.gif)
Ring (computer security)
Encyclopedia
Computer science
Computer science or computing science is the study of the theoretical foundations of information and computation and of practical techniques for their implementation and application in computer systems...
, hierarchical protection domains, often called protection rings, are a mechanism to protect data and functionality from faults (fault tolerance) and malicious behaviour (computer security
Computer security
Computer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
). This approach is diametrically opposite to that of capability-based security
Capability-based security
Capability-based security is a concept in the design of secure computing systems, one of the existing security models. A capability is a communicable, unforgeable token of authority. It refers to a value that references an object along with an associated set of access rights...
.
Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical levels or layers of privilege within the architecture of a computer system. This is generally hardware-enforced by some CPU
Central processing unit
The central processing unit is the portion of a computer system that carries out the instructions of a computer program, to perform the basic arithmetical, logical, and input/output operations of the system. The CPU plays a role somewhat analogous to the brain in the computer. The term has been in...
architecture
Computer architecture
In computer science and engineering, computer architecture is the practical art of selecting and interconnecting hardware components to create computers that meet functional, performance and cost goals and the formal modelling of those systems....
s that provide different CPU modes
CPU modes
CPU modes are operating modes for the central processing unit of some computer architectures that place restrictions on the type and scope of operations that can be performed by certain processes being run by the CPU...
at the hardware or microcode
Microcode
Microcode is a layer of hardware-level instructions and/or data structures involved in the implementation of higher level machine code instructions in many computers and other processors; it resides in special high-speed memory and translates machine instructions into sequences of detailed...
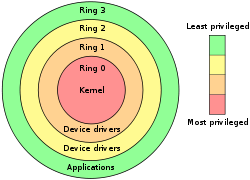
level. Rings are arranged in a hierarchy from most privileged (most trusted, usually numbered zero) to least privileged (least trusted, usually with the highest ring number). On most operating systems, Ring 0 is the level with the most privileges and interacts most directly with the physical hardware such as the CPU and memory.
Special gates between rings are provided to allow an outer ring to access an inner ring's resources in a predefined manner, as opposed to allowing arbitrary usage. Correctly gating access between rings can improve security by preventing programs from one ring or privilege level from misusing resources intended for programs in another. For example, spyware
Spyware
Spyware is a type of malware that can be installed on computers, and which collects small pieces of information about users without their knowledge. The presence of spyware is typically hidden from the user, and can be difficult to detect. Typically, spyware is secretly installed on the user's...
running as a user program in Ring 3 should be prevented from turning on a web camera without informing the user, since hardware access should be a Ring 1 function reserved for device drivers
Device driver
In computing, a device driver or software driver is a computer program allowing higher-level computer programs to interact with a hardware device....
. Programs such as web browsers running in higher numbered rings must request access to the network, a resource restricted to a lower numbered ring.
Implementations
Hardware supported rings were among the most revolutionary concepts introduced by the MulticsMultics
Multics was an influential early time-sharing operating system. The project was started in 1964 in Cambridge, Massachusetts...
operating system, a highly secure predecessor of today's UNIX
Unix
Unix is a multitasking, multi-user computer operating system originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Brian Kernighan, Douglas McIlroy, and Joe Ossanna...
family of operating systems. However, most general-purpose systems use only two rings, even if the hardware they run on provides more CPU modes
CPU modes
CPU modes are operating modes for the central processing unit of some computer architectures that place restrictions on the type and scope of operations that can be performed by certain processes being run by the CPU...
than that. For example, Windows XP and below only uses two rings, with ring 0 corresponding to kernel mode and ring 3 to user mode.
Many modern CPU architectures (including the popular Intel x86 architecture) include some form of ring protection, although the Windows NT
Windows NT
Windows NT is a family of operating systems produced by Microsoft, the first version of which was released in July 1993. It was a powerful high-level-language-based, processor-independent, multiprocessing, multiuser operating system with features comparable to Unix. It was intended to complement...
operating system, like Unix, does not fully exploit this feature. OS/2
OS/2
OS/2 is a computer operating system, initially created by Microsoft and IBM, then later developed by IBM exclusively. The name stands for "Operating System/2," because it was introduced as part of the same generation change release as IBM's "Personal System/2 " line of second-generation personal...
did to some extent, as it used three rings: ring 0 for kernel code and device drivers, ring 2 for privileged code (user programs with I/O access permissions), and ring 3 for unprivileged code (nearly all user programs). Under DOS
DOS
DOS, short for "Disk Operating System", is an acronym for several closely related operating systems that dominated the IBM PC compatible market between 1981 and 1995, or until about 2000 if one includes the partially DOS-based Microsoft Windows versions 95, 98, and Millennium Edition.Related...
