IP tunnel
Encyclopedia
An IP tunnel is an Internet Protocol
(IP) network communications channel between two networks. It is used to transport another network protocol by encapsulation
of its packets.
IP tunnels are often used for connecting two disjoint IP networks that don't have a native routing path to each other, via an underlying routable protocol across an intermediate transport network. In conjunction with the IPsec
protocol they may be used to create a virtual private network
between two or more private networks across a public network such as the Internet
. Another prominent use is to connect islands of IPv6
installations across the IPv4
Internet.
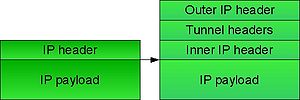 In IP tunnelling, every IP packet, including addressing information of its source and destination IP networks, is encapsulated within another packet format native to the transit network.
In IP tunnelling, every IP packet, including addressing information of its source and destination IP networks, is encapsulated within another packet format native to the transit network.
At the borders between the source network and the transit network, as well as the transit network and the destination network, gateways are used that establish the end-points of the IP tunnel across the transit network. Thus, the IP tunnel endpoints become native IP routers that establish a standard IP route between the source and destination networks. Packets traversing these end-points from the transit network are stripped from their transit frame format headers and trailers used in the tunnelling protocol and thus converted into native IP format and injected into the IP stack of the tunnel endpoints. In addition, any other protocol encapsulations used during transit, such as IPsec or Transport Layer Security
, are removed.
IP in IP
, sometimes called ipencap, is an example of IP encapsulation within IP and is described in RFC 2003. Other variants of the IP-in-IP variety are IPv6-in-IPv4 (6in4
) and IPv4-in-IPv6 (4in6
).
IP tunneling often bypasses simple firewall rules transparently since the specific nature and addressing of the original datagrams are hidden. Content-control software
is usually required to block IP tunnels.
Internet Protocol
The Internet Protocol is the principal communications protocol used for relaying datagrams across an internetwork using the Internet Protocol Suite...
(IP) network communications channel between two networks. It is used to transport another network protocol by encapsulation
Encapsulation (networking)
In computer networking, encapsulation is a method of designing modular communication protocols in which logically separate functions in the network are abstracted from their underlying structures by inclusion or information hiding within higher level objects....
of its packets.
IP tunnels are often used for connecting two disjoint IP networks that don't have a native routing path to each other, via an underlying routable protocol across an intermediate transport network. In conjunction with the IPsec
IPsec
Internet Protocol Security is a protocol suite for securing Internet Protocol communications by authenticating and encrypting each IP packet of a communication session...
protocol they may be used to create a virtual private network
Virtual private network
A virtual private network is a network that uses primarily public telecommunication infrastructure, such as the Internet, to provide remote offices or traveling users access to a central organizational network....
between two or more private networks across a public network such as the Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
. Another prominent use is to connect islands of IPv6
IPv6
Internet Protocol version 6 is a version of the Internet Protocol . It is designed to succeed the Internet Protocol version 4...
installations across the IPv4
IPv4
Internet Protocol version 4 is the fourth revision in the development of the Internet Protocol and the first version of the protocol to be widely deployed. Together with IPv6, it is at the core of standards-based internetworking methods of the Internet...
Internet.

At the borders between the source network and the transit network, as well as the transit network and the destination network, gateways are used that establish the end-points of the IP tunnel across the transit network. Thus, the IP tunnel endpoints become native IP routers that establish a standard IP route between the source and destination networks. Packets traversing these end-points from the transit network are stripped from their transit frame format headers and trailers used in the tunnelling protocol and thus converted into native IP format and injected into the IP stack of the tunnel endpoints. In addition, any other protocol encapsulations used during transit, such as IPsec or Transport Layer Security
Transport Layer Security
Transport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
, are removed.
IP in IP
IP in IP
IP in IP is an IP tunneling protocol that encapsulates one IP packet in another IP packet. To encapsulate an IP packet in another IP packet, an outer header is added with SourceIP, the entry point of the tunnel and the Destination point, the exit point of the tunnel. While doing this the inner...
, sometimes called ipencap, is an example of IP encapsulation within IP and is described in RFC 2003. Other variants of the IP-in-IP variety are IPv6-in-IPv4 (6in4
6in4
6in4 is an Internet transition mechanism for migrating from Internet Protocol version 4 to IPv6. 6in4 uses tunneling to encapsulate IPv6 traffic over explicitly-configured IPv4 links as defined in RFC 4213 . The 6in4 traffic is sent over the IPv4 Internet inside IPv4 packets whose IP headers have...
) and IPv4-in-IPv6 (4in6
4in6
4in6 refers to tunneling of IPv4 in IPv6. It is an Internet interoperation mechanism allowing Internet Protocol version 4 to be used in an IPv6 only network. 4in6 uses tunneling to encapsulate IPv4 traffic over configured IPv6 tunnels as defined in RFC 2473...
).
IP tunneling often bypasses simple firewall rules transparently since the specific nature and addressing of the original datagrams are hidden. Content-control software
Content-control software
Content-control software, also known as censorware or web filtering software, is a term for software designed and optimized for controlling what content is permitted to a reader, especially when it is used to restrict material delivered over the Web...
is usually required to block IP tunnels.
See also
- Tunnelling protocol
- Tunnel Setup ProtocolTunnel Setup ProtocolIn computer networking, the Tunnel Setup Protocol is a networking control protocol used to negotiate IP tunnel setup parameters between a tunnel client host and a tunnel broker server, the tunnel end-points. The protocol is defined in RFC 5572...
- Tunnel brokerTunnel brokerIn the context of computer networking, a tunnel broker is a service which provides a network tunnel. These tunnels can provide encapsulated connectivity over existing infrastructure to a new infrastructure....
- Generic Routing EncapsulationGeneric Routing EncapsulationGeneric Routing Encapsulation is a tunneling protocol developed by Cisco Systems that can encapsulate a wide variety of network layer protocols inside virtual point-to-point links over an Internet Protocol internetwork.-Overview:...

