
IEEE 802.15.4
Encyclopedia
IEEE 802.15.4 is a standard which specifies the physical layer
and media access control
for low-rate wireless personal area network
s (LR-WPANs). It is maintained by the IEEE 802.15
working group.
It is the basis for the ZigBee
, ISA100.11a
, WirelessHART
, and MiWi
specifications, each of which further extends the standard by developing the upper layers
which are not defined by 802.15.4. Alternatively, it can be used with 6LoWPAN
and standard Internet protocols to build a Wireless Embedded Internet.
). The emphasis is on very low cost communication of nearby devices with little to no underlying infrastructure, intending to exploit this to lower power consumption even more.
The basic framework conceives a 10-meter communications range with a transfer rate of 250 kbit/s. Tradeoffs are possible to favor more radically embedded devices
with even lower power requirements, through the definition of not one, but several physical layers. Lower transfer rates of 20 and 40 kbit/s were initially defined, with the 100 kbit/s rate being added in the current revision.
Even lower rates can be considered with the resulting effect on power consumption. As already mentioned, the main identifying feature of 802.15.4 among WPAN's is the importance of achieving extremely low manufacturing and operation costs and technological simplicity, without sacrificing flexibility or generality.
Important features include real-time
suitability by reservation of guaranteed time slots, collision avoidance through CSMA/CA and integrated support for secure communications. Devices also include power management functions such as link quality and energy detection.
802.15.4-conformant devices may use one of three possible frequency bands for operation.
. The definition of the network layers is based on the OSI model
; although only the lower layers are defined in the standard, interaction with upper layers is intended, possibly using a IEEE 802.2
logical link control
sublayer accessing the MAC through a convergence sublayer. Implementations may rely on external devices or be purely embedded, self-functioning devices.
transceiver
and performs channel selection and energy and signal management functions. It operates on one of three possible unlicensed frequency bands:
The original 2003 version of the standard specifies two physical layers based on direct sequence spread spectrum (DSSS) techniques: one working in the 868/915 MHz bands with transfer rates of 20 and 40 kbit/s, and one in the 2450 MHz band with a rate of 250 kbit/s.
The 2006 revision improves the maximum data rates of the 868/915 MHz bands, bringing them up to support 100 and 250 kbit/s as well. Moreover, it goes on to define four physical layers depending on the modulation
method used. Three of them preserve the DSSS approach: in the 868/915 MHz bands, using either binary or offset quadrature phase shift keying (the second of which is optional); in the 2450 MHz band, using the latter. An alternative, optional 868/915 MHz layer is defined using a combination of binary keying and amplitude shift keying
(thus based on parallel, not sequential spread spectrum, PSSS). Dynamic switching between supported 868/915 MHz PHYs is possible.
Beyond these three bands, the IEEE802.15.4c study group is considering the newly opened 314-316 MHz, 430-434 MHz, and 779-787 MHz bands in China, while the IEEE 802.15 Task Group 4d is defining an amendment to the existing standard 802.15.4-2006 to support the new 950 MHz-956 MHz band in Japan. First standard amendments by these groups were released in April 2009.
In August 2007, IEEE 802.15.4a
was released expanding the four PHYs available in the earlier 2006 version to six, including one PHY using Direct Sequence ultra-wideband
(UWB) and another using chirp spread spectrum
(CSS). The UWB PHY is allocated frequencies in three ranges: below 1 GHz, between 3 and 5 GHz, and between 6 and 10 GHz. The CSS PHY is allocated spectrum in the 2450 MHz ISM band.
In April, 2009 IEEE 802.15.4c and IEEE 802.15.4d were released expanding the available PHYs with several additional PHYs: one for 780 MHz band using O-QPSK or MPSK, another for 950 MHz using GFSK or BPSK.
, Unison RTOS and DSPnano RTOS
stacks also use a few items of IEEE 802.15.4 hardware.
The first one is the full-function device (FFD). It can serve as the coordinator of a personal area network just as it may function as a common node. It implements a general model of communication which allows it to talk to any other device: it may also relay messages, in which case it is dubbed a coordinator (PAN coordinator when it is in charge of the whole network).
On the other hand there are reduced-function devices (RFD). These are meant to be extremely simple devices with very modest resource and communication requirements; due to this, they can only communicate with FFD's and can never act as coordinators.