, the kernel, drivers and applications typically run on ring 3, whereas 386 memory managers such as EMM386
EMM386
The name EMM386 was used for the expanded memory managers of both Microsoft's MS-DOS and Digital Research's DR-DOS, which created expanded memory using extended memory on Intel 80386 CPUs. There also is an EMM386.EXE available in FreeDOS....
run at ring 0. In addition to this, DR-DOS
DR-DOS
DR-DOS is an MS-DOS-compatible operating system for IBM PC-compatible personal computers, originally developed by Gary Kildall's Digital Research and derived from Concurrent PC DOS 6.0, which was an advanced successor of CP/M-86...
' EMM386 3.xx can optionally run some modules (such as DPMS
DOS Protected Mode Services
DOS Protected Mode Services is a set of extended DOS memory management services to allow DPMS-enabled DOS drivers to load and execute in extended memory and protected mode....
) on ring 1 instead. OpenVMS
OpenVMS
OpenVMS , previously known as VAX-11/VMS, VAX/VMS or VMS, is a computer server operating system that runs on VAX, Alpha and Itanium-based families of computers. Contrary to what its name suggests, OpenVMS is not open source software; however, the source listings are available for purchase...
uses four modes called (in order of decreasing privileges) Kernel, Executive, Supervisor and User.
There has been a renewed interest in this design structure, with the proliferation of the Xen
Xen
Xen is a virtual-machine monitor providing services that allow multiple computer operating systems to execute on the same computer hardware concurrently....
VMM software, ongoing discussion
Tanenbaum-Torvalds debate
The Tanenbaum–Torvalds debate is a debate between Andrew S. Tanenbaum and Linus Torvalds, regarding Linux and kernel architecture in general. Tanenbaum began the debate in 1992 on the Usenet discussion group [news:///comp.os.minix comp.os.minix], arguing that microkernels are superior to...
on monolithic
Monolithic kernel
A monolithic kernel is an operating system architecture where the entire operating system is working in the kernel space and alone as supervisor mode...
- vs. micro-kernel
Microkernel
In computer science, a microkernel is the near-minimum amount of software that can provide the mechanisms needed to implement an operating system . These mechanisms include low-level address space management, thread management, and inter-process communication...
(particularly in Usenet
Usenet
Usenet is a worldwide distributed Internet discussion system. It developed from the general purpose UUCP architecture of the same name.Duke University graduate students Tom Truscott and Jim Ellis conceived the idea in 1979 and it was established in 1980...
newsgroups and Web forums), Microsoft's Ring-1 design structure as part of their NGSCB
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base , formerly known as Palladium, is a software architecture designed by Microsoft which is expected to implement parts of the controversial "Trusted Computing" concept on future versions of the Microsoft Windows operating system. NGSCB is part of...
initiative and hypervisor
Hypervisor
In computing, a hypervisor, also called virtual machine manager , is one of many hardware virtualization techniques that allow multiple operating systems, termed guests, to run concurrently on a host computer. It is so named because it is conceptually one level higher than a supervisory program...
s embedded in firmware
Firmware
In electronic systems and computing, firmware is a term often used to denote the fixed, usually rather small, programs and/or data structures that internally control various electronic devices...
such as Intel VT-x (formerly Vanderpool).
The original Multics system had eight rings, but many modern systems have fewer. The hardware is aware of the current ring of the executing instruction thread
Thread (computer science)
In computer science, a thread of execution is the smallest unit of processing that can be scheduled by an operating system. The implementation of threads and processes differs from one operating system to another, but in most cases, a thread is contained inside a process...
at all times, thanks to special machine registers. In some systems, areas of virtual memory are instead assigned ring numbers in hardware. One example is the Data General Eclipse MV/8000
Data General Eclipse MV/8000
The Eclipse MV/8000 was the first in a family of 32-bit minicomputers produced by Data General during the 1980s. Codenamed Eagle during development, its architecture was a new 32-bit design backward compatible with the previous 16-bit Eclipse series. The development of the computer and the people...
, in which the top three bits of the PC served as the ring register. Thus code executing with the virtual PC set to 0xE200000, for example, would automatically be in ring 7, and calling a subroutine in a different section of memory would automatically cause a ring transfer.
