Enterprise Information Security Architecture
Encyclopedia
Enterprise information security architecture (EISA) is a part of enterprise architecture
focusing on information security throughout the enterprise.
technology, it relates more broadly to the security practice of business optimization in that it addresses business security architecture, performance management and security process architecture as well.
Enterprise information security architecture is becoming a common practice within the financial institutions around the globe
. The primary purpose of creating an enterprise information security architecture is to ensure that business strategy and IT security are aligned. As such, enterprise information security architecture allows traceability
from the business strategy down to the underlying technology.
 Enterprise information security architecture was first formally positioned by Gartner
Enterprise information security architecture was first formally positioned by Gartner
in their whitepaper called “Incorporating Security into the Enterprise Architecture Process”. This was published on 24 January 2006. Since this publication, security architecture has moved from being a silo based architecture to an enterprise focused solution that incorporates business, information
and technology
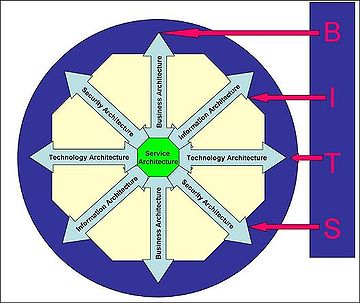
. The picture below represents a one-dimensional view of enterprise architecture as a service-oriented architecture. It also reflects the new addition to the enterprise architecture family called “Security”. Business architecture, information architecture and technology architecture use to be called BIT for short. Now with security as part of the architecture family it has become BITS.
Security architectural change imperatives now include things like
Given these descriptions, whose levels of detail will vary according to affordability and other practical considerations, decision makers are provided the means to make informed decisions about where to invest resources, where to realign organizational goals and processes, and what policies and procedures will support core missions or business functions.
A strong enterprise information security architecture process helps to answer basic questions like:
Implementing enterprise information security architecture generally starts with documenting the organization's strategy and other necessary details such as where and how it operates. The process then cascades down to documenting discrete core competencies, business processes, and how the organization interacts with itself and with external parties such as customers, suppliers, and government entities.
Having documented the organization's strategy and structure, the architecture process then flows down into the discrete information technology components such as:
Wherever possible, all of the above should be related explicitly to the organization's strategy, goals, and operations
. The enterprise information security architecture will document the current state of the technical security components listed above, as well as an ideal-world desired future state (Reference Architecture) and finally a "Target" future state which is the result of engineering tradeoffs and compromises vs. the ideal. Essentially the result is a nested and interrelated set of models, usually managed and maintained with specialised software available on the market.
Such exhaustive mapping of IT dependencies
has notable overlaps with both metadata
in the general IT sense, and with the ITIL
concept of the Configuration Management Database. Maintaining the accuracy of such data can be a significant challenge.
Along with the models and diagrams goes a set of best practices aimed at securing adaptability, scalability
, manageability etc. These systems engineering best practices are not unique to enterprise information security architecture but are essential to its success nonetheless. They involve such things as componentization, asynchronous communication
between major components, standardization
of key identifiers and so on.
Successful application of enterprise information security architecture requires appropriate positioning in the organization. The analogy of city-planning is often invoked in this connection, and is instructive.
An intermediate outcome of an architecture process is a comprehensive inventory of business security strategy, business security processes, organizational chart
s, technical security inventories, system and interface diagrams, and network topologies, and the explicit relationships between them. The inventories and diagrams are merely tools that support decision making. But this is not sufficient. It must be a living process.
The organization must design and implement a process that ensures continual movement from the current state to the future state. The future state will generally be a combination of one or more
 Enterprise information security architecture frameworks is only a subset of enterprise architecture frameworks. If we had to simplify the conceptual abstraction
Enterprise information security architecture frameworks is only a subset of enterprise architecture frameworks. If we had to simplify the conceptual abstraction
of enterprise information security architecture within a generic framework, the picture on the right would be acceptable as a high-level conceptual security architecture framework.
Other open enterprise architecture frameworks are:
technology governance process at any organization of significant size. More and more companies are implementing a formal enterprise security architecture process to support the governance
and management
of IT.
However, as noted in the opening paragraph of this article it ideally relates more broadly to the practice of business optimization in that it addresses business security architecture, performance management and process security architecture as well. Enterprise Information Security Architecture is also related to IT security portfolio management and metadata
in the enterprise IT sense.
