Lawful interception
Encyclopedia
Lawful interception is obtaining communications network data pursuant to lawful authority for the purpose of analysis
or evidence
. Such data generally consist of signalling
or network management
information or, in fewer instances, the content of the communications. If the data are not obtained in real-time, the activity is referred to as access to retained data (RD).
There are many bases for this activity that include infrastructure protection and cybersecurity. In general, the operator of public network infrastructure can undertake LI activities for those purposes. Operators of private network infrastructures have an inherent right to maintain LI capabilities within their own networks unless otherwise prohibited.
One of the bases for LI is the interception of telecommunications by law enforcement agencies (LEAs), regulatory or administrative agencies, and intelligence services, in accordance with local law. Under some legal systems, implementations—particularly real-time access to content—may require due process and receiving proper authorization from competent authorities—an activity that was formerly known as "wiretapping" and has existed since the inception of electronic communications. The material below primarily treats this narrow segment of LI.
With the legacy public switched telephone network
(PSTN), wireless, and cable systems, lawful interception (LI) was generally performed by accessing the mechanical or digital switches supporting the targets' calls. The introduction of packet switched networks, softswitch technology, and server-based applications the past two decades fundamentally altered how LI is undertaken.
, with the specific capabilities promulgated jointly by the Federal Communications Commission and the Department of Justice.
To prevent investigations' being compromised, LI systems may be designed in a manner that hides the interception from the telecommunications operator concerned. This is a requirement in some jurisdictions.
To ensure systematic procedures for carrying out interception, while also lowering the costs of interception solutions, industry groups and government agencies worldwide have attempted to standardize the technical processes behind lawful interception. One organization, ETSI, has been a major driver in lawful interception standards not only for Europe, but worldwide.
This architecture attempts to define a systematic and extensible means by which network operators and law enforcement agents (LEAs) can interact, especially as networks grow in sophistication and scope of services. Note this architecture applies to not only “traditional” wireline and wireless voice calls, but to IP-based services such as Voice over IP
, email, instant messaging, etc. The architecture is now applied worldwide (in some cases with slight variations in terminology), including in the United States in the context of CALEA
conformance. Three stages are called for in the architecture:
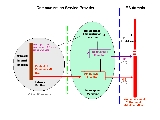
The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, including destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, duration, etc. Call content is namely the stream of data carrying the call. Included in the architecture is the lawful interception management function, which covers interception session set-up and tear down, scheduling, target identification, etc. Communications between the network operator and LEA are via the Handover Interfaces (designated HI). Communications data and content are typically delivered from the network operator to the LEA in an encrypted format over an IP-based VPN. The interception of traditional voice calls still often relies on the establishment of an ISDN channel that is set up at the time of the interception.
As stated above, the ETSI architecture is equally applicable to IP-based services where IRI (or CD) is dependent on parameters associated with the traffic from a given application to be intercepted. For example, in the case of email IRI would be similar to the header information on an email message (e.g., destination email address, source email address, time email was transmitted) as well as pertinent header information within the IP packets conveying the message (e.g., source IP address of email server originating the email message). Of course, more in-depth information would be obtained by the interception system so as to avoid the usual email address spoofing that often takes place (e.g., spoofing of source address). Voice-over-IP likewise has its own IRI, including data derived from Session Initiation Protocol (SIP) messages that are used to set up and tear down a VOIP call.
ETSI LI Technical Committee work today is primarily focussed on developing the new Retained Data Handover and Next Generation Network specifications, as well as perfecting the innovative TS102232 standards suite that apply to most contemporary network uses.
USA interception standards that help network operators and service providers conform to CALEA are mainly those specified by the Federal Communications Commission (which has both plenary legislative and review authority under CALEA) CableLabs
, and the Alliance for Telecommunications Industry Solutions (ATIS)
. ATIS's standards include new standards for broadband Internet access and VoIP services, as well as legacy J-STD-025B which updates the earlier J-STD-025A to include packetized voice and CDMA wireless interception. All of these standards have been challenged as "deficient" by the U.S. Dept of Justice pursuant to CALEA.
Generic global standards have also been developed by Cisco via the Internet Engineering Task Force (IETF)
that provide a front-end means of supporting most LI real-time handover standards.
(Budapest, 23 Nov 2001). The secretariat for the Convention is the Council of Europe. However, the treaty itself has signatories worldwide and provides a global scope.
