
Non-interference
Encyclopedia
Non-interference is a strict multilevel security
policy model, first described by Goguen and Meseguer in 1982, and amplified further in 1984.
That is, if a low (uncleared) user is working on the machine, it will respond in exactly the same manner (on the low outputs) whether or not a high (cleared) user is working with sensitive data. The low user will not be able to acquire any information
about the activities (if any) of the high user.
 be a memory configuration, and let
be a memory configuration, and let  and
and 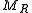 be the projection of the memory
be the projection of the memory 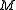 to the low and high parts, respectively. Let
to the low and high parts, respectively. Let  be the function that compares the low parts of the memory configurations, i.e.,
be the function that compares the low parts of the memory configurations, i.e., 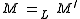 iff
iff  . Let
. Let  be the execution of the program
be the execution of the program 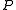 starting with memory configuration
starting with memory configuration 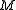 and terminating with the memory configuration
and terminating with the memory configuration  .
.
The definition of non-interference for a deterministic program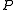 is the following :
is the following :
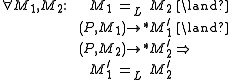
This strictness comes with a price. It is very difficult to make a computer system with this property. There may be only one or two commercially available products that have been verified to comply with this policy, and these would essentially be as simple as switches and one-way information filters (although these could be arranged to provide useful behaviour).
Computer systems that comply with the Bell-LaPadula Model do not suffer from this problem since they explicitly forbid "read-up." Consequently, a computer system that complies with non-interference will not necessarily comply with the Bell-LaPadula Model. Thus, the Bell–LaPadula model and the non-interference model are incomparable: the Bell-LaPadula Model is stricter regarding read-up, and the non-interference model is stricter with respect to covert channels.
Multilevel security
Multilevel security or Multiple Levels of Security is the application of a computer system to process information with different sensitivities , permit simultaneous access by users with different security clearances and needs-to-know, and prevent users from obtaining access to information for...
policy model, first described by Goguen and Meseguer in 1982, and amplified further in 1984.
Introduction
In simple terms, a computer is modeled as a machine with inputs and outputs. Inputs and outputs are classified as either low (low sensitivity, not highly classified) or high (sensitive, not to be viewed by uncleared individuals). A computer has the non-interference property if and only if any sequence of low inputs will produce the same low outputs, regardless of what the high level inputs are.That is, if a low (uncleared) user is working on the machine, it will respond in exactly the same manner (on the low outputs) whether or not a high (cleared) user is working with sensitive data. The low user will not be able to acquire any information
Information
Information in its most restricted technical sense is a message or collection of messages that consists of an ordered sequence of symbols, or it is the meaning that can be interpreted from such a message or collection of messages. Information can be recorded or transmitted. It can be recorded as...
about the activities (if any) of the high user.
Formal expression
Let be a memory configuration, and let
be a memory configuration, and let  and
and 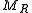 be the projection of the memory
be the projection of the memory 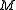 to the low and high parts, respectively. Let
to the low and high parts, respectively. Let  be the function that compares the low parts of the memory configurations, i.e.,
be the function that compares the low parts of the memory configurations, i.e., 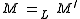 iff
iff  . Let
. Let  be the execution of the program
be the execution of the program 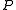 starting with memory configuration
starting with memory configuration 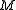 and terminating with the memory configuration
and terminating with the memory configuration  .
.The definition of non-interference for a deterministic program
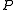 is the following :
is the following :
Strictness
This is a very strict policy, in that a computer system with covert channels may comply with, say, the Bell–LaPadula model, but will not comply with non-interference. The reverse could be true (under reasonable conditions, being that the system should have labelled files, etc.) except for the "No classified information at startup" exceptions noted below. However, non-interference has been shown to be stronger than non-deducibility.This strictness comes with a price. It is very difficult to make a computer system with this property. There may be only one or two commercially available products that have been verified to comply with this policy, and these would essentially be as simple as switches and one-way information filters (although these could be arranged to provide useful behaviour).
No classified information at startup
If the computer has (at time=0) any high (i.e., classified) information within it, or low users create high information subsequent to time=0 (so-called "write-up," which is allowed by many computer security policies), then the computer can legally leak all that high information to the low user, and can still be said to comply with the non-interference policy. The low user will not be able to learn anything about high user activities, but can learn about any high information that was created through means other than the actions of high users.(von Oheimb 2004)Computer systems that comply with the Bell-LaPadula Model do not suffer from this problem since they explicitly forbid "read-up." Consequently, a computer system that complies with non-interference will not necessarily comply with the Bell-LaPadula Model. Thus, the Bell–LaPadula model and the non-interference model are incomparable: the Bell-LaPadula Model is stricter regarding read-up, and the non-interference model is stricter with respect to covert channels.