The hardware severely restricts the ways in which control can be passed from one ring to another, and also enforces restrictions on the types of memory access that can be performed across rings. Typically there is a special gate or call instruction that transfers control in a secure way towards predefined entry points in lower-level (more trusted) rings; this functions as a supervisor call in many operating systems that use the ring architecture. The hardware restrictions are designed to limit opportunities for accidental or malicious breaches of security. In addition, the most privileged ring may be given special capabilities, (such as real memory addressing that bypasses the virtual-memory
Virtual memory
In computing, virtual memory is a memory management technique developed for multitasking kernels. This technique virtualizes a computer architecture's various forms of computer data storage , allowing a program to be designed as though there is only one kind of memory, "virtual" memory, which...
hardware).
Ring protection can be combined with processor modes (master/kernel/privileged mode versus slave/user/unprivileged mode) in some systems. Operating systems running on hardware supporting both may use both forms of protection or only one.
Effective use of ring architecture requires close cooperation between hardware and the operating system. Operating systems designed to work on multiple hardware platforms may make only limited use of rings if they are not present on every supported platform. Often the security model is simplified to "kernel" and "user" even if hardware provides finer granularity through rings.
Supervisor mode
In computer terms supervisor mode is a hardware-mediated flag which can be changed by code running in system-level software. System-level tasks or threads will have this flag set while they are running, whereas user-space applications will not. This flag determines whether it would be possible to execute machine code operations such as modifying registers for various descriptor tables, or performing operations such as disabling interrupts. The idea of having two different modes to operate in comes from “with more control comes more responsibility” — a program in supervisor mode is trusted never to fail, since a failure may cause the whole computer system to crash.Supervisor mode is “An execution mode on some processors which enables execution of all instructions, including privileged instructions. It may also give access to a different address space, to memory management hardware and to other peripherals. This is the mode in which the operating system usually runs.”
In a monolithic kernel, the operating system runs in supervisor mode and the applications run in user mode. Other types of operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
s, like those with an exokernel
Exokernel
Exokernel is an operating system kernel developed by the MIT Parallel and Distributed Operating Systems group, and also a class of similar operating systems....
or microkernel
Microkernel
In computer science, a microkernel is the near-minimum amount of software that can provide the mechanisms needed to implement an operating system . These mechanisms include low-level address space management, thread management, and inter-process communication...
do not necessarily share this behavior.
Some examples from the PC world:
- LinuxLinux kernelThe Linux kernel is an operating system kernel used by the Linux family of Unix-like operating systems. It is one of the most prominent examples of free and open source software....
and WindowsMicrosoft WindowsMicrosoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
are two operating systems that use supervisor/user-mode. To perform specialized functions, user-mode code must perform a system callSystem callIn computing, a system call is how a program requests a service from an operating system's kernel. This may include hardware related services , creating and executing new processes, and communicating with integral kernel services...
into supervisor mode or even to the kernel space where trusted code of the operating system will perform the needed task and return it back to user space.
- DOSDOSDOS, short for "Disk Operating System", is an acronym for several closely related operating systems that dominated the IBM PC compatible market between 1981 and 1995, or until about 2000 if one includes the partially DOS-based Microsoft Windows versions 95, 98, and Millennium Edition.Related...
(for as long as no 386 memory manager such as EMM386EMM386The name EMM386 was used for the expanded memory managers of both Microsoft's MS-DOS and Digital Research's DR-DOS, which created expanded memory using extended memory on Intel 80386 CPUs. There also is an EMM386.EXE available in FreeDOS....
is loaded), as well as other simple operating systems, and many embedded devices run in supervisor mode permanently, meaning that drivers can be written directly as user programs.
Most processors have at least two different modes. The x86-processors have four different modes divided into four different rings. Programs that run in Ring 0 can do anything with the system, and code that runs in Ring 3 should be able to fail at any time without impact to the rest of the computer system. Ring 1 and Ring 2 are rarely used, but could be configured with different levels of access.
Switching from “user mode” to “kernel mode” is, in most existing systems, very expensive. It has been measured, on the basic request getpid, to cost 1000-1500 cycles on most machines. Of these just around 100 are for the actual switch (70 from user to kernel space, and 40 back), the rest is "kernel overhead". In the L3 microkernel
L3 microkernel
L3 is a microkernel running on Intel's x86 computers. L3 is designed to be "very lean and features fast, message-based, synchronous IPC, simple-to-use external paging mechanisms and a security mechanism based on secure domains ." It is the predecessor of L4, another microkernel with similar design...
the minimization of this overhead reduced the overall cost to around 150 cycles.