Individual countries have different legal requirements relating to lawful interception. The Global Lawful Interception Industry Forum lists many of these, as does the Council of Europe secretariat. For example, in the United Kingdom the law is known as RIPA (Regulation of Investigatory Powers Act), in United States
there is an array of federal and state criminal law, in Commonwealth of Independent States
countries as SORM
.
, the European Council
Resolution of 17 January 1995 on the Lawful Interception of Telecommunications (Official Journal C 329) mandated similar measures to CALEA on a pan-European basis. Although some EU member countries reluctantly accepted this resolution out of privacy concerns (which are more pronounced in Europe than the US), there appears now to be general agreement with the resolution. Interestingly enough, interception mandates in Europe are generally more rigorous than those of the US; for example, both voice and ISP public network operators in the Netherlands
have been required to support interception capabilities for years. In addition, publicly available statistics indicate that the number of interceptions in Europe exceed by many hundreds of times those undertaken in the U.S.
Europe continues to maintain its global leadership role in this sector through the adoption by the European Parliament and Council in 2006 of the far reaching Data Retention Directive
. The provisions of the Directive broadly to almost all public electronic communications and require the capture of most related information, including location, for every communication. The information must be stored for a period of at least six months up to two years and made available to law enforcement upon lawful request. The Directive has been widely emulated in other countries.
, two Federal statutes apply to half of the lawful interception. The other half occur pursuant to local law. The 1968 Omnibus Crime Control and Safe Streets Act
, Title III pertains mainly to lawful interception criminal investigations. The second law, the 1978 Foreign Intelligence Surveillance Act, or FISA, as amended by the Patriot Act, governs wiretapping for intelligence purposes
where the subject of the investigation must be a foreign (non-US) national or a person working as an agent on behalf of a foreign country. The Administrator of the U.S. Courts annual reports indicate that the cases are related to illegal drug distribution
, with cell phones as the dominant form of intercepted communication.
During the 1990s, as in most countries, to help law enforcement and the FBI more effectively carry out wiretap operations, especially in view of the emerging digital voice and wireless network
s at the time, the US Congress passed CALEA
in 1994 . This act provides the Federal statutory framework for network operator assistance to LEAs in providing evidence and tactical information. In 2005, CALEA was applied to public broadband networks
Internet access and Voice over IP
services that are interconnected to the Public Switched Telephone Network
(PSTN).
– was fined US$1,000,000 in 2006 for failing to secure its systems against unlawful access.
Analysis
Analysis is the process of breaking a complex topic or substance into smaller parts to gain a better understanding of it. The technique has been applied in the study of mathematics and logic since before Aristotle , though analysis as a formal concept is a relatively recent development.The word is...
or evidence
Evidence
Evidence in its broadest sense includes everything that is used to determine or demonstrate the truth of an assertion. Giving or procuring evidence is the process of using those things that are either presumed to be true, or were themselves proven via evidence, to demonstrate an assertion's truth...
. Such data generally consist of signalling
Signalling (telecommunications)
In telecommunication, signaling has the following meanings:*the use of signals for controlling communications...
or network management
Network management
Network management refers to the activities, methods, procedures, and tools that pertain to the operation, administration, maintenance, and provisioning of networked systems....
information or, in fewer instances, the content of the communications. If the data are not obtained in real-time, the activity is referred to as access to retained data (RD).
There are many bases for this activity that include infrastructure protection and cybersecurity. In general, the operator of public network infrastructure can undertake LI activities for those purposes. Operators of private network infrastructures have an inherent right to maintain LI capabilities within their own networks unless otherwise prohibited.
One of the bases for LI is the interception of telecommunications by law enforcement agencies (LEAs), regulatory or administrative agencies, and intelligence services, in accordance with local law. Under some legal systems, implementations—particularly real-time access to content—may require due process and receiving proper authorization from competent authorities—an activity that was formerly known as "wiretapping" and has existed since the inception of electronic communications. The material below primarily treats this narrow segment of LI.
With the legacy public switched telephone network
Public switched telephone network
The public switched telephone network is the network of the world's public circuit-switched telephone networks. It consists of telephone lines, fiber optic cables, microwave transmission links, cellular networks, communications satellites, and undersea telephone cables, all inter-connected by...
(PSTN), wireless, and cable systems, lawful interception (LI) was generally performed by accessing the mechanical or digital switches supporting the targets' calls. The introduction of packet switched networks, softswitch technology, and server-based applications the past two decades fundamentally altered how LI is undertaken.