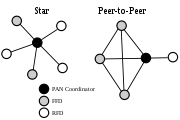
 Networks can be built as either peer-to-peer
Networks can be built as either peer-to-peer
or star
networks. However, every network needs at least one FFD to work as the coordinator of the network. Networks are thus formed by groups of devices separated by suitable distances. Each device has a unique 64-bit identifier, and if some conditions are met short 16-bit identifiers can be used within a restricted environment. Namely, within each PAN domain, communications will probably use short identifiers.
Peer-to-peer (or point-to-point) networks can form arbitrary patterns of connections, and their extension is only limited by the distance between each pair of nodes. They are meant to serve as the basis for ad hoc networks capable of performing self-management and organization. Since the standard does not define a network layer, routing
is not directly supported, but such an additional layer can add support for multihop communications. Further topological restrictions may be added; the standard mentions the cluster tree as a structure which exploits the fact that an RFD may only be associated with one FFD at a time to form a network where RFD's are exclusively leaves of a tree, and most of the nodes are FFD's. The structure can be extended as a generic mesh network whose nodes are cluster tree networks with a local coordinator for each cluster, in addition to the global coordinator.
A more structured star pattern is also supported, where the coordinator of the network will necessarily be the central node. Such a network can originate when an FFD decides to create its own PAN and declare itself its coordinator, after choosing a unique PAN identifier. After that, other devices can join the network, which is fully independent from all other star networks.
are the basic unit of data transport, of which there are four fundamental types (data, acknowledgment, beacon and MAC command frames), which provide a reasonable tradeoff between simplicity and robustness. Additionally, a superframe structure, defined by the coordinator, may be used, in which case two beacons act as its limits and provide synchronization to other devices as well as configuration information. A superframe consists of sixteen equal-length slots, which can be further divided into an active part and an inactive part, during which the coordinator may enter power saving mode, not needing to control its network.
Within superframes contention occurs between their limits, and is resolved by CSMA/CA. Every transmission must end before the arrival of the second beacon. As mentioned before, applications with well-defined bandwidth needs can use up to seven domains of one or more contention
less guaranteed time slots, trailing at the end of the superframe. The first part of the superframe must be sufficient to give service to the network structure and its devices. Superframes are typically utilized within the context of low-latency devices, whose associations must be kept even if inactive for long periods of time.
Data transfers to the coordinator require a beacon synchronization phase, if applicable, followed by CSMA/CA transmission (by means of slots if superframes are in use); acknowledgment
is optional. Data transfers from the coordinator usually follow device requests: if beacons are in use, these are used to signal requests; the coordinator acknowledges the request and then sends the data in packets which are acknowledged by the device. The same is done when superframes are not in use, only in this case there are no beacons to keep track of pending messages.
Point-to-point networks may either use unslotted CSMA/CA or synchronization mechanisms; in this case, communication between any two devices is possible, whereas in “structured” modes one of the devices must be the network coordinator.
In general, all implemented procedures follow a typical request-confirm/indication-response classification.
algorithm; acknowledgments do not adhere to this discipline. Common data transmission utilizes unallocated slots when beaconing is in use; again, confirmations do not follow the same process.
Confirmation messages may be optional under certain circumstances, in which case a success assumption is made. Whatever the case, if a device is unable to process a frame at a given time, it simply does not confirm its reception: timeout-based retransmission
can be performed a number of times, following after that a decision of whether to abort or keep trying.
Because the predicted environment of these devices demands maximization of battery life, the protocols tend to favor the methods which lead to it, implementing periodic checks for pending messages, the frequency of which depends on application needs.
Regarding secure communications, the MAC sublayer offers facilities which can be harnessed by upper layers to achieve the desired level of security. Higher-layer processes may specify keys to perform symmetric cryptography to protect the payload and restrict it to a group of devices or just a point-to-point link; these groups of devices can be specified in access control list
s. Furthermore, MAC computes freshness checks between successive receptions to ensure that presumably old frames, or data which is no longer considered valid, does not transcend to higher layers.
In addition to this secure mode, there is another, insecure MAC mode, which allows access control lists merely as a means to decide on the acceptance of frames according to their (presumed) source.
Physical layer
The physical layer or layer 1 is the first and lowest layer in the seven-layer OSI model of computer networking. The implementation of this layer is often termed PHY....
and media access control
Media Access Control
The media access control data communication protocol sub-layer, also known as the medium access control, is a sublayer of the data link layer specified in the seven-layer OSI model , and in the four-layer TCP/IP model...
for low-rate wireless personal area network
Personal area network
A personal area network is a computer network used for communication among computer devices, including telephones and personal digital assistants, in proximity to an individual's body. The devices may or may not belong to the person in question. The reach of a PAN is typically a few meters...
s (LR-WPANs). It is maintained by the IEEE 802.15
IEEE 802.15
IEEE 802.15 is a working group of the Institute of Electrical and Electronics Engineers IEEE 802 standards committee which specifies wireless personal area network standards. It includes seven task groups.-Task group 1 :...
working group.
