
Advanced Access Content System
Encyclopedia
Standardization
Standardization is the process of developing and implementing technical standards.The goals of standardization can be to help with independence of single suppliers , compatibility, interoperability, safety, repeatability, or quality....
for content distribution and digital rights management
Digital rights management
Digital rights management is a class of access control technologies that are used by hardware manufacturers, publishers, copyright holders and individuals with the intent to limit the use of digital content and devices after sale. DRM is any technology that inhibits uses of digital content that...
, intended to restrict access to and copying
Copying
Copying is the duplication of information or an artifact based only on an instance of that information or artifact, and not using the process that originally generated it. With analog forms of information, copying is only possible to a limited degree of accuracy, which depends on the quality of the...
of the "next generation
Generation
Generation , also known as procreation in biological sciences, is the act of producing offspring....
" of optical discs and DVD
DVD
A DVD is an optical disc storage media format, invented and developed by Philips, Sony, Toshiba, and Panasonic in 1995. DVDs offer higher storage capacity than Compact Discs while having the same dimensions....
s. The specification was publicly released in April 2005 and the standard has been adopted as the access restriction scheme for HD DVD
HD DVD
HD DVD is a discontinued high-density optical disc format for storing data and high-definition video.Supported principally by Toshiba, HD DVD was envisioned to be the successor to the standard DVD format...
and Blu-ray Disc
Blu-ray Disc
Blu-ray Disc is an optical disc storage medium designed to supersede the DVD format. The plastic disc is 120 mm in diameter and 1.2 mm thick, the same size as DVDs and CDs. Blu-ray Discs contain 25 GB per layer, with dual layer discs being the norm for feature-length video discs...
(BD). It is developed by AACS Licensing Administrator, LLC
AACS LA
AACS LA is the body that develops and licenses the AACS copy-protection system used on the HD DVD and Blu-ray Disc high-definition optical disc formats....
(AACS LA), a consortium
Consortium
A consortium is an association of two or more individuals, companies, organizations or governments with the objective of participating in a common activity or pooling their resources for achieving a common goal....
that includes Disney
The Walt Disney Company
The Walt Disney Company is the largest media conglomerate in the world in terms of revenue. Founded on October 16, 1923, by Walt and Roy Disney as the Disney Brothers Cartoon Studio, Walt Disney Productions established itself as a leader in the American animation industry before diversifying into...
, Intel, Microsoft
Microsoft
Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions...
, Panasonic, Warner Bros.
Warner Bros.
Warner Bros. Entertainment, Inc., also known as Warner Bros. Pictures or simply Warner Bros. , is an American producer of film and television entertainment.One of the major film studios, it is a subsidiary of Time Warner, with its headquarters in Burbank,...
, IBM
IBM
International Business Machines Corporation or IBM is an American multinational technology and consulting corporation headquartered in Armonk, New York, United States. IBM manufactures and sells computer hardware and software, and it offers infrastructure, hosting and consulting services in areas...
, Toshiba
Toshiba
is a multinational electronics and electrical equipment corporation headquartered in Tokyo, Japan. It is a diversified manufacturer and marketer of electrical products, spanning information & communications equipment and systems, Internet-based solutions and services, electronic components and...
and Sony
Sony
, commonly referred to as Sony, is a Japanese multinational conglomerate corporation headquartered in Minato, Tokyo, Japan and the world's fifth largest media conglomerate measured by revenues....
. AACS has been operating under an "interim agreement" since the final specification (including provisions for Managed Copy) has not yet been finalised.
Since appearing in devices in 2006, several AACS decryption keys have been extracted from weakly protected software players and published on the Internet, allowing decryption by other unlicensed software.
Encryption
AACS uses cryptographyCryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
to control the use of digital media. It encrypts content under one or more title keys using the Advanced Encryption Standard
Advanced Encryption Standard
Advanced Encryption Standard is a specification for the encryption of electronic data. It has been adopted by the U.S. government and is now used worldwide. It supersedes DES...
