
Trifid cipher
Encyclopedia
In classical cryptography
, the trifid cipher is a cipher invented around 1901 by Felix Delastelle
, which extends the concept of the bifid cipher
to a third dimension, allowing each symbol to be fractionated into 3 elements instead of two. That is, while the bifid uses the Polybius square
to turn each symbol into coordinates on a 5 × 5 (or 6 × 6) square, the trifid turns them into coordinates on a 3 × 3 × 3 cube. As with the bifid, this is then combined with transposition
to achieve diffusion
. However a higher degree of diffusion is achieved because each output symbol depends on 3 input symbols instead of two. Thus the trifid was the first practical trigraphic substitution.
cubic analogue of the Polybius square is drawn up:
In theory, the message is then converted to its coordinate
s in this grid; in practice, it is more convenient to write the triplets of trits out in a table, like so:
Then the coordinates are written out vertically beneath the message:
T R E A T Y E N D S B O E R W A R .
2 1 3 3 2 1 3 3 2 1 1 1 3 1 2 3 1 3
3 1 1 3 3 1 1 1 2 3 2 3 1 1 2 3 1 1
3 2 1 2 3 3 1 2 2 3 3 1 1 2 3 2 2 3
They are then read out in rows:
2 1 3 3 2 1 3 3 2 1 1 1 3 1 2 3 1 3 3 1 1 3 3 1 1 1 2 3 2 3 1 1 2 3 1 1 3 2 1 2 3 3 1 2 2 3 3 1 1 2 3 2 2 3
Then divided up into triplets again, and the triplets turned back into letters using the table:
213 321 332 111 312 313 311 331 112 323 112 311 321 233 122 331 123 223
M U A F N . E Q R K R E U T X Q B W
In this way, each ciphertext
character depends on three plaintext
characters, so the trifid is a trigraphic cipher. To decrypt, the procedure is simply reversed.
Since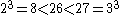 , our cube needs to have a side length of at least three in order to fit in the 26 letters of the alphabet. But if we go even to 4, then our symbol set would have
, our cube needs to have a side length of at least three in order to fit in the 26 letters of the alphabet. But if we go even to 4, then our symbol set would have 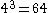 symbols, which is probably too much for classical cryptography. Thus, the trifid is only ever implemented with a 3 × 3 × 3 cube, and each coordinate is indicated by a trinary digit
symbols, which is probably too much for classical cryptography. Thus, the trifid is only ever implemented with a 3 × 3 × 3 cube, and each coordinate is indicated by a trinary digit
, or trit. Incidentally, note that since this gives us 27 symbols, we will have one extra. In the example above, the period or full-stop was used.
If we increase the dimensions further to four, noting that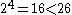 , we still need a side length of 3 - giving a symbol set of size
, we still need a side length of 3 - giving a symbol set of size 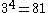 , far more than we need. If we go one step further, to five dimensions, then we only need a side length of 2, since
, far more than we need. If we go one step further, to five dimensions, then we only need a side length of 2, since 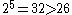 . But such a binary
. But such a binary
encoding - 5 bit
s - is what occurs in Baudot code
for telegraphic purposes. Breaking letters into bits and manipulating the bits individually is the hallmark of modern cryptography. Thus, in a sense, the trifid cipher can be thought to stand on the border between classical cryptography's ancient Polybius square
, and the binary manipulations of the modern world.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, the trifid cipher is a cipher invented around 1901 by Felix Delastelle
Felix Delastelle
Félix Marie Delastelle was a Frenchman most famous for his invention of several systems of polygraphic substitution ciphers including the bifid, trifid, and the four-square ciphers....
, which extends the concept of the bifid cipher
Bifid cipher
In classical cryptography, the bifid cipher is a cipher which combines the Polybius square with transposition, and uses fractionation to achieve diffusion...
to a third dimension, allowing each symbol to be fractionated into 3 elements instead of two. That is, while the bifid uses the Polybius square
Polybius square
In cryptography, the Polybius square, also known as the Polybius checkerboard, is a device invented by the Ancient Greek historian and scholar Polybius, described in , for fractionating plaintext characters so that they can be represented by a smaller set of symbols.-Basic form :The original square...
to turn each symbol into coordinates on a 5 × 5 (or 6 × 6) square, the trifid turns them into coordinates on a 3 × 3 × 3 cube. As with the bifid, this is then combined with transposition
Transposition cipher
In cryptography, a transposition cipher is a method of encryption by which the positions held by units of plaintext are shifted according to a regular system, so that the ciphertext constitutes a permutation of the plaintext. That is, the order of the units is changed...
to achieve diffusion
Confusion and diffusion
In cryptography, confusion and diffusion are two properties of the operation of a secure cipher which were identified by Claude Shannon in his paper Communication Theory of Secrecy Systems, published in 1949....
. However a higher degree of diffusion is achieved because each output symbol depends on 3 input symbols instead of two. Thus the trifid was the first practical trigraphic substitution.