It is the basis for the ZigBee
ZigBee
ZigBee is a specification for a suite of high level communication protocols using small, low-power digital radios based on an IEEE 802 standard for personal area networks. Applications include wireless light switches, electrical meters with in-home-displays, and other consumer and industrial...
, ISA100.11a
Isa100.11a
ISA100.11a is an open wireless networking technology standard developed by the International Society of Automation . The official description is "Wireless Systems for Industrial Automation: Process Control and Related Applications"....
, WirelessHART
WirelessHART
WirelessHART is a wireless sensor networking technology based on the Highway Addressable Remote Transducer Protocol .-Description:The protocol utilizes a time synchronized, self-organizing, and self-healing mesh architecture...
, and MiWi
MiWi
MiWi and MiWi P2P are proprietary wireless protocols designed by Microchip Technology that uses small, low-power digital radios based on the IEEE 802.15.4 standard for wireless personal area networks...
specifications, each of which further extends the standard by developing the upper layers
Protocol stack
The protocol stack is an implementation of a computer networking protocol suite. The terms are often used interchangeably. Strictly speaking, the suite is the definition of the protocols, and the stack is the software implementation of them....
which are not defined by 802.15.4. Alternatively, it can be used with 6LoWPAN
6loWPAN
6LoWPAN is an acronym of IPv6 over Low power Wireless Personal Area Networks. 6lowpan is the name of a working group in the internet area of the IETF....
and standard Internet protocols to build a Wireless Embedded Internet.
Overview
IEEE standard 802.15.4 intends to offer the fundamental lower network layers of a type of wireless personal area network (WPAN) which focuses on low-cost, low-speed ubiquitous communication between devices (in contrast with other, more end-user oriented approaches, such as Wi-FiWi-Fi
Wi-Fi or Wifi, is a mechanism for wirelessly connecting electronic devices. A device enabled with Wi-Fi, such as a personal computer, video game console, smartphone, or digital audio player, can connect to the Internet via a wireless network access point. An access point has a range of about 20...
). The emphasis is on very low cost communication of nearby devices with little to no underlying infrastructure, intending to exploit this to lower power consumption even more.
The basic framework conceives a 10-meter communications range with a transfer rate of 250 kbit/s. Tradeoffs are possible to favor more radically embedded devices
Embedded system
An embedded system is a computer system designed for specific control functions within a larger system. often with real-time computing constraints. It is embedded as part of a complete device often including hardware and mechanical parts. By contrast, a general-purpose computer, such as a personal...
with even lower power requirements, through the definition of not one, but several physical layers. Lower transfer rates of 20 and 40 kbit/s were initially defined, with the 100 kbit/s rate being added in the current revision.
Even lower rates can be considered with the resulting effect on power consumption. As already mentioned, the main identifying feature of 802.15.4 among WPAN's is the importance of achieving extremely low manufacturing and operation costs and technological simplicity, without sacrificing flexibility or generality.
Important features include real-time
Real-time computing
In computer science, real-time computing , or reactive computing, is the study of hardware and software systems that are subject to a "real-time constraint"— e.g. operational deadlines from event to system response. Real-time programs must guarantee response within strict time constraints...
suitability by reservation of guaranteed time slots, collision avoidance through CSMA/CA and integrated support for secure communications. Devices also include power management functions such as link quality and energy detection.
802.15.4-conformant devices may use one of three possible frequency bands for operation.
Protocol architecture
Devices are conceived to interact with each other over a conceptually simple wireless networkWireless network
Wireless network refers to any type of computer network that is not connected by cables of any kind. It is a method by which homes, telecommunications networks and enterprise installations avoid the costly process of introducing cables into a building, or as a connection between various equipment...
. The definition of the network layers is based on the OSI model
OSI model
The Open Systems Interconnection model is a product of the Open Systems Interconnection effort at the International Organization for Standardization. It is a prescription of characterizing and standardizing the functions of a communications system in terms of abstraction layers. Similar...
