symmetric key algorithm is a 10-round Feistel cipherFeistel cipher
In cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German-born physicist and cryptographer Horst Feistel who did pioneering research while working for IBM ; it is also commonly known as a Feistel network. A large proportion of block...
. Like DES
Data Encryption Standard
The Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
, it has a key size
Key size
In cryptography, key size or key length is the size measured in bits of the key used in a cryptographic algorithm . An algorithm's key length is distinct from its cryptographic security, which is a logarithmic measure of the fastest known computational attack on the algorithm, also measured in bits...
of 56 bits and a block size
Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
of 64 bits. The encryption and decryption algorithms are available for peer review
Peer review
Peer review is a process of self-regulation by a profession or a process of evaluation involving qualified individuals within the relevant field. Peer review methods are employed to maintain standards, improve performance and provide credibility...
, but implementations require the so-called "secret constant", the values of the substitution box
Substitution box
In cryptography, an S-Box is a basic component of symmetric key algorithms which performs substitution. In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext — Shannon's property of confusion...
(S-box), which are only available under a license from the 4C Entity.
The 4C Entity licenses a different set of S-boxes for each application (such as DVD-Audio
DVD-Audio
DVD-Audio is a digital format for delivering high-fidelity audio content on a DVD. DVD-Audio is not intended to be a video delivery format and is not the same as video DVDs containing concert films or music videos....
, DVD-Video
DVD-Video
DVD-Video is a consumer video format used to store digital video on DVD discs, and is currently the dominant consumer video format in Asia, North America, Europe, and Australia. Discs using the DVD-Video specification require a DVD drive and a MPEG-2 decoder...
and CPRM).
Cryptanalysis
In 2008, an attack was published against a reduced 8-round version of Cryptomeria to discover the S-box in a chosen-key scenario. In a practical experiment, the attack succeeded in recovering parts of the S-box in 15 hours of CPU time, using 2 plaintext-ciphertext pairs.A paper by Julia Borghoff, Lars Knudsen
Lars Knudsen
Lars Ramkilde Knudsen is a Danish researcher in cryptography, particularly interested in the design and analysis of block ciphers, hash functions and message authentication codes .-Academic:...
, Gregor Leander and Krystian Matusiewicz in 2009 breaks the full-round cipher in three different scenarios; it presents a 224 time complexity attack to recover the S-box in a chosen-key scenario, a 248 boomerang attack
Boomerang attack
In cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David Wagner, who used it to break the COCONUT98 cipher....
to recover the key with a known S-box using 244 adaptively chosen plaintexts/ciphertexts, and a 253.5 attack when both the key and S-box are unknown.
Distributed brute force cracking effort
Following an announcement by Japanese HDTVHigh-definition television
High-definition television is video that has resolution substantially higher than that of traditional television systems . HDTV has one or two million pixels per frame, roughly five times that of SD...
broadcasters that they would start broadcasting programs with the copy-once broadcast flag
Broadcast flag
A broadcast flag is a set of status bits sent in the data stream of a digital television program that indicates whether or not the data stream can be recorded, or if there are any restrictions on recorded content...
starting with 2004-04-05, a distributed Cryptomeria cipher brute force cracking effort was launched on 2003-12-21. To enforce the broadcast flag, digital video recorder
Digital video recorder
A digital video recorder , sometimes referred to by the merchandising term personal video recorder , is a consumer electronics device or application software that records video in a digital format to a disk drive, USB flash drive, SD memory card or other local or networked mass storage device...
s employ CPRM-compatible storage devices, which the project aimed to circumvent. However, the project was ended and declared a failure on 2004-03-08 after searching the entire 56-bit keyspace, failing to turn up a valid key for unknown reasons.
Because the attack was based on S-box values from DVD-Audio
DVD-Audio
DVD-Audio is a digital format for delivering high-fidelity audio content on a DVD. DVD-Audio is not intended to be a video delivery format and is not the same as video DVDs containing concert films or music videos....
, it was suggested that CPRM may use different S-boxes.
Another brute force attack to recover DVD-Audio
DVD-Audio
DVD-Audio is a digital format for delivering high-fidelity audio content on a DVD. DVD-Audio is not intended to be a video delivery format and is not the same as video DVDs containing concert films or music videos....
CPPM device keys was mounted on 2009-05-06. The attack was intended to find any of 24570 secret device keys by testing MKB
Media Key Block
The Media Key Block is one of the keys that are included inside the copying protection system AACS. This system is used to protect Blu-ray and HD DVD formats from being copied...
file from Queen "The Game" DVD-Audio
DVD-Audio
DVD-Audio is a digital format for delivering high-fidelity audio content on a DVD. DVD-Audio is not intended to be a video delivery format and is not the same as video DVDs containing concert films or music videos....
disc. On 2009-10-20 such key for column 0 and row 24408 was discovered.
The similar brute force attack to recover DVD-VR
DVD-VR
The DVD-VR standard defines a logical format for video recording on DVD-R, DVD-RW, and DVD-RAM style media, including the dual layer versions of these media. As opposed to media recorded with the DVD+VR recording standard, the resulting media are not DVD-Video compliant, and will not play back in...
CPRM device keys was mounted on 2009-10-20. The attack was intended to find any of 3066 secret device keys by testing MKB
Media Key Block
The Media Key Block is one of the keys that are included inside the copying protection system AACS. This system is used to protect Blu-ray and HD DVD formats from being copied...
from Panasonic LM-AF120LE DVD-RAM
DVD-RAM
DVD-RAM is a disc specification presented in 1996 by the DVD Forum, which specifies rewritable DVD-RAM media and the appropriate DVD writers. DVD-RAM media have been used in computers as well as camcorders and personal video recorders since 1998.-Design:DVD-RAM is one of three competing...
disc. On 2009-11-27 such key for column 0 and row 2630 was discovered.
By now the CPPM/CPRM protection scheme is deemed unreliable.

