
Open mail relay
Encyclopedia
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
to send e-mail
E-mail
Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
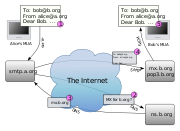
through it, not just mail destined to or originating from known users. This used to be the default configuration in many mail servers; indeed, it was the way the Internet was initially set up, but open mail relays have become unpopular due to their exploitation by spammers
Spam (electronic)
Spam is the use of electronic messaging systems to send unsolicited bulk messages indiscriminately...
and worms
Computer worm
A computer worm is a self-replicating malware computer program, which uses a computer network to send copies of itself to other nodes and it may do so without any user intervention. This is due to security shortcomings on the target computer. Unlike a computer virus, it does not need to attach...
. Many relays were closed, or were placed on blacklist
Blacklist (computing)
In computing, a blacklist or block list is a basic access control mechanism that allows everyone access, except for the members of the black list . The opposite is a whitelist, which means allow nobody, except members of the white list...
s by other servers.
History and technology
Until the 1990s being an open relay was a common configuration for a mail server and was often the default on UNIXUnix
Unix is a multitasking, multi-user computer operating system originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Brian Kernighan, Douglas McIlroy, and Joe Ossanna...
systems at installation. This was due, in part, to the traditional store-and-forward method of getting e-mail to its destination. E-mail was passed from computer to computer (through and beyond the Internet) via modems on telephone lines. For many early networks, such as UUCPNET, FidoNet
FidoNet
FidoNet is a worldwide computer network that is used for communication between bulletin board systems. It was most popular in the early to mid 1990s, prior to the introduction of easy and affordable access to the Internet...
and BITNET
BITNET
BITNET was a cooperative USA university network founded in 1981 by Ira Fuchs at the City University of New York and Greydon Freeman at Yale University...
, lists of machines that were open relays were a core part of those networks. Filtering
E-mail filtering
Email filtering is the processing of email to organize it according to specified criteria. Most often this refers to the automatic processing of incoming messages, but the term also applies to the intervention of human intelligence in addition to anti-spam techniques, and to outgoing emails as well...
and speed of e-mail delivery were not priorities at that time and in any case the government and educational servers which started the Internet were covered by a federal edict forbidding the transfer of commercial messages.
Abuse by spammers
In the mid-1990s, with the rise of spamming, spammers resorted to re-routing their e-mail through third party e-mail servers to avoid detection and to exploit the additional resources of these open relay servers. Spammers would send one e-mail to the open relay and (effectively) include a large blind carbon copyBlind Carbon Copy
In the context of correspondence, blind carbon copy refers to the practice of sending a message to multiple recipients in such a way that conceals the fact that there may be additional addressees from the complete list of recipients...
list, then the open relay would relay that spam to the entire list. While this greatly reduced the bandwidth requirements for spammers at a time when Internet connections were limited, it forced each spam to be an exact copy and thus easier to detect. After abuse by spammers became widespread, operating an open relay came to be frowned upon among the majority of Internet server administrators and other prominent users,. Open relays are recommended against in RFC 2505 and RFC 5321 (which defines SMTP). The exact copy nature of spam using open relays made it easy to create bulk e-mail detection systems such as Vipul's Razor
Vipul's Razor
Vipul's Razor is a checksum-based, distributed, collaborative, spam-detection-and-filtering network. Through user contribution, Razor establishes a distributed and constantly updating catalogue of spam in propagation that is consulted by email clients to filter out known spam. Detection is done...
and the Distributed Checksum Clearinghouse
Distributed Checksum Clearinghouse
Distributed Checksum Clearinghouse is a hash sharing method of spam email detection.The basic logic in DCC is that most spam mails are sent to many recipients. The same message body appearing many times is therefore bulk email. DCC identifies bulk email by taking a checksum and sending that...
. To counter this, spammers were forced to switch to using hash buster
Hash buster
A hash buster is a program which randomly adds characters to data for the data's hash sum to be different than if the characters were not added.This is typically used to add words to spam e-mails, to bypass hash filters...
s to make them less effective and the advantage of using open relays was removed since every copy of spam was "unique" and had to be sent individually.
Since open mail relays make no effort to verify that the owner of an address is the actual sender of an e-mail, open mail relays are vulnerable to address spoofing
E-mail spoofing
Email spoofing is email activity in which the sender address and other parts of the email header are altered to appear as though the email originated from a different source. Because core SMTP doesn't provide any authentication, it is easy to impersonate and forge emails...
.
Anti-spam efforts
Many Internet service providers use DNSBLDNSBL
A DNSBL is a list of IP addresses published through the Internet Domain Name Service either as a zone file that can be used by DNS server software, or as a live DNS zone that can be queried in real-time...
s (DNS-based Blocking Lists) to disallow mail from open relays. Once a mail server is detected or reported that allows third parties to send mail through them, they will be added to one or more such lists, and other e-mail servers using those lists will reject any mail coming from those sites. The relay need not actually be used for sending spam to be blacklisted: instead, it may be blacklisted after simple test that just confirms open access.
This trend reduced the percentage of mail senders that were open relays from over 90% down to well under 1% over several years. This led to spammers adopting other techniques, such as the use of botnet
Botnet
A botnet is a collection of compromised computers connected to the Internet. Termed "bots," they are generally used for malicious purposes. When a computer becomes compromised, it becomes a part of a botnet...
s of zombie computer
Zombie computer
In computer science, a zombie is a computer connected to the Internet that has been compromised by a cracker, computer virus or trojan horse and can be used to perform malicious tasks of one sort or another under remote direction. Botnets of zombie computers are often used to spread e-mail spam...
s to send spam.