Operation
First, a mixed alphabetSubstitution cipher
In cryptography, a substitution cipher is a method of encryption by which units of plaintext are replaced with ciphertext according to a regular system; the "units" may be single letters , pairs of letters, triplets of letters, mixtures of the above, and so forth...
cubic analogue of the Polybius square is drawn up:
| Layer 1 | Layer 2 | Layer 3 | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 1 | 2 | 3 | 1 | 2 | 3 | |||||
| 1 | F | J | O | 1 | V | Z | L | 1 | E | U | Q | ||
| 2 | R | X | C | 2 | G | D | P | 2 | N | H | A | ||
| 3 | Y | B | S | 3 | M | W | T | 3 | . | K | I |
In theory, the message is then converted to its coordinate
Cartesian coordinate system
A Cartesian coordinate system specifies each point uniquely in a plane by a pair of numerical coordinates, which are the signed distances from the point to two fixed perpendicular directed lines, measured in the same unit of length...
s in this grid; in practice, it is more convenient to write the triplets of trits out in a table, like so:
| F 111 | C 132 | W 223 | U 321 |
| R 112 | S 133 | L 231 | H 322 |
| Y 113 | V 211 | P 232 | K 323 |
| J 121 | G 212 | T 233 | Q 331 |
| X 122 | M 213 | E 311 | A 332 |
| B 123 | Z 221 | N 312 | I 333 |
| O 131 | D 222 | . 313 |
Then the coordinates are written out vertically beneath the message:
T R E A T Y E N D S B O E R W A R .
2 1 3 3 2 1 3 3 2 1 1 1 3 1 2 3 1 3
3 1 1 3 3 1 1 1 2 3 2 3 1 1 2 3 1 1
3 2 1 2 3 3 1 2 2 3 3 1 1 2 3 2 2 3
They are then read out in rows:
2 1 3 3 2 1 3 3 2 1 1 1 3 1 2 3 1 3 3 1 1 3 3 1 1 1 2 3 2 3 1 1 2 3 1 1 3 2 1 2 3 3 1 2 2 3 3 1 1 2 3 2 2 3
Then divided up into triplets again, and the triplets turned back into letters using the table:
213 321 332 111 312 313 311 331 112 323 112 311 321 233 122 331 123 223
M U A F N . E Q R K R E U T X Q B W
In this way, each ciphertext
Ciphertext
In cryptography, ciphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher...
character depends on three plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
characters, so the trifid is a trigraphic cipher. To decrypt, the procedure is simply reversed.
Dimensions
As the bifid concept is extended to higher dimensions, we are much less free in our choice of parameters.Since
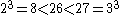 , our cube needs to have a side length of at least three in order to fit in the 26 letters of the alphabet. But if we go even to 4, then our symbol set would have
, our cube needs to have a side length of at least three in order to fit in the 26 letters of the alphabet. But if we go even to 4, then our symbol set would have 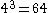 symbols, which is probably too much for classical cryptography. Thus, the trifid is only ever implemented with a 3 × 3 × 3 cube, and each coordinate is indicated by a trinary digit
symbols, which is probably too much for classical cryptography. Thus, the trifid is only ever implemented with a 3 × 3 × 3 cube, and each coordinate is indicated by a trinary digitTernary
Ternary is an adjective meaning "composed of three items". It can refer to:* Ternary complex, a complex formed by the interaction of three molecules* Ternary compound, a type of chemical compound...
, or trit. Incidentally, note that since this gives us 27 symbols, we will have one extra. In the example above, the period or full-stop was used.
If we increase the dimensions further to four, noting that
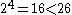 , we still need a side length of 3 - giving a symbol set of size
, we still need a side length of 3 - giving a symbol set of size 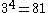 , far more than we need. If we go one step further, to five dimensions, then we only need a side length of 2, since
, far more than we need. If we go one step further, to five dimensions, then we only need a side length of 2, since 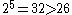 . But such a binary
. But such a binaryBinary numeral system
The binary numeral system, or base-2 number system, represents numeric values using two symbols, 0 and 1. More specifically, the usual base-2 system is a positional notation with a radix of 2...
encoding - 5 bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
s - is what occurs in Baudot code
Baudot code
The Baudot code, invented by Émile Baudot, is a character set predating EBCDIC and ASCII. It was the predecessor to the International Telegraph Alphabet No 2 , the teleprinter code in use until the advent of ASCII. Each character in the alphabet is represented by a series of bits, sent over a...
for telegraphic purposes. Breaking letters into bits and manipulating the bits individually is the hallmark of modern cryptography. Thus, in a sense, the trifid cipher can be thought to stand on the border between classical cryptography's ancient Polybius square
Polybius square
In cryptography, the Polybius square, also known as the Polybius checkerboard, is a device invented by the Ancient Greek historian and scholar Polybius, described in , for fractionating plaintext characters so that they can be represented by a smaller set of symbols.-Basic form :The original square...
, and the binary manipulations of the modern world.
See also
Other ciphers by Delastelle:- Four-square cipherFour-square cipherThe four-square cipher is a manual symmetric encryption technique. It was invented by famous French cryptographer Felix Delastelle.The technique encrypts pairs of letters , and thus falls into a category of ciphers known as polygraphic substitution ciphers...
(related to PlayfairPlayfair cipherThe Playfair cipher or Playfair square is a manual symmetric encryption technique and was the first literal digraph substitution cipher. The scheme was invented in 1854 by Charles Wheatstone, but bears the name of Lord Playfair who promoted the use of the cipher.The technique encrypts pairs of...
) - Bifid cipherBifid cipherIn classical cryptography, the bifid cipher is a cipher which combines the Polybius square with transposition, and uses fractionation to achieve diffusion...
(similar to trifid)