Technical description
Almost all countries have LI capability requirements and have implemented them using global LI requirements and standards developed by the European Telecommunications Standards Institute (ETSI), 3rd Generation Partnership Project (3GPP), or CableLabs organizations—for wireline/Internet, wireless, and cable systems, respectively. In the USA, the comparable requirements are enabled by the Communications Assistance for Law Enforcement Act (CALEA)Communications Assistance for Law Enforcement Act
The Communications Assistance for Law Enforcement Act is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton...
, with the specific capabilities promulgated jointly by the Federal Communications Commission and the Department of Justice.
To prevent investigations' being compromised, LI systems may be designed in a manner that hides the interception from the telecommunications operator concerned. This is a requirement in some jurisdictions.
To ensure systematic procedures for carrying out interception, while also lowering the costs of interception solutions, industry groups and government agencies worldwide have attempted to standardize the technical processes behind lawful interception. One organization, ETSI, has been a major driver in lawful interception standards not only for Europe, but worldwide.
This architecture attempts to define a systematic and extensible means by which network operators and law enforcement agents (LEAs) can interact, especially as networks grow in sophistication and scope of services. Note this architecture applies to not only “traditional” wireline and wireless voice calls, but to IP-based services such as Voice over IP
Voice over IP
Voice over Internet Protocol is a family of technologies, methodologies, communication protocols, and transmission techniques for the delivery of voice communications and multimedia sessions over Internet Protocol networks, such as the Internet...
, email, instant messaging, etc. The architecture is now applied worldwide (in some cases with slight variations in terminology), including in the United States in the context of CALEA
Communications Assistance for Law Enforcement Act
The Communications Assistance for Law Enforcement Act is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton...
conformance. Three stages are called for in the architecture:
- collection where target-related “call” data and content are extracted from the network
- mediation where the data is formatted to conform to specific standards
- delivery of the data and content to the law enforcement agency (LEA).
The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, including destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, duration, etc. Call content is namely the stream of data carrying the call. Included in the architecture is the lawful interception management function, which covers interception session set-up and tear down, scheduling, target identification, etc. Communications between the network operator and LEA are via the Handover Interfaces (designated HI). Communications data and content are typically delivered from the network operator to the LEA in an encrypted format over an IP-based VPN. The interception of traditional voice calls still often relies on the establishment of an ISDN channel that is set up at the time of the interception.
As stated above, the ETSI architecture is equally applicable to IP-based services where IRI (or CD) is dependent on parameters associated with the traffic from a given application to be intercepted. For example, in the case of email IRI would be similar to the header information on an email message (e.g., destination email address, source email address, time email was transmitted) as well as pertinent header information within the IP packets conveying the message (e.g., source IP address of email server originating the email message). Of course, more in-depth information would be obtained by the interception system so as to avoid the usual email address spoofing that often takes place (e.g., spoofing of source address). Voice-over-IP likewise has its own IRI, including data derived from Session Initiation Protocol (SIP) messages that are used to set up and tear down a VOIP call.
ETSI LI Technical Committee work today is primarily focussed on developing the new Retained Data Handover and Next Generation Network specifications, as well as perfecting the innovative TS102232 standards suite that apply to most contemporary network uses.
USA interception standards that help network operators and service providers conform to CALEA are mainly those specified by the Federal Communications Commission (which has both plenary legislative and review authority under CALEA) CableLabs
CableLabs
Founded in 1988 by cable television operating companies, Cable Television Laboratories, Inc. is a not-for-profit research and development consortium that has cable operators as its members. System operators from around the world are eligible to be members. Members dues are based on revenue...
, and the Alliance for Telecommunications Industry Solutions (ATIS)
Alliance for Telecommunications Industry Solutions
The Alliance for Telecommunications Industry Solutions is a standards organization that develops technical and operational standards for the telecommunication industry. ATIS is headquartered in Washington, D.C....
. ATIS's standards include new standards for broadband Internet access and VoIP services, as well as legacy J-STD-025B which updates the earlier J-STD-025A to include packetized voice and CDMA wireless interception. All of these standards have been challenged as "deficient" by the U.S. Dept of Justice pursuant to CALEA.
Generic global standards have also been developed by Cisco via the Internet Engineering Task Force (IETF)
Internet Engineering Task Force
The Internet Engineering Task Force develops and promotes Internet standards, cooperating closely with the W3C and ISO/IEC standards bodies and dealing in particular with standards of the TCP/IP and Internet protocol suite...
that provide a front-end means of supporting most LI real-time handover standards.
