
Neuman-Stubblebine protocol
Encyclopedia
The Neuman–Stubblebine protocol is a computer network
authentication
protocol
designed for use on insecure networks (e.g., the Internet
). It allows individuals communicating over such a network to prove their identity to each other. This protocol utilizes time stamps, but does not depend on synchronized clocks.
(A) initiates the communication to Bob (B) with S is a server trusted by both parties, the protocol can be specified as follows using security protocol notation
:

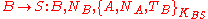
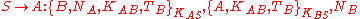
Alice forwards the message and verifies is the same that she generated earlier. Bob will verify
is the same that she generated earlier. Bob will verify 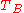 and
and 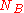 have not changed when he receives the message.
have not changed when he receives the message.
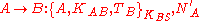
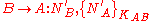
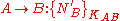
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
authentication
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
protocol
Communications protocol
A communications protocol is a system of digital message formats and rules for exchanging those messages in or between computing systems and in telecommunications...
designed for use on insecure networks (e.g., the Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
). It allows individuals communicating over such a network to prove their identity to each other. This protocol utilizes time stamps, but does not depend on synchronized clocks.
The protocol
If AliceAlice and Bob
The names Alice and Bob are commonly used placeholder names for archetypal characters in fields such as cryptography and physics. The names are used for convenience; for example, "Alice sends a message to Bob encrypted with his public key" is easier to follow than "Party A sends a message to Party...
(A) initiates the communication to Bob (B) with S is a server trusted by both parties, the protocol can be specified as follows using security protocol notation
Security protocol notation
In cryptography, security protocol notation is a way of expressing a protocol of correspondence between entities of a dynamic system, such as a computer network...
:
- A and B are identities of Alice and Bob respectively
- M is a session identifier
-
 is a symmetric key known only to A and S
is a symmetric key known only to A and S -
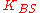 is a symmetric key known only to B and S
is a symmetric key known only to B and S -
 and
and 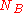 are noncesCryptographic nonceIn security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
are noncesCryptographic nonceIn security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
generated by A and B respectively -
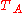 and
and 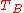 are timestampsTimestampA timestamp is a sequence of characters, denoting the date or time at which a certain event occurred. A timestamp is the time at which an event is recorded by a computer, not the time of the event itself...
are timestampsTimestampA timestamp is a sequence of characters, denoting the date or time at which a certain event occurred. A timestamp is the time at which an event is recorded by a computer, not the time of the event itself...
generated by A and B respectively -
 is a generated symmetric key, which will be the session keySession keyA session key is a single-use symmetric key used for encrypting all messages in one communication session. A closely related term is traffic encryption key or TEK, which refers to any key used to encrypt messages, as opposed to other uses, like encrypting other keys .Session keys can introduce...
is a generated symmetric key, which will be the session keySession keyA session key is a single-use symmetric key used for encrypting all messages in one communication session. A closely related term is traffic encryption key or TEK, which refers to any key used to encrypt messages, as opposed to other uses, like encrypting other keys .Session keys can introduce...
of the session between A and B

- Alice notified Bob of intent to initiate secure communication.
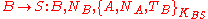
- Bob generates a times stamp and a nonce, and sends this to the trusted Server.
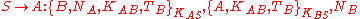
- The trusted Server generates a session key and a message for Alice to forward to Bob.
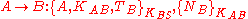
Alice forwards the message and verifies
 is the same that she generated earlier. Bob will verify
is the same that she generated earlier. Bob will verify 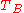 and
and 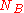 have not changed when he receives the message.
have not changed when he receives the message.Subsequent communications
An advantage provided by this protocol is that Alice can utilize the trusted Server's message to initiate authentication with Bob within some predetermined time limit without utilizing the trusted Server. The protocol proceeds as follows using the same definitions as above.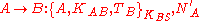
- Alice sends the message the trusted Server sent her previously when communication with Bob.
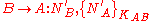
- Bob sends Alice a new nonce and her new nonce encrypted with session key that Alice resent from previous communication.
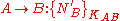
- Alice returns Bob's nonce encrypted with the session key to allow him to verify the communication is successful.
Attack
Using the theorem prover SPASS it has been shown that this protocol can be attacked . This attack and two more from are outlined in http://www.lsv.ens-cachan.fr/Software/spore/neumannStubblebine.pdf.See also
- Kerberos
- Needham–Schroeder protocol
- Otway–Rees protocol
- YahalomYahalom (protocol)Yahalom is an authentication and secure key-sharing protocol designed for use on an insecure network such as the Internet. Yahalom uses a trusted arbitrator to distribute a shared key between two people...
- Wide Mouth Frog protocolWide Mouth Frog protocolThe Wide-Mouth Frog protocol is a computer network authentication protocol designed for use on insecure networks . It allows individuals communicating over a network to prove their identity to each other while also preventing eavesdropping or replay attacks, and provides for detection of...

