
Ciphertext stealing
Encyclopedia
In cryptography
, ciphertext stealing (CTS) is a general method of using a block cipher mode of operation that allows for processing of messages that are not evenly divisible into blocks without resulting in any expansion of the ciphertext
, at the cost of slightly increased complexity.
, resulting in a reordered transmission of the last two blocks of ciphertext and no ciphertext expansion. This is accomplished by padding the last plaintext block (which is possibly incomplete) with the high order bits from the second to last ciphertext block (stealing the ciphertext from the second to last block). The (now full) last block is encrypted, and then exchanged with the second to last ciphertext block, which is then truncated to the length of the final plaintext block, removing the bits that were stolen, resulting in ciphertext of the same length as the original message size. In all cases, the processing of all but the last two blocks is unchanged. The scheme described is consistent with Daemen
and Schneier
; Meyer describes a related, but incompatible scheme (with respect to bit ordering and key use).
In principle any block-oriented block cipher mode of operation can be used, but stream-cipher-like modes can already be applied to messages of arbitrary length without padding, so they do not benefit from this technique. The common modes of operation that are coupled with ciphertext stealing are ECB and CBC.
Ciphertext stealing for ECB mode requires the plaintext to be longer than one block
. A possible workaround
is to use a stream cipher-like block cipher mode of operation when the plaintext length is one block
or less, such as the CTR, CFB or OFB modes.
Ciphertext stealing for CBC mode doesn't necessarily require the plaintext to be longer than one block
. In the case where the plaintext is one block long or less the IV can act as the prior block of ciphertext. In this case a modified IV must be sent to the receiver. This may not be possible in situations where the IV can not be set by the sender when the ciphertext is sent (e.g., when the IV is a derived or pre-established value), and in this case ciphertext stealing for CBC mode can only occur in plaintexts longer than one block.
To implement CTS encryption or decryption for data of unknown length, the implementation must delay processing (and buffer) the two most recent blocks of data, so that they can be properly processed at the end of the data stream.
The following steps describe how to handle the last two blocks of the plaintext, called Pn−1 and Pn, where the length of Pn−1 equals the block size of the cipher in bits, B, the length of the last block, Pn, is M bits, and K is the key that is in use. M can range from 1 to B, inclusive, so Pn could possibly be a complete block. The CBC mode description also makes use of the ciphertext block just previous to the blocks concerned, Cn−2, which may in fact be the IV if the plaintext fits within two blocks.
For this description, the following functions and operators are used:
A bit error in the transmission of Cn would result in the block-wide corruption of Pn−1. This is a significant change from ECB's error propagation behavior.
A bit error in the transmission of Cn would result in a corresponding bit error in Pn, and in the block-wide corruption of Pn−1.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, ciphertext stealing (CTS) is a general method of using a block cipher mode of operation that allows for processing of messages that are not evenly divisible into blocks without resulting in any expansion of the ciphertext
Ciphertext
In cryptography, ciphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher...
, at the cost of slightly increased complexity.
General characteristics
Ciphertext stealing is the technique of altering processing of the last two blocks of plaintextPlaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
, resulting in a reordered transmission of the last two blocks of ciphertext and no ciphertext expansion. This is accomplished by padding the last plaintext block (which is possibly incomplete) with the high order bits from the second to last ciphertext block (stealing the ciphertext from the second to last block). The (now full) last block is encrypted, and then exchanged with the second to last ciphertext block, which is then truncated to the length of the final plaintext block, removing the bits that were stolen, resulting in ciphertext of the same length as the original message size. In all cases, the processing of all but the last two blocks is unchanged. The scheme described is consistent with Daemen
Joan Daemen
Joan Daemen |Limburg]], Belgium) is a Belgian cryptographer and one of the designers of Rijndael, the Advanced Encryption Standard , together with Vincent Rijmen. He has also designed or co-designed the MMB, Square, SHARK, NOEKEON, 3-Way, and BaseKing block ciphers...
and Schneier
Bruce Schneier
Bruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
; Meyer describes a related, but incompatible scheme (with respect to bit ordering and key use).
In principle any block-oriented block cipher mode of operation can be used, but stream-cipher-like modes can already be applied to messages of arbitrary length without padding, so they do not benefit from this technique. The common modes of operation that are coupled with ciphertext stealing are ECB and CBC.
Ciphertext stealing for ECB mode requires the plaintext to be longer than one block
Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
. A possible workaround
Workaround
A workaround is a bypass of a recognized problem in a system. A workaround is typically a temporary fix that implies that a genuine solution to the problem is needed...
is to use a stream cipher-like block cipher mode of operation when the plaintext length is one block
Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
or less, such as the CTR, CFB or OFB modes.