Laws
The principal global treaty-based legal instrument relating to LI (including retained data) is the Convention on CybercrimeConvention on Cybercrime
The Convention on Cybercrime, also known as the Budapest Convention on Cybercrime or just the Budapest Convention, is the first international treaty seeking to address Computer crime and Internet crimes by harmonizing national laws, improving investigative techniques and increasing cooperation...
(Budapest, 23 Nov 2001). The secretariat for the Convention is the Council of Europe. However, the treaty itself has signatories worldwide and provides a global scope.
Individual countries have different legal requirements relating to lawful interception. The Global Lawful Interception Industry Forum lists many of these, as does the Council of Europe secretariat. For example, in the United Kingdom the law is known as RIPA (Regulation of Investigatory Powers Act), in United States
United States
The United States of America is a federal constitutional republic comprising fifty states and a federal district...
there is an array of federal and state criminal law, in Commonwealth of Independent States
Commonwealth of Independent States
The Commonwealth of Independent States is a regional organization whose participating countries are former Soviet Republics, formed during the breakup of the Soviet Union....
countries as SORM
SORM
SORM is a technical system for search and surveillance in the internet...
.
Europe
In the European UnionEuropean Union
The European Union is an economic and political union of 27 independent member states which are located primarily in Europe. The EU traces its origins from the European Coal and Steel Community and the European Economic Community , formed by six countries in 1958...
, the European Council
European Council
The European Council is an institution of the European Union. It comprises the heads of state or government of the EU member states, along with the President of the European Commission and the President of the European Council, currently Herman Van Rompuy...
Resolution of 17 January 1995 on the Lawful Interception of Telecommunications (Official Journal C 329) mandated similar measures to CALEA on a pan-European basis. Although some EU member countries reluctantly accepted this resolution out of privacy concerns (which are more pronounced in Europe than the US), there appears now to be general agreement with the resolution. Interestingly enough, interception mandates in Europe are generally more rigorous than those of the US; for example, both voice and ISP public network operators in the Netherlands
Netherlands
The Netherlands is a constituent country of the Kingdom of the Netherlands, located mainly in North-West Europe and with several islands in the Caribbean. Mainland Netherlands borders the North Sea to the north and west, Belgium to the south, and Germany to the east, and shares maritime borders...
have been required to support interception capabilities for years. In addition, publicly available statistics indicate that the number of interceptions in Europe exceed by many hundreds of times those undertaken in the U.S.
Europe continues to maintain its global leadership role in this sector through the adoption by the European Parliament and Council in 2006 of the far reaching Data Retention Directive
Data Retention Directive
The Data Retention Directive, more formally "Directive 2006/24/EC of the European Parliament and of the Council of 15 March 2006 on the retention of data generated or processed in connection with the provision of publicly available electronic communications services or of public communications...
. The provisions of the Directive broadly to almost all public electronic communications and require the capture of most related information, including location, for every communication. The information must be stored for a period of at least six months up to two years and made available to law enforcement upon lawful request. The Directive has been widely emulated in other countries.
United States of America
In the United StatesUnited States
The United States of America is a federal constitutional republic comprising fifty states and a federal district...
, two Federal statutes apply to half of the lawful interception. The other half occur pursuant to local law. The 1968 Omnibus Crime Control and Safe Streets Act
Omnibus Crime Control and Safe Streets Act of 1968
The Omnibus Crime Control and Safe Streets Act of 1968 was legislation passed by the Congress of the United States that established the Law Enforcement Assistance Administration . Title III of the Act set rules for obtaining wiretap orders in the United States. It has been started shortly after...
, Title III pertains mainly to lawful interception criminal investigations. The second law, the 1978 Foreign Intelligence Surveillance Act, or FISA, as amended by the Patriot Act, governs wiretapping for intelligence purposes
Intelligence (information gathering)
Intelligence assessment is the development of forecasts of behaviour or recommended courses of action to the leadership of an organization, based on a wide range of available information sources both overt and covert. Assessments are developed in response to requirements declared by the leadership...
where the subject of the investigation must be a foreign (non-US) national or a person working as an agent on behalf of a foreign country. The Administrator of the U.S. Courts annual reports indicate that the cases are related to illegal drug distribution
Illegal drug trade
The illegal drug trade is a global black market, dedicated to cultivation, manufacture, distribution and sale of those substances which are subject to drug prohibition laws. Most jurisdictions prohibit trade, except under license, of many types of drugs by drug prohibition laws.A UN report said the...