Enterprise architecture
An enterprise architecture is a rigorous description of the structure of an enterprise, which comprises enterprise components , the externally visible properties of those components, and the relationships between them...
focusing on information security throughout the enterprise.
Overview
Enterprise information security architecture (EISA) is the practice of applying a comprehensive and rigorous method for describing a current and/or future structure and behavior for an organization's security processes, information security systems, personnel and organizational sub-units, so that they align with the organization's core goals and strategic direction. Although often associated strictly with information securityInformation security
Information security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction....
technology, it relates more broadly to the security practice of business optimization in that it addresses business security architecture, performance management and security process architecture as well.
Enterprise information security architecture is becoming a common practice within the financial institutions around the globe
Globe
A globe is a three-dimensional scale model of Earth or other spheroid celestial body such as a planet, star, or moon...
. The primary purpose of creating an enterprise information security architecture is to ensure that business strategy and IT security are aligned. As such, enterprise information security architecture allows traceability
Traceability
Traceability refers to the completeness of the information about every step in a process chain.The formal definition: Traceability is the ability to chronologically interrelate uniquely identifiable entities in a way that is verifiable....
from the business strategy down to the underlying technology.
Positioning

Gartner
Gartner, Inc. is an information technology research and advisory firm headquartered in Stamford, Connecticut, United States. It was known as GartnerGroup until 2001....
in their whitepaper called “Incorporating Security into the Enterprise Architecture Process”. This was published on 24 January 2006. Since this publication, security architecture has moved from being a silo based architecture to an enterprise focused solution that incorporates business, information
Information
Information in its most restricted technical sense is a message or collection of messages that consists of an ordered sequence of symbols, or it is the meaning that can be interpreted from such a message or collection of messages. Information can be recorded or transmitted. It can be recorded as...
and technology
Technology
Technology is the making, usage, and knowledge of tools, machines, techniques, crafts, systems or methods of organization in order to solve a problem or perform a specific function. It can also refer to the collection of such tools, machinery, and procedures. The word technology comes ;...
. The picture below represents a one-dimensional view of enterprise architecture as a service-oriented architecture. It also reflects the new addition to the enterprise architecture family called “Security”. Business architecture, information architecture and technology architecture use to be called BIT for short. Now with security as part of the architecture family it has become BITS.
Security architectural change imperatives now include things like
- Business roadmaps
- Legislative and legal requirements
- Technology roadmaps
- Industry trends
- Risk trends
- Visionaries
Goals
- Provide structure, coherence and cohesiveness.
- Must enable business-to-security alignment.
- Defined top-down beginning with business strategy.
- Ensure that all models and implementations can be traced back to the business strategy, specific business requirements and key principles.
- Provide abstraction so that complicating factors, such as geography and technology religion, can be removed and reinstated at different levels of detail only when required.
- Establish a common "language" for information security within the organization
Methodology
The practice of enterprise information security architecture involves developing an architecture security framework to describe a series of "current", "intermediate" and "target" reference architectures and applying them to align programs of change. These frameworks detail the organizations, roles, entities and relationships that exist or should exist to perform a set of business processes. This framework will provide a rigorous taxonomy and ontology that clearly identifies what processes a business performs and detailed information about how those processes are executed and secured. The end product is a set of artifacts that describe in varying degrees of detail exactly what and how a business operates and what security controls are required. These artifacts are often graphical.Given these descriptions, whose levels of detail will vary according to affordability and other practical considerations, decision makers are provided the means to make informed decisions about where to invest resources, where to realign organizational goals and processes, and what policies and procedures will support core missions or business functions.
A strong enterprise information security architecture process helps to answer basic questions like:
- What is the information security risk posture of the organization?
- Is the current architecture supporting and adding value to the security of the organization?
- How might a security architecture be modified so that it adds more value to the organization?
- Based on what we know about what the organization wants to accomplish in the future, will the current security architecture support or hinder that?
Implementing enterprise information security architecture generally starts with documenting the organization's strategy and other necessary details such as where and how it operates. The process then cascades down to documenting discrete core competencies, business processes, and how the organization interacts with itself and with external parties such as customers, suppliers, and government entities.
