
Access Control Matrix
Encyclopedia
In computer science
, an Access Control Matrix or Access Matrix is an abstract, formal security model
of protection state in computer systems, that characterizes the rights of each subject with respect to every object in the system. It was first introduced by Butler W. Lampson in 1971.
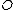 , that is the set of entities that needs to be protected (e.g. processes, files, memory pages) and a set of subjects
, that is the set of entities that needs to be protected (e.g. processes, files, memory pages) and a set of subjects 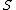 , that consists of all active entities (e.g. users, processes). Further there exists a set of rights
, that consists of all active entities (e.g. users, processes). Further there exists a set of rights  of the form
of the form 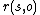 , where
, where 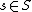 ,
,  and
and 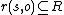 . A right thereby specifies the kind of access a subject is allowed to process object.
. A right thereby specifies the kind of access a subject is allowed to process object.
system. It does not model the rules by which permissions can change in any particular system, and therefore only gives an incomplete description of the system's access control security policy
.
An Access Control Matrix should be thought of only as an abstract model of permissions at a given point in time; a literal implementation of it as a two-dimensional array would have excessive memory requirements. Capability-based security
and access control list
s are categories of concrete access control mechanisms whose static permissions can be modeled using Access Control Matrices. Although these two mechanisms have sometimes been presented (for example in Butler Lampson's Protection paper) as simply row-based and column-based implementations of the Access Control Matrix, this view has been criticized as drawing a misleading equivalence between systems that does not take into account dynamic behaviour.
Computer science
Computer science or computing science is the study of the theoretical foundations of information and computation and of practical techniques for their implementation and application in computer systems...
, an Access Control Matrix or Access Matrix is an abstract, formal security model
Computer security model
A computer security model is a scheme for specifying and enforcing security policies.A security model may be founded upon a formal model of access rights, a model of computation, a model of distributed computing, or no particular theoretical grounding at all....
of protection state in computer systems, that characterizes the rights of each subject with respect to every object in the system. It was first introduced by Butler W. Lampson in 1971.
Definition
According to the model, the protection state of a computer system can be abstracted as a set of objects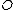 , that is the set of entities that needs to be protected (e.g. processes, files, memory pages) and a set of subjects
, that is the set of entities that needs to be protected (e.g. processes, files, memory pages) and a set of subjects 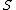 , that consists of all active entities (e.g. users, processes). Further there exists a set of rights
, that consists of all active entities (e.g. users, processes). Further there exists a set of rights  of the form
of the form 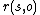 , where
, where 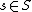 ,
,  and
and 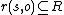 . A right thereby specifies the kind of access a subject is allowed to process object.
. A right thereby specifies the kind of access a subject is allowed to process object.Example
In this matrix example there exists two processes, a file and a device. The first process has the ability to execute the second, read the file and write some information to the device, while the second process can only send information to the first.| Asset 1 | Asset 2 | file | device | |
| Role 1 | read, write, execute, own | execute | read | write |
| Role 2 | read | read, write, execute, own |
Utility
Because it does not define the granularity of protection mechanisms, the Access Control Matrix can be used as a model of the static access permissions in any type of access controlAccess control
Access control refers to exerting control over who can interact with a resource. Often but not always, this involves an authority, who does the controlling. The resource can be a given building, group of buildings, or computer-based information system...
system. It does not model the rules by which permissions can change in any particular system, and therefore only gives an incomplete description of the system's access control security policy
Security policy
Security policy is a definition of what it means to be secure for a system, organization or other entity. For an organization, it addresses the constraints on behavior of its members as well as constraints imposed on adversaries by mechanisms such as doors, locks, keys and walls...
.
An Access Control Matrix should be thought of only as an abstract model of permissions at a given point in time; a literal implementation of it as a two-dimensional array would have excessive memory requirements. Capability-based security
Capability-based security
Capability-based security is a concept in the design of secure computing systems, one of the existing security models. A capability is a communicable, unforgeable token of authority. It refers to a value that references an object along with an associated set of access rights...
and access control list
Access control list
An access control list , with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject...
s are categories of concrete access control mechanisms whose static permissions can be modeled using Access Control Matrices. Although these two mechanisms have sometimes been presented (for example in Butler Lampson's Protection paper) as simply row-based and column-based implementations of the Access Control Matrix, this view has been criticized as drawing a misleading equivalence between systems that does not take into account dynamic behaviour.
See also
- Capability-based securityCapability-based securityCapability-based security is a concept in the design of secure computing systems, one of the existing security models. A capability is a communicable, unforgeable token of authority. It refers to a value that references an object along with an associated set of access rights...
- Access control listAccess control listAn access control list , with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject...
(ACL) - Computer security policyComputer security policyA computer security policy defines the goals and elements of an organization's computer systems. The definition can be highly formal or informal. Security policies are enforced by organizational policies or security mechanisms. A technical implementation defines whether a computer system is secure...
- Computer security modelComputer security modelA computer security model is a scheme for specifying and enforcing security policies.A security model may be founded upon a formal model of access rights, a model of computation, a model of distributed computing, or no particular theoretical grounding at all....