, with cell phones as the dominant form of intercepted communication.
During the 1990s, as in most countries, to help law enforcement and the FBI more effectively carry out wiretap operations, especially in view of the emerging digital voice and wireless network
Wireless network
Wireless network refers to any type of computer network that is not connected by cables of any kind. It is a method by which homes, telecommunications networks and enterprise installations avoid the costly process of introducing cables into a building, or as a connection between various equipment...
s at the time, the US Congress passed CALEA
Communications Assistance for Law Enforcement Act
The Communications Assistance for Law Enforcement Act is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton...
in 1994 . This act provides the Federal statutory framework for network operator assistance to LEAs in providing evidence and tactical information. In 2005, CALEA was applied to public broadband networks
Broadband Networks
The ideal telecommunication network has the following characteristics: broadband, multi-media, multi-point, multi-rate and economical implementation for a diversity of services [1][2]. The Broadband Integrated Services Digital Network provides these characteristics in today's networks...
Internet access and Voice over IP
Voice over IP
Voice over Internet Protocol is a family of technologies, methodologies, communication protocols, and transmission techniques for the delivery of voice communications and multimedia sessions over Internet Protocol networks, such as the Internet...
services that are interconnected to the Public Switched Telephone Network
Public switched telephone network
The public switched telephone network is the network of the world's public circuit-switched telephone networks. It consists of telephone lines, fiber optic cables, microwave transmission links, cellular networks, communications satellites, and undersea telephone cables, all inter-connected by...
(PSTN).
Canada
Police ability to lawfully intercept private communications is governed by Part VI of the Criminal Code of Canada (Invasion Of Privacy).Elsewhere
Most countries worldwide maintain LI requirements similar to those Europe and the U.S., and have moved to the ETSI handover standards. The Convention on Cybercrime requires such capabilities.Illegal use
As with many law enforcement tools, LI systems may be subverted for illicit purposes. This occurred in Greece during the 2004 Olympics. The telephone operator – Vodafone GreeceVodafone Greece
Vodafone Greece is the Greek subsidiary of Vodafone. Its headquarters are in Halandri - one of the northern suburbs of Athens.Vodafone Greece was established in Greece in 1992 – under the trade name Panafon – with the participation of Vodafone Group Plc., France Telecom, Intracom and Data Bank, and...
– was fined US$1,000,000 in 2006 for failing to secure its systems against unlawful access.
See also
- Secrecy of correspondenceSecrecy of correspondenceThe secrecy of correspondence ) or literally translated as secrecy of letters, is a fundamental legal principle enshrined in the constitutions of several European countries. It guarantees that the content of sealed letters is never revealed and letters in transit are not opened by government...
- Telecommunications data retentionTelecommunications data retentionIn the field of telecommunications, data retention generally refers to the storage of call detail records of telephony and internet traffic and transaction data by governments and commercial organisations...
- Network Monitoring Interface CardNetwork Monitoring Interface CardA network monitoring interface card or NMIC is similar to a network card . However, unlike a standard network card, an NMIC is designed to passively listen on a network. At a functional level, an NMIC may differ from a NIC, in that the NMIC may not have a MAC Address, may lack the ability to...
- SS7 probeSS7 probeSS7 Probe is a physical device to obtain signalling and/or bearer information from a telecommunications network, such as the PSTN or a corporate telephone system. The probe passively monitors the E1/T1 or SDH/SONET bearers, and extracts the signalling information for onward presentation to a...
- SIGINTSIGINTSignals intelligence is intelligence-gathering by interception of signals, whether between people , whether involving electronic signals not directly used in communication , or combinations of the two...
- SurveillanceSurveillanceSurveillance is the monitoring of the behavior, activities, or other changing information, usually of people. It is sometimes done in a surreptitious manner...
External links
- Application of the US PATRIOT Act in wiretapping
- White Paper on Interception of IP Networks
- White Paper on Interception of 3G and 4G Wireless Networks
- 3GPP Lawful Interception requirements for GSM
- Guide to the one party consent exception to the rule against interception of private communications in Canada
- Global LI Industry Forum, an overview of laws and standards
- Lawfull Intercept of WiMAX Signals
- Airangel talk about Lawful Intercept and the impact on Hotels