One consequence of the new unacceptability of open relays was an inconvenience for some end users and certain internet service provider
Internet service provider
An Internet service provider is a company that provides access to the Internet. Access ISPs directly connect customers to the Internet using copper wires, wireless or fiber-optic connections. Hosting ISPs lease server space for smaller businesses and host other people servers...
s. To allow customers to use their e-mail addresses at Internet locations other than the company's systems (such as at school or work), many mail sites explicitly allowed open relaying so that customers could send e-mail via the ISP from any location. Once open relay became unacceptable due to abuse (and unusable due to blocking of open relays) ISPs and other sites had to adopt new protocols to allow remote users to send mail. These include smart host
Smart host
A smart host is a type of mail relay server which allows an SMTP server to route e-mail to an intermediate mail server rather than directly to the recipient’s server. Often this smart host requires authentication from the sender to verify that the sender has privileges to have mail forwarded...
s, SMTP-AUTH, POP before SMTP
POP before SMTP
POP before SMTP or SMTP after POP is a method of authorization used by mail server software which helps allow users the option to send e-mail from any location, as long as they can demonstrably also fetch their mail from the same place....
, and the use of virtual private network
Virtual private network
A virtual private network is a network that uses primarily public telecommunication infrastructure, such as the Internet, to provide remote offices or traveling users access to a central organizational network....
s (VPNs). The IETF has written a best current practice
Best Current Practice
A best current practice is a de facto, dynamic level of performance in engineering and information technology. It is more flexible than a standard, since techniques and tools are continually evolving....
s covering Email Submission Operations in RFC 5068.
Note that the above only becomes an issue if the user wishes to (or has to) continue to send e-mail remotely, using the same SMTP server which they were previously accessing locally. If they have valid access to some other SMTP server from their new, remote location, then they will typically be able to use that new server to send e-mails as if from their old address, even when this server is properly secured. (Although this may involve some reconfiguration of the user's E-mail client
E-mail client
An email client, email reader, or more formally mail user agent , is a computer program used to manage a user's email.The term can refer to any system capable of accessing the user's email mailbox, regardless of it being a mail user agent, a relaying server, or a human typing on a terminal...
which may not be entirely straightforward.)
The Can Spam Act of 2003 makes it illegal to send spam through an open relay in the United States
United States
The United States of America is a federal constitutional republic comprising fifty states and a federal district...
, but makes no provision regarding sending personal e-mail through them or regarding their operation, although the effectiveness of the act has been questioned.
Modern-day proponents
The most famous open mail relay operating today is probably that of John Gilmore, who argues that running an open relay is a free speech issue. His server is included on many open relay blacklists (many of which are generated by "automatic detection", that is, by anti-spam blacklisters sending an (unsolicited) test e-mail to other servers to see if they will be relayed). These measures cause much of his outgoing e-mail to be blocked. Along with his further deliberate configuration of the server, his open relay enables people to send e-mail without their IP address being directly visible to the recipient and thereby send e-mail anonymouslyAnonymity
Anonymity is derived from the Greek word ἀνωνυμία, anonymia, meaning "without a name" or "namelessness". In colloquial use, anonymity typically refers to the state of an individual's personal identity, or personally identifiable information, being publicly unknown.There are many reasons why a...
. In 2002, his open relay, along with 24 others, was used by a computer worm
Computer worm
A computer worm is a self-replicating malware computer program, which uses a computer network to send copies of itself to other nodes and it may do so without any user intervention. This is due to security shortcomings on the target computer. Unlike a computer virus, it does not need to attach...
to propagate.
John Gilmore and other open relay proponents declare that they do not support spam and spamming, but see bigger threat in attempts to limit web capabilities that may block evolution of the new, next generation technologies. They compare the network communication restrictions with restrictions that some phone companies tried to place on their lines in the past, preventing transferring of computer data rather than speech.
Closing relays
In order not to be considered "open," an e-mail relay should be configured to accept and forward only the following messages (details will vary from system to system - in particular, further restrictions may well apply):- Messages from local IP addressIP addressAn Internet Protocol address is a numerical label assigned to each device participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing...
es to local mailboxes - Messages from local IP addresses to non-local mailboxes
- Messages from non-local IP addresses to local mailboxes
- Messages from clients that are authenticatedAuthenticationAuthentication is the act of confirming the truth of an attribute of a datum or entity...
and authorizedAuthorizationAuthorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy...
In particular, a properly secured SMTP mail relay should not accept and forward arbitrary e-mails from non-local IP addresses to non-local mailboxes by an unauthenticated or unauthorized user.
In general, any other rules which an administrator chooses to enforce (for instance, based on what an e-mail gives as its own envelope from address) must be in addition to, rather than instead of, the above. If not, the relay is still effectively open (for instance, by the above rules): it is easy to forge e-mail header and envelope information, it is considerably harder to successfully forge an IP address in a TCP/IP transaction due to the three-way handshake that occurs as a connection is started.
Open relays have also resulted from security flaws in software, rather than misconfiguration by system administrators. In these cases, security patches need to be applied to close the relay.
Internet initiatives to close open relays have ultimately proven to be unsuccessful because spammers have created distributed botnet
Botnet
A botnet is a collection of compromised computers connected to the Internet. Termed "bots," they are generally used for malicious purposes. When a computer becomes compromised, it becomes a part of a botnet...
s of zombie computer
Zombie computer
In computer science, a zombie is a computer connected to the Internet that has been compromised by a cracker, computer virus or trojan horse and can be used to perform malicious tasks of one sort or another under remote direction. Botnets of zombie computers are often used to spread e-mail spam...
s that contain malware with mail relaying capability. The number of clients under spammers' control is now so great that previous anti-spam countermeasures that focused on closing open relays are no longer effective.

