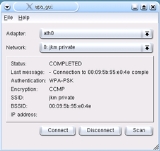
Wpa supplicant
Encyclopedia
wpa_supplicant is a free software
implementation of an IEEE 802.11i
supplicant
for Linux
, FreeBSD
, NetBSD
and Microsoft Windows
. In addition to being a full-featured WPA2 supplicant, it also implements WPA
and older wireless LAN
security protocols. Features include:
Included with the supplicant are a graphical user interface
and a command line interface utility for interacting with the running supplicant. From either of these interfaces it is possible to review a list of currently visible networks, select one of them, provide any additional security information needed to authenticate with the network (e.g. a passphrase
or username and password
) and add it to the preference list to enable automatic reconnection in the future.
The graphical user interface is built on top of the Qt library
from Qt Software (formerly Trolltech).
Free software
Free software, software libre or libre software is software that can be used, studied, and modified without restriction, and which can be copied and redistributed in modified or unmodified form either without restriction, or with restrictions that only ensure that further recipients can also do...
implementation of an IEEE 802.11i
IEEE 802.11i
IEEE 802.11i-2004 or 802.11i, implemented as WPA2, is an amendment to the original IEEE 802.11. The draft standard was ratified on 24 June 2004. This standard specifies security mechanisms for wireless networks. It replaced the short Authentication and privacy clause of the original standard with...
supplicant
Supplicant (computer)
The term supplicant is used in the IEEE 802.1X standard, where the supplicant is an entity at one end of a point-to-point LAN segment that seeks to be authenticated by an authenticator attached to the other end of that link. In practice, a supplicant is a software application installed on an...
for Linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
, FreeBSD
FreeBSD
FreeBSD is a free Unix-like operating system descended from AT&T UNIX via BSD UNIX. Although for legal reasons FreeBSD cannot be called “UNIX”, as the direct descendant of BSD UNIX , FreeBSD’s internals and system APIs are UNIX-compliant...
, NetBSD
NetBSD
NetBSD is a freely available open source version of the Berkeley Software Distribution Unix operating system. It was the second open source BSD descendant to be formally released, after 386BSD, and continues to be actively developed. The NetBSD project is primarily focused on high quality design,...
and Microsoft Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
. In addition to being a full-featured WPA2 supplicant, it also implements WPA
Wi-Fi Protected Access
Wi-Fi Protected Access and Wi-Fi Protected Access II are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks...
and older wireless LAN
Wireless LAN
A wireless local area network links two or more devices using some wireless distribution method , and usually providing a connection through an access point to the wider internet. This gives users the mobility to move around within a local coverage area and still be connected to the network...
security protocols. Features include:
- WPA and full IEEE 802.11i/RSN/WPA2
- WPA-PSK and WPA2-PSK (pre-shared key) ("WPA-Personal")
- WPA with EAPExtensible Authentication ProtocolExtensible Authentication Protocol, or EAP, is an authentication framework frequently used in wireless networks and Point-to-Point connections. It is defined in RFC 3748, which made RFC 2284 obsolete, and was updated by RFC 5247....
(e.g., with RADIUSRADIUSRemote Authentication Dial In User Service is a networking protocol that provides centralized Authentication, Authorization, and Accounting management for computers to connect and use a network service...
authentication server) ("WPA-Enterprise") - key management for CCMPCCMPCounter Mode with Cipher Block Chaining Message Authentication Code Protocol or CCMP is an encryption protocol designed for Wireless LAN products that implement the standards of the IEEE 802.11i amendment to the original IEEE 802.11 standard...
, TKIP, WEPWired Equivalent PrivacyWired Equivalent Privacy is a weak security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standard ratified in September 1999, its intention was to provide data confidentiality comparable to that of a traditional wired network...
(both 104/128 and 40/64 bit) - RSN: PMKSA caching, pre-authentication
Included with the supplicant are a graphical user interface
Graphical user interface
In computing, a graphical user interface is a type of user interface that allows users to interact with electronic devices with images rather than text commands. GUIs can be used in computers, hand-held devices such as MP3 players, portable media players or gaming devices, household appliances and...
and a command line interface utility for interacting with the running supplicant. From either of these interfaces it is possible to review a list of currently visible networks, select one of them, provide any additional security information needed to authenticate with the network (e.g. a passphrase
Passphrase
A passphrase is a sequence of words or other text used to control access to a computer system, program or data. A passphrase is similar to a password in usage, but is generally longer for added security. Passphrases are often used to control both access to, and operation of, cryptographic programs...
or username and password
Password
A password is a secret word or string of characters that is used for authentication, to prove identity or gain access to a resource . The password should be kept secret from those not allowed access....
) and add it to the preference list to enable automatic reconnection in the future.
The graphical user interface is built on top of the Qt library
Qt (toolkit)
Qt is a cross-platform application framework that is widely used for developing application software with a graphical user interface , and also used for developing non-GUI programs such as command-line tools and consoles for servers...
from Qt Software (formerly Trolltech).
EAP methods
wpa_supplicant can authenticate with any of the following EAP (Extensible Authentication Protocol) methods:- EAP-TLS
- EAP-PEAP (both PEAPv0 and PEAPv1)
- EAP-TTLS
- EAP-SIM
- EAP-AKA
- EAP-PSK (experimental)
- EAP-FAST
- EAP-PAX
- EAP-SAKE
- EAP-GPSK
- LEAP (note: requires special functions in the driver)
See also
- NetworkManagerNetworkManagerNetwork Manager is a software utility aimed at simplifying the use of computer networks on Linux-based and other Unix-like operating systems.- Overview :...
- Devicescape
- Wireless supplicantWireless SupplicantA Wireless Supplicant is a program that runs on a computer and is responsible for making login requests to a wireless network. It handles passing the login and encryption credentials to the authentication server. It also handles roaming from one wireless access point to another, in order to...
- XsupplicantXsupplicantXsupplicant is a supplicant that allows a workstation to authenticate with a RADIUS server using 802.1x and the Extensible Authentication Protocol...