(AES). Title keys are decrypted using a combination of a media key (encoded in a Media Key Block
Media Key Block
The Media Key Block is one of the keys that are included inside the copying protection system AACS. This system is used to protect Blu-ray and HD DVD formats from being copied...
) and the Volume ID of the media (e.g., a physical serial number embedded on a pre-recorded disc).
The principal difference between AACS and CSS
Content Scramble System
Content Scramble System is a Digital Rights Management and encryption system employed on almost all commercially produced DVD-Video discs. CSS utilizes a proprietary 40-bit stream cipher algorithm...
, the DRM system used on DVD
DVD
A DVD is an optical disc storage media format, invented and developed by Philips, Sony, Toshiba, and Panasonic in 1995. DVDs offer higher storage capacity than Compact Discs while having the same dimensions....
s, lies in how the device decryption keys are organized.
Under CSS, all players of a given model are provisioned with the same shared decryption key. Content is encrypted under the title-specific key, which is itself encrypted under each model's key. Thus each disc contains a collection of several hundred encrypted keys, one for each licensed player model.
In principle, this approach allows licensors to "revoke" a given player model (prevent it from playing back future content) by omitting to encrypt future title keys with the player model's key. In practice, however, revoking all players of a particular model is costly, as it causes many users to lose playback capability. Furthermore, the inclusion of a shared key across many players makes key compromise significantly more likely, as was demonstrated by a number of compromises in the mid-1990s.
The approach of AACS provisions each individual player with a unique set of decryption keys which are used in a broadcast encryption
Broadcast encryption
Broadcast encryption is the cryptographic problem of encrypting broadcast content in such a way that only qualified users can decrypt the content. The challenge arises from the requirement that unsubscription of some users should not affect the remaining users...
scheme. This approach allows licensors to "revoke" individual players, or more specifically, the decryption keys associated with the player. Thus, if a given player's keys are compromised and published, the AACS LA can simply revoke those keys in future content, making the keys/player useless for decrypting new titles.
AACS also has traitor tracing
Traitor tracing
Traitor tracing is a copyright infringement detection system which works by tracing the source of leaked files rather than by direct copy protection. The method is that the distributor adds a unique value to each copy given out...
. The standard allows different versions of short sections of a movie to be encrypted with different keys. A certain player will only be able to decrypt one version of each section. By embedding a digital watermark
Digital watermarking
Digital watermarking is the process of embedding information into a digital signal which may be used to verify its authenticity or the identity of its owners, in the same manner as paper bearing a watermark for visible identification. In digital watermarking, the signal may be audio, pictures, or...
in the different versions and analyzing what sections of the movie the attacker publishes, the compromised keys can eventually be identified and revoked (this feature is called Sequence keys in the AACS specifications).
Volume IDs
Volume IDs are unique identifiers or serial numbers that are stored on pre-recorded discs with special hardware. They cannot be duplicated on consumers' recordable media. The point of this is to prevent simple bit-by-bit copies, since the Volume ID is required (though not sufficient) for decoding content. On Blu-ray discs, the Volume ID is stored in the BD-ROM MarkROM-Mark
In computing, ROM Mark or BD-ROM Mark is a serialization technology designed to guard against mass production piracy or the mass duplication and sale of unauthorized copies of pre-recorded Blu-ray Discs...
.
To read the Volume ID, a cryptographic certificate
Public key certificate
In cryptography, a public key certificate is an electronic document which uses a digital signature to bind a public key with an identity — information such as the name of a person or an organization, their address, and so forth...
(the Private Host Key) signed by the AACS LA is required. However, hackers claim to have circumvented that particular protection by modifying the firmware of an HD DVD reader.
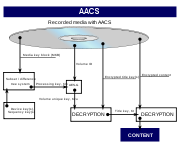
Decryption process
To view the movie, the player must first decrypt the content on the disc. The decryption process is somewhat convoluted. The disc contains 4 items—the Media Key Block (MKB), the Volume ID, the Encrypted Title Keys, and the Encrypted Content. The MKB is encrypted in a subset difference tree approach. Essentially, a set of keys are arranged in a tree such that any given key can be used to find every other key except its parent keys. This way, to revoke a given device keyDevice Keys
Device Keys play a role in the cryptographic key management procedure in the Advanced Access Content System specification. This specification defines a method for protecting audiovisual entertainment content, including high-definition content....
