
Bootstrapping Server Function
Encyclopedia
Cellular network
A cellular network is a radio network distributed over land areas called cells, each served by at least one fixed-location transceiver known as a cell site or base station. When joined together these cells provide radio coverage over a wide geographic area...
s which provides application independent functions for mutual authentication
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
of user equipment and servers unknown to each other and for 'bootstrapping' the exchange of secret session keys afterwards. This allows the use of additional services like Mobile TV
Mobile TV
Mobile television usually means television watched on a small handheld device. It may be a pay TV service broadcast on mobile phone networks or received free-to-air via terrestrial television stations from either regular broadcast or a special mobile TV transmission format...
and PKI
Public key infrastructure
Public Key Infrastructure is a set of hardware, software, people, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates. In cryptography, a PKI is an arrangement that binds public keys with respective user identities by means of a certificate...
, which need authentication and secured communication.
GBA/GAA Setup
The setup and function to deploy a generic security relation as described is called Generic Bootstrapping Architecture (GBAGeneric Bootstrapping Architecture
-Introduction:In mobile phones, Generic Bootstrapping Architecture is one technology enabling the authentication of a user. This authentication is possible if the user owns a valid identity on an HLR Home Location Register or a Home Subscriber Server...
) or Generic Authentication Architecture
Generic Authentication Architecture
Generic Authentication Architecture is a standard made by 3GPP defined in . Taken from the document:"This Technical Report aims to give an overview of the different mechanisms that mobile applications can rely upon for authentication between server and client...
(GAA). In short, it consists of the following elements.
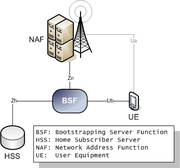
- user equipment (UE), e. g. a mobile cellular telephone; needs access to a specific service
- application server (NAF: Network Application Function), e. g. for mobile TV; provides the service
- BSF (Bootstrapping Server Function); arranges security relation between UE and NAF
- mobile network operator's Home Subscriber Server (HSS); hosts user profiles.
In this case, the term 'bootstrapping
Bootstrapping
Bootstrapping or booting refers to a group of metaphors that share a common meaning: a self-sustaining process that proceeds without external help....
' is related to building a security relation with a previously unknown device first and to allow installing security elements (keys) in the device and the BSF afterwards.
Workflow
The BSF is introduced by the application server (NAF), after an unknown UE device is trying to get service access: the NAF refers the UE to the BSF. UE and BSF mutually authenticate via 3GPP3GPP
The 3rd Generation Partnership Project is a collaboration between groups of telecommunications associations, known as the Organizational Partners...
protocol AKA (Authentication and Key Agreement); additionally, the BSF sends related queries to the Home Subscriber Server (HSS).
Afterwards, UE and BSF agree on a session key to be used for encrypted data exchange with the application server (NAF). When the UE again connects to the NAF, the NAF is able to obtain the session key as well as user specific data from the BSF and can start data exchange with the end device (UE), using the related session keys for encryption.
Standards
BSF is standardised in recent versions of 3GPP Standards: GAA (Generic Authentication Architecture) and GBA (Generic Bootstrapping ArchitectureGeneric Bootstrapping Architecture
-Introduction:In mobile phones, Generic Bootstrapping Architecture is one technology enabling the authentication of a user. This authentication is possible if the user owns a valid identity on an HLR Home Location Register or a Home Subscriber Server...
), and 3GPP TS 33.919, 33.220 24.109, 29.109

