
Carrier sense multiple access with collision detection
Encyclopedia
Media Access Control
The media access control data communication protocol sub-layer, also known as the medium access control, is a sublayer of the data link layer specified in the seven-layer OSI model , and in the four-layer TCP/IP model...
method in which:
- a carrierCarrier waveIn telecommunications, a carrier wave or carrier is a waveform that is modulated with an input signal for the purpose of conveying information. This carrier wave is usually a much higher frequency than the input signal...
sensing scheme is used. - a transmitting dataDataThe term data refers to qualitative or quantitative attributes of a variable or set of variables. Data are typically the results of measurements and can be the basis of graphs, images, or observations of a set of variables. Data are often viewed as the lowest level of abstraction from which...
station that detects another signalTransmission (telecommunications)Transmission, in telecommunications, is the process of sending, propagating and receiving an analogue or digital information signal over a physical point-to-point or point-to-multipoint transmission medium, either wired, optical fiber or wireless...
while transmitting a frame, stops transmitting that frame, transmits a jam signal, and then waits for a random time interval before trying to resend the frame.
CSMA/CD is a modification of pure carrier sense multiple access
Carrier Sense Multiple Access
Carrier Sense Multiple Access is a probabilistic Media Access Control protocol in which a node verifies the absence of other traffic before transmitting on a shared transmission medium, such as an electrical bus, or a band of the electromagnetic spectrum."Carrier Sense" describes the fact that a...
(CSMA). CSMA/CD is used to improve CSMA performance by terminating transmission as soon as a collision is detected, thus shortening the time required before a retry can be attempted.
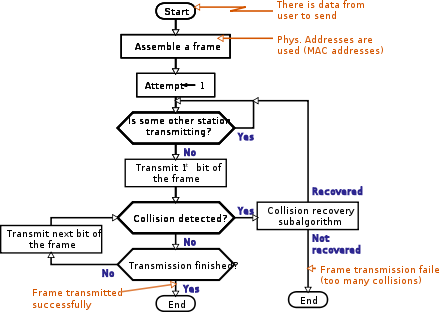
Main procedure
- Frame ready for transmission.
- Is medium idle? If not, wait until it becomes readyOn Ethernet, stations must additionally wait the 96 bit interframe gapInterframe gapEthernet devices must allow a minimum idle period between transmission of Ethernet frames known as the interframe gap , interframe spacing, or interpacket gap . A brief recovery time between frames allows devices to prepare for reception of the next frame...
period. - Start transmitting.
- Did a collision occur? If so, go to collision detected procedure.
- Reset retransmission counters and end frame transmission.
Collision detected procedure
- Continue transmission until minimum packet time is reached to ensure that all receivers detect the collision.
- Increment retransmission counter.
- Was the maximum number of transmission attempts reached? If so, abort transmission.
- Calculate and wait random backoffExponential backoffExponential backoff is an algorithm that uses feedback to multiplicatively decrease the rate of some process, in order to gradually find an acceptable rate.-Binary exponential backoff / truncated exponential backoff:...
period based on number of collisions. - Re-enter main procedure at stage 1.
This can be likened to what happens at a dinner party, where all the guests talk to each other through a common medium (the air). Before speaking, each guest politely waits for the current speaker to finish. If two guests start speaking at the same time, both stop and wait for short, random periods of time (in Ethernet, this time is measured in microseconds). The hope is that by each choosing a random period of time, both guests will not choose the same time to try to speak again, thus avoiding another collision.
Methods for collision detection are media dependent, but on an electrical bus such as 10BASE-5 or 10BASE-2, collisions can be detected by comparing transmitted data with received data or by recognizing a higher than normal signal amplitude on the bus.
Jam signal
The jam signal is a signalSignalling (telecommunications)
In telecommunication, signaling has the following meanings:*the use of signals for controlling communications...
that carries a 32-bit
32-bit
The range of integer values that can be stored in 32 bits is 0 through 4,294,967,295. Hence, a processor with 32-bit memory addresses can directly access 4 GB of byte-addressable memory....
binary pattern sent by a data station to inform the other stations that they must not transmit.
The maximum jam-time is calculated as follows: The maximum allowed diameter of an Ethernet
Ethernet
Ethernet is a family of computer networking technologies for local area networks commercially introduced in 1980. Standardized in IEEE 802.3, Ethernet has largely replaced competing wired LAN technologies....
installation is limited to 232 bits. This makes a round-trip-time of 464 bits. As the slot time in Ethernet is 512 bits, the difference between slot time and round-trip-time is 48 bits (6 bytes), which is the maximum "jam-time".
This in turn means: A station noting a collision has occurred is sending a 4 to 6 byte long pattern composed of 16 1-0 bit combinations. Note: The size of this jam signal is clearly beyond the minimum allowed frame-size of 64 bytes.
The purpose of this is to ensure that any other node which may currently be receiving a frame will receive the jam signal in place of the correct 32-bit MAC CRC, this causes the other receivers to discard the frame due to a CRC error.
Applications
CSMA/CD was used in now obsolete shared media Ethernet variants (10BASE510BASE5
10BASE5 was the original commercially available variant of Ethernet.For its physical layer it used cable similar to RG-8/U coaxial cable but with extra braided shielding. This is a stiff, diameter cable with an impedance of 50 ohms , a solid center conductor, a foam insulating filler, a shielding...
, 10BASE2
10BASE2
10BASE2 is a variant of Ethernet that uses thin coaxial cable , terminated with BNC connectors...
) and in the early versions of twisted-pair Ethernet which used repeater hubs. Modern Ethernet networks built with switches and full-duplex connections no longer utilize CSMA/CD though it is still supported for backwards compatibility. IEEE Std 802.3, which defines all Ethernet variants, for historical reasons still bears the title "Carrier sense multiple access with collision detection (CSMA/CD) access method and physical layer specifications".
Variations of the concept are used in radio frequency
Radio frequency
Radio frequency is a rate of oscillation in the range of about 3 kHz to 300 GHz, which corresponds to the frequency of radio waves, and the alternating currents which carry radio signals...
systems that rely on frequency sharing
Frequency sharing
In telecommunication, frequency sharing is the assignment to or use of the same radio frequency by two or more stations that are separated geographically or that use the frequency at different times....
, including Automatic Packet Reporting System.
See also
- Carrier sense multiple access with collision avoidanceCarrier sense multiple access with collision avoidanceCarrier sense multiple access with collision avoidance , in computer networking, is a wireless network multiple access method in which:*a carrier sensing scheme is used....
(CSMA/CA) - Collision domainCollision domainA collision domain is a section of a network where data packets can collide with one another when being sent on a shared medium or through repeaters, in particular, when using early versions of Ethernet. A network collision occurs when more than one device attempts to send a packet on a network...
- Late collisionLate collisionLate Collision in computer networking is a type of collision found in the CSMA/CD protocol standard. If a collision error occurs after the first 512 bits of data are transmitted by the transmitting station, a late collision is said to have occurred...