, the MKB needs only be encrypted with that device key's parent key.
Once the MKB is decrypted, it provides the Media Key, or the km. The km is combined with the Volume ID (which the program can only get by presenting a cryptographic certificate to the drive, as described above) in a one-way encryption scheme (AES-G) to produce the Volume Unique Key (Kvu). The Kvu is used to decrypt the encrypted title keys, and that is used to decrypt the encrypted content.
Analog Outputs
AACS-compliant players must follow guidelines pertaining to outputs over analog connections. This is set by a flag called the Image Constraint Token (ICT), which restricts the resolution for analog outputs to 960×540. Full 1920×1080 resolution is restricted to HDMI or DVI outputs that support HDCPHigh-Bandwidth Digital Content Protection
High-bandwidth Digital Content Protection is a form of digital copy protection developed by Intel Corporation to prevent copying of digital audio and video content as it travels across connections...
. The decision to set the flag to restrict output ("down-convert") is left to the content provider. Warner Pictures is a proponent of ICT, and it is expected that Paramount and Universal will implement down-conversion as well.
AACS guidelines require that any title that implements the ICT must clearly state so on the packaging. The German magazine "Der Spiegel" has reported about an unofficial agreement between film studios and electronics manufacturers to not use ICT until 2010 - 2012. However, some titles have already been released that apply ICT.
Audio watermarking
On June 5, 2009, the licensing agreements for AACS were finalized, which were updated to make CinaviaCinavia
Cinavia is a digital rights management system created by Verance. It requires two parts to work: a proprietary imperceptible audio watermark, and a piece of hardware which is able to detect that watermark. Known hardware which can detect Cinavia watermarks include the PlayStation 3 , as well as...
detection on commercial Blu-ray disc players a requirement.
Managed Copy
Managed Copy refers to a system by which consumers can make legal copies of films and other digital content protected by AACS. This requires the device to obtain authorization by contacting a remote server on the Internet. The copies will still be protected by DRMDigital rights management
Digital rights management is a class of access control technologies that are used by hardware manufacturers, publishers, copyright holders and individuals with the intent to limit the use of digital content and devices after sale. DRM is any technology that inhibits uses of digital content that...
, so infinite copying is not possible (unless it is explicitly allowed by the content owner). It is mandatory for content providers to give the consumer this flexibility in both the HD DVD and the Blu-ray standards (commonly called Mandatory Managed Copy). The Blu-ray standards adopted Mandatory Managed Copy later than HD DVD, after HP
Hewlett-Packard
Hewlett-Packard Company or HP is an American multinational information technology corporation headquartered in Palo Alto, California, USA that provides products, technologies, softwares, solutions and services to consumers, small- and medium-sized businesses and large enterprises, including...
requested it.
Possible scenarios for Managed Copy include (but are not limited to):
- Create an exact duplicate onto a recordable disc for backup
- Create a full-resolution copy for storage on a media server
- Create a scaled-down version for watching on a portable device
This feature was not included in the interim standard, so the first devices on the market did not have this capability. It was expected to be a part of the final AACS specification.
In June 2009, the final AACS agreements were ratified and posted online, and include information on the Managed Copy aspects of AACS.
History
On February 24, 2001, Dalit Naor, Moni Naor and Jeff Lotspiech published a paper entitled "Revocation and Tracing Schemes for Stateless Receivers", where they described a broadcast encryption scheme using a construct called Naor-Naor-Lotspiech subset-difference trees. That paper laid the theoretical foundations of AACS.The AACS LA consortium was founded in 2004. With DeCSS
DeCSS
DeCSS is a computer program capable of decrypting content on a commercially produced DVD video disc. Before the release of DeCSS, there was no way for computers running a Linux-based operating system to play video DVDs....
in hindsight, the IEEE Spectrum
IEEE Spectrum
IEEE Spectrum is a magazine edited by the Institute of Electrical and Electronics Engineers. The IEEE's description of it is:IEEE Spectrum began publishing in January 1964 as a successor to Electrical Engineering...
magazine's readers voted AACS to be one of the technologies most likely to fail in the January 2005 issue.