Maurice Wilkes wrote:
... it eventually became clear that the hierarchical protection that rings provided did not closely match the requirements of the system programmer and gave little or no improvement on the simple system of having two modes only. Rings of protection lent themselves to efficient implementation in hardware, but there was little else to be said for them. [...] The attractiveness of fine-grained protection remained, even after it was seen that rings of protection did not provide the answer... This again proved a blind alley...
To gain performance and determinism, some systems place functions that would likely be viewed as application logic, rather than as device drivers, in kernel mode; security applications (access control
Access control
Access control refers to exerting control over who can interact with a resource. Often but not always, this involves an authority, who does the controlling. The resource can be a given building, group of buildings, or computer-based information system...
, firewalls
Firewall (computing)
A firewall is a device or set of devices designed to permit or deny network transmissions based upon a set of rules and is frequently used to protect networks from unauthorized access while permitting legitimate communications to pass....
, etc.) and operating system monitors are cited as examples. At least one embedded database management system, eXtremeDB Kernel Mode, has been developed specifically for kernel mode deployment, to provide a local database for kernel-based application functions, and to eliminate the context switch
Context switch
A context switch is the computing process of storing and restoring the state of a CPU so that execution can be resumed from the same point at a later time. This enables multiple processes to share a single CPU. The context switch is an essential feature of a multitasking operating system...
es that would otherwise occur when kernel functions interact with a database system running in user mode.
Hypervisor mode
Recent CPUs from Intel and AMD offer x86 virtualizationX86 virtualization
In computing, x86 virtualization is the facility that allows multiple operating systems to simultaneously share x86 processor resources in a safe and efficient manner, a facility generically known as hardware virtualization...
instructions for a hypervisor
Hypervisor
In computing, a hypervisor, also called virtual machine manager , is one of many hardware virtualization techniques that allow multiple operating systems, termed guests, to run concurrently on a host computer. It is so named because it is conceptually one level higher than a supervisory program...
to control Ring 0 hardware access. Although they are mutually incompatible, both Intel VT-x (codenamed "Vanderpool") and AMD-V (codenamed "Pacifica") create a new "Ring -1" so that a guest operating system can run Ring 0 operations natively without affecting other guests or the host OS.
Interoperation between CPU and OS levels of abstraction
Many CPU hardware architectures provide far more flexibility than is exploited by the operating systemOperating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
s that they normally run. Proper use of complex CPU modes requires very close cooperation between the operating system and the CPU, and thus tends to tie the OS to the CPU architecture. When the OS and the CPU are specifically designed for each other, this is not a problem (although some hardware features may still be left unexploited), but when the OS is designed to be compatible with multiple, different CPU architectures, a large part of the CPU mode features may be ignored by the OS. For example, the reason Windows uses only two levels (ring 0 and ring 3) is that some hardware architectures that were supported in the past (such as PowerPC
PowerPC
PowerPC is a RISC architecture created by the 1991 Apple–IBM–Motorola alliance, known as AIM...
or MIPS
MIPS architecture
MIPS is a reduced instruction set computer instruction set architecture developed by MIPS Technologies . The early MIPS architectures were 32-bit, and later versions were 64-bit...
) implemented only two privilege levels.
Multics
Multics
Multics was an influential early time-sharing operating system. The project was started in 1964 in Cambridge, Massachusetts...
was an operating system designed specifically for a special CPU architecture (which in turn was designed specifically for Multics), and it took full advantage of the CPU modes available to it. However, it was an exception to the rule. Today, this high degree of interoperation between the OS and the hardware is not often cost-effective, despite the potential advantages for security and stability.
Ultimately, the purpose of distinct operating modes for the CPU is to provide hardware protection against accidental or deliberate corruption of the system environment (and corresponding breaches of system security) by software. Only "trusted" portions of system software are allowed to execute in the unrestricted environment of kernel mode, and only then when absolutely necessary. All other software executes in one or more user modes. If a processor generates a fault or exception condition in a user mode, in most cases system stability is unaffected; if a processor generates a fault or exception condition in kernel mode, most operating systems will halt the system with an unrecoverable error. When a hierarchy of modes exists (ring-base security), faults and exceptions at one privilege level may destabilize only the higher-numbered privilege levels. Thus, a fault in Ring 0 (the kernel mode with the highest privilege) will crash the entire system, but a fault in Ring 2 will only affect rings 3 and beyond and Ring 2 itself, at most.