Ciphertext stealing for CBC mode doesn't necessarily require the plaintext to be longer than one block
Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
. In the case where the plaintext is one block long or less the IV can act as the prior block of ciphertext. In this case a modified IV must be sent to the receiver. This may not be possible in situations where the IV can not be set by the sender when the ciphertext is sent (e.g., when the IV is a derived or pre-established value), and in this case ciphertext stealing for CBC mode can only occur in plaintexts longer than one block.
To implement CTS encryption or decryption for data of unknown length, the implementation must delay processing (and buffer) the two most recent blocks of data, so that they can be properly processed at the end of the data stream.
Ciphertext stealing mode description
In order to encrypt or decrypt data, use the standard block cipher mode of operation on all but the last two blocks of data.The following steps describe how to handle the last two blocks of the plaintext, called Pn−1 and Pn, where the length of Pn−1 equals the block size of the cipher in bits, B, the length of the last block, Pn, is M bits, and K is the key that is in use. M can range from 1 to B, inclusive, so Pn could possibly be a complete block. The CBC mode description also makes use of the ciphertext block just previous to the blocks concerned, Cn−2, which may in fact be the IV if the plaintext fits within two blocks.
For this description, the following functions and operators are used:
- Head (data, a): returns the first a bits of the 'data' string.
- Tail (data, a): returns the last a bits of the 'data' string.
- Encrypt (K, data): use the underlying block cipher in encrypt mode on the 'data' string using the key K.
- Decrypt (K, data): use the underlying block cipher in decrypt mode on the 'data' string using the key K.
- XOR: Bitwise Exclusive-OR. Equivalent to bitwise addition without use of a carry bit.
- ||: Concatenation operator. Combine the strings on either side of the operator.
- 0a: a string of a 0 bits.
ECB ciphertext stealing
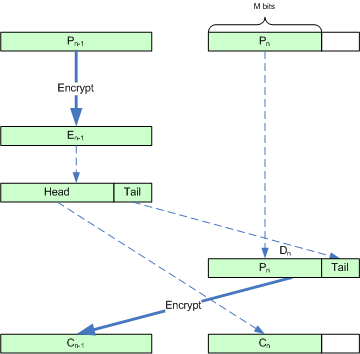
Ciphertext stealing in ECB mode introduces an inter-block dependency within the last two blocks, resulting in altered error propagation behavior for the last two blocks.ECB encryption steps (see figure)

- En−1 = Encrypt (K, Pn−1). Encrypt Pn−1 to create En−1. This is equivalent to the behavior of standard ECB mode.
- Cn = Head (En−1, M). Select the first M bits of En−1 to create Cn. The final ciphertext block, Cn, is composed of the leading M bits of the second-to-last ciphertext block. In all cases, the last two blocks are sent in a different order than the corresponding plaintext blocks.
- Dn = Pn || Tail (En−1, B−M). Pad Pn with the low order bits from En−1.
- Cn−1 = Encrypt (K, Dn). Encrypt Dn to create Cn−1. For the first M bits, this is equivalent to what would happen in ECB mode (other than the ciphertext ordering). For the last B−M bits, this is the second time that these data have been encrypted under this key (It was already encrypted in the production of En−1 in step 2).
ECB decryption steps
- Dn = Decrypt (K, Cn−1). Decrypt Cn−1 to create Dn. This undoes step 4 of the encryption process.
- En−1 = Cn || Tail (Dn, B−M). Pad Cn with the extracted ciphertext in the tail end of Dn (placed there in step 3 of the ECB encryption process).
- Pn = Head (Dn, M). Select the first M bits of Dn to create Pn. As described in step 3 of the ECB encryption process, the first M bits of Dn contain Pn. We queue this last (possibly partial) block for eventual output.
- Pn−1 = Decrypt (K, En−1). Decrypt En−1 to create Pn−1. This reverses encryption step 1.
ECB ciphertext stealing error propagation
A bit error in the transmission of Cn−1 would result in the block-wide corruption of both Pn−1 and Pn.A bit error in the transmission of Cn would result in the block-wide corruption of Pn−1. This is a significant change from ECB's error propagation behavior.
CBC ciphertext stealing
In CBC, there is already interaction between processing of different adjacent blocks, so CTS has less conceptual impact in this mode. Error propagation is affected.CBC encryption steps
- Xn−1 = Pn−1 XOR Cn−2. Exclusive-OR Pn−1 with the previous ciphertext block, Cn−2, to create Xn−1. This is equivalent to the behavior of standard CBC mode.