The final AACS standard was delayed, and then delayed again when an important member of the Blu-ray group voiced concerns. At the request of Toshiba, an interim standard was published which did not include some features, like managed copy. As of October 15, 2007, the final AACS standard had not yet been released.
Open-source implementations
On December 26, 2006, a person using the aliasPseudonym
A pseudonym is a name that a person assumes for a particular purpose and that differs from his or her original orthonym...
"muslix64" published a working, open-sourced AACS decrypting utility named BackupHDDVD
BackupHDDVD
BackupHDDVD is a small computer software utility program available in command line and GUI versions which aids in the decryption of commercial HD DVD discs protected by the Advanced Access Content System. It is used to back up discs, often to enable playback on hardware configurations without full...
, looking at the publicly available AACS specifications. Given the correct keys, it can be used to decrypt AACS-encrypted content. A corresponding BackupBluRay
BackupBluRay
BackupBluRay is a free, open source utility which aids in the decryption of AACS copy-protected content on Blu-ray discs, presumably for the purpose of backing up a video that a consumer has purchased...
program was soon developed, as well as a "ClownBD" program mimicking CloneDVD
CloneDVD
CloneDVD is a proprietary DVD cloning software, developed by Elaborate Bytes, that can be used to make backup copies of any DVD movie not copy-protected . The program is able to transcode a dual layer DVD movie to fit it onto a DVD-R, DVD+R or DVD+R DL disc...
but for Blu-ray. SlySoft
SlySoft
SlySoft Inc. is a software company located in St. John's, Antigua and Barbuda. Its products consist of software to back up and convert digital media, including CDs, DVDs, HD DVDs, and Blu-ray Discs, as well as copy and back up optical media and render PC-based games playable without the...
have stated they are working on CloneBD that supports Blu-ray.
Security
Both title keys and one of the keys used to decrypt them (known as Processing Keys in the AACS specifications) have been found by using debuggers to inspect the memory space of running HD DVD and Blu-ray player programs.Hackers also claim to have found Device Keys
(used to calculate the Processing Key) and a Host Private Key
(a key signed by the AACS LA used for hand-shaking between host and HD drive; required for reading the Volume ID). The first unprotected HD movies were available soon afterwards.
The processing key was widely published
AACS encryption key controversy
A controversy surrounding the AACS cryptographic key arose in April 2007 when the Motion Picture Association of America and the Advanced Access Content System Licensing Administrator, LLC began issuing demand letters to websites publishing a 128-bit number, represented in hexadecimal as 09 F9 11...
on the Internet after it was found and the AACS LA sent multiple DMCA takedown notices in the aim of censoring it.
Some sites that rely on user-submitted content, like Digg
Digg
Digg is a social news website. Prior to Digg v4, its cornerstone function consisted of letting people vote stories up or down, called digging and burying, respectively. Digg's popularity prompted the creation of copycat social networking sites with story submission and voting systems...
and Wikipedia
Wikipedia
Wikipedia is a free, web-based, collaborative, multilingual encyclopedia project supported by the non-profit Wikimedia Foundation. Its 20 million articles have been written collaboratively by volunteers around the world. Almost all of its articles can be edited by anyone with access to the site,...
, tried to remove any mentions of the key.
The Digg administrators eventually gave up trying to censor submissions that contained the key.
The AACS key extractions highlight the inherent weakness in any DRM system that permit software players for PCs to be used for playback of content. No matter how many layers of encryption are employed, it does not offer any true protection, since the keys needed to obtain the unencrypted content stream must be available somewhere in memory for playback to be possible. The PC platform offers no way to prevent memory snooping attacks on such keys, since a PC configuration can always be emulated by a virtual machine
Virtual machine
A virtual machine is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software emulation or hardware virtualization or both together.-VM Definitions:A virtual machine is a software...