Having documented the organization's strategy and structure, the architecture process then flows down into the discrete information technology components such as:
- Organization charts, activities, and process flows of how the IT Organization operates
- Organization cycles, periods and timing
- Suppliers of technology hardware, software, and services
- Applications and software inventories and diagrams
- Interfaces between applications - that is: events, messages and data flows
- Intranet, Extranet, Internet, eCommerce, EDI links with parties within and outside of the organization
- Data classifications, Databases and supporting data models
- Hardware, platforms, hosting: servers, network components and security devices and where they are kept
- Local and wide area networks, Internet connectivity diagrams
Wherever possible, all of the above should be related explicitly to the organization's strategy, goals, and operations
Business operations
Business operations are those ongoing recurring activities involved in the running of a business for the purpose of producing value for the stakeholders...
. The enterprise information security architecture will document the current state of the technical security components listed above, as well as an ideal-world desired future state (Reference Architecture) and finally a "Target" future state which is the result of engineering tradeoffs and compromises vs. the ideal. Essentially the result is a nested and interrelated set of models, usually managed and maintained with specialised software available on the market.
Such exhaustive mapping of IT dependencies
Dependency (project management)
In a project network, a dependency is a link amongst a project's terminal elements.There are four kinds of dependencies with respect to ordering terminal elements :# Finish to start...
has notable overlaps with both metadata
Metadata
The term metadata is an ambiguous term which is used for two fundamentally different concepts . Although the expression "data about data" is often used, it does not apply to both in the same way. Structural metadata, the design and specification of data structures, cannot be about data, because at...
in the general IT sense, and with the ITIL
Itil
Itil may mean:*Atil or Itil, the ancient capital of Khazaria*Itil , also Idel, Atil, Atal, the ancient and modern Turkic name of the river Volga.ITIL can stand for:*Information Technology Infrastructure Library...
concept of the Configuration Management Database. Maintaining the accuracy of such data can be a significant challenge.
Along with the models and diagrams goes a set of best practices aimed at securing adaptability, scalability
Scalability
In electronics scalability is the ability of a system, network, or process, to handle growing amount of work in a graceful manner or its ability to be enlarged to accommodate that growth...
, manageability etc. These systems engineering best practices are not unique to enterprise information security architecture but are essential to its success nonetheless. They involve such things as componentization, asynchronous communication
Asynchronous communication
In telecommunications, asynchronous communication is transmission of data without the use of an external clock signal, where data can be transmitted intermittently rather than in a steady stream. Any timing required to recover data from the communication symbols is encoded within the symbols...
between major components, standardization
Standardization
Standardization is the process of developing and implementing technical standards.The goals of standardization can be to help with independence of single suppliers , compatibility, interoperability, safety, repeatability, or quality....
of key identifiers and so on.
Successful application of enterprise information security architecture requires appropriate positioning in the organization. The analogy of city-planning is often invoked in this connection, and is instructive.
An intermediate outcome of an architecture process is a comprehensive inventory of business security strategy, business security processes, organizational chart
Organizational chart
An organizational chart is a diagram that shows the structure of an organization and the relationships and relative ranks of its parts and positions/jobs...
s, technical security inventories, system and interface diagrams, and network topologies, and the explicit relationships between them. The inventories and diagrams are merely tools that support decision making. But this is not sufficient. It must be a living process.
The organization must design and implement a process that ensures continual movement from the current state to the future state. The future state will generally be a combination of one or more
- Closing gaps that are present between the current organization strategy and the ability of the IT security dimensions to support it
- Closing gaps that are present between the desired future organization strategy and the ability of the security dimensions to support it
- Necessary upgrades and replacements that must be made to the IT security architecture based on supplier viability, age and performance of hardware and software, capacity issues, known or anticipated regulatory requirements, and other issues not driven explicitly by the organization's functional management.
- On a regular basis, the current state and future state are redefined to account for evolution of the architecture, changes in organizational strategy, and purely external factors such as changes in technology and customer/vendor/government requirements, and changes to both internal and external threat landscapes over time.
High-level security architecture framework

Abstraction
Abstraction is a process by which higher concepts are derived from the usage and classification of literal concepts, first principles, or other methods....
of enterprise information security architecture within a generic framework, the picture on the right would be acceptable as a high-level conceptual security architecture framework.
Other open enterprise architecture frameworks are:
- The U.S. Department of Defense (DoD) Architecture Framework (DoDAF)
- Extended Enterprise Architecture Framework (E2AF) from the Institute For Enterprise Architecture Developments.