- En−1 = Encrypt (K, Xn−1). Encrypt Xn−1 to create En−1. This is equivalent to the behavior of standard CBC mode.
- Cn = Head (En−1, M). Select the first M bits of En−1 to create Cn. The final ciphertext block, Cn, is composed of the leading M bits of the second-to-last ciphertext block. In all cases, the last two blocks are sent in a different order than the corresponding plaintext blocks.
- P = Pn || 0B−M. Pad Pn with zeros at the end to create P of length B. The zero padding in this step is important for step 5.
- Dn = En−1 XOR P. Exclusive-OR En−1 with P to create Dn. For the first M bits of the block, this is equivalent to CBC mode; the first M bits of the previous block's ciphertext, En−1,are XORed with the M bits of plaintext of the last plaintext block. The zero padding of P in step 4 was important, because it makes the XOR operation's effect on the last B−M bits equivalent to copying the last B−M bits of En−1 to the end of Dn. These are the same bits that were stripped off of En−1 in step 3 when Cn was created.
- Cn−1 = Encrypt (K, Dn). Encrypt Dn to create Cn−1. For the first M bits, this is equivalent to what would happen in CBC mode (other than the ciphertext ordering). For the last B−M bits, this is the second time that these data have been encrypted under this key (It was already encrypted in the production of En−1 in step 2).
CBC decryption steps
- Dn = Decrypt (K, Cn−1). Decrypt Cn−1 to create Dn. This undoes step 6 of the encryption process.
- C = Cn || 0B−M. Pad Cn with zeros at the end to create a block C of length B. We are padding Cn with zeros to help in step 3.
- Xn = Dn XOR C. Exclusive-OR Dn with C to create Xn. Looking at the first M bits, this step has the result of XORing Cn (the first M bits of the encryption process' En−1) with the (now decrypted) Pn XOR Head (En−1, M) (see steps 4-5 of the encryption process). In other words, we have CBC decrypted the first M bits of Pn. Looking at the last B−M bits, this recovers the last B−M bits of En−1.
- Pn = Head (Xn, M). Select the first M bits of Xn to create Pn. As described in step 3, the first M bits of Xn contain Pn. We queue this last (possibly partial) block for eventual output.
- En−1 = Cn || Tail (Xn, B−M). Append the tail (B−M) bits of Xn to Cn to create En−1. As described in step 3, En−1 is composed of all of Cn (which is M bits long) appended with the last B−M bits of Xn. We reassemble En−1 (which is the same En−1 seen in the encryption process) for processing in step 6.
- Xn−1 = Decrypt (K, En−1). Decrypt En−1 to create Xn−1. This reverses encryption step 2. Xn−1 is the same as in the encryption process.
- Pn−1 = Xn−1 XOR Cn−2. Exclusive-OR Xn−1 with the previous ciphertext block, Cn−2, to create Pn−1. Finally, we reverse the XOR step from step 1 of the encryption process.
CBC Implementation Notes
For CBC ciphertext stealing, there is a clever (but opaque) method of implementing the described ciphertext stealing process using a standard CBC interface. Using this method imposes a performance penalty in the decryption stage of one extra block decryption operation over what would be necessary using a dedicated implementation.CBC ciphertext stealing encryption using a standard CBC interface
- Pad the last partial plaintext block with 0.
- Encrypt the whole padded plaintext using the standard CBC mode.
- Swap the last two ciphertext blocks.
- Truncate the ciphertext to the length of the original plaintext.
CBC ciphertext stealing decryption using a standard CBC interface
- Dn = Decrypt (K, Cn−1). Decrypt the second to the last ciphertext block, using zeros as IV.
- Cn = Cn || Tail (Dn, B−M). Pad the ciphertext to the nearest multiple of the block size using the last B−M bits of block cipher decryption of the second-to-last ciphertext block.
- Swap the last two ciphertext blocks.
- Decrypt the ciphertext using the standard CBC mode up to the last block.
- Exclusive-OR the last ciphertext (was already decrypted in step 1) with the second last plaintext.
- Truncate the plaintext to the length of the original ciphertext.
CBC ciphertext stealing error propagation
A bit error in the transmission of Cn−1 would result in the block-wide corruption of both Pn−1 and Pn.A bit error in the transmission of Cn would result in a corresponding bit error in Pn, and in the block-wide corruption of Pn−1.