; although only the lower layers are defined in the standard, interaction with upper layers is intended, possibly using a IEEE 802.2
IEEE 802.2
IEEE 802.2 is the IEEE 802 standard defining Logical Link Control , which is the upper portion of the data link layer of the OSI Model. The LLC sublayer presents a uniform interface to the user of the data link service, usually the network layer...
logical link control
Logical Link Control
The logical link control data communication protocol layer is the upper sub-layer of the data link layer in the seven-layer OSI reference model...
sublayer accessing the MAC through a convergence sublayer. Implementations may rely on external devices or be purely embedded, self-functioning devices.
The physical layer
The physical layer (PHY) ultimately provides the data transmission service, as well as the interface to the physical layer management entity, which offers access to every layer management function and maintains a database of information on related personal area networks. Thus, the PHY manages the physical RFRadio frequency
Radio frequency is a rate of oscillation in the range of about 3 kHz to 300 GHz, which corresponds to the frequency of radio waves, and the alternating currents which carry radio signals...
transceiver
Transceiver
A transceiver is a device comprising both a transmitter and a receiver which are combined and share common circuitry or a single housing. When no circuitry is common between transmit and receive functions, the device is a transmitter-receiver. The term originated in the early 1920s...
and performs channel selection and energy and signal management functions. It operates on one of three possible unlicensed frequency bands:
- 868.0-868.6 MHz: Europe, allows one communication channel (2003, 2006)
- 902-928 MHz: North America, up to ten channels (2003), extended to thirty (2006)
- 2400-2483.5 MHz: worldwide use, up to sixteen channels (2003, 2006)
The original 2003 version of the standard specifies two physical layers based on direct sequence spread spectrum (DSSS) techniques: one working in the 868/915 MHz bands with transfer rates of 20 and 40 kbit/s, and one in the 2450 MHz band with a rate of 250 kbit/s.
The 2006 revision improves the maximum data rates of the 868/915 MHz bands, bringing them up to support 100 and 250 kbit/s as well. Moreover, it goes on to define four physical layers depending on the modulation
Modulation
In electronics and telecommunications, modulation is the process of varying one or more properties of a high-frequency periodic waveform, called the carrier signal, with a modulating signal which typically contains information to be transmitted...
method used. Three of them preserve the DSSS approach: in the 868/915 MHz bands, using either binary or offset quadrature phase shift keying (the second of which is optional); in the 2450 MHz band, using the latter. An alternative, optional 868/915 MHz layer is defined using a combination of binary keying and amplitude shift keying
Amplitude-shift keying
Amplitude-shift keying is a form of modulation that represents digital data as variations in the amplitude of a carrier wave.Any digital modulation scheme uses a finite number of distinct signals to represent digital data. ASK uses a finite number of amplitudes, each assigned a unique pattern of...
(thus based on parallel, not sequential spread spectrum, PSSS). Dynamic switching between supported 868/915 MHz PHYs is possible.
Beyond these three bands, the IEEE802.15.4c study group is considering the newly opened 314-316 MHz, 430-434 MHz, and 779-787 MHz bands in China, while the IEEE 802.15 Task Group 4d is defining an amendment to the existing standard 802.15.4-2006 to support the new 950 MHz-956 MHz band in Japan. First standard amendments by these groups were released in April 2009.
In August 2007, IEEE 802.15.4a
IEEE 802.15.4a
IEEE 802.15.4a is an amendment to IEEE 802.15.4 specifying that additional physical layers be added to the original standard.-Overview:...
was released expanding the four PHYs available in the earlier 2006 version to six, including one PHY using Direct Sequence ultra-wideband
Ultra-wideband
Ultra-wideband is a radio technology that can be used at very low energy levels for short-range high-bandwidth communications by using a large portion of the radio spectrum. UWB has traditional applications in non-cooperative radar imaging...
(UWB) and another using chirp spread spectrum
Chirp spread spectrum
In digital communications, Chirp spread spectrum is a spread spectrum technique that uses wideband linear frequency modulated chirp pulses to encode information. A chirp is a sinusoidal signal whose frequency increases or decreases over a certain amount of time...
(CSS). The UWB PHY is allocated frequencies in three ranges: below 1 GHz, between 3 and 5 GHz, and between 6 and 10 GHz. The CSS PHY is allocated spectrum in the 2450 MHz ISM band.
In April, 2009 IEEE 802.15.4c and IEEE 802.15.4d were released expanding the available PHYs with several additional PHYs: one for 780 MHz band using O-QPSK or MPSK, another for 950 MHz using GFSK or BPSK.