, in theory without any running program or external system being able to detect the virtualization. The only way to wholly prevent attacks like this would require changes to the PC platform (see Trusted Computing
Trusted Computing
Trusted Computing is a technology developed and promoted by the Trusted Computing Group. The term is taken from the field of trusted systems and has a specialized meaning. With Trusted Computing, the computer will consistently behave in expected ways, and those behaviors will be enforced by...
) which could provide protection against such attacks. This would require that content distributors do not permit their content to be played on PCs without trusted computing technology, by not providing the companies making software players for non-trusted PCs with the needed encryption keys.
On April 16, 2007, the AACS consortium announced that it had expired certain encryption keys used by PC-based applications. Patches were available for WinDVD and PowerDVD which used new and uncompromised encryption keys.
The old, compromised keys can still be used to decrypt old titles, but not newer releases as they will be encrypted with these new keys. All users of the affected players (even those considered "legitimate" by the AACS LA) are forced to upgrade or replace their player software in order to view new titles.
Despite all revocations, current titles can be decrypted using new MKB v7, v9 or v10 keys widely available in the Internet.
Besides spreading processing keys on the Internet, there have also been efforts to spread title keys on various sites.
The AACS LA has sent DMCA takedown notices to such sites on at least one occasion.
There is also commercial software (AnyDVD HD
AnyDVD
AnyDVD is a Microsoft Windows driver allowing decryption of DVDs on-the-fly, as well as targeted removal of copy preventions and user operation prohibitions . With an upgrade, it will also do the same for HD DVD and Blu-ray. The AnyDVD program runs in the background, making discs unrestricted and...
) that can circumvent the AACS protection. Apparently this program works even with movies released after the AACS LA expired the first batch of keys.
While great care has been taken with AACS to ensure that contents are encrypted right up to the display device, on the first versions of some Blu-ray and HD DVD
HD DVD
HD DVD is a discontinued high-density optical disc format for storing data and high-definition video.Supported principally by Toshiba, HD DVD was envisioned to be the successor to the standard DVD format...
software players a perfect copy of any still frame from a film could be made simply by utilizing the Print Screen
Print screen
Print screen is a key present on most PC keyboards. It is typically situated in the same section as the break key and scroll lock key...
function of the Windows operating system. This was broken in later versions.
Patent challenges
On May 30, 2007, Canadian encryption vendor Certicom sued Sony alleging that AACS violated two of its patents, "Strengthened public key protocol" and "Digital signatures on a Smartcard." The patents were filed in 1999 and 2001 respectively, and in 2003 the National Security AgencyNational Security Agency
The National Security Agency/Central Security Service is a cryptologic intelligence agency of the United States Department of Defense responsible for the collection and analysis of foreign communications and foreign signals intelligence, as well as protecting U.S...
paid $25 million for the right to use 26 of Certicom's patents, including the two that Sony is alleged to have infringed on.
See also
- History of attacks against Advanced Access Content System
- AACS encryption key controversyAACS encryption key controversyA controversy surrounding the AACS cryptographic key arose in April 2007 when the Motion Picture Association of America and the Advanced Access Content System Licensing Administrator, LLC began issuing demand letters to websites publishing a 128-bit number, represented in hexadecimal as 09 F9 11...
External links
- AACS homepage
- AACS specifications
- Understanding AACS, an introductory forum thread.
- ISAN homepage, ISAN as required in the Content ID defined in AACS Introduction and Common Cryptographic Elements rev 0.91
- libaacs, an open source library implementing AACS
- Hal Finney on 'AACS and Processing Key' -(Hal FinneyHal Finney (cypherpunk)Hal Finney is a developer for PGP Corporation, and was the 2nd developer hired after Phil Zimmerman. In his early career, he is credited as lead developer on several console games...
on the tree key revocation scheme in AACS)