- Federal Enterprise ArchitectureFederal Enterprise ArchitectureA federal enterprise architecture is the enterprise architecture of a federal government. It provides a common methodology for information technology acquisition, use, and disposal in the Federal government....
of the United States Government (FEA) - Capgemini's Integrated Architecture Framework
- The UK Ministry of Defence (MOD) Architecture Framework (MODAF)MODAFThe British Ministry of Defence Architecture Framework is an Architecture Framework which defines a standardised way of conducting Enterprise Architecture, originally developed by the UK Ministry of Defence....
- NIH Enterprise Architecture Framework
- Open SecurityOpen SecurityOpen security is an initiative to approach application security challenges using open source philosophies and methodologies. Traditional application security is based on the premise that any application or service relies on security through obscurity.On the developer side, legitimate software and...
Architecture - Information Assurance Enterprise Architectural Framework (IAEAF)
- SABSA framework and methodology
- Service-Oriented ModelingService-oriented modelingService-oriented modeling is the discipline of modeling business and software systems, for the purpose of designing and specifying service-oriented business systems within a variety of architectural styles, such as enterprise architecture, application architecture, service-oriented architecture,...
Framework (SOMF) - The Open Group Architecture Framework (TOGAF)TOGAFThe Open Group Architecture Framework is a framework for enterprise architecture which provides a comprehensive approach for designing, planning, implementation, and governance of an enterprise information architecture...
- Zachman FrameworkZachman frameworkThe Zachman Framework is an Enterprise Architecture framework for enterprise architecture, which provides a formal and highly structured way of viewing and defining an enterprise...
Relationship to other IT disciplines
Enterprise information security architecture is a key component of the information securityInformation security
Information security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction....
technology governance process at any organization of significant size. More and more companies are implementing a formal enterprise security architecture process to support the governance
Governance
Governance is the act of governing. It relates to decisions that define expectations, grant power, or verify performance. It consists of either a separate process or part of management or leadership processes...
and management
Management
Management in all business and organizational activities is the act of getting people together to accomplish desired goals and objectives using available resources efficiently and effectively...
of IT.
However, as noted in the opening paragraph of this article it ideally relates more broadly to the practice of business optimization in that it addresses business security architecture, performance management and process security architecture as well. Enterprise Information Security Architecture is also related to IT security portfolio management and metadata
Metadata
The term metadata is an ambiguous term which is used for two fundamentally different concepts . Although the expression "data about data" is often used, it does not apply to both in the same way. Structural metadata, the design and specification of data structures, cannot be about data, because at...
in the enterprise IT sense.
See also
- Enterprise architectureEnterprise architectureAn enterprise architecture is a rigorous description of the structure of an enterprise, which comprises enterprise components , the externally visible properties of those components, and the relationships between them...
- Enterprise architecture planningEnterprise Architecture PlanningEnterprise Architecture Planning in Enterprise Architecture is the planning process of defining architectures for the use of information in support of the business and the plan for implementing those architectures.- Overview :...
- Information securityInformation securityInformation security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction....
- Information assuranceInformation AssuranceInformation assurance is the practice of managing risks related to the use, processing, storage, and transmission of information or data and the systems and processes used for those purposes...
Further reading
- Carbone, J. A. (2004). IT architecture toolkit. Enterprise computing series. Upper Saddle River, NJ, Prentice Hall PTR.
- Cook, M. A. (1996). Building enterprise information architectures : reengineering information systems. Hewlett-Packard professional books. Upper Saddle River, NJ, Prentice Hall.
- Fowler, M. (2003). Patterns of enterprise application architecture. The Addison-Wesley signature series. Boston, Addison-Wesley.
- Togaf Guide to Security Architecture "http://www.opengroup.org/pubs/catalog/w055.htm"
- Groot, R., M. Smits and H. Kuipers (2005). "A Method to Redesign the IS Portfolios in Large Organisations", Proceedings of the 38th Annual Hawaii International Conference on System Sciences (HICSS'05). Track 8, p. 223a. IEEE.
- Steven SpewakSteven SpewakSteven H. Spewak was an American management consultant, author, and lecturer on enterprise architectures, who influenced the direction of enterprise architecture thinking, especially in government.- Biography :...
and S. C. Hill (1993). Enterprise architecture planning : developing a blueprint for data, applications, and technology. Boston, QED Pub. Group.