The MAC layer
The medium access control (MAC) enables the transmission of MAC frames through the use of the physical channel. Besides the data service, it offers a management interface and itself manages access to the physical channel and network beaconing. It also controls frame validation, guarantees time slots and handles node associations. Finally, it offers hook points for secure services.Higher layers
Other higher-level layers and interoperability sublayers are not defined in the standard. There exist specifications, such as ZigBee, which build on this standard to propose integral solutions. TinyOSTinyOS
TinyOS is a free and open source component-based operating system and platform targeting wireless sensor networks . TinyOS is an embedded operating system written in the nesC programming language as a set of cooperating tasks and processes. It is intended to be incorporated into smartdust...
, Unison RTOS and DSPnano RTOS
DSPnano RTOS
DSPnano is an embedded real-time operating system which is 100% compatible with POSIX and offers a tiny embedded Linux compatible solution. It was first created in 1996 and was one of the first pthread based real-time kernels...
stacks also use a few items of IEEE 802.15.4 hardware.
Node types
The standard defines two types of network node.The first one is the full-function device (FFD). It can serve as the coordinator of a personal area network just as it may function as a common node. It implements a general model of communication which allows it to talk to any other device: it may also relay messages, in which case it is dubbed a coordinator (PAN coordinator when it is in charge of the whole network).
On the other hand there are reduced-function devices (RFD). These are meant to be extremely simple devices with very modest resource and communication requirements; due to this, they can only communicate with FFD's and can never act as coordinators.
Topologies


Peer-to-peer
Peer-to-peer computing or networking is a distributed application architecture that partitions tasks or workloads among peers. Peers are equally privileged, equipotent participants in the application...
or star
Star network
Star networks are one of the most common computer network topologies. In its simplest form, a star network consists of one central switch, hub or computer, which acts as a conduit to transmit messages...
networks. However, every network needs at least one FFD to work as the coordinator of the network. Networks are thus formed by groups of devices separated by suitable distances. Each device has a unique 64-bit identifier, and if some conditions are met short 16-bit identifiers can be used within a restricted environment. Namely, within each PAN domain, communications will probably use short identifiers.
Peer-to-peer (or point-to-point) networks can form arbitrary patterns of connections, and their extension is only limited by the distance between each pair of nodes. They are meant to serve as the basis for ad hoc networks capable of performing self-management and organization. Since the standard does not define a network layer, routing
Routing
Routing is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
is not directly supported, but such an additional layer can add support for multihop communications. Further topological restrictions may be added; the standard mentions the cluster tree as a structure which exploits the fact that an RFD may only be associated with one FFD at a time to form a network where RFD's are exclusively leaves of a tree, and most of the nodes are FFD's. The structure can be extended as a generic mesh network whose nodes are cluster tree networks with a local coordinator for each cluster, in addition to the global coordinator.
A more structured star pattern is also supported, where the coordinator of the network will necessarily be the central node. Such a network can originate when an FFD decides to create its own PAN and declare itself its coordinator, after choosing a unique PAN identifier. After that, other devices can join the network, which is fully independent from all other star networks.
Data transport architecture
FramesData frame
In computer networking and telecommunication, a frame is a digital data transmission unit or data packet that includes frame synchronization, i.e. a sequence of bits or symbols making it possible for the receiver to detect the beginning and end of the packet in the stream of symbols or bits...
are the basic unit of data transport, of which there are four fundamental types (data, acknowledgment, beacon and MAC command frames), which provide a reasonable tradeoff between simplicity and robustness. Additionally, a superframe structure, defined by the coordinator, may be used, in which case two beacons act as its limits and provide synchronization to other devices as well as configuration information. A superframe consists of sixteen equal-length slots, which can be further divided into an active part and an inactive part, during which the coordinator may enter power saving mode, not needing to control its network.
Within superframes contention occurs between their limits, and is resolved by CSMA/CA. Every transmission must end before the arrival of the second beacon. As mentioned before, applications with well-defined bandwidth needs can use up to seven domains of one or more contention
Contention
Contention may refer to:* The main contention, in rhetoric, the main point being argued* Resource contention, a general concept in communications and computing, is competition by users of a system for the facility at the same time:...
less guaranteed time slots, trailing at the end of the superframe. The first part of the superframe must be sufficient to give service to the network structure and its devices. Superframes are typically utilized within the context of low-latency devices, whose associations must be kept even if inactive for long periods of time.
