
Threefish
Encyclopedia
Threefish is a tweakable block cipher designed as part of the Skein hash function, an entry in the NIST hash function competition
. Threefish uses no S-boxes or other table lookups in order to avoid cache timing attack
s; its nonlinearity comes from alternating additions with exclusive ORs. In that respect, it's similar to Salsa20
, TEA
, and the SHA-3 candidates CubeHash
and BLAKE
.
Threefish and the Skein hash function were designed by Bruce Schneier
, Niels Ferguson
, Stefan Lucks
, Doug Whiting, Mihir Bellare
, Tadayoshi Kohno, Jon Callas
, and Jesse Walker.
with the rebound attack was published. The attack mounts a known-key distinguisher against 53 of 72 rounds in Threefish-256, and 57 of 72 rounds in Threefish-512. It also affects the Skein
hash function. This is a follow-up to the earlier attack published in February, which breaks 39 and 42 rounds respectively. In response to this attack, the Skein team tweaked the rotation constants used in Threefish and thereby the key schedule
constants for round 3 of the NIST hash function competition.
In 2009, a related key boomerang attack
against a reduced round Threefish version was published. For the 32-round version, the time complexity is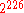 and the memory complexity is
and the memory complexity is  ; for the 33-round version, the time complexity is
; for the 33-round version, the time complexity is  with a negligible memory usage. The attacks also work against the tweaked version of Threefish: for the 32-round version, the time complexity is
with a negligible memory usage. The attacks also work against the tweaked version of Threefish: for the 32-round version, the time complexity is  and the memory complexity is
and the memory complexity is  ; for the 33-round version, the time complexity is
; for the 33-round version, the time complexity is  with a negligible memory usage.
with a negligible memory usage.
NIST hash function competition
The NIST hash function competition is an open competition held by the US National Institute of Standards and Technology for a new SHA-3 function to replace the older SHA-1 and SHA-2, which was formally announced in the Federal Register on November 2, 2007...
. Threefish uses no S-boxes or other table lookups in order to avoid cache timing attack
Timing attack
In cryptography, a timing attack is a side channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute cryptographic algorithms...
s; its nonlinearity comes from alternating additions with exclusive ORs. In that respect, it's similar to Salsa20
Salsa20
Salsa20 is a stream cipher submitted to eSTREAM by Daniel Bernstein. It is built on a pseudorandom function based on 32-bit addition, bitwise addition and rotation operations, which maps a 256-bit key, a 64-bit nonce , and a 64-bit stream position to a 512-bit output...
, TEA
Tiny Encryption Algorithm
In cryptography, the Tiny Encryption Algorithm is a block cipher notable for its simplicity of description and implementation, typically a few lines of code...
, and the SHA-3 candidates CubeHash
CubeHash
CubeHash is a cryptographic hash function submitted to the NIST hash function competition by Daniel J. Bernstein. Message blocks are XORed into the initial bits of a 128-byte state, which goes through an r-round bijective transformation between blocks. The initial NIST proposal required about...
and BLAKE
BLAKE (hash function)
BLAKE is a cryptographic hash function submitted to the NIST hash function competition by Jean-Philippe Aumasson, Luca Henzen, Willi Meier, and Raphael C.-W. Phan. It is based on Dan Bernstein's ChaCha stream cipher, but a permuted copy of the input block, XORed with some round constants, is added...
.
Threefish and the Skein hash function were designed by Bruce Schneier
Bruce Schneier
Bruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
, Niels Ferguson
Niels Ferguson
Niels T. Ferguson is a Dutch cryptographer and consultant who currently works for Microsoft. He has worked with others, including Bruce Schneier, designing cryptographic algorithms, testing algorithms and protocols, and writing papers and books...
, Stefan Lucks
Stefan Lucks
Stefan Lucks is a researcher in the fields of communications security and cryptography. Lucks is known for his attack on Triple DES, and for extending Lars Knudsen's Square attack to Twofish, a cipher outside the Square family, thus generalising the attack into integral cryptanalysis...
, Doug Whiting, Mihir Bellare
Mihir Bellare
Mihir Bellare is a cryptographer and professor at the University of California, San Diego. He has published several seminal papers in the field of cryptography , many coauthored with Phillip Rogaway. Bellare has published a number of papers in the field of Format-Preserving Encryption...
, Tadayoshi Kohno, Jon Callas
Jon Callas
Jon Callas is an American computer security expert and Chief Technical Officer of Entrust. Callas has a long history of work in the computer security field, and is a frequent speaker at industry conferences. Additionally, Callas is a contributor to multiple IETF RFCs...
, and Jesse Walker.
Security
In October 2010, an attack that combines rotational cryptanalysisRotational cryptanalysis
In cryptography, rotational cryptanalysis is a generic cryptanalytic attack against algorithms that rely on three operations: modular addition, rotation and XOR — ARX for short...
with the rebound attack was published. The attack mounts a known-key distinguisher against 53 of 72 rounds in Threefish-256, and 57 of 72 rounds in Threefish-512. It also affects the Skein
Skein (hash function)
Skein is a cryptographic hash function and one out of five finalists in the NIST hash function competition to design what will become the SHA-3 standard, the intended successor of SHA-1 and SHA-2...
hash function. This is a follow-up to the earlier attack published in February, which breaks 39 and 42 rounds respectively. In response to this attack, the Skein team tweaked the rotation constants used in Threefish and thereby the key schedule
Key schedule
[[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES [[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES [[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES ("[[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES ("...
constants for round 3 of the NIST hash function competition.
In 2009, a related key boomerang attack
Boomerang attack
In cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David Wagner, who used it to break the COCONUT98 cipher....
against a reduced round Threefish version was published. For the 32-round version, the time complexity is
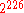 and the memory complexity is
and the memory complexity is  ; for the 33-round version, the time complexity is
; for the 33-round version, the time complexity is  with a negligible memory usage. The attacks also work against the tweaked version of Threefish: for the 32-round version, the time complexity is
with a negligible memory usage. The attacks also work against the tweaked version of Threefish: for the 32-round version, the time complexity is  and the memory complexity is
and the memory complexity is  ; for the 33-round version, the time complexity is
; for the 33-round version, the time complexity is  with a negligible memory usage.
with a negligible memory usage.External links
- "Homepage" Homepage of the Skein Hash Function Family.