Transitions between modes are at the discretion of the executing thread
Thread (computer science)
In computer science, a thread of execution is the smallest unit of processing that can be scheduled by an operating system. The implementation of threads and processes differs from one operating system to another, but in most cases, a thread is contained inside a process...
when the transition is from a level of high privilege to one of low privilege (as from kernel to user modes), but transitions from lower to higher levels of privilege can take place only through secure, hardware-controlled "gates" that are traversed by executing special instructions or when external interrupts are received.
Microkernel
Microkernel
In computer science, a microkernel is the near-minimum amount of software that can provide the mechanisms needed to implement an operating system . These mechanisms include low-level address space management, thread management, and inter-process communication...
operating systems attempt to minimize the amount of code running in privileged mode, for purposes of security
Computer security
Computer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
and elegance
Elegance
Elegance is a synonym for beauty that has come to acquire the additional connotations of unusual effectiveness and simplicity. It is frequently used as a standard of tastefulness particularly in the areas of visual design, decoration, the sciences, and the esthetics of mathematics...
, but ultimately sacrificing performance.
See also
- System callSystem callIn computing, a system call is how a program requests a service from an operating system's kernel. This may include hardware related services , creating and executing new processes, and communicating with integral kernel services...
- Protected modeProtected modeIn computing, protected mode, also called protected virtual address mode, is an operational mode of x86-compatible central processing units...
(x86-compatible CPUs of the 80286 series or later) - MulticsMulticsMultics was an influential early time-sharing operating system. The project was started in 1964 in Cambridge, Massachusetts...
Further reading
- David T. Rogers: A FRAMEWORK FOR DYNAMIC SUBVERSION Thesis, June 2003 (pdf)
- Glossary of MulticsMulticsMultics was an influential early time-sharing operating system. The project was started in 1964 in Cambridge, Massachusetts...
acronyms and terms: [ftp://ftp.stratus.com/vos/multics/tvv/mgr.html#ring Ring] - William J. Caelli: "Trusted Systems" in an Age of NIIP: Lessons from the Past for the Future. 2002 (pdf)
- Haruna R. Isa, William R. Shockley, Cynthia E. Irvine: A Multi-threading Architecture for Multilevel Secure Transaction Processing 1999 (pdf)
- Ivan Kelly: Report Porting MINIX to Xen 2006
- Paul Barham, Boris Dragovic, Keir Fraser, Steven Hand, Tim Harris, Alex Ho, Rolf Neugebauer, Ian Pratt, Andrew Warfield: Xen and the Art of Virtualization 2003 (pdf)
- Marcus Peinado, Yuqun Chen, Paul England, and John Manferdelli: NGSCB: A Trusted Open System (pdf)
- Michael D. Schroeder, Jerome H. SaltzerJerome H. SaltzerJerome H. Saltzer is a computer scientist who has made many notable contributions.-Career:He received an Sc. D in Electrical Engineering from MIT in 1966...
: [ftp://ftp.digital.com/pub/Digital/SRC/publications/mds/protection.pdf A Hardware Architecture for Implementing Protection Rings] 1972 (pdf) - Intel Architecture Software Developer's Manual Volume 3: System Programming (Order Number 243192) Chapter 4 Protection; section 4.5 Privilege levels. (pdf)
- Tzi-cker Chiueh, Ganesh Venkitachalam, Prashant Pradhan: Integrating segmentation and paging protection for safe, efficient and transparent software extensions 1999 Chapter 3: Protection hardware features in Intel X86 architecture; section 3.1 Protection checks. (pdf)
- Takahiro Shinagawa, Kenji Kono, Takashi Masuda: Exploiting Segmentation Mechanism for Protecting Against Malicious Mobile Code 2000 chapter 3 Implementation; section 3.2.1 Ring Protection (pdf)
- Boebert, William Earl and R. Kain. A Practical Alternative to Hierarchical Integrity Policies. Proceedings of the 8th National Computer Security Conference, 1985.
- Gorine, Andrei and Krivolapov, Alexander. Kernel Mode Databases: A DBMS technology for high-performance applications, Dr. Dobb's Journal, May, 2008.