Data transfers to the coordinator require a beacon synchronization phase, if applicable, followed by CSMA/CA transmission (by means of slots if superframes are in use); acknowledgment
Acknowledgment
Acknowledgment may refer to:*Acknowledgment , a statement of gratitude for assistance in producing a work...
is optional. Data transfers from the coordinator usually follow device requests: if beacons are in use, these are used to signal requests; the coordinator acknowledges the request and then sends the data in packets which are acknowledged by the device. The same is done when superframes are not in use, only in this case there are no beacons to keep track of pending messages.
Point-to-point networks may either use unslotted CSMA/CA or synchronization mechanisms; in this case, communication between any two devices is possible, whereas in “structured” modes one of the devices must be the network coordinator.
In general, all implemented procedures follow a typical request-confirm/indication-response classification.
Reliability and security
The physical medium is accessed through a CSMA/CA protocol. Networks which are not using beaconing mechanisms utilize an unslotted variation which is based on the listening of the medium, leveraged by a random exponential backoffExponential backoff
Exponential backoff is an algorithm that uses feedback to multiplicatively decrease the rate of some process, in order to gradually find an acceptable rate.-Binary exponential backoff / truncated exponential backoff:...
algorithm; acknowledgments do not adhere to this discipline. Common data transmission utilizes unallocated slots when beaconing is in use; again, confirmations do not follow the same process.
Confirmation messages may be optional under certain circumstances, in which case a success assumption is made. Whatever the case, if a device is unable to process a frame at a given time, it simply does not confirm its reception: timeout-based retransmission
Timeout (telecommunication)
In telecommunication and related engineering , the term timeout or time-out has several meanings, including...
can be performed a number of times, following after that a decision of whether to abort or keep trying.
Because the predicted environment of these devices demands maximization of battery life, the protocols tend to favor the methods which lead to it, implementing periodic checks for pending messages, the frequency of which depends on application needs.
Regarding secure communications, the MAC sublayer offers facilities which can be harnessed by upper layers to achieve the desired level of security. Higher-layer processes may specify keys to perform symmetric cryptography to protect the payload and restrict it to a group of devices or just a point-to-point link; these groups of devices can be specified in access control list
Access control list
An access control list , with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject...
s. Furthermore, MAC computes freshness checks between successive receptions to ensure that presumably old frames, or data which is no longer considered valid, does not transcend to higher layers.
In addition to this secure mode, there is another, insecure MAC mode, which allows access control lists merely as a means to decide on the acceptance of frames according to their (presumed) source.
See also
- 6LoWPAN6loWPAN6LoWPAN is an acronym of IPv6 over Low power Wireless Personal Area Networks. 6lowpan is the name of a working group in the internet area of the IETF....
- BluetoothBluetoothBluetooth is a proprietary open wireless technology standard for exchanging data over short distances from fixed and mobile devices, creating personal area networks with high levels of security...
- DASH7DASH7DASH7 is an open source wireless sensor networking standard for wireless sensor networking, which operates in the 433 MHz unlicensed ISM band. DASH7 provides multi-year battery life, range of up to 2 km, low latency for connecting with moving things, a very small open source protocol...
- EnOceanEnOceanEnOcean is a German wireless, energy harvesting technology used primarily in building automation systems, based in Oberhaching. It is not set out for international, European or national standardization; however, EnOcean GmbH is offering its technology and licenses for the patented features under...
- IEEE 802.15IEEE 802.15IEEE 802.15 is a working group of the Institute of Electrical and Electronics Engineers IEEE 802 standards committee which specifies wireless personal area network standards. It includes seven task groups.-Task group 1 :...
- INSTEONINSTEONInsteon is a system for connecting lighting switches and loads without extra wiring. INSTEON is a dual-band mesh home area networking topology employing AC-power lines and a radio-frequency protocol to communicate with devices...
- NeuRFonNeuRFonThe neuRFon project was a research program begun in 1999 at Motorola Labs to develop ad hoc wireless networking for wireless sensor network applications...
- SenceiveSenceiveSenceive Ltd. is a wireless mesh network provider for sensor networks based on IEEE 802.15.4 and its proprietary full-mesh networking protocol FlatMesh...
- Wireless personal area network
- ZigBeeZigBeeZigBee is a specification for a suite of high level communication protocols using small, low-power digital radios based on an IEEE 802 standard for personal area networks. Applications include wireless light switches, electrical meters with in-home-displays, and other consumer and industrial...
- Isa100.11aIsa100.11aISA100.11a is an open wireless networking technology standard developed by the International Society of Automation . The official description is "Wireless Systems for Industrial Automation: Process Control and Related Applications"....

