
YAK (cryptography)
Encyclopedia
The YAK is a public-key authenticated key agreement protocol. It is considered the simplest among the related protocols, including MQV
, HMQV, Station-to-Station protocol
, SSL/ TLS
etc. The authentication is based on public key pairs. As with other protocols, YAK normally requires a Public Key Infrastructure
to distribute authentic public keys to the communicating parties. The author suggests that YAK may be unencumbered by patent.
 with generator
with generator 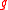 of prime order
of prime order 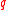 in
in
which the discrete log problem is hard. Typically a Schnorr group is used. In general, YAK can use any prime order group
that is suitable for public key cryptography, including Elliptic curve cryptography
. Let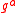 be Alice's long-term public key and
be Alice's long-term public key and 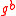 be Bob's. The protocol executes in one round.
be Bob's. The protocol executes in one round.
One round: Alice selects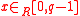 and sends out
and sends out 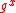 together with a Zero-knowledge proof
together with a Zero-knowledge proof
(using for example Schnorr signature
) for the proof of the exponent . Similarly, Bob selects
. Similarly, Bob selects 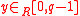 and sends out
and sends out 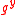 together with a Zero-knowledge proof
together with a Zero-knowledge proof
for the proof of the exponent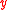 .
.
The above communication can be completed in one round as neither party depends on the other. When it finishes, Alice and Bob verify the received Zero-knowledge proofs. Alice then computes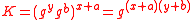 . Similarly, Bob computes
. Similarly, Bob computes 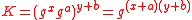 . With the same keying material
. With the same keying material  , Alice and Bob can derive a session key using a Cryptographic hash function
, Alice and Bob can derive a session key using a Cryptographic hash function
: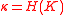 .
.
primitive is secure, the YAK protocol is proved to fulfill the following properties.
MQV
MQV is an authenticated protocol for key agreement based on the Diffie–Hellman scheme. Like other authenticated Diffie-Hellman schemes, MQV provides protection against an active attacker...
, HMQV, Station-to-Station protocol
Station-to-Station protocol
The Station-to-Station protocol is a cryptographic key agreement scheme based on classic Diffie-Hellman that provides mutual key and entity authentication....
, SSL/ TLS
Transport Layer Security
Transport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
etc. The authentication is based on public key pairs. As with other protocols, YAK normally requires a Public Key Infrastructure
Public key infrastructure
Public Key Infrastructure is a set of hardware, software, people, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates. In cryptography, a PKI is an arrangement that binds public keys with respective user identities by means of a certificate...
to distribute authentic public keys to the communicating parties. The author suggests that YAK may be unencumbered by patent.
Description
Two parties, Alice and Bob, agree on a group with generator
with generator 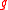 of prime order
of prime order 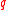 in
inwhich the discrete log problem is hard. Typically a Schnorr group is used. In general, YAK can use any prime order group
that is suitable for public key cryptography, including Elliptic curve cryptography
Elliptic curve cryptography
Elliptic curve cryptography is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. The use of elliptic curves in cryptography was suggested independently by Neal Koblitz and Victor S...
. Let
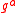 be Alice's long-term public key and
be Alice's long-term public key and 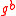 be Bob's. The protocol executes in one round.
be Bob's. The protocol executes in one round.One round: Alice selects
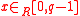 and sends out
and sends out 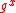 together with a Zero-knowledge proof
together with a Zero-knowledge proofZero-knowledge proof
In cryptography, a zero-knowledge proof or zero-knowledge protocol is an interactive method for one party to prove to another that a statement is true, without revealing anything other than the veracity of the statement....
(using for example Schnorr signature
Schnorr signature
In cryptography, a Schnorr signature is a digital signature produced by the Schnorr signature algorithm. Its security is based on the intractability of certain discrete logarithm problems. It is considered the simplest digital signature scheme to be provably secure in a random oracle model . It is...
) for the proof of the exponent
 . Similarly, Bob selects
. Similarly, Bob selects 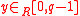 and sends out
and sends out 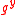 together with a Zero-knowledge proof
together with a Zero-knowledge proofZero-knowledge proof
In cryptography, a zero-knowledge proof or zero-knowledge protocol is an interactive method for one party to prove to another that a statement is true, without revealing anything other than the veracity of the statement....
for the proof of the exponent
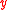 .
.The above communication can be completed in one round as neither party depends on the other. When it finishes, Alice and Bob verify the received Zero-knowledge proofs. Alice then computes
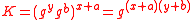 . Similarly, Bob computes
. Similarly, Bob computes 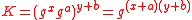 . With the same keying material
. With the same keying material  , Alice and Bob can derive a session key using a Cryptographic hash function
, Alice and Bob can derive a session key using a Cryptographic hash functionCryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
:
 .
.Security properties
Given that the underlying zero knowledge proofNon-interactive zero-knowledge proof
Non-interactive zero-knowledge proofs are a variant of zero-knowledge proofs. Blum, Feldman, and Micali showed that a common reference string shared between the prover and the verifier is enough to achieve computational zero-knowledge without requiring interaction. Goldreich and Oren gave...
primitive is secure, the YAK protocol is proved to fulfill the following properties.
- Private key security - An attacker cannot learn the user's static private key even if he is able to learn all session specific secrets in any compromised session.
- Full forward secrecy - Session keys that were securely established in the past uncorrupted sessions will remain incomputable in the future even when both users' static private keys are disclosed.
- Session key security - An attacker cannot compute the session key if he impersonates a user but has no access to the user's private key.

